A recently identified trojan porn clicker is still infecting apps on Google Play.
The post Porn clicker keeps infecting apps on Google Play appeared first on We Live Security.
![]()
A recently identified trojan porn clicker is still infecting apps on Google Play.
The post Porn clicker keeps infecting apps on Google Play appeared first on We Live Security.
![]()
Malware Writers Can’t Keep Their Hands Off Porn
In April, we reported on a porn clicker app that slipped into Google Play posing as the popular Dubsmash app. It seems that this malware has mutated and once again had a short-lived career on Google Play, this time hidden in various “gaming” apps.
For your viewing pleasure
The original form of this porn clicker ran completely hidden in the background, meaning victims did not even notice that anything was happening. This time, however, the authors made the porn a bit more visible to their victims.
The new mutation appeared on Google Play on July 14th and was included in five games, each of which was downloaded by 5,000-10,000 users. Fortunately, Google reacted quickly and has already taken down the games from the Play Store.
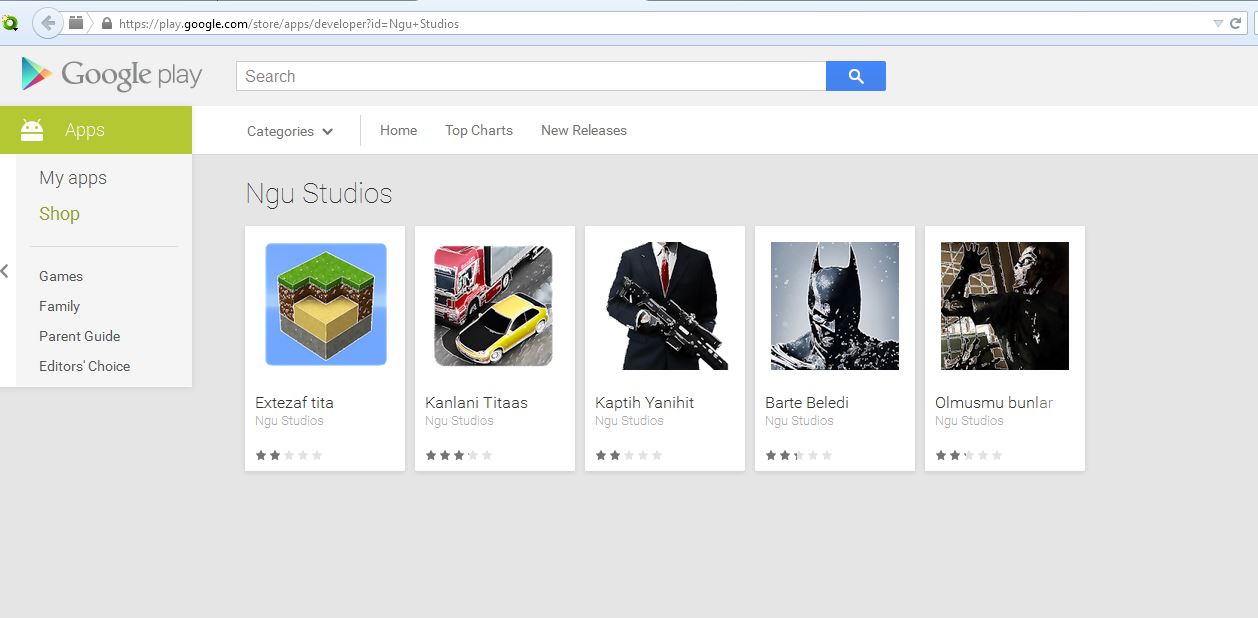
The selection of “gaming” apps affected by Clicker-AR malware on the Google Play Store.
Once the app was downloaded, it did not really seem to do anything significant when opened by the user. However, once the unsuspecting victim opened his/her browser or other apps, the app began to run in the background and redirect the user to porn sites. Users may not have necessarily understood where these porn redirects were coming from, since it was only possible to stop them from happening once the app was killed.
May I?
This new mutation, which Avast detects as Clicker-AR, requested one important permission that played a vital role in helping the app do its job. The app requested permission to “draw over other apps”, meaning it could interfere with the interface of any application or change what victims saw in other applications. This helped the malware put its adult content in the forefront of users’ screens.
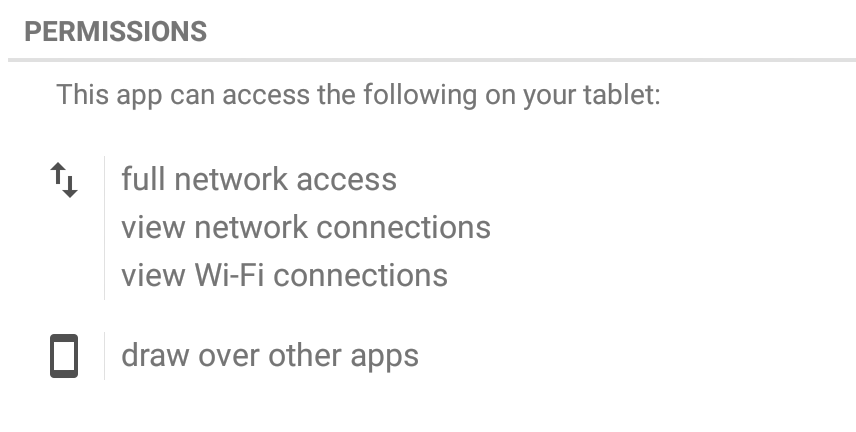
Let’s play “Clue”
We did not immediately realize that the group behind Clicker-AR was comprised of the same folks from Turkey behind the fake Dubsmash app. Then, our colleague Nikolaos Chrysaidos dug a bit deeper and was able to connect some clues to figure out who was behind this piece of malware. He noticed that the fake Dubsmash app and the new apps shared the same decryption base64 code for the porn links. We then noticed that they shared the same function with the same name “bilgiVer”, which means “give information” in Turkish. Finally, the old and new apps used the same DNS from Turkey. Not only did they have a server in Turkey, but they also now made use of an additional server in the U.S. – it seems they made some investments using their financial gain from April!
Bye bye, porn!
As mentioned above, these malicious apps have already been removed from Google Play and Avast detects the malware as Clicker-AR. The following games are infected with Clicker-AR: Extezaf tita, Kanlani Titaas, Kapith Yanihit, Barte Beledi, and Olmusmi bunlar. If you have any of these apps installed on your device, we suggest you remove them (unless you, um, enjoy them) and make sure you have an antivirus app, like Avast Mobile Security, installed to protect yourself from mobile malware.
Follow Avast on Twitter where we keep you updated on cybersecurity news every day.
![]()
Malware detected on Android
Over time, we’ve noticed the presence of some fairly heated user debates disputing the necessity of security or antivirus apps for Android devices. This could have been sparked by our recent post which argues that you can’t always rely on the security of Google Play or because of the myth that antivirus companies create viruses to sell more software.
Certain security gurus claim that if users stick to downloading and purchasing apps using only the Google Play Store, nothing bad will happen to their devices. However, we found that this line of thinking is not 100% correct, as was demonstrated through the discovery of a rogue Dubsmash app or in the infamous case of apps on Google Play posing as games and infecting millions of users with adware. Despite these findings, there are some users who still feel that they’re safe whenever using Google Play. This feeling of false security could have negative consequences; for example, when your data or financial information is stolen or when you have to resort to resetting your device in order to cleanse it of malware.
So, we know we can’t rely on the Google Play Store all the time, but are third-party stores more secure? Of course not. In this case, how is it still possible that it’s not a problem to use third-party stores? First of all, it’s necessary to point out that there are certain legitimate and clean third-party stores, such as Amazon and FDroid. At the same time, there are tons of shady stores and even more black market .apk files promising to deliver you the latest features of a cracked app.
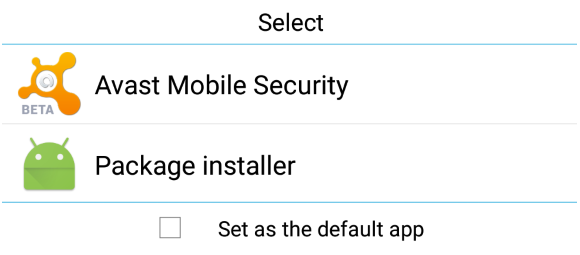
Android default apk handler
Besides the well known (and default) security options of Android, there is another useful feature that remains more or less unknown by average users: the default app feature. When Android (and also Windows) is about to open a file, it looks into its database to determine which application should be used and launches it. If you set Avast Mobile Security to be run at this preliminary stage of an app’s installation, it will scan the .apk file before it is opened and the installation process has begun. If any mistake or bug is detected, the process is halted and you’ll be given the option to uninstall the app.
If you have already installed Avast in your Android smartphone or tablet and this option is no longer shown, the easiest option will be to uninstall it, reboot and install it again. When the dialog pops up, choose Avast as your default handler for .apk files. As mobile malware reached the one million Android sample mark last year, the Avast database continues to grow exponentially. Avast Mobile Security also performs very well with new and unknown malware, as independent tests show us.
You can be safer and have a complete peace of mind while using third-party stores if you keep Avast Mobile Security running as your default installation package app. Download Avast Mobile Security for free on the Google Play Store.
![]()
Over 500,000 Android users targeted by phishing apps harvesting their Facebook credentials. ESET detects these trojans as Android/Spy.Feabme.A.
The post Apps on Google Play Steal Facebook Credentials appeared first on We Live Security.
![]()
We are happy to announce that AVG’s Tablet AntiVirus Security FREE has been voted as the best tablet security app in a Czech and Slovak app award.
The awards, organized by Czech company Tuesday Business Network, are designed to celebrate the very best of Czech and Slovak app development industry.
A shortlist of products was drawn up by public nominations and an expert panel selected the winners.
AVG Tablet AntiVirus Security FREE has many powerful protection and anti-theft features that can help you keep your device safe as well as protecting the data stored on it.
These include:
Download AVG Tablet AntiVirus Security FREE from Google Play today.
![]()
![]()
Porn clickers pretending to be the the Dubsmash application have found their way back onto Google Play, a month after being removed.
The post ESET uncovers another porn clicker on Google Play appeared first on We Live Security.
![]()
ESET has discovered over 30 scareware apps available for download from the Google Play store. The apps have been installed by more than 600,000 Android users.
The post Scareware: Fake Minecraft apps Scare Hundreds of Thousands on Google Play appeared first on We Live Security.
![]()
Everyone from celebrities like Lena Dunham to Hugh Jackman are using the (currently) seventh most popular app available on Google Play: Dubsmash. Dubsmash is an app with more than 10 million Google Play installations that lets users choose a sound, record a video to go along with the sound and send their dub to their friends or social media channels. Dubsmash is not only widely popular amongst teens and celebs, but the app has also caught the attention of malware authors.
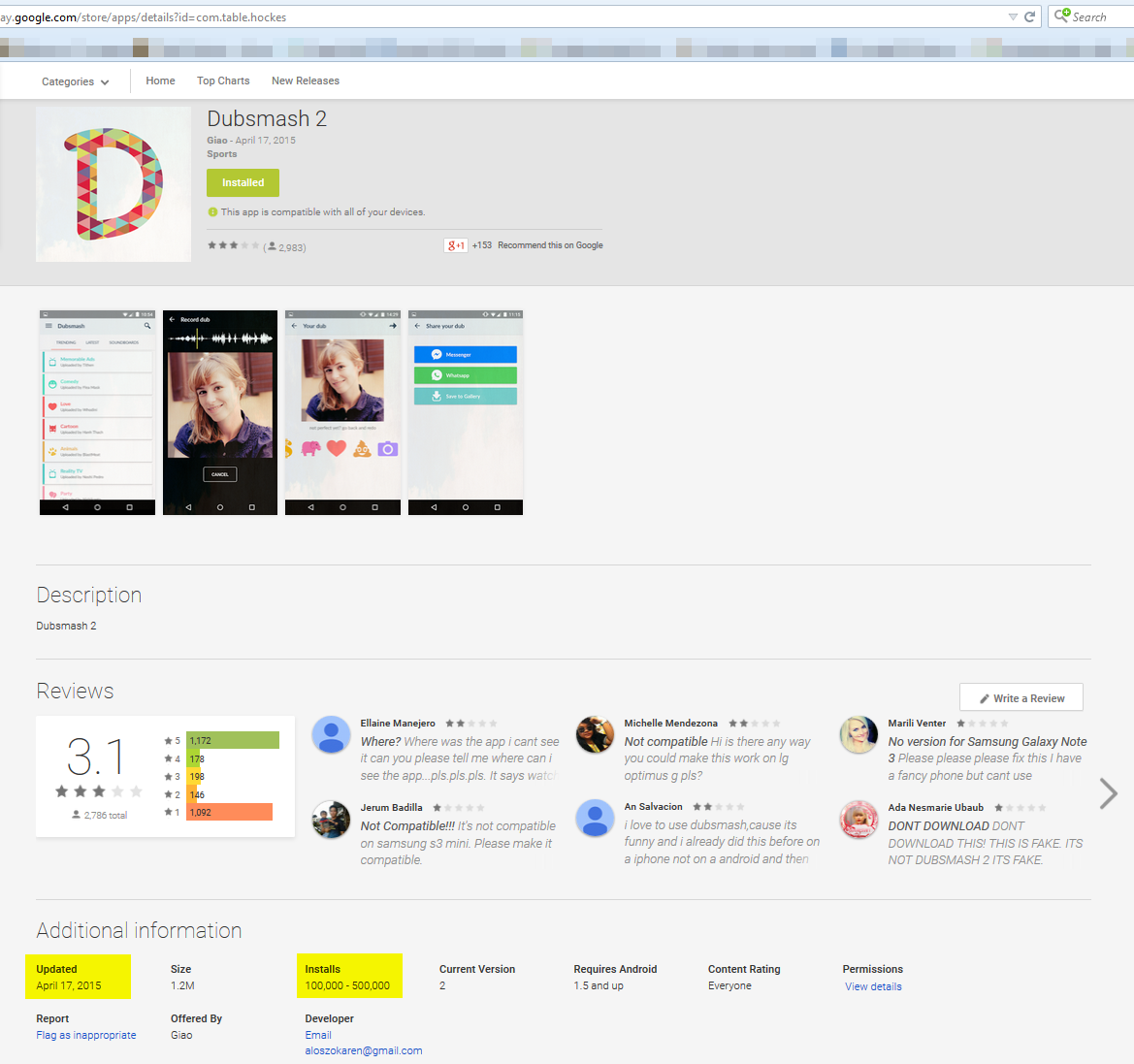
Google removed the rouge app after Avast notified them
Avast recently discovered “Dubsmash 2” (with the package name “com.table.hockes”) on Google Play – and no, it was not the bigger and better version of the original app. The app is a so called “porn clicker” and was installed 100,000-500,000 times from the Google Play Store. We contacted Google when we discovered the rogue app and it was removed from the Play Store shortly thereafter. Once the app was installed there was no evidence of an app named “Dubsmash 2” on the user’s device, instead the app installed an app icon named “Setting IS”. This is a common trick malware authors use to make it harder for the user to figure out which app is causing problems. This should also be the user’s first clue that something shady is going on. The “Settings IS” icon looked very similar to the actual Android Settings icon (see screenshot below).
The app’s mischievous activities could be triggered by two actions. The first possible way was by simply launching the “Settings IS” app and the second, which occurred only if the user had not yet launched the app, was via the BroadcastReceiver component within the app. BroadcastReceiver observed the device’s Internet connectivity and if the BroadcastReceiver noticed the device was connected to the Internet, the app’s true functions would be triggered.
If the “Settings IS” app was opened by the user, the Google Play Store would launch to the actual “Dubsmash” app download page.

The rogue icon looked very similar to the Android Settings icon
Once activated, the app sent an HTTP GET request to an encrypted URL. If the request returned a string containing the character “1” two services would begin to work: MyService and Streaming. Using this method the author could also effectively turn off the start of the services remotely.
The MyService service began by deleting the “Settings IS” app icon from the device’s main menu and scheduled a task to run every 60 seconds in the background of the device, meaning the user never realized that anything was happening. The task would download a list of links to various porn sites from an encrypted URL stored within the app, along with JavaScript execution code. One of the porn links from the list would be launched in the browser and after ten seconds, the JavaScript code (also downloaded from an encrypted URL) was executed, clicking further links within the porn site. In the case seen in the picture below, the function opened a random link from the web page.
The developer probably made money on pay-per-click ads.
The second service, the Streaming service, was fairly similar in structure to the MyService component in that it also scheduled a task to run every 60 seconds. The main difference to MyService, is that users could notice the Service tasks did not run secretly in the background. The task would check for changes in the device’s IP address or date. If either of them had changed, a video would launch in the device’s YouTube app. The YouTube app needed to be installed on the device for this to function properly. The video address was also obtained from an encrypted URL.
The encrypted URLs used by the app
After decrypting and further examining the URLs and the video from YouTube, the Avast Virus Lab came to the conclusion that the malware most likely originated from Turkey. The developer’s name listed on Google Play and YouTube hint to this.
We suspect the app developer used the porn clicker method for financial gain. Through clicks on multiple ads within the porn sites, the app developer probably received pay-per-click earnings from advertisers who thought he was displaying their ads on websites for people to actually see.
Despite being undesirable, but basically harmless to the user and less sophisticated than other malware families such as Fobus or Simplocker, this app shows that although there are safeguards in place, undesirable apps that fool users can still slip into the Google Play store.
If you installed Dubsmash 2 (package name “com.table.hockes”), you can delete the app by going into Settings -> Apps -> find “Settings IS” and then uninstall the app.
The Avast Mobile Security application detects this threat as Android:Clicker. SHA-256 hash: de98363968182c27879aa6bdd9a499e30c6beffcc10371c90af2edc32350fac4
Thank you Nikolaos Chrysaidos for your help with the analysis ![]()
Our mobile phones are fantastic little devices — these days, they’re as powerful and can accomplish nearly all the things a regular computer can. While this is convenient for us, it also gives cybercrooks a relatively easy in-road to your private data and financial information. As 2015 rolls along, consumers continue to become more aware of mobile security options available to them, since they will increasingly use mobile apps that contain sensitive banking, financial, and personal health information.
Last year, more than 1 billion Android devices were shipped out to customers around the world. With Android winning the majority of the smartphone market, it offers a tempting target to malware authors. The average user is not especially concerned about being infected with a virus on their phone or tablet, but unfortunately, mobile malware is more than just a myth. Avast currently has more than one million samples of mobile malware in its database, with 2,850 new mobile threats being created every day by hackers.
Even if you think your chances of being infected with malware are low, we suggest that you go ahead and install a good mobile antivirus software. The great thing about Avast Mobile Security is that it’s free, so your investment is minimal – just a few minutes of setup and you’re ready to go.
Avast Mobile Security includes antivirus protection which scans your apps to see what they are doing, and a Web shield that scans URLs for malware or phishing. Malicious apps allow malware to enter your phone, so it’s good to have Avast on your side to detect when a bad one slips by on Google Play or another app store.

When taking a look at Avast Mobile Security’s features and capabilities, it’s easy to see why it’s a top-rated mobile security app.
AV-TEST All-Stars
Avast Mobile Security did not commit any mistakes when tested with 1,932 legitimate apps from the Google Play Store and 981 legitimate apps from third party app stores. In addition, all this protection, according to AV-TEST, did not “impact the battery life”, or “slow down the device during normal usage”, and “does not generate too much traffic”.
To compare the choices of mobile antivirus software, you can look at the January 2015 “Mobile Security Test” conducted by the independent labs at AV-TEST. They looked at 31 popular Android security apps. Avast Mobile Security tops the list because it detected 100% of malicious apps without any impact on the battery life or slowing down of the device.
AMS Referral Program
In the latest update of Avast Mobile Security, we added a referral program, so you can recommend Avast Mobile Security to your friends and family. Not only can you recommend the best mobile security app available on Google Play, but you will be rewarded for doing so; you can earn up to three months of Avast Mobile Premium for free!
Here is how it works: For every five friends you send an SMS to recommending Avast, you get one free month of Avast Mobile Premium. Cool, huh?
There you have it — we’re huge fans of Avast Mobile Security, and we think you will be too. Download Avast Mobile Security for free on Google Play.
Google is taking additional security measures to shut out malware from its app store by introducing a human screening process.
The post Google Play security tightened with human screening process appeared first on We Live Security.