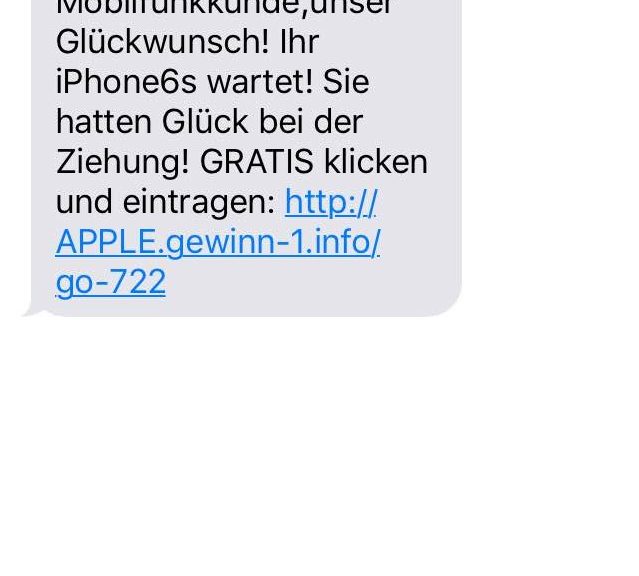
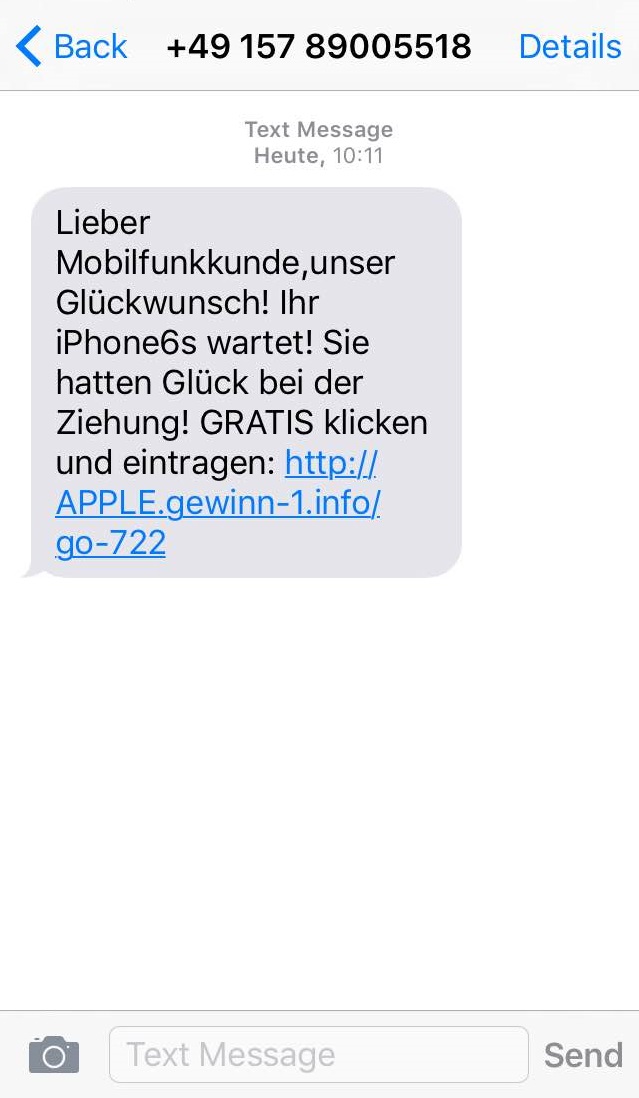
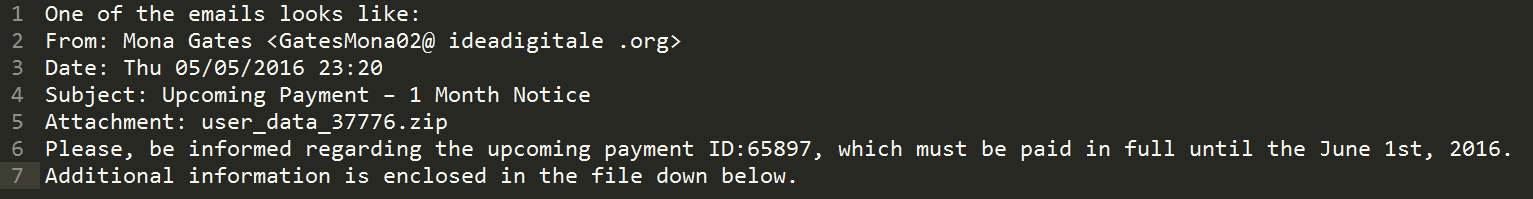
You have already read some of our tips to help prevent the most feared and common cyber-threat of the moment, ransomware; it can hijack your computer and all the computers in your company. Its main strength is that it is able to block computers and encrypt files, and the only one who is able to decrypt it is the cyber-criminal that created it, which is why so many victims are paying the ransom demanded by these attackers.
When an attack is this sophisticated, the only way to combat it is by taking precautions. Any recommendations you may have can help you, but there is a key measure that is worth mentioning: the backup copies are your best allies to resist the escalation of a cyber-abduction.
In the second part of this guide, we will explain what is essential and how you can handle a ransomware attack.
First of all, ransomware does not block everything. If your devices have been infected, the first thing you should check is that the information is really encrypted. There are mediocre cyber-criminals that are taking advantage of the success of better-prepared, cyber-crime mafias. They do these second-rate jobs in order to simulate attacks that in reality don’t actually hijack your files, and then they reap the benefits. If you do not know how to distinguish a real threat from an imposter, make sure to consult an expert before forking the cash over to the bad guys.
Another important thing to consider: Do you have a backup? After you have verified that the attack is in fact a legitimate ransomware, the first thing you need to ask any security professional is if your company has backup copies of everything that is important. It is the only effective defense. If you have backups, you can eliminate the infected system completely, load your backups, and then everything will be back to normal.
Uses reliable tools. Not all programs are equally effective in creating backups. Unfortunately, many organizations have found that the software used to create a backup is not able replace the detailed information exactly the same as it was before the ransomware attack. Choose your work team carefully and protect your files. Good security solutions offer reliable tools.
For security reasons, it is better to keep your backups offline. In addition to this, if you want to keep ransomware from dragging you down, do not store backups on a shared disk. The more isolated your backups are from the network that is possibly infected, the more likely you are to survive and retrieve your sensitive information from them.
Make several different copies. Even if you are the most careful while carrying out these procedures, there is always a fragile moment. Those few minutes when the disk guarding your backup is copying the data, and is connected to the rest of the network. In that precise moment you are vulnerable to a cyber-criminal. In order to prevent infection, it is advisable to backups in several periods: in real time (if resources permit it), daily, weekly and monthly. They must be separate backups, and at least one of them should be disconnected from the rest of the network.
The post A Kidnapping Survival Guide: How to Combat Digital Ransomware (Part 2) appeared first on Panda Security Mediacenter.

![]()