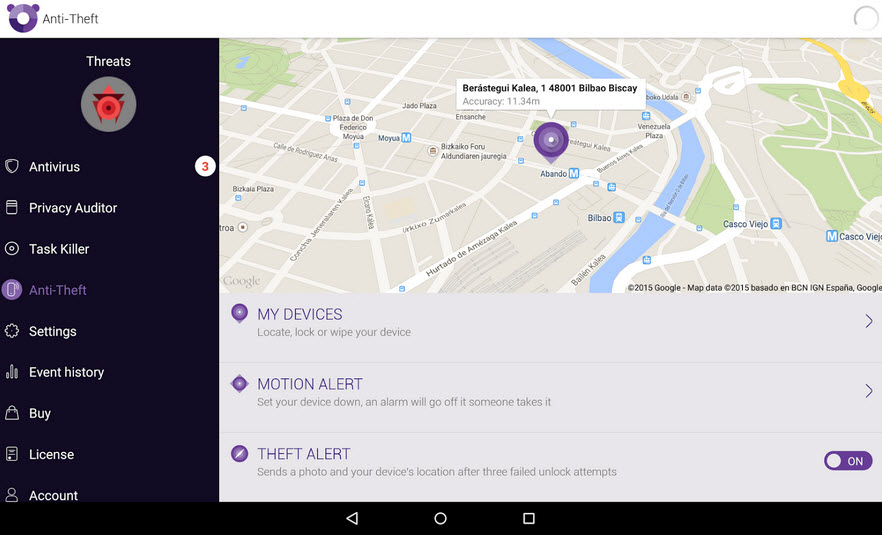
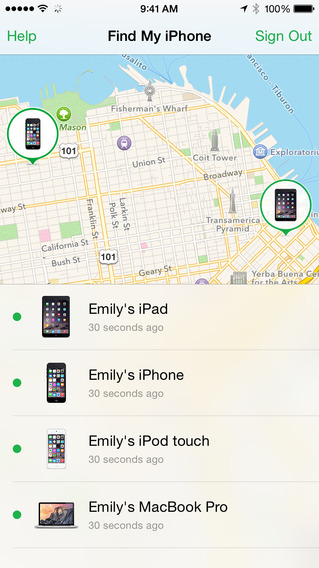
Mobile companies are now a reality. Nobody doubts that accessing corporate applications through smartphones and / or tablets is not only convenient but also necessary, for increasing productivity to levels which were thought impossible until a few years ago. In addition, the demand by workers, employees and companies’ suppliers for access to the organizations’ mobile satellite systems, applications and certain data, is imperative. The problem, however, is that the boom in mobility has also brought certain risks which many companies are not yet aware of.
A company is not secure anymore if it only limits itself to protecting the traditional organizational perimeter. It is no longer enough to have firewalls, threat management solutions, antispam and content filtering. Now it is necessary to protect access and not only from a PC. So it is essential to have a real strategy and best practice regarding the use of mobility in the company: a strategy that in addition to ensuring the safety of the devices also incorporates other elements such as the protection of data and applications with which the mobile users interact. In addition, this strategy must be compatible with another requirement: that it does not interfere, in any way with the agility and entrepreneurial dynamism which the use of mobile devices provides.
Secure devices and encrypted communications
One of the first requirements to be included in any mobile security strategy is to protect mobile devices with antimalware security software. Yes, malicious software attacks not only the operating systems of traditional desktops or laptops. Recently especially Android, Google’s mobile operating system which is the most widespread in the market, and iOS, the Apple platform, have become a focus for cybercriminals. Even so, and despite the evangelization of the leading manufacturers of security software, there are still many companies (as also occurs with users on a personal level) who have not protected their mobile devices with the high risk that this entails. It is an indispensible task to have antivirus software in place and, of course, updated.
Another important aspect, in addition to encrypting communications on mobile devices so that no data can be intercepted, is to use a user authentication device that goes beyond the traditional password. In fact, many mobile devices already allow by default identification by fingerprint and there are even some prototypes which will bring recognition through the iris as standard practice. There is no need, however, to use biometrics. The use of passwords can also be combined with other means of identification, for example involving the use of email or text messages to the mobile itself, other security tokens, etc. In this respect, organizations should train employees to use the correct identification tools and to know how to act in case of loss or theft of the device.
Beware of third-party software
It should also establish policies that restrict employees from using third party software that may cause risks for companies. There are many professionals who, when installing an app of dubious origin or which, although it seems authentic is in fact an imitation created by cybercriminals, see how their device is attacked and consequently the security of data handled by their organization seriously compromised. Following this line, the consultants, Gartner, advise that jailbreaks on iOS devices and rooting on Android phones should be avoided, these being two practices which give the user administrator privileges with the risks which this involves for companies.
Interestingly, the experts at Gartner claimed in a public study in 2014 that most of the security breaches which will occur on mobile devices in 2017 (up 75%) will be the result of a bad configuration of applications built for these gadgets. An example of this is the misuse of personal cloud services through apps that users of smartphones and tablets have installed. The best defense, they argue, is that the company should install a fixed configuration for this type of device under the umbrella of a management policy for mobile equipment which must be complemented with other tools for data protection.
The consultants also recommend that companies should specify which platforms and operating systems should be used for their mobile devices by their employees and that versions which cannot be updated or supported should be avoided, and that users should be required to register or be certified when entering applications such as virtual corporate email, VPNs, wireless and other shared applications. What is essential, they stress, is that the security team know what types of systems and applications its employees need to access and for what purpose, in order to establish the appropriate controls. Also, mobile devices must be configured to prevent wireless networks that are not safe and users should be recommended to disable the Bluetooth option to avoid unexpected scares.
Controls and audits are highly recommended
Finally, it is also recommended that companies undergo regular audits and controls (at least once a year) to evaluate the quality and robustness of their mobile security policy. It should not be forgotten that security incidents not only entail negative economic repercussions and loss of core assets such as the company’s own data or that relating to customers (or citizens, in the case of government departments) but also damage reputation and image. And to remedy this is just to be more aware of the new realities of today’s organizations, now completely mobile.
The post The safe mobile company, a fantasy? appeared first on MediaCenter Panda Security.
![]()