 PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
Cyber-crime does not stop
Cyber-criminals continue attacking without giving sensitive infrastructures the chance to take a break, as seen in the attack suffered by 21st Century Holdings, a clinic specialized in cancer treatments with headquarters in Florida. The clinic had to alert their 2.2 million patients and workers that their personal data might have been compromised.
The Rosen Hotels & Resort chain has been the victim of an attack that occurred between September 2014 and February 2016. The company alerted their clients who may have used a credit or debit card in their establishments over this time period that their data could have been stolen by the attackers.
Even the world’s most powerful governments haven’t been spared, such as the United States, where the Department of Defense has presented a rewards program called “Hack the Pentagon” in which rewards are offered to hackers who find security holes in the Pentagon’s web pages, applications and networks.
Smartphones are another easy target for cyber-criminals. SNAP is the name of a vulnerability that affects the LG G3 phones. The problem is due to an error in the implementation of LG notifications called Smart Notice, which allows JavaScript to be executed.
The growing sector, the Internet of Things, is also affected by this year’s criminal activity. In this area, we can see how something as innocent as a doorbell can be attacked. Manufacturers are becoming more aware of their product’s safety, in fact, General Motors just launched a new rewards program for hackers who are able to find vulnerabilities in their vehicles.
Q1 in numbers
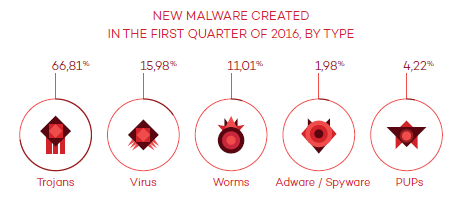
The PandaLabs study shows that Trojans continue to be in the lead of all malware samples. Out all malware samples created in 2016, Trojans are number one with 66.81% of the total (an increase compared to last year), followed by viruses (15.98%), worms (11.01%), PUPs (4.22%) and aware/Spyware (1.98%):
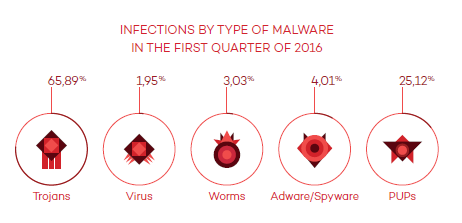
When we analyze the infections caused by malware worldwide, we find Trojans in the lead again. This is normal if we take into account the rise in ransomware infections, including the rise of Trojans, which is also one of the most popular attacks cyber-criminals use because it allows them to obtain money easily and securely. There are more and more companies whose networks are falling victim to these cyber-criminals and who are paying millions of euros to rescue their stolen information:
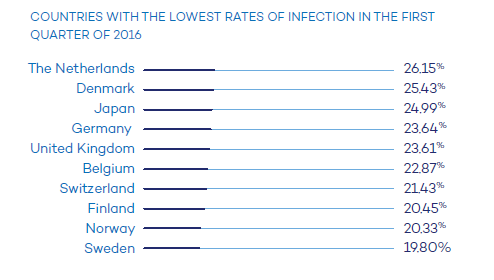
According to PandaLabs, Asia and Latin America are the most affected regions
In this study we can find a table showing the countries with the highest and lowest infection rates in Q1 of 2016: Asia and Latin America (China leads the ranking with 51.35% of infections) are the most affected countries; while the Scandinavian countries have the lowest infection rates with (Sweden at the lowest at 19.80%).

 If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
The post PandaLabs identifies 227,000 malware samples per day in the first quarter of 2016 appeared first on Panda Security Mediacenter.
![]()








