Ever answered your mobile phone only to find silence? Or that a machine has called you? Or even that it’s a completely unexpected call from someone claiming to be from the Internal Revenue Service (IRS)?
![]()
Ever answered your mobile phone only to find silence? Or that a machine has called you? Or even that it’s a completely unexpected call from someone claiming to be from the Internal Revenue Service (IRS)?
![]()

The following could be the story plot of the next Hollywood horror blockbuster. Average Paul works hard all year to put food on the table like millions of Americans. And being the good guy that he is, Average Paul understands that paying taxes is part of the game (even though he feels he pays too much of it).
Now, Average Paul has heard he could file his taxes online. He thinks it’s worth a shot: he’s expecting a bit of money back, and if there’s enough, he’ll take the family to Indiana to visit the in-laws. Some websites even say e-filing with them is completely free so why would he go to a physical agent. There’s nothing wrong about that!
The IRS, which administers the Internal Revenue Code here in the US, is keen to get a share of Average Paul’s revenues and has set-up a secured website for that very purpose. So has scammer Joe Crook, but his website isn’t secure at all. And this is where the horror story begins.
Average Paul is a busy guy, he’s gone online at the end of his latest shift, and he’s entered all sort of personal information on a website he found on Google. The problem is, he’s not on the IRS Internet site, neither he is on a certified website that helps in preparing and e-filing his federal and state Income taxes. He’s made his way onto Joe Crook’s fake website, and he’s about to get scammed.
Preparing your tax returns is a battle itself. Everyone wants to pay the least they can. It’s one of those universal truths. How can you make sure you’re not sharing confidential details with shady characters like Joe Crook? How can you do the right thing without being left out of pocket later on?
Last year the IRS disclosed that more than 700,000 social security numbers and other sensitive information had been stolen. Sadly, there’s no silver bullet to protect yourself when those entrusted with our information fail to keep it safe! Fortunately, you can take action by protecting your computer and mobile devices from malware and virus with Panda Security. The company has brought to the market multiple packages to suit all budgets. It pays to protect your computer.
This tax season, be clever and don’t let Joe Crook fleece you out. By being protected, you are not only saving yourself, but you are preventing Joe Crook from developing his so-called “business.” Don’t support the scammers by being unprepared!
The post Paying taxes is taxing enough appeared first on Panda Security Mediacenter.

It’s true that it’s easiest and most convenient to start using new devices or software with their default settings. But it’s not the most secure, not by a long shot. Accepting the default configuration without reviewing what it actually is could be dangerous to your company’s confidential information.
The default settings are predetermined by the manufacturer and basically put usability before all else. In the case of a router, for example, this could be a predefined password, or in the case of an OS it could be the applications that come preinstalled. The primary concern is for the ease of use when getting started with a new product, without having to perform the configuration yourself. With three or four clicks, you’re ready to enjoy the use of your new device and are probably barely aware of having accepted the default settings.
The problem is, in many cases, the default passwords for a slew of devices (everything from routers to POS terminals) are easy to find on forums and other easy-to-find places on the internet. Case in point, one POS manufacturer used the same password for 25 years: 166816. The credential was easy to find with a simple Google search. Any business that failed to change the password was unwittingly exposing themselves and their clients to cyberattacks.
And money isn’t the only thing at stake. We need look no further than the our own company’s wifi network to witness serious potential danger, namely that the default credentials it comes with could be easily compromised. The danger is that someone from outside could connect the corporate network and even make internal changes, possibly even locking the owners out of it. It wouldn’t take an evil genius. If your device’s default configuration hasn’t been change, all it would take is someone with some basic technical skills and access to the Internet.
Any IT department in any corporate environment should be aware that changing the default sittings isn’t just about changing the password. In fact, the best thing would be to personally configure all operating systems from the beginning to increase their security.
It should be up to the company, for example, which applications and programs will be installed on the devices that employees will use, removing or adding options from the predefined ones, thus avoiding any software that is not going to be used. Such software, it should be said, could also end up being an added vulnerability. If at some point the program stops receiving security updates, it could actually become a gateway for cybercriminals. If it is unnecessary, might as well get rid of it and save yourself from future hassles.
In short, any configuration that comes straight from the factory can pose a short- or medium- term risk for companies. The best thing to do is to create a customized configuration with which security and protection against possible attacks remains in the hands of the company’s IT experts.
The post Default Settings, and Why the Initial Configuration is not the Most Secure appeared first on Panda Security Mediacenter.
Avast is a fantastic employer, we have offices around the world, and a cool company culture . More than 20% of Avast employees are women, which means there are 435 of us! For International Women’s Day on March 8th, we asked our female colleagues a few questions to find out why they like working for Avast.
![]()
Often seen as a male-dominated industry, women have played an important part in driving developments in the computer industry. As we celebrate International Women’s Day, these eight women have blazed a trail in IT, setting an example to us all.
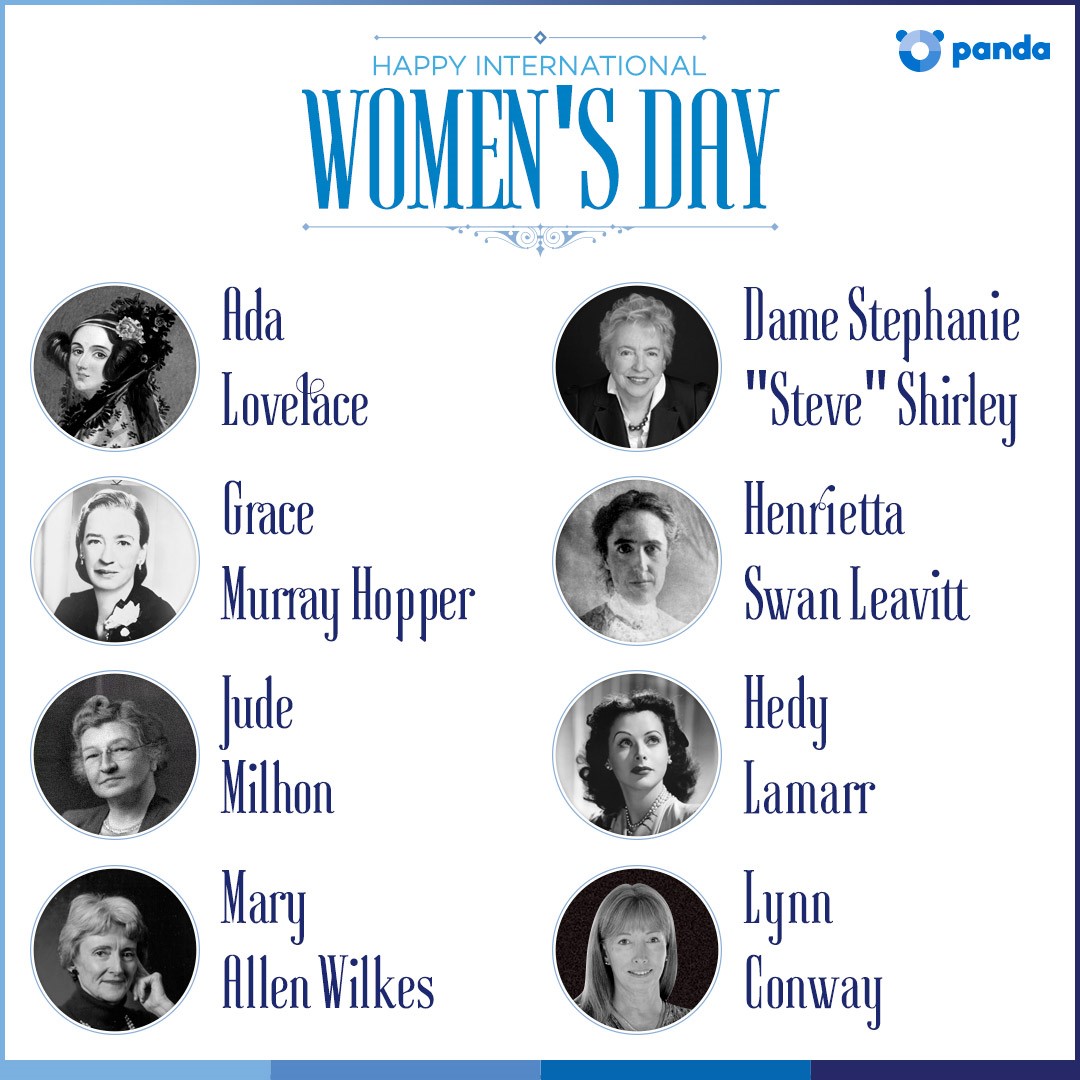 Ada Lovelace
Ada LovelaceDespite being the daughter of the well-known bohemian hell-raiser George Byron, Ada Lovelace’s own life was incredibly successful, albeit slightly less “colourful”. Encouraged to study maths and logic by her mother, Ada’s studies soon brought her into contact with Charles Babbage, ‘the father of computers’.
As part of her work with Babbage, Ada created what is believed to be the first ever computer program – an algorithm to be run by Babbage’s legendary Analytical Engine.
As well as being a Rear Admiral in the United States Navy, Grace was one of the first programmers of the Harvard Mark I computer. Her work led to the creation of the first compiler – a tool used to change computer code into a fully-functioning application.
Grace was also instrumental in creating COBOL, one of the first programming languages, and one that is still in use today.
During study for a graduate degree, Henrietta began working at the Harvard College Observatory. Her job – as a human computer was to help grade photographs taken through the observatory’s telescope, and to perform complex mathematical calculations.
Henrietta’s work paved the way for the techniques used by astronomers today to calculate the distance between Earth and distant galaxies.
Best known as a Hollywood actress, Hedy Lamarr was also an accomplished inventor in between roles. During World War II, Hedy helped to create a jam-proof radio guidance system to be used with torpedoes.
Although this signal-hopping technology was deployed by the US Navy until the 1960s (where it proved to be particularly effective), it is still in use today. The same basic principles are also used in modern WiFi and Bluetooth radio technologies – like those that make your smartphone and tablet work wirelessly.
After leaving school, Stephanie went to work for the Post Office Research Station where she helped build computers from scratch. She also learned to program machine code – the very low level language used by computer parts to work properly.
In 1962, Stephanie founded Freelance Programmers, a software company with the intention of helping women get into IT – just 1% of her programmers were male. The team worked on a broad range of projects, including the black box recorder for the supersonic jetliner, Concorde.
Having taught herself to program computers, Jude’s first job was in the IT department of a US food manufacturer. She also helped to create the Berkley Software Distribution (BSD) operating system which is still in use today.
Jude was also a committed social activist and hacker, going by the name of “St Jude”. Coining the term “cypherpunks”, St Jude helped to promote the idea of using cryptography to protect personal information as a route to social and political change.
Despite majoring in philosophy and theology, Mary became a computer programmer at the Massachusetts University of Technology. Initially she was programming IBM systems as part of a speech recognition project.
Later Mary was moved to a team working on LINC, widely believed to be the world’s first “personal computer”. As far back as 1964, Mary was using the LINC computer at home to refine the system’s design.
After a very successful period at university, Lynn was recruited by IBM to work on a project designing an advanced supercomputer. Known as the Advanced Computing Systems (ACS) project, the resulting computer is believed to have been an example of the first superscalar design.
Later Lynn worked for major organisations including DARPA and Xerox, and MIT as an associate professor.
Although these women may serve as examples to women considering a career in IT, their experiences and achievements are actually a lesson for all young people – regardless of gender.
The post International Women’s Day: 8 empowered woman in the computing world appeared first on Panda Security Mediacenter.
After years of using hotspots, many of us who connect our PCs via Wi-Fi away from home have learned the difference between secured and unsecured networks – and are now smarter and safer when we get online at the café or airport. But our connection habits are changing. In 2016, average smartphone usage grew 38 percent, and more mobile phone traffic – nearly 60 percent – was handled by Wi-Fi hotspots than by cellular networks, putting our phones at risk, too. Add the proliferation of Internet of Things (IoT) devices, and today’s Wi-Fi threats can outpace even the tech-savviest among us. Because we have greater mobility and connectivity, hackers are motivated to take advantage of our need for both.
![]()
http://www.pandasecurity.com/mediacenter/src/uploads/2017/03/IMG-MC-bromaimpresoras-300×225.jpg
Printers are everywhere, but they’re not exactly the sort of device that we pay especial attention to when it comes to our businesses IT security infrastructure. In reality, corporate networks of printers that are not properly protected could end up being one of the company’s biggest security gaps.
A spectacular example of this can be found in an apparently mysterious event that recently affected more than 160,000 printers all over the world. Without warning, every one of them printed the same document, which warned that the printer in question would now be part of a bot network. In short, the printer had been infected and now seemed to respond only to orders coming from its new cybercriminal master.
Whatevs, flaming botnet. I DON’T EVEN LIKE THE OFFICE PRINTER. @lmaostack pic.twitter.com/UKxE9aKxCL
— Stephanie Sanchez (@IAmStephanieS) February 6, 2017
As it turns out, behind this singular attack was Stackoverflowin, an enigmatic hacker who explained that the whole thing was a joke intended to raise awareness of printers’ vulnerabilities. “It was kind of on impulse,” he acknowledged. As he explained, he was looking to raise awareness of how dangerous it is to expose connected printers to the public internet without a firewall or other tools.
In order for the humor of this singular attack to be noticed, the hacker’s warning came with a fun robot drawn with ASCII art. But jokes aside, the situation really is quite serious: printers of every kind and from all over the world have fallen into Stackoverflowin’s trap.
To achieve this, the hacker developed a script able to track printers connected to the Internet with one of its ports open. Using the open port, he was able to order the device to print the enigmatic document.
However, it is actually quite simple to heed Stackoverflowin’s warning and fix the problem. Just make sure that the ports on the printer network have a secure password and that all devices on your corporate network are covered by the right protection to avoid cyberattacks that, next time, may not be so friendly.
In case this wasn’t enough, a group of German researchers has published a study that shows that numerous printer security flaws can be exploited to access the memory of these devices and steal data such as passwords or even confidential documents. So check your printers! This is an issue that we collectively need to take more seriously, and these potentially vulnerabilities are worth looking into.
The post Over a Hundred Thousand Printers Simultaneously Ghost Printed Goofy ASCII Art appeared first on Panda Security Mediacenter.
People often trust their social media contacts more than traditional advertising, and more readily believe everything from restaurant reviews to political opinions when it comes from a social network. An amusing or tragic anecdote that may not be representative of any trend has a better chance of going viral than a well-reported story with lots of analysis and facts. As always, there are marketers, abusers, propagandists, and outright criminals who are quick to exploit these psychological biases. The person who attacks you over a political tweet may be a paid troll or a robot. The spam you ignored in your inbox is now served into a trusted social media feed. The phishing attacks and malicious links you’d never click on in an anonymous email may now appear as a recommendation from a good friend, or a celebrity you admire. These attacks may even be customized by AI to target you perfectly, the way you get shopping or movie recommendations.
![]()
Mobile threats are on a rise, becoming more sophisticated and difficult to detect.We expect that in 2018 it will reach the same magnitude as PC malware.
![]()
http://www.pandasecurity.com/mediacenter/src/uploads/2017/03/pandasecurity-smartwatch-antivirus-300×225.jpg
Once upon a time… many, years ago, telephones were meant to call people up, and watches were made to tell the time. Life was simple then. Well, kind of. That all changed when things got smaller, and once they got smaller they got smarter: the phones got smarter, and so did the wristwatches. Don’t get me wrong, the benefits of miniaturization are immense. But “smart” comes at a price. Increased capabilities and connectivity are leaving our latest gadgets and devices exposed to baddies. That begs the question: is your smartwatch protected?
The idea of anyone hacking into your old Timex does sound ludicrous. However, newer smartwatches present severe challenges to developers: how can a digital watch win the battle against hackers? Remember, we’re talking about a device that goes far beyond telling the time. It can be used to monitor health conditions, or make payments by linking up with your bank. Nobody sensible fancies sharing their medical files around… or bank details for that matter!
Many manufacturers of smartwatches, from Asus, Huawei, and LG to Samsung, Moto and Tag Heuer, have chosen Google’s Android Wear 2.0 operating system for their products. Android Wear integrates Google Now and provides the ability to download applications from Google Play Store, amongst other benefits. In the coming years, the smartwatch market will develop further with device shipments expected to keep growing through the year 2021 to reach 70 million units. That presents criminals with a brand new area where to operate. Don’t let them short-change you.
Analysts expect Apple devices to continue leading a big portion of the smartwatch market. But Android Wear devices will quickly catch up as the technology gets adopted increasingly in emerging markets. Functionalities are growing exponentially driven by technological advances and so does the risks to security. It’s no wonder consumers are looking for better protection for their wearable products.
Smart devices collect an awful lot of data these days, so if this data isn’t properly stored and managed, it can lead to security breaches of monumental proportions. All it takes is a malicious and unscrupulous commercial entity acquiring this data to make your life a misery. Increasingly, consumers across the country realize the need to protect themselves. Anti-virus software from companies like Panda Security has got the answer, covering many operating systems all at once. What’s best, it’s even possible to try out this protection for a month free of charge.
It’s worth looking into. You wouldn’t let your wallet on a table, or share credit card details around, would you…? Of course not! Now, you’re carrying your financial details around your wrist, and this requires careful consideration. Isn’t it time you protect your assets? Check out today what Panda Security can do for you.
The post Androidwear 2: is your smartwatch protected? appeared first on Panda Security Mediacenter.