“The main threats targeting Mac users are mostly adware, but this new threat shows that the trend may change.”

For Mac users, hell has finally frozen over. The first case of working ransomware targeting OS X was reported this past weekend.
“This is the first one in the wild that is definitely functional, encrypts your files and seeks a ransom,” said Palo Alto Threat Intelligence Director Ryan Olson in a Reuters interview. The researchers dubbed the ransomware “KeRanger.”
Ransomware has successfully attacked Windows and Android users, usually when a user is tricked into clicking an infected link in an email or an infected ad on a website. The ransomware then locks all the files in the system and demands money for a key that will unlock the files. (another good reason not to click on links in emails.)
“Any ransomware that gets onto your device, whether a Mac, PC, or smartphone, is a serious threat. Most people are scared when they see their device has been locked and their data has been encrypted so they pay the ransom,” said Jan Sirmer, a researcher from the Avast Virus Lab. “We generally advise against paying the ransom, because this rewards the malware authors for their work and encourages them to continue spreading ransom, but sometimes it can’t be helped.”
One of the most recent attacks locked up the servers of the Hollywood Presbyterian Medical Center in Los Angeles. Because their patient records are vital to hospital operation, they opted to pay $17,000 in bitcoin, the preferred digital currency of cybercrooks, to get them back. Law enforcement offices have been victims as well.
![]()
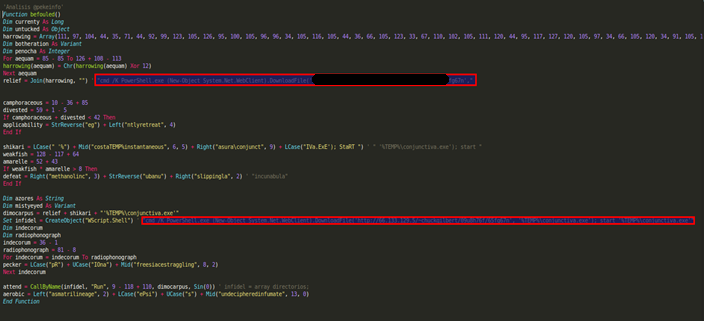


 It’s that time of the year again – tax season is upon us.
It’s that time of the year again – tax season is upon us.