Here are the exploit kits to watch for over the next three to six months.
Tag Archives: Locky
New Cerber Variant Leverages Tor2Web Proxies, Google Redirects
Researchers have discovered that criminals behind the latest Cerber ransomware variant are leveraging Google redirects and Tor2Web proxies in a new and novel way to evade detection.
Locky Targets OPM Breach Victims
A phishing campaign is targeting some of the 22 million victims of the massive United States Office of Personnel Management breaches of 2014 and 2015.
Inside the RIG Exploit Kit
In a deep analysis of RIG, Cisco Talos team outlined the way the exploit kit combines different web technologies such as DoSWF, JavaScript, Flash and VBscript to obfuscate attacks.
Locky ransomware goes Nordic with Odin…

… but don’t miss the forest for the trees! The latest Locky variant appropriates Nordic mythology with a vacuum-cleaner approach to encrypting victims’ files.
The post Locky ransomware goes Nordic with Odin… appeared first on Avira Blog.
Locky takes the wheel again

Ransomware returns to its earlier hands-on approach.
The post Locky takes the wheel again appeared first on Avira Blog.
Locky ransomware goes on Autopilot

Locky ransomware goes on Stealth Autopilot – latest ransomware configuration encrypts files without communication or directions from Evil Overlords
The post Locky ransomware goes on Autopilot appeared first on Avira Blog.
Know the tricks of the new Locky

In this new Tales from Ransomwhere we discovered the tricks of one of the most infamous families in the landscape of the ransomware: Locky .
Recently (our colleagues from Avira reported it in July) they added a new feature, it includes an offline mode so it is able to encrypt files when the connection to the server is not available. The weak point is that this key is the same for every computer which files are encrypted, that’s why this is just something that is performed when for some reason the C&C server is unavailable.
On top of this now they have changed the way they infect computers. Usually these attacks rely on a small downloader Trojan who downloads and executes the ransomware. For example, when the attack comes from a javascript file, this usually downloads a small executable which only function is to get the ransomware and execute it. As I have explained in previous articles, cybercriminals are all the time making small changes trying to avoid detection from security solutions.
Distribution of new attack
In this case the attack is being distributed through email, we have seen a number of them with a zip file that has a javascript file inside named “utility_bills_copies <random characters>.js”. However there are different versions using different subjects and file types, for example this one:
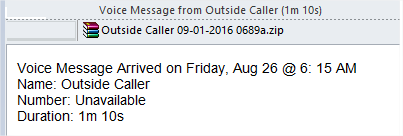
Which inside has the following file:
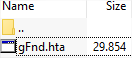
They have skipped the downloader Trojan part and the script gets the Locky variant in DLL format (with the downloader in most cases the downloaded file was an EXE), which is executed using Windows rundll32.exe. The first sighting of this was on August 22nd, and so far they keep using the same strategy. As you can see they are launching one wave per week:
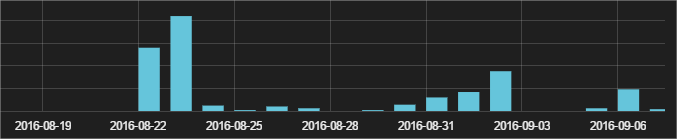
The most severely affected territories
We have seen just a few hundred infection attempts mainly in North and South America and Europe, although there are some in Africa and Asia too. In case they get a good return of investment we’ll probably see an increase in the next weeks. Here you can find a few hashes of this Locky variant:
The post Know the tricks of the new Locky appeared first on Panda Security Mediacenter.
Locky goes offline (by design)
New Locky variant can encrypt files without directions from the ransomware’s CnC. That makes it tougher to block. But, this new variant may have the weakness that once someone has paid the ransom for their private key ID – it should be possible to reuse the same key for other victims with the same public key.
The post Locky goes offline (by design) appeared first on Avira Blog.
Locky is back with a twist of COM
Locky is continuing to evolve after its return to the marketplace last week. The new June 28 variant uses Windows COM objects to erase old copies, resulting in more difficult behavior-based detection by security programs.
The post Locky is back with a twist of COM appeared first on Avira Blog.



