A day after researchers detailed a technique that attackers are using to upload malicious firmware images to Cisco routers, academic researchers say they have scanned the entire IPv4 address space and discovered a total of 79 likely compromised routers. The researchers at the University of Michigan used their Zmap tool, which can scan the Internet in about […]
Tag Archives: Malware
CoreBot Adds New Capabilities, Transitions to Banking Trojan
As many researchers expected it would, CoreBot, the credential-stealing malware that first surfaced last month, has added a bevy of new capabilities and reinvented itself as a robust banking Trojan.
Attackers Replacing Firmware on Cisco Routers
Cisco routers are built into the fabric of the Internet and enterprise networks, a fact that makes them highly attractive targets for attackers. Researchers at FireEye have come across attacks recently in which hackers have been modifying the firmware of Cisco routers and using that foothold to maintain persistence on the victim’s network. Such a technique […]
PandaLabs detected more than 21 million new threats during the second quarter of 2015, an increase of 43% compared to the same period in 2014
PandaLabs, the laboratory set up by Panda Security, has published its quarterly report where it shows the latest statistics on malware and cyberattacks that have been at the forefront of this year’s second quarter. The creation of new malware samples have broken records in this timeframe.
The world of cybersecurity doesn’t take a moment’s rest and cybercriminals are a constant threat. The number of malware examples continues increasing and shows no sign of stopping, so here we’ll share with you the most important details of this report.
Malware can’t be contained
The creation of new types of malware continues to grow, reaching an average of 230,000 new examples every day during the second quarter of 2015. This represents an increase of 2% compared to the first quarter of the year. The figure is alarming and more than 21 million new threats have been generated during these three months. Compared to the same period last year, where there were 160,000 samples, this shows an increase of 43%.
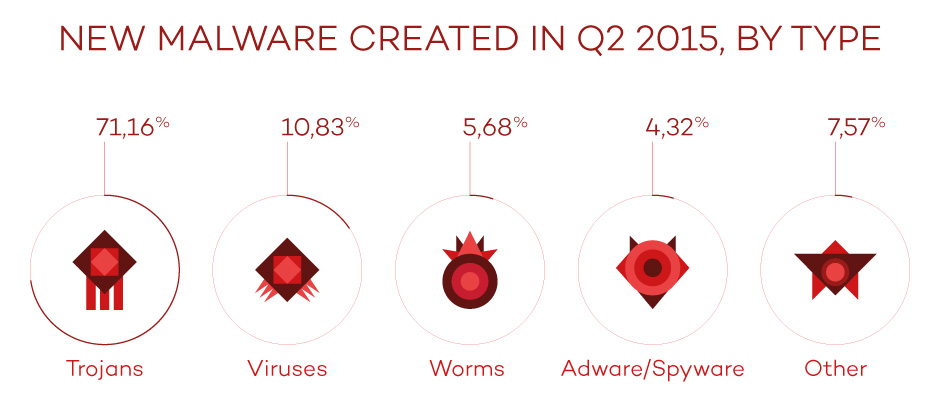
Of the new malware created this quarter, the most popular has been the Trojan, which accounted for 71.16%. This was followed by traditional viruses which made up 10.83%.
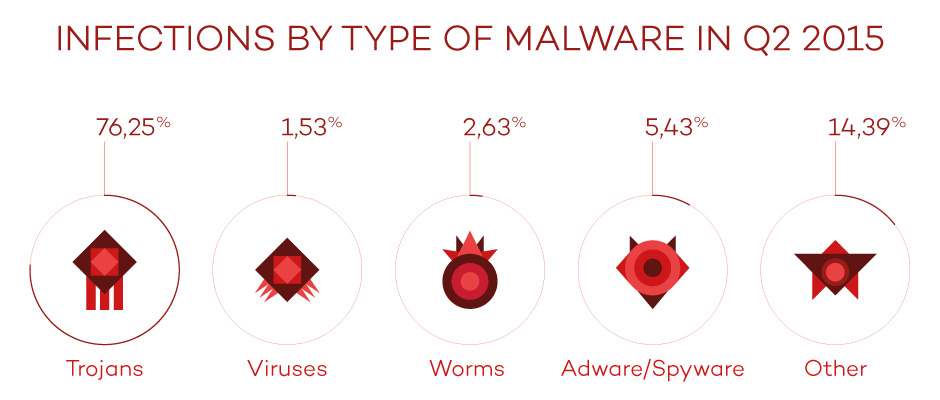
If we analyze the infection by type of malware we can see that, logically, the figures are the same as those for newly created malware, except for the category marked others, whose percentage is higher by a significant margin. Trojans continue to be the main cause of infection, with 76.25% of all users infected by them.
Asia and Latin America show a higher rate of infection
China, once again, sits at the top of the chart with 47.53% of all computers infected. It is followed by Peru (43.11%) and Turkey (41.97%), respectively.
On the other hand, the countries with the lowest infection rates were Sweden (21.57%), Norway (22.22%), and Japan (23.57%). It is important to highlight Europe as the region with the lowest rate of infection worldwide, with nine countries on this ranking. As regards Spain, the rate of infection was (36.37%), which places it above the worldwide average.
Cybercrime is the order of the day
Among the main threats that were collected in the study, the use of Cryptolocker was highlighted as being used to infect both private users and businesses.
In the case of private users, cybercriminals have begun to reuse an old technique that was first used over 20 years ago. It consists of infecting the victim via the macros in Office documents, mainly Word. One such example which was discovered by PandaLabs was a Word document containing a blurred image. At the top of the document in bold capital letters there was a message that indicated that the image was blurred for security reasons. If the user wanted access to the information then they had to enable the macros, with an arrow pointing to the button to be pressed. Once enabled, it showed you the clear image while simultaneously infecting you with a type of Cryptolocker.
In this quarter we have seen some of these notable cyberattacks on businesses:
- Ryanair, the well-known low-cost airline, was the victim of an attack which led to the loss of 5 million dollars.
- CareFirst BlueCross BlueShield, an American medical insurer, suffered an attack which saw the theft of information relating to over a million clients.
- AdultFriendFinder, an online dating site, suffered an attack which saw the theft of private user information. The attackers offered the stolen information to the first one to pay them 70 bitcoins, equivalent to $17,000 at the time. Not long after, the complete database was published online.
- LastPass, a leading password management company, was another victim of information theft.
- The well-known group Syrian Electronic Army managed to infiltrate the website of the US Navy, publishing propaganda promoting Bashar Al-Assad and his regime in Syria.
- Ben Rhodes, Assistant to the President of the United States and Deputy National Security Advisor for Strategic Communications and Speechwriting, stated that the White House had fallen victim to an IT attack.
In the second quarter, attacks focused on mobile devices were popular among hackers. WhatsApp is a popular way to attract and try to infect users with a trick called WhatsApp Trendy Blue. It passes itself off as a “new version” of the application with extra features when, in reality, the only thing it does is sign the user up to an expensive billing service.
These are just some of the important cases that we have seen this quarter. More than ever, businesses need to be prepared for this massive avalanche of information theft. They need to reinforce their systems and security solutions, and understand that a simple antivirus is no longer enough to safely protect themselves from an attack. Preventing attacks is the best way to combat them, as the costs associated with an attack put the stability and existence of businesses at risk.
The complete report is available here.
The post PandaLabs detected more than 21 million new threats during the second quarter of 2015, an increase of 43% compared to the same period in 2014 appeared first on MediaCenter Panda Security.
Know the difference between adware and porn?
“I know it when I see it,” is how US Supreme Court judge Steward Potter described his definition of pornography. But when it comes to adware, the description is far less titillating: You know it when you CAN’T see how to get rid of it.
The post Know the difference between adware and porn? appeared first on Avira Blog.
Aggressive Android ransomware spreading in the USA
The latest ESET discovery of the first known Android lock-screen-type ransomware that spreads in the wild and sets the phone’s PIN lock is examined.
The post Aggressive Android ransomware spreading in the USA appeared first on We Live Security.
![]()
What does the Avast Sandbox do?

The Sandbox is like a hamster ball. It keeps potential troublemakers isolated.
The Avast Sandbox lets you run a questionable program without risking your computer.
The Avast Sandbox is a special security feature which allows you to run potentially suspicious applications automatically in a completely isolated environment. This is particularly useful if you don’t completely trust whatever you just downloaded or you visit dodgy websites because programs running within the sandbox have limited access to your files and system, so there is no risk to your computer or any of your other files.
Here’s how it works: By default, if an application is started and Avast detects anything suspicious, it will automatically run the application in the Sandbox. The advantage of running an application in the Sandbox is that it allows you to check suspicious applications while remaining completely protected against any malicious actions that an infected application might try to perform.
The browser or other application will then open in a special window, indicating that it is being run inside the Sandbox. When the Sandbox is closed, it will be restored to its original state and any downloaded files or changed browser settings will be automatically deleted.

The sandbox window in Avast Premier.
The Avast Sandbox is part of Avast Premier 2015, Avast Internet Security 2015 and Avast Pro Antivirus 2015.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Turla APT Group Abusing Satellite Internet Links
Researchers at Kaspersky Lab have revealed that the Turla APT gang is using satellite-based Internet links to hide command-and-control activities.
Phones Under Attack By New Mobile Ransomware
Another Android threat similar to the well-known Koler A from last year is causing panic among Android users. The family is detected by Avira as Android/Locker.A and has tens of thousands of variants, with new ones created every day.
The post Phones Under Attack By New Mobile Ransomware appeared first on Avira Blog.
Sophisticated webinjects ‘tailored’ to beat bank security
From its relatively simplistic and niche origins, webinjects have advanced significantly in recent years to become a more sophisticated beast.
The post Sophisticated webinjects ‘tailored’ to beat bank security appeared first on We Live Security.
![]()