The Spanish Police has warned of the reappearance of the Police Virus for Android.
Here we explain you how can they attack your cell phone, and what can you do to protect it!
*** Posted June 2, 2014
A few days ago a new Android malware showed up, Android/Koler.A. It was in the news as it was actually a Police Virus / ransomware attack, similar to the ones we have seen in Windows computers, but this time it was targeting mobile phones.
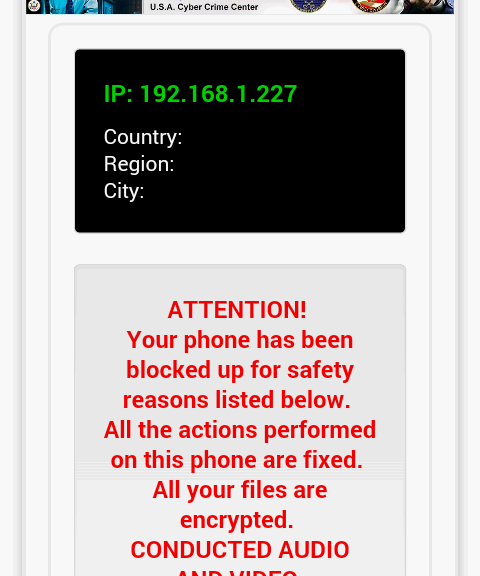
Although in this case this piece of malware cannot encrypt any of the phone data, it is nasty and it is really difficult to get rid of it (without antivirus for Android), as the warning message is always on top and the user has only a few seconds to try to uninstall it.
While we were studying it, we found a new variant exactly the same as the first one but this one was connecting to a different server, in order to download the proper warning. And this server was still up… It turns out that the cybercriminals made a small mistake configuring it and left the door half-opened Sadly, we could not get access to all the information there (there was a mysql database with all the payments, infections, etc. that we couldn’t reach ) but still we were able to download some files from the server and take a look at how it works.
I won’t go into details about the mistake they made to leave that door half-opened, as of course we do not want to help them 
Unsurprisingly, the way it works from the server side is really similar to the ones targeting Windows and that we have seen in the past: a number of scripts to geolocalize the device and show the message in the local language and with the images of local law enforcement. It saves information from all infected devices in the database and it takes the IMEI number of the mobile phone, adding the MD5 of the malware that is infecting the device. Doing this they can track the number of infections per malware variant and measure the success of their different infection campaigns.
This Trojan is targeting users from 31 different countries from all around the world; 23 of them are Europeans:
Austria, Belgium, Czech Republic, Germany, Denmark, Finland, France, Greece, Hungary, Ireland, Italy, Latvia, Netherlands, Norway, Poland, Portugal, Romania, Spain, Sweden, Switzerland, Slovenia, Slovakia and United Kingdom.
Users from these countries are also being targeted: Australia, Bolivia, Canada, Ecuador, Mexico, New Zealand, Turkey and United States of America.
What if you have already been infected?
Well, probably you won’t have an antivirus installed in your phone, which makes the clean up a bit difficult. The “infection” screen will be on top of everything, and this malware also disables the Back key. However the Home button will still work, so you can give it a try, push the Home buttom, go to the App menu and uninstall the malicious app:
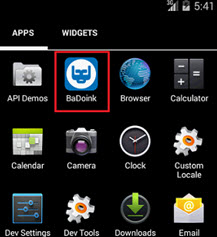
The bad news is that you will only have 5 seconds to do this, as the warning screens pops up every 5 seconds. What can you do then? Well, you just need to restart your phone in “safe mode“. Depending on the mobile phone you have, it can be made in different ways. Those running pure Android versions (Nexus, Motorola) only need to go to the shutdown menu and press for a couple of seconds on shutdown, until the following message shows up:
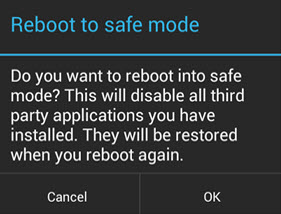
Click OK, and once the phone is restarted you can uninstall the malicious app. To go back to normal just restart the phone in the usual way. If you are using a phone with a custom Android version (Samsung, etc.), you can easily use Google to find out how it is done in your device.
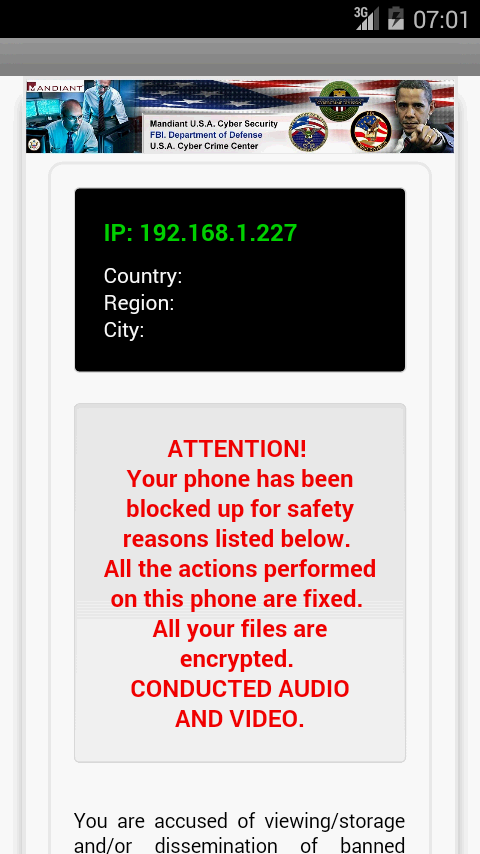
We managed to grab the ransom message screens for every country, where you can find a number of known people, such as the Obama (president of the United States), François Hollande (president of France), Queen Elisabeth… It was also funny to see in the US one that they mention Mandiant (the company who showed up how China had in their army a cyber-espionage unit).
The post The Police Virus strikes again! Android systems attacked! appeared first on MediaCenter Panda Security.