With SMS we saw how the language evolved in order to save characters, now the way we express ourselves through mobile devices has experienced a new transformation. With the arrival of instant messaging apps, with WhatsApp on top, there are people who are able to communicate exclusively with emoticons.

Humans move freely between images. This is why, we could not miss the innovation that would set aside the numbers and characters of our language to create new passwords based on illustrations. But these are not just any scribbles, these are precisely those emojis that are revolutionizing the way in which we express ourselves.
The company Intelligence Environment has developed the first password in which they don’t alternate numbers and letters, but emoticons. “Our research shows 64% of ‘millennials’ regularly communicate only using emojis” said David Webber, Manager Director of the company. “So we decided to reinvent the passcode for a new generation by developing the world’s first emoji security technology”.
In order to replace the passwords that we usually use to access applications and services via the Internet, this British developer has created a system in which the sequence of expressions, hand universal gestures and so many other visual realities make things more difficult for those trying to access what they shouldn’t.
The creators of this new way of composing passcodes claim that this system, as well as being more comfortable for the user, increases the security of passwords, since there are many more combinations based on emoticons. “There are 480 times more permutations using emojis over traditional four digit passcodes” says Webber.
Users will be able to choose from 44 emoticons, which are available on all operating systems. According to the British company’s estimates, these emojis can give up to 3,498,308 million unique permutations. In case of only using combinations with numbers from 0 to 9, as we do today for example with our credit card PIN, options are reduced to only 7,290 permutations.
This way we can create stories which are easier to remember and take advantage of one of the main benefits of this new access codes system. Rather than monotonous successions of letters and numbers which we repeat in several services to prevent our memory from playing us a dirty trick, with Emoji Passcode we will be able to create different passwords for different platforms.
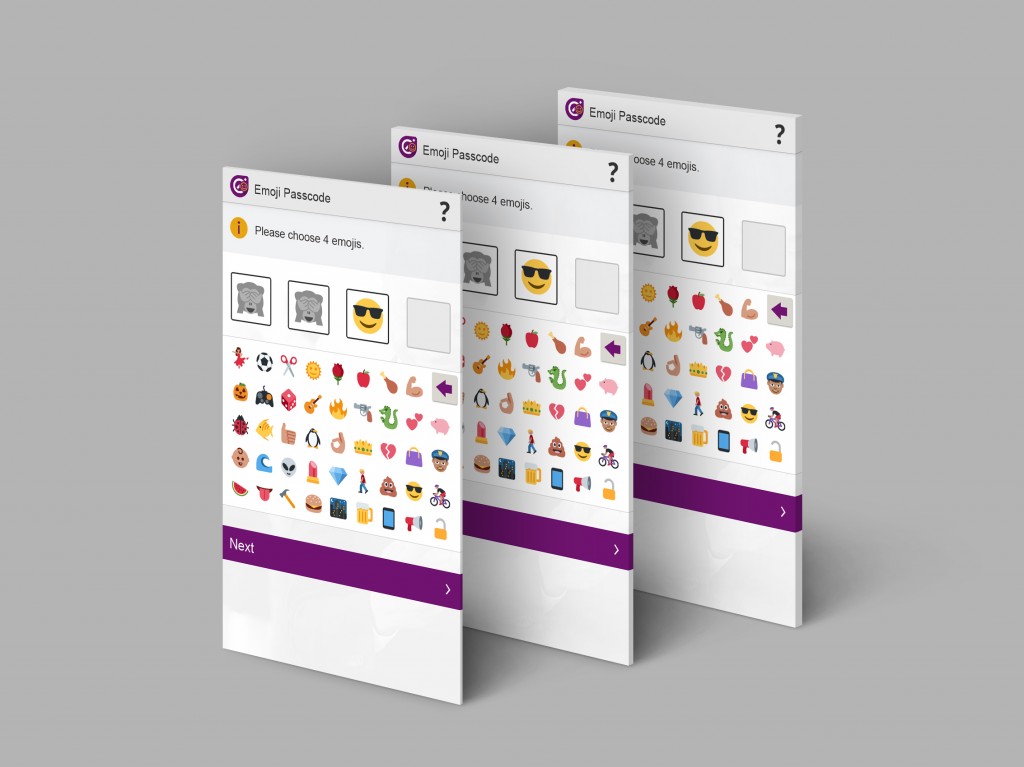
According to a study conducted by Intelligence Environment in United Kingdom, one third of the over 1,300 people who took part in a survey claimed to have forgotten the PIN for their credit cards recently. Therefore, this British company’s managers intend to implement their new creation, first of all, in the services offered by banks via the Internet.
Tony Buzan took part in the creation of this Emoji Passcode. He is a British memory expert memory who pointed out that this new method of passwords “plays to humans’ ability to remember pictures”. Something which as this educational consultant claims, “It is anchored in our evolutionary history. We remember more information when it’s in pictorial form”.
If within a few months we come across this new password method, we will possibly fail on our first attempts. However, as time goes by, remembering or forgetting our passwords will depend on the same factors as it does today: mainly, that our memory wants or not to play us a dirty trick.
The post Passwords using emojis. Are they safer? appeared first on MediaCenter Panda Security.


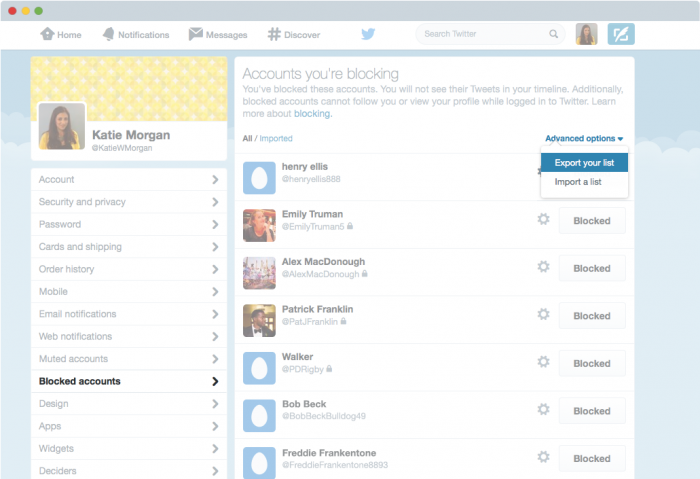
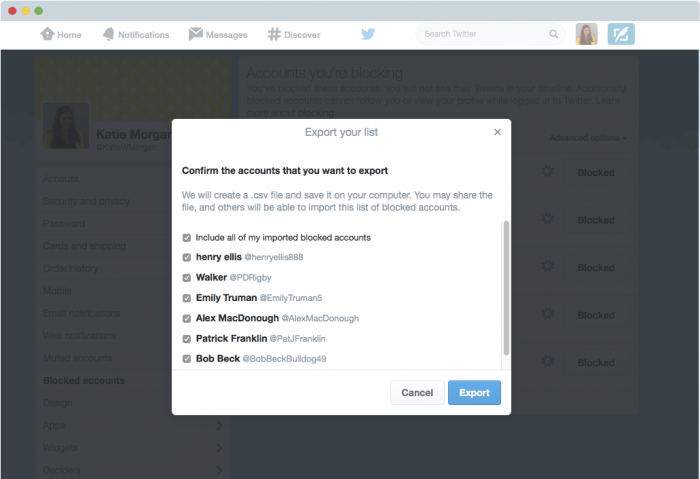



 More than 600 million Samsung phones were reported to be at risk because of a vulnerability found in the keyboard app SwiftKey. The best way to protect yourself is to use a virtual private network (VPN) when using an unsecured Wi-Fi hotspot. If you have a Samsung S6, S5, or S4, you need to read
More than 600 million Samsung phones were reported to be at risk because of a vulnerability found in the keyboard app SwiftKey. The best way to protect yourself is to use a virtual private network (VPN) when using an unsecured Wi-Fi hotspot. If you have a Samsung S6, S5, or S4, you need to read  As we learned from the Hola VPN service revelations, any old VPN service will not do. Hola was selling their users’ bandwidth and installing and running code on their devices without their knowledge or permission. Find out the details in
As we learned from the Hola VPN service revelations, any old VPN service will not do. Hola was selling their users’ bandwidth and installing and running code on their devices without their knowledge or permission. Find out the details in  Mobile developer Martin Banas, attended Apple’s Worldwide Developers Conference in San Francisco. Besides spending lots of time standing in lines, he enjoyed meeting other developers and hearing the latest news about OS X El Capitan and Apple Pay. Weren’t able to attend, bit wish you could have? Martin’s conference report,
Mobile developer Martin Banas, attended Apple’s Worldwide Developers Conference in San Francisco. Besides spending lots of time standing in lines, he enjoyed meeting other developers and hearing the latest news about OS X El Capitan and Apple Pay. Weren’t able to attend, bit wish you could have? Martin’s conference report, 

 More from the Edward Snowden files. It was revealed this week that U.S. and U.K. spy agencies were attempting to reverse engineer major antivirus companies software, including Avast’s. CEO Vince Steckler spoke to RT News about government spying in the computer age. You can read the article,
More from the Edward Snowden files. It was revealed this week that U.S. and U.K. spy agencies were attempting to reverse engineer major antivirus companies software, including Avast’s. CEO Vince Steckler spoke to RT News about government spying in the computer age. You can read the article,  And if the real world of cybercrime is not enough, our favorite new show of the summer Mr. Robot debuted on the USA Network this past week. We excitedly watched the first episode then talked to Avast security expert, Pedram Amini, to find out
And if the real world of cybercrime is not enough, our favorite new show of the summer Mr. Robot debuted on the USA Network this past week. We excitedly watched the first episode then talked to Avast security expert, Pedram Amini, to find out 
