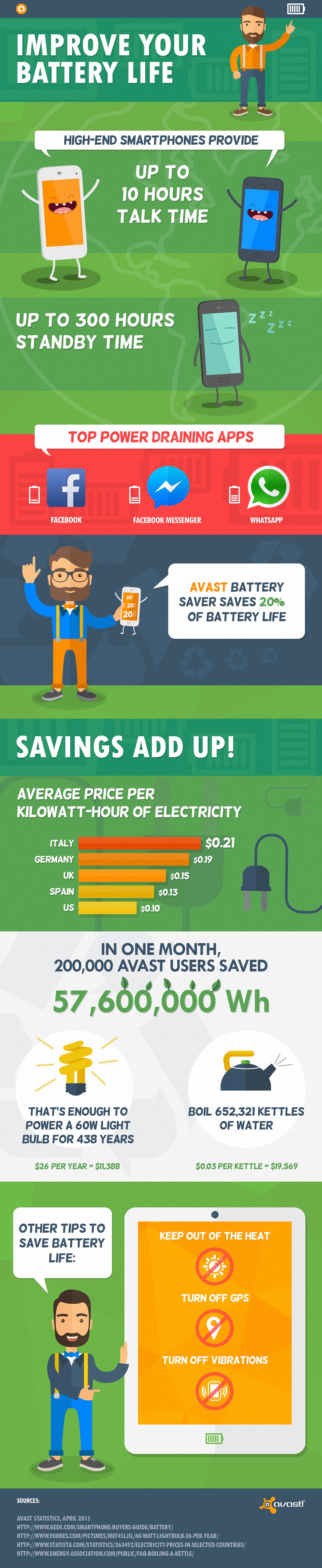
Either by mistake or ignorance, your company may be facing a hefty fine. You may ask yourself why? The answer, the daily emails your employees send to multiple clients massively. Do they send them using blind carbon copy (bcc)?
Inside the Spanish Organic Law on Personal Data Protection (LOPD) lies the exact explanation to why one of those emails sent to multiple clients without concealing their addresses may cost your company dear.
When managing a company’s client data base the responsibility is to protect them. This consists on not sharing or selling their information to others, people or companies. Here lays the problem with emails sent without bcc, every recipient can see who has received that same email which according to the LOPD is a serious offense.
It can turn out to be a very expensive mistake, if any of the recipients decided to report your company. The law provides fines between 40.000 and 300.000 euros, although normally sanctions end up being lower, depending on the number of affected clients or on how many times the mistake had been committed.
How to avoid it?
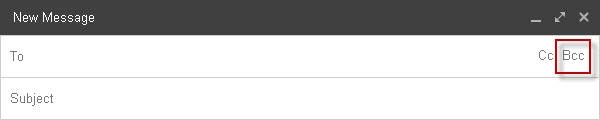
If you want to avoid making this mistakes is as simple as paying a bit of attention when sending mass emailing. Just add the recipients’ addresses through the Bcc button which is on the email top bar. This way the recipients’ addresses will be hidden and won’t be visible to those who had received that same email.
However, mass mailing without adding the recipients to the Bcc list is not the only problem a company might have while communicating, their presence in social networks can play an important role if used without caution.
We find Twitter is the most problematic one. If a company decided to follow unilaterally other users it may be breaking the Spanish Organic Law on Personal Data Protection and the Law of Services of the Information Society. You may wonder why? The reason is that a simple “follow” on Twitter is considered a commercial communication. And if the communication hadn’t been previously approved by the other user we will be looking at a case of spam.

In this case the solution is also simple, though it may be a bit painful for companies that will no longer be able to follow thousands of Twitter users. To do so and not be considered spam, companies must previously obtain the other users’ consent. In this case, the user following the company’s Twitter account may be understood as the necessary consent.
The whole company must be aware of the information its employees handle daily, everyone else’s information must be also protected, especially online. Something as simple as sending emails using bcc or choosing who our company follows on Twitter, may be enough to protect the information of others, and to avoid penalty.
The post Mass emails without BCC and other unsafe (and illegal) habits appeared first on MediaCenter Panda Security.