
Something as simple as an SMS has threaten Apple and its iPhones. A security flaw has been found in Cupertino’s Smartphone, it is one of those text messages which gives the user a nasty surprise: when you receive it, your iPhone reboots.
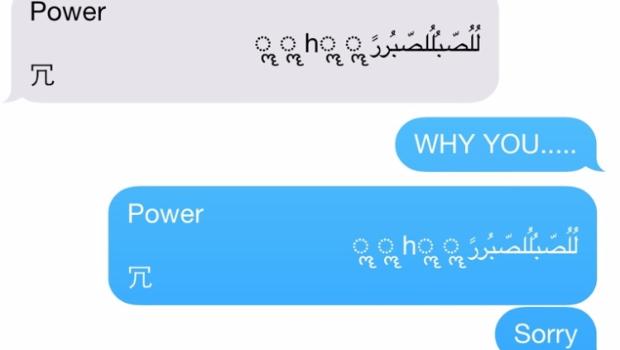
The SMS that causes the device’s failure is not an ordinary text message. Therefore, it is virtually impossible that users receive this SMS by accident. The bug is a text string with symbols and Arabic characters in a specific sequence, which causes iMessage to collapse and the iPhone to reboot.
Just like you have seen in the video, it is not necessary that the user access the messaging application. As soon as you receive it, the device reboots. If that wasn’t enough, once the iPhone is back on, it is not possible to access the messaging application to eliminate the malicious conversation: it is blocked.
In addition, the SMS has not only highlighted the existence of a vulnerability in iPhones, but it also caused iPads, Macs and even the brand-new Apple Watch to crash too.
The company has already announced that they are aware of the vulnerability and that they will solve it through a future iOS update.
Are we still in danger?
Meanwhile, the controversial SMS continues to cause chaos on Apple devices. Putting an end to its effects is not easy, but fortunately, there are some fixes available to re-open the Messages app:
- Ask the person who sent you the malicious SMS to send you another text message so the conversation continues, cancelling the effects of the first. Once received a second message, the user can access the conversation list and eliminate it.
- Ask Siri. This is the solution proposed by Apple, but this time you will be the one paying for the SMS as you will be the one sending it. After receiving the damn message and seeing how the device reboots, the user could ask Siri to “read unread messages”. Siri won’t be able to read the SMS and will ask you if you want to reply. In that moment, you will be able to dictate a message to Siri, so the last strand of the conversation is not the one that causes the system’s failure. This way you will be able to access the conversations lists and delete the thread.
- Send a picture via the Photos app, which will allow you to access the message history and then delete the conversation, at last.
All this taking into account that the character strand that causes the failure in the system is not a usual message. If you receive it, it is because your prankster friend or someone else wants to give you a hard time. So, until Apple launches the next iOS update we will need these tricks to fix this problem.
The post Need help fixing the iOS text message bug causing iPhone crashing/reboot? appeared first on MediaCenter Panda Security.







