Connections are made and maintained online via social media
You can get insight into the life of a stranger through their Instagram photos, Snapchats, or profile pages, but when does it become too much? Our names alone can connect the dots for a perpetrator, making it easy to know our whereabouts. Information about where we work, where we went to University, or where our favorite coffee shop is…it’s all online. Everything you “share” can have serious backlash: identity theft.
Celebrities are commonly impersonated online, on fake Instagram and Facebook accounts, but they are not the only ones who need to keep track of their digital reputations. A stranger can copy your photos and concoct their own version of your life. It could be very possible that someone has already impersonated you.
Fight the fakes
The social network created by Mark Zuckerberg is fighting these fake accounts. A tool has been created that automatically notifies users who may be victims of phishing. This feature is already available in 75% of the world’s countries.
When Facebook detects that another person may be posing as you, they automatically notify you about the potentially “fake” profile. After that, the user can confirm or deny whether the profile is a fake. If it’s confirmed, Facebook gets to work; more specifically, the team manually carries out this part of the notification system.
Although they say impersonation is not a widespread problem, Zuckberberg has added this to the list of harassment he doesn’t want associated with his company. To fight it, they will continue their strict and controversial naming policy (requiring users to identify themselves with their real names), but will also actively pursue phishers.
Using our photos without our consent
Facebook has also launched two other security features that are next in line. One is a new system that reports the existence of intimate photos shared without the user’s consent and the other is a tool that lets them check the security status of images uploaded to their accounts. They have also introduced a feature that gives users the ability to manage the privacy settings of their photos (Who can see them? Do you really want them to be public?).
Though security is always advancing, the bad guys of the Internet are closely following behind. Next time you decide to upload personal photos, “check-in” to a geographical location, or update your work history on LinkedIn, remember that someone, somewhere might use your identity for their own personal gain.
The post Facebook alerts you if someone tries to steal your identity appeared first on Panda Security Mediacenter.






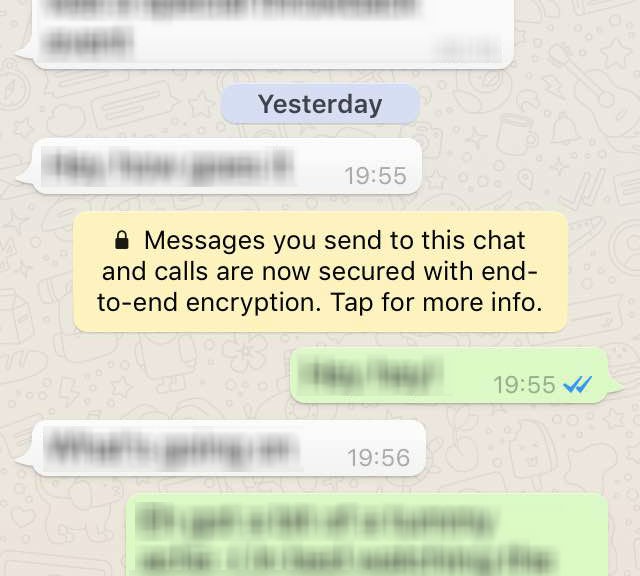
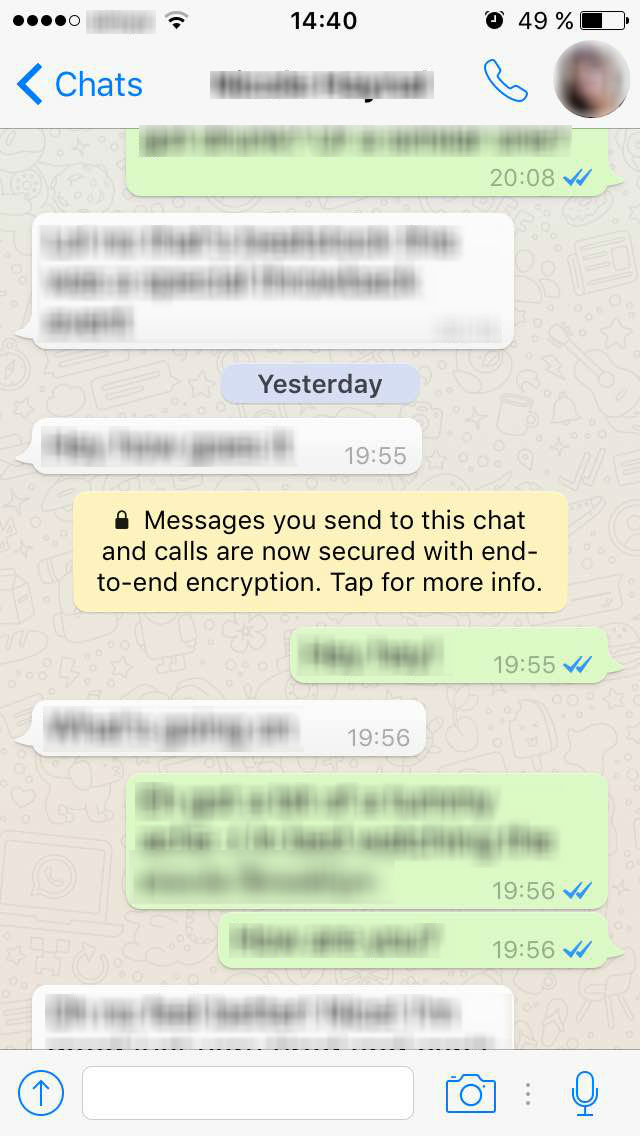
 Avid WhatsApp-ers were the first ones to notice the new security changes the company put into action last week. Now, your conversations on WhatsApp are safer through end-to-end encryption. With this new security system, your messages safely travel from mobile to mobile, from your hands to the person on the other side of the message.
Avid WhatsApp-ers were the first ones to notice the new security changes the company put into action last week. Now, your conversations on WhatsApp are safer through end-to-end encryption. With this new security system, your messages safely travel from mobile to mobile, from your hands to the person on the other side of the message.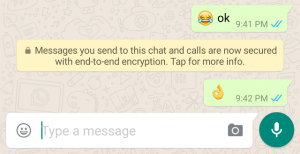


 Alan Scott (center) and fellow Mid-Valley Literacy Center staff members having a blast during a company fundraiser.
Alan Scott (center) and fellow Mid-Valley Literacy Center staff members having a blast during a company fundraiser.