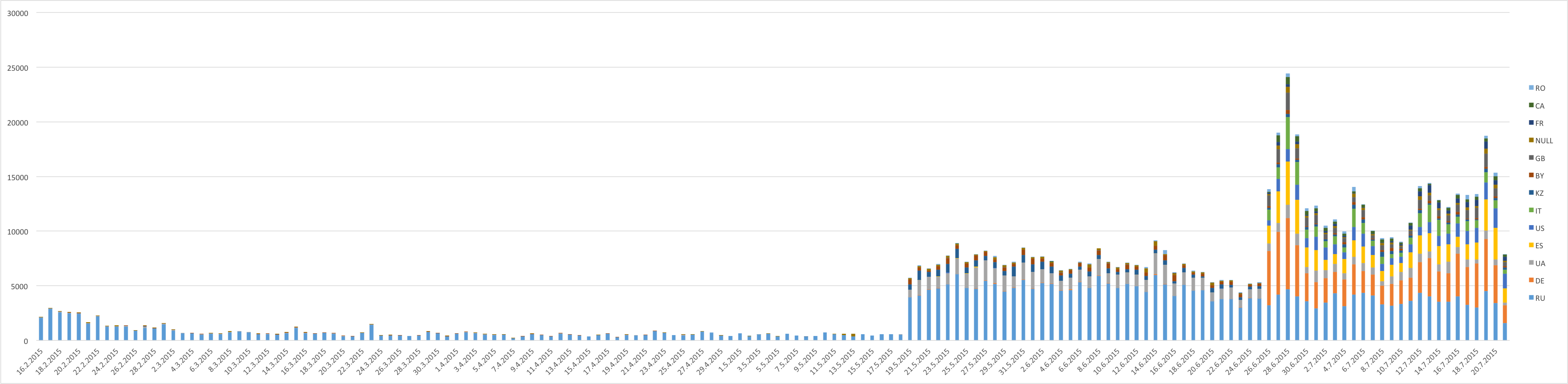
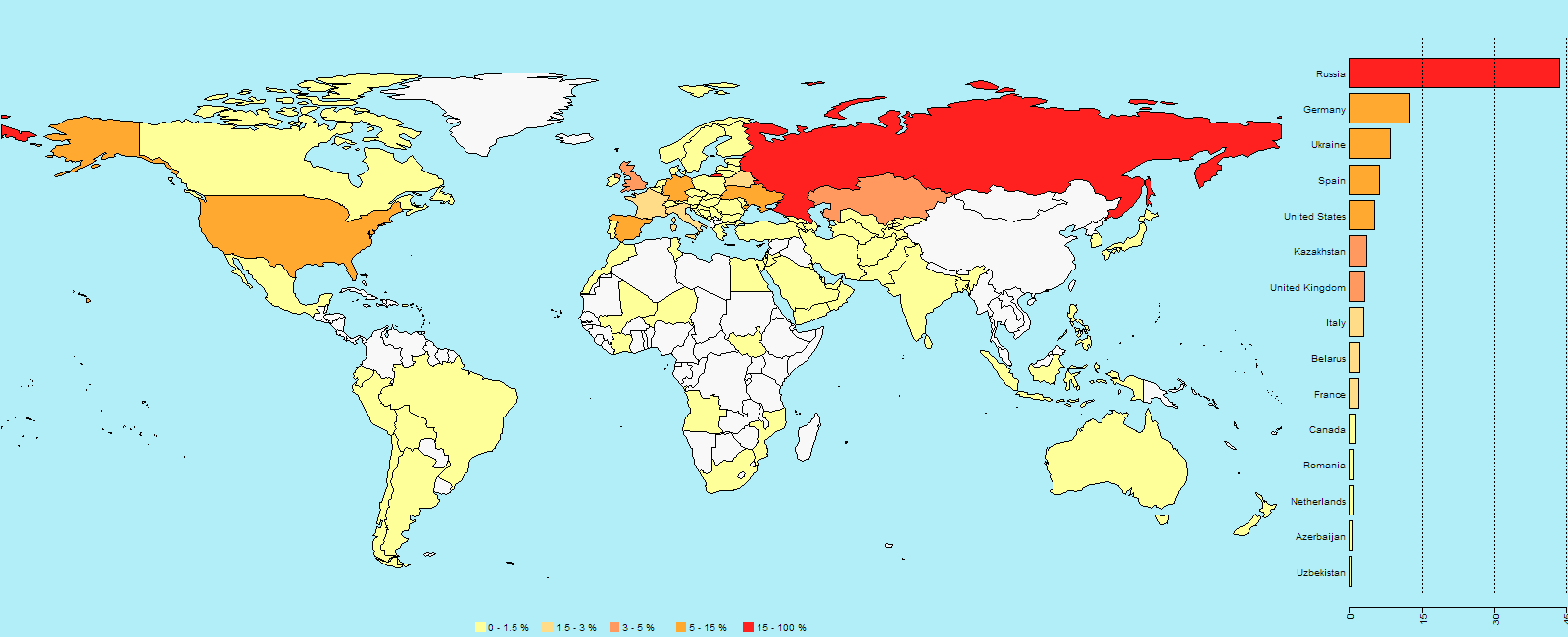
The major theme of this week’s Mr. Robot episode revolved around vulnerabilities. As much as we sometimes try to deny it, we all have weaknesses. Cybercriminals, being the intelligent people they are, unfortunately often use their smarts for evil. They know that it is human nature to have weaknesses since no one is perfect, and they exploit these weaknesses using a tactic called social engineering.
“People make the best exploits”
Whether directly or indirectly, humans and the software they create can be exploited via their weaknesses and vulnerabilities.
FSociety penetrates Steel Mountain, E Corp’s data security center, by exploiting human weaknesses. We first see this happen when Elliot exploits Bill Harper, a sales associate at Steel Mountain, by dismantling his self-worth and telling him that no one in his life really cares about him. Elliot then requests to speak to someone who matters and Bill, disheartened and humiliated, calls his supervisor.
To FSociety’s surprise, Trudy comes instead of Wendy, the supervisor they were expecting and were prepared to utilize to get into the next level of Steel Mountain. This slightly throws off FSociety for a few seconds, but they make a quick comeback by doing a bit of online research. They learn that Trudy’s weakness is her husband and use a Linux distribution called Kali to send her a text message appearing to be sent from her husband saying that he is in the hospital. I researched more about this tool and found out that when using it, it is possible for anyone to spoof SMS and make messages appear as if they are from a number the recipient knows — a trick that is also employed in fraud emails.
The interesting thing about this, though, is they say they do not have Trudy’s number, just her husband’s number. Yet, they type her number into the program to send the message.

via USA Network – Mr. Robot airs on USA Network Wednesdays at 10/9 central
How cybercriminals use social engineering
I sat down with my colleague, Mobile Malware Analyst Nikolaos Chrysaidos, to discuss social engineering and how it can affect people just like you and me.
Stefanie: First off, what is social engineering?
Nikolaos: Social engineering is a combination of psychological techniques that cybercriminals use to trick people into giving up sensitive information or performing certain actions, such as downloading malware. Social engineering essentially exploits people’s weaknesses and as Elliot said in this episode, “People make the best exploits”. No one is perfect and not everyone always has the best judgment, which makes social engineering such a successful tactic. Social engineering is not successful because people are not intelligent enough; it is successful because cybercriminals specifically target and exploit people’s weaknesses.
Stefanie: We saw FSociety socially engineer their way into Steel Mountain, but what are some examples of social engineering that target consumers?
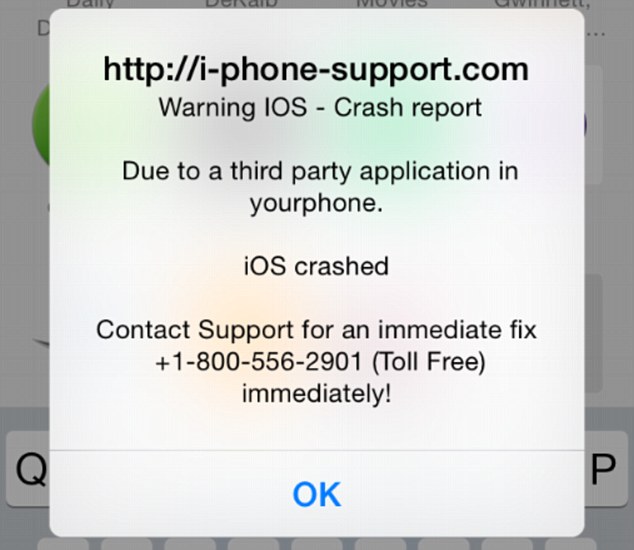
Nikolaos: Generally, social engineering tactics targeted at consumers either trick the victim into thinking they have won a prize, create fear by implying that something is wrong, or that the victim absolutely needs something. This can happen in the form of spearphishing attacks, in which hackers send messages pretending to be a trusted entity or friend of the victim. These messages include call-to-actions that, for example, prompt the victim to update their banking information, tell them there is an important attachment that they need to open which is really malware, or that they have won a prize and need to provide information to retrieve it. Social engineering can also use apps or advertising to trick people into doing certain things.
We often see in the mobile space that hackers scare victims into downloading fake antivirus apps by telling them that their device has a virus on it. In reality, the app steals private data from the device or holds files on the device for ransom, like Simplocker did.
Another way hackers trick users into downloading malware or into giving up personal information, is via malicious advertising. These ads often tell you, for example, that you do not have the latest version of Flash and should download it. They also tend to offer adult services, such as porn, live webcam chats or even mail-order brides. Once clicked on, these malicious ads can download malware onto your device.
Stefanie: Wow! Seems like people really need to be careful! What is some advice you can give to avoid becoming a victim of social engineering?
Nikolaos: Always double check emails from your bank to make sure they are legitimate. Banks should never email you asking to enter sensitive information via a link or send vital information as an email attachment. The same goes for emails from friends that contain links or attachments, if they seem fishy or off, call your friend and ask if the email really came from them before you take any actions.
As for mobile apps, make sure you only download apps from official app stores, like Google Play. If you do choose to download from a third-party store, make sure you have an antivirus solution installed and running. If an app asks you for permissions that don’t make sense to the app’s functions or if the app wants you to alter your security settings, then something is wrong and you should not download the app. You should be similarly cautious with advertisements offering you video players or adult content.
To maximize your protection against threats, you should have antivirus software installed on your PC and mobile device. In case you accidentally fall prey to a social engineering trick, antiviruses will catch malicious programs and websites before they can cause damage.
Never use Wikipedia as a trusted source
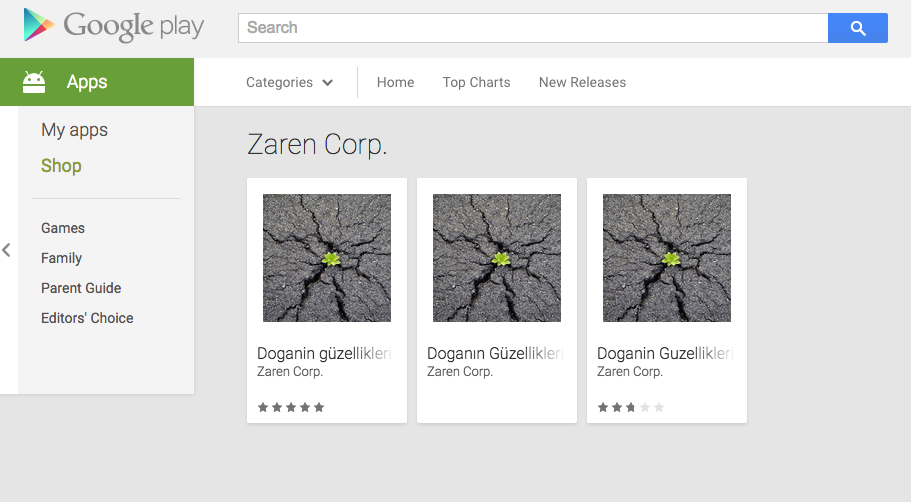
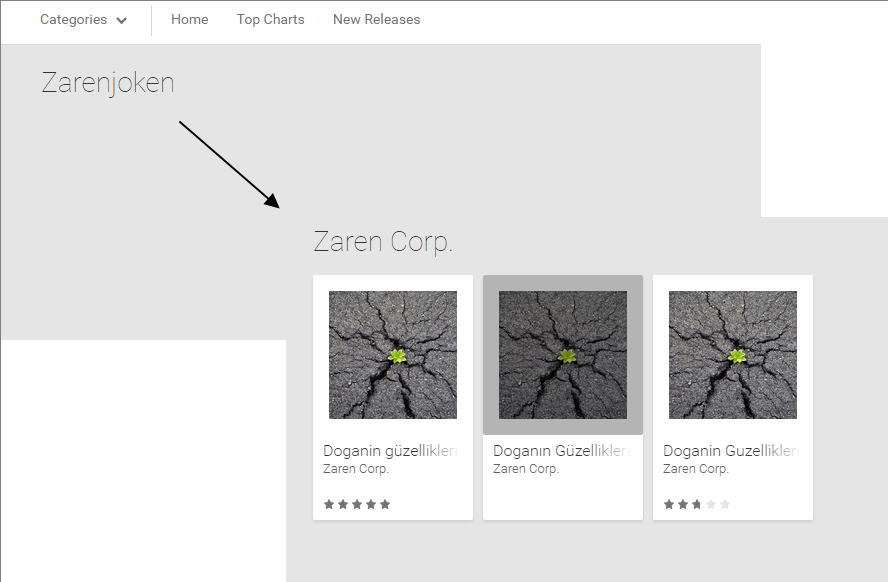
This was drilled into my head by my professors in college. Now, I am not saying Wikipedia is bad — there is a sea full of valuable information on Wikipedia, but the site can be edited by nearly anyone. Apparently people even try to delete entire pages –ahem, Donald Trump. You can’t always trust what you read on Wikipedia, despite the editors’ best efforts to keep the pages factual. FSociety, of course, knows how easily a Wikipedia page can be manipulated and abuses Mobley’s extensive Wikipedia editing history to edit Sam Sepiol’s Wiki page. Elliot tells Bill Harper, a sales associate at Steel Mountain, that he is Sam Sepiol, a young billionaire who co-founded tech startup Bleetz and that Bill should look him up. Bill searches for Sam Sepiol and reads his Wikipedia page, where Elliot’s picture is uploaded and thus Elliot is granted a tour of Steel Mountain.
Be aware of how much you share with the Internet
This week’s Ashley Madison data breach is, hopefully, a major wake up call for a lot of people. This breach should teach everyone that the minute you put your personal information online, it’sout of your hands and could be up for grabs. In this week’s episode, Fernando realizes this when he learns he was busted, because he put his business on social media. He did use codes to cipher his communications, but apparently the codes he used were too obvious and easily crackable. Clearly, Fernando should be looking to hire a new adviser and fire his “aspirational little brother”.
You should use caution when uploading your business onto social media. FSociety discovered the weaknesses of multiple people just by Google searching them and checking out their blogs, Twitter and Facebook profiles. This can be done by anyone, so make sure to examine your social media accounts’ settings and set everything to private. Also, be sure to think twice before you upload content or sign up for services online. Think about how these choices may affect you in the future, who can see them and if you really want the world to see it.
What did you think of this week’s Mr. Robot episode? Make sure you follow Avast on Twitter and check out our Hack Chat channel on YouTube to keep up with future Mr. Robot discussions!

 We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to Avast Hack Chat on YouTube to see all of our videos.
We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to Avast Hack Chat on YouTube to see all of our videos.


![]() Now for some good news. Avast Browser Cleanup removes those unwanted browser add-ons. You know the ones. They take up space on your browser, change your search engine, and even your home page. Avast Browser Cleanup has removed more than 650 million unwanted add-ons and extensions from our users’ browsers in the past two years. You can get it for free in all Avast products or download it as a standalone version.
Now for some good news. Avast Browser Cleanup removes those unwanted browser add-ons. You know the ones. They take up space on your browser, change your search engine, and even your home page. Avast Browser Cleanup has removed more than 650 million unwanted add-ons and extensions from our users’ browsers in the past two years. You can get it for free in all Avast products or download it as a standalone version.
 BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of Remotium, a leader in virtual enterprise mobility. Their technology provides enterprises with secure access to business-critical applications from anywhere and from any mobile or desktop device.
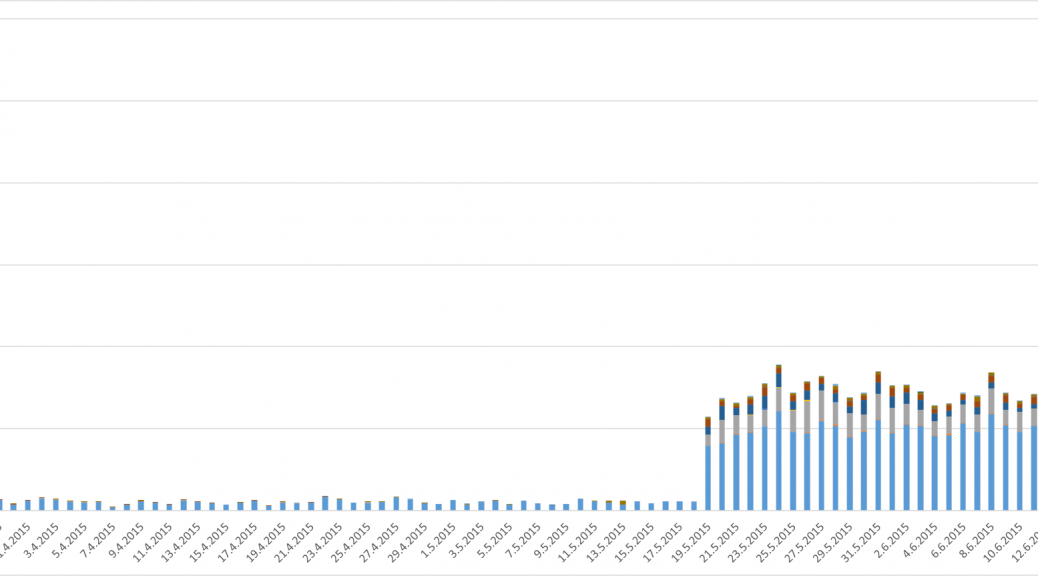
BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of Remotium, a leader in virtual enterprise mobility. Their technology provides enterprises with secure access to business-critical applications from anywhere and from any mobile or desktop device. Students wanting to know how they did on their AP test installed Avast SecureLine VPN so they could see the scores right away. We have extended the 7-day free trial for an additional 30 days for all these clever kids. We hope you will keep your devices safe while using unsecured Wi-Fi around your new college campus this fall.
Students wanting to know how they did on their AP test installed Avast SecureLine VPN so they could see the scores right away. We have extended the 7-day free trial for an additional 30 days for all these clever kids. We hope you will keep your devices safe while using unsecured Wi-Fi around your new college campus this fall.![]()