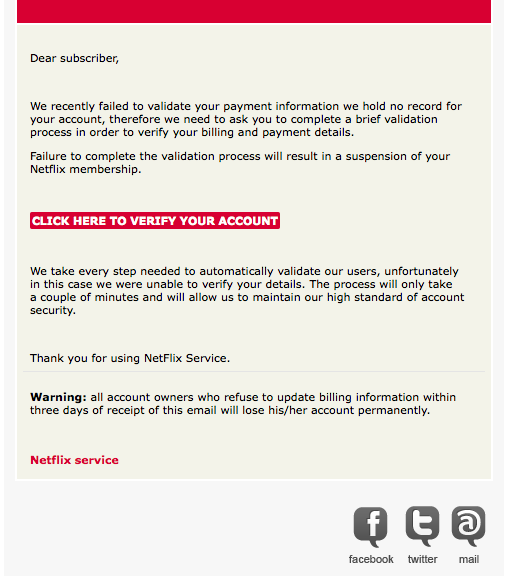
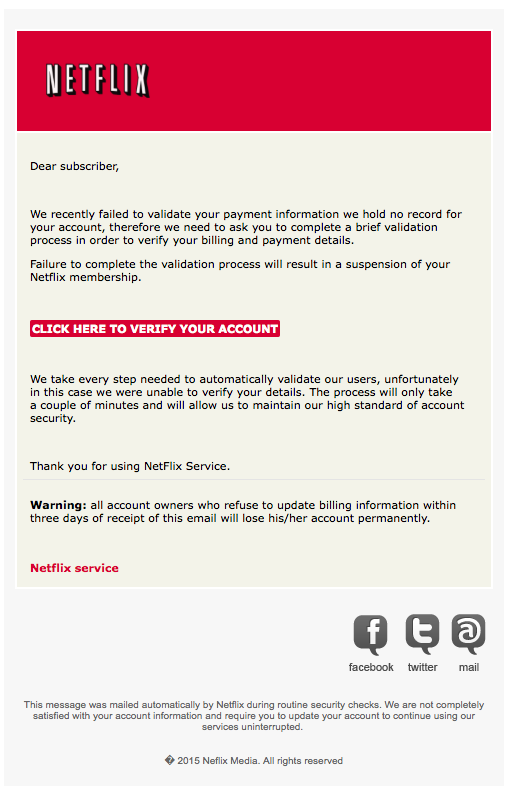
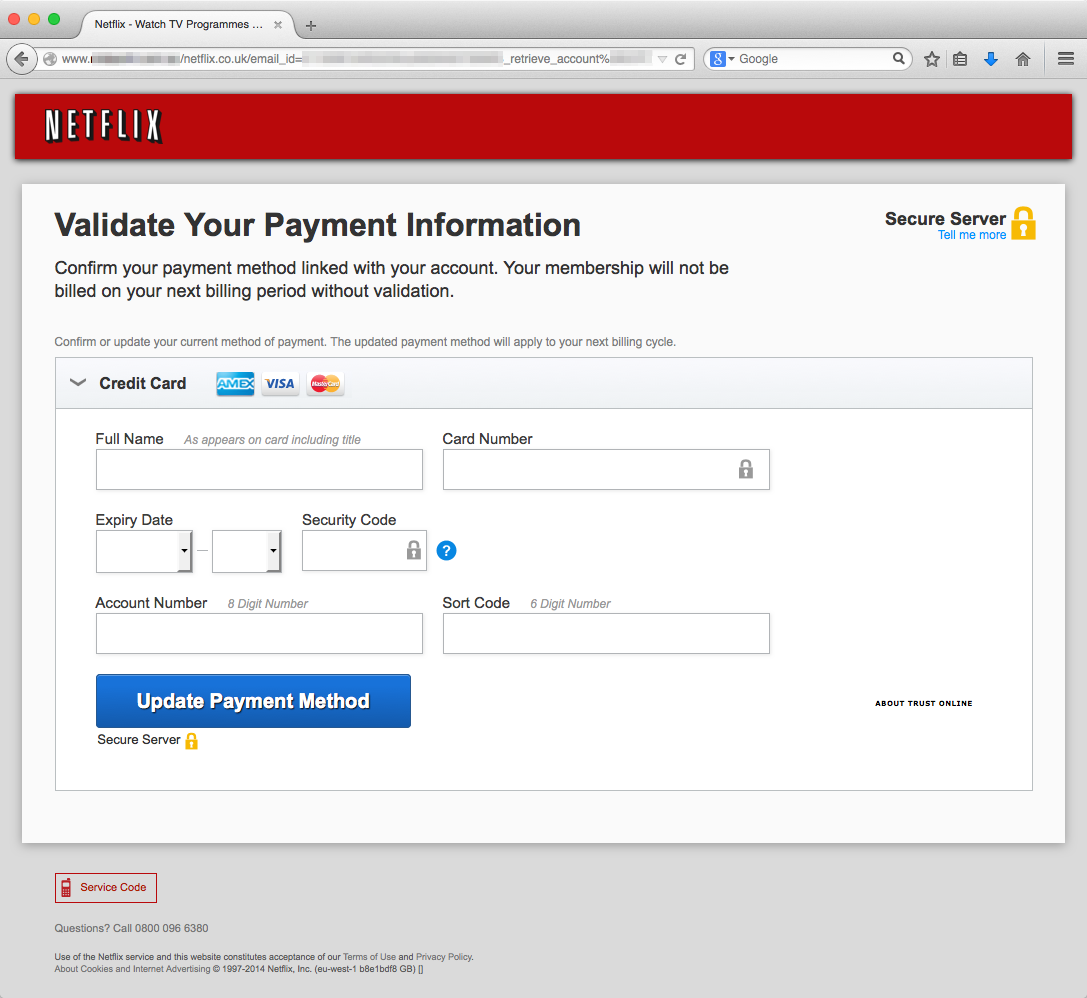
Phishing emails and instant messages attempt to lure you with bait, just like with fishing in the real world, which is where the term phishing originated.
Just like a real fish, as you learn to identify the types of phishing bait being used, you’ll drastically reduce your chances of getting caught.
Successful phishing scams utilise three tricks to catch victims:
Urgency
Threatening you with a consequence if you don’t act.
e.g. “A request to terminate your account, or a claim that it’s about to be suspended.”
Curiosity
Offering you some juicy bait, tempting you to act.
e.g. “Attached is a company report that contains the salary information of your colleagues.”
Familiarity
Tricking you into acting thinking it’s from someone you know.
e.g. “There’s an important message from someone waiting for you online.”
Armed with this knowledge you’ll be more alert to suspicious emails and messages when they land in your inbox.
#1: Check the facts before acting
Verifying the authenticity of a message can be a challenge- especially if the sender’s email or social media account has been hacked.
Here are two easy ways to check whether or not the message is a scam.
- If you know the sender, contact them using another service (email, social, phone etc) to check that their message is legitimate.
- If not, enter the subject line or some other small part of the message into your favourite search engine.
If your search reveals others who have reported this message, or are asking questions about its authenticity then you’ve proven two things – first, you’re not alone and second, it probably is a phishing, scam or hoax email.
#2: Make sure it is safe
A phishing email or instant message typically contains a web link (URL) to click on, and in the case of an email possibly even an attachment of some kind.
Check out this video to learn how to tell if it’s a bad link or not:
However, it’s worth emphasising that knowing if a link is truly “bad” before you click isn’t a perfect science, and often security professionals can’t even tell until they visit it.
If there’s an attachment on the email you need to be particularly careful NOT to open it. Believe it or not, even PDF and Word files can be infected! If you weren’t expecting the file, don’t open it. No exceptions.
A great way to help with these safety checks is to protect your devices with antivirus software which will scan all files and attachments for malware and even scan links to check they are safe.
#3: Report it
Lastly, if you do spot a phishing email, be a good online citizen and consider taking the time to help out by immediately reporting it directly to the legitimate organisation or person that’s being impersonated.
Many large companies, particularly banks, have websites dedicated to providing further resources and information about how to stay safe from phishing, along with ways to report phishing cases to them, and also examples of recent scams that are circulating.
Each and every one of us has the ability to improve the lives each other online, so make sure you share this information on how to stop phishing with those you care about.
Until next time, stay safe out there.