Sony Pictures Entertainment is still in the process of trying to recover from an apparent compromise of some of the company’s computer systems. The attack first came to light on Monday, and the extent of the incident is still emerging. The compromise appears to affect just the networks at SPE, a division of Sony. Reports […]
Tag Archives: Malware
Experts Question Legality of Use of Regin Malware by Intel Agencies
Though security researchers involved in uncovering the attack have remained mum on the attribution of Regin, privacy experts say that if one of the intelligence agencies is involved, there’s no legal basis for the operation.
‘Citadel’ trojan attacking password managers
Using password managers is often recommended as good practice in order to prevent overusing the same logins, but a new malware has been uncovered that specifically targets the password managers that hold all the variants.
The post ‘Citadel’ trojan attacking password managers appeared first on We Live Security.
![]()
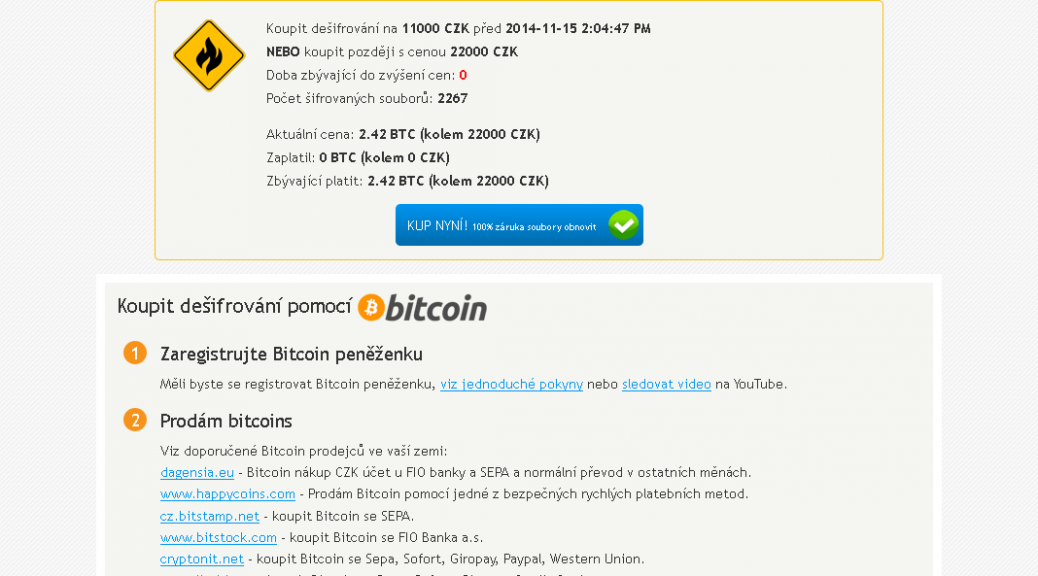
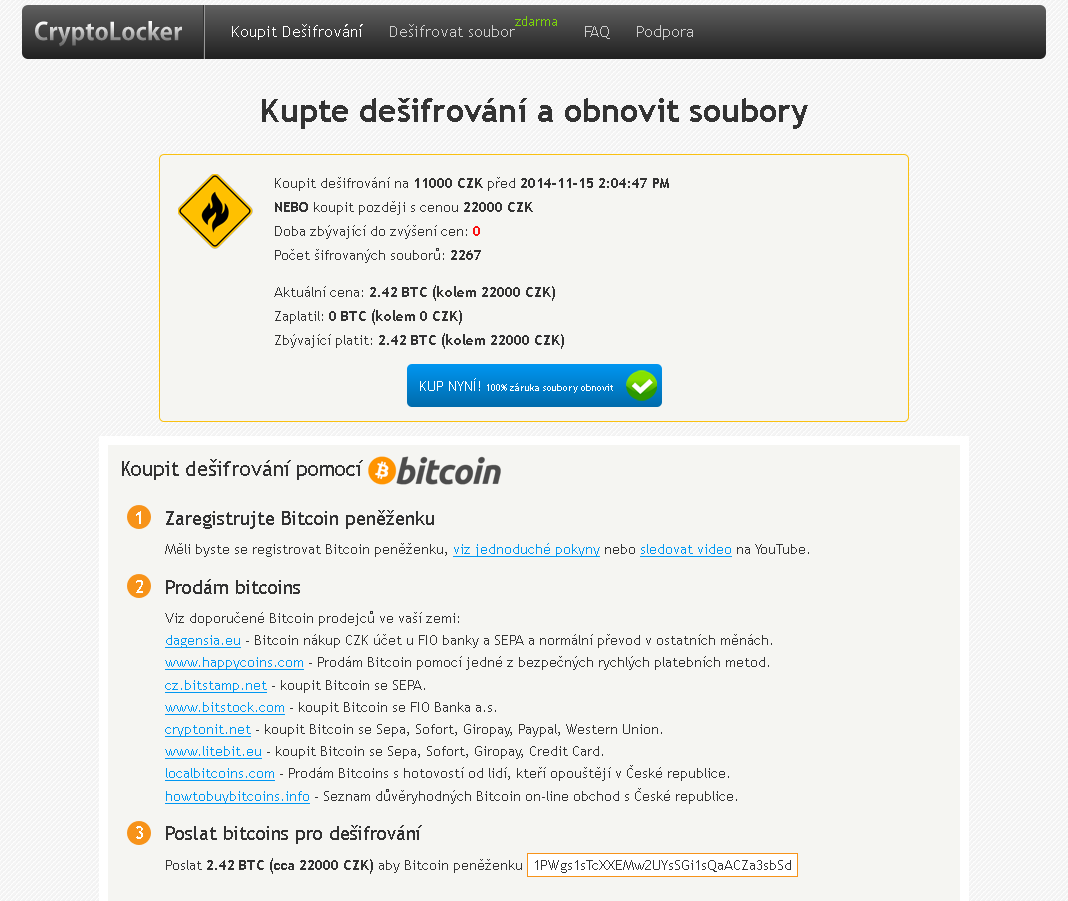
New CryptoLocker variant emerges in Czech Republic
What is ransomware?
As we witnessed with CryptoLocker earlier this year, ransomware is a type of malware which encrypts certain files on your system and then extorts a ransom to unlock them.
Which files are affected?
Most ransomware does not target important system files but instead looks for user files to encrypt. These can be everything from JPG images to office documents and emails, anything personal that could be a value to the user.
What is new about this variant?
Previous ransomware variants had weak or flawed encryption, which meant that files often could be recovered. This new variant contains a much stronger algorithm and encrypted files are almost impossible to recover without the encryption key, which is only held by the attacker. Interestingly the ransom can be paid in cryptocurrency as well as Czech Koruna.
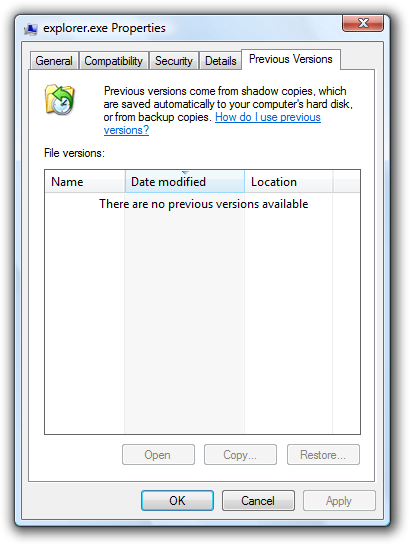
Is there any way to recover my files without paying the ransom?
Historically, it has been possible to restore files using Shadow Copy, a tool that allows users to backup parts of their system even while they are in use. Sadly most new ransomware variants are resistant to recovery with Shadow Copy. Always seek advice before taking any drastic action to recover data encrypted by ransomware.
How can you stay protected?
- Always backup -remember that malware has ability to encrypt files on all disks connected to your computer (including external USB disks, etc.) so be careful of leaving your backup connected to your machine or plugging in a backup to an infected device.
- Think before you click – If you are unsure whether a link or file is untrustworthy, it is always safer to ignore it and delete it. Never download a file or follow a link from an untrustworthy source.
- Get protection – As new variants emerge, they are continuously added to the database of definitions maintained by security companies like AVG. Up-to-date virus definitions are your front line protection against malware.
- Get some Identity Protection tools – Security software like AVG has specially designed tools to protect your personal data from fraudsters and malware.
Story from Tomas Prochazka
![]()
![]()
Can e-cigarettes give you malware?
The long-term health effects of electronic cigarettes – or E-cigarettes – are still open for discussion – but the devices could harm your computer, at least if one report is to be believed.
The post Can e-cigarettes give you malware? appeared first on We Live Security.
![]()
Week in Security: Grief for gamers, Unicorn spotted – and America wakes up
Cybercriminals once again had gamers in their sights this week, with leaks of multiple account details and a new Steam scam – but there was good news in the form of upgraded security on Whatsapp, and dawning awareness on privacy.
The post Week in Security: Grief for gamers, Unicorn spotted – and America wakes up appeared first on We Live Security.
![]()
Facebook scams – ‘Naked woman eaten by shark’ is latest bait
The latest salacious video – promising ‘Naked Woman Eaten by a Shark’ – is just one in a long chain of viral video scams spread via Faceboook.
The post Facebook scams – ‘Naked woman eaten by shark’ is latest bait appeared first on We Live Security.
![]()
Wireless attacks against ‘air gapped’ targets are possible, Israeli team claims
A team of Israeli researchers has demonstrated a way to hack into an ultra-secure air-gapped network, install malware, and retreive information – without using hardware such as USB keys.
The post Wireless attacks against ‘air gapped’ targets are possible, Israeli team claims appeared first on We Live Security.
![]()
Attackers Using Compromised Web Plug-Ins in CryptoPHP Blackhat SEO Campaign
Researchers have discovered a group of attackers who have published a variety of compromised WordPress themes and plug-ins on legitimate-looking sites, tricking developers into downloading and installing them on their own sites. The components then give the attackers remote control of the compromised sites and researchers say the attack may have been ongoing since September 2013. […]
Angler Exploit Kit Adds New Flash Exploit for CVE-2014-8440
Exploit kit authors are nothing if not opportunistic, and they know a prime opportunity when they see one. Adobe Flash bugs fit that description nicely, and the people behind the Angler exploit kit already are exploiting one of the Flash bugs patched last week in the kit’s arsenal. This is a common tactic for exploit […]