Google has taken quite a bit of heat in recent weeks for its decision not to patch a vulnerability in the WebView component of Android in older versions, leaving hundreds of millions of users exposed to potential attacks. Now, a Google engineer is explaining the company’s reasoning, saying that patching older versions of the OS […]
Tag Archives: google
Unpatched Apple Vulnerabilities Latest Google Project Zero Disclosures
Three unpatched Apple OS X vulnerabilities were disclosed by Google’s Project Zero research team. Project Zero discloses if a bug is not patched within 90 days of reporting it to the affected vendor.
Chrome 40 Patches 62 Security Vulnerabilities, Pays Bounties Aplenty
Google released version 40 of the Chrome browser, patching 62 vulnerabilities, including close to two-dozen critical memory corruption flaws.
Threatpost News Wrap, January 16, 2015
Dennis Fisher and Mike Mimoso discuss the security news of the past week, including the proposed changes to the CFAA, David Cameron’s encryption comments, the NSA’s quasi-apology regarding Dual EC and the Microsoft-Google disclosure feud.
Round 2: Google Deadline Closes on Pair of Microsoft Vulnerabilities
Google Project Zero has disclosed a pair of unpatched Windows vulnerabilities after the expiration of its 90-day deadline. Microsoft said it will patch one bug in February, and both sides agree the second does not merit a security bulletin.
Google to remove support for old versions of Android WebView
Earlier this week, Google announced that they will no longer release patches for WebView versions JellyBean and older.
WebView is a core Android component which is used to display web pages on mobile devices and has been a target for exploitation from hackers. Google’s decision to stop patching old versions of WebView could potentially leave millions of users at risk.
Here is a video of Elad Shapira, one of our mobile security experts, executing an exploit on WebView.
How many people are affected?
While it’s quite common for companies to pull support for legacy products, Android is a special case as there are many devices still running old versions of the operating system.
In fact, the latest mass-market version of Android (4.4, KitKat)- only makes up 40% of the overall Android market meaning that up to 60% of all Android devices might receive no further WebView patches.
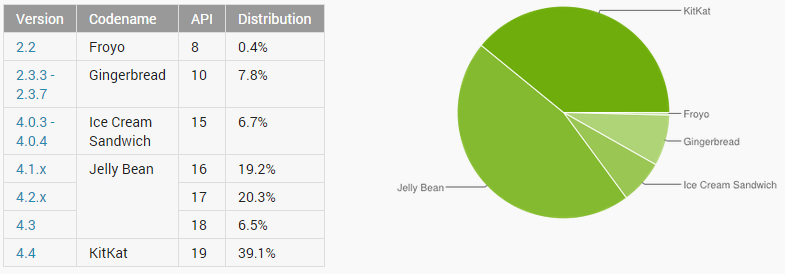
Image courtesy of securitystreet
Why does this matter?
Support in the form of patches and security fixes are one of the most important ways to keep our devices safe. New vulnerabilities in operating systems and apps are found all the time and can cause privacy and security concerns for end users.
Software developers use security patches to protect fix these vulnerabilities and protect users from harm.
Having said that, Android is by its very nature open source, so there is always the possibility for newly discovered vulnerabilities to be patched by the Android community but that is a Band-Aid fix at best.
What can be done to help you keep safe?
The most straightforward step to help stay safe (and the one Google is likely hoping we all adopt) is to upgrade to the latest version of Android. For some however, this would prove prohibitively expensive and would require the purchase of a new device.
Those with recent devices should be able to upgrade to KitKat without much problem and people with brand new devices should be on version 5, Lollipop.
As a complementary measure, having a fully updated security app running on your device will help keep you safe from most scams and malware.
Google Passes on Older Android Patches; 930 Million Devices Vulnerable
Google has decided that it will no longer provide Webview patches for Android systems running Jelly Bean 4.3, or older, putting the onus on OEMs and the open source security community to provide patches to users.
Certificate Transparency Moves Forward With First Independent Log
The Certificate Transparency scheme proposed by Google engineers has taken a couple of significant steps forward recently, with the approval of the first independent certificate log and the passing of a deadline for all extended validation certificates to be CT-compliant or lose the green indicator in Google Chrome. On Jan. 1, a CT log operated by […]
Google Engineers Critical of Aviator Browser Security
Google security engineers have criticized the security and privacy of WhiteHat Security’s Aviator browser, after finding a remote code execution vulnerability within hours of Aviator’s release as open source.
Exploits Circulating for Remote Code Execution Flaws in NTP Protocol
Researchers at Google have uncovered several serious vulnerabilities in the Network Time Protocol and experts warn that there are exploits publicly available for some of the bugs. The vulnerabilities are present in all versions of NTP prior to 4.2.8 and include several buffer overflows that are remotely exploitable. The NTP is a protocol that’s used […]