2014 has been an active year for cybercrime. Let’s start with the most recent and then take a look at some of the other important security events of the year.
State-sponsored espionage
We are ending the year with the most publicized and destructive hack of a major global company by another country – now identified as North Korea. The Sony Entertainment attack, still being investigated by the FBI, resulted in the theft of 100 terabytes of confidential employee data, business documents, and unreleased films. It was an attack on privacy due to the theft of a massive amount of personal records, but also essentially blackmail; aiming to silence something that the North Korean government didn’t like – namely the release of The Interview, a movie depicting an assassination attempt on Kim Jong-Un.
Most of the blame for state-sponsored cybercrime in 2014 has been with Russian or Chinese hackers. Whether private or state-sponsored, these hackers have attempted to access secret information from the United States government, military, or large American companies. Recently, Chinese hackers sponsored by the military were indicted for economic espionage by the U.S. Department of Justice.
 Large data breaches
Large data breaches
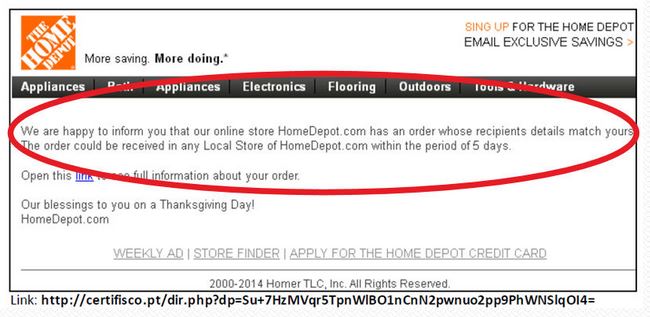
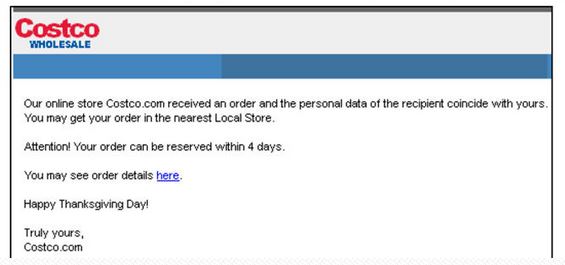
Along with the Sony breach, other notable companies that suffered from cybercrime include Home Depot, eBay, Michaels, Staples, Sally Beauty Supply, and others. A significant number of these breaches were begun months or years ago, but were revealed or discovered in 2014.
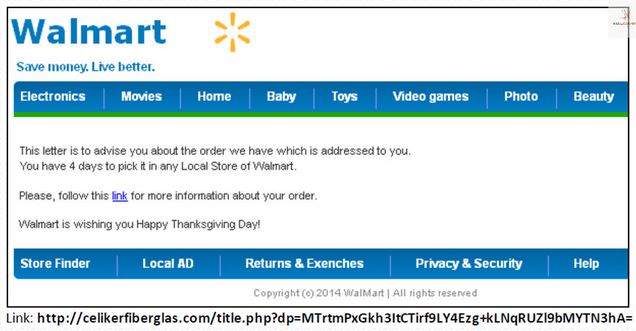
Nearly 110 million records were stolen from Home Depot; the largest ever breach of a U.S retailer. The cyber-heist included 56 million payment card numbers and 53 million email addresses.
JPMorgan Chase’s data breach impacted nearly 80 million households in the U.S., as well as 7 million small- and medium-sized businesses. Cybercriminals were able to gain access after stealing an employee’s password, reminiscent of the Target breach from 2013. This breach is said to be one of the largest breaches of a financial institution. The FBI is still investigating.
Financial and data stealing malware
GameOver Zeus, called the most infamous malware ever created, infected millions of Internet users around the world and has stolen millions of dollars by retrieving online banking credentials from the infected systems.
Tinba Trojan banking malware uses a social engineering technique called spearfishing to target its victims. The spam campaign targeted Bank of America, ING Direct, and HSBC customers using scare tactics to get customers to download a Trojan which gathered personal information.
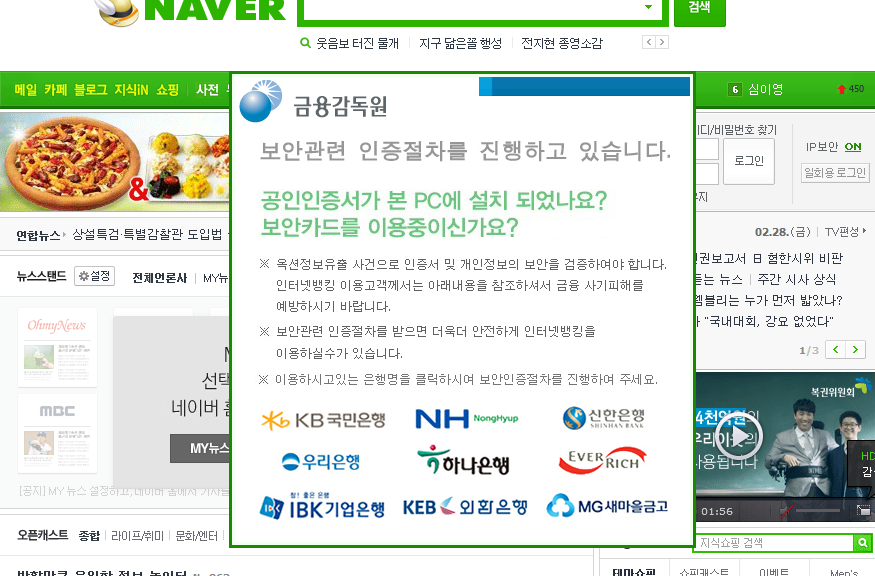
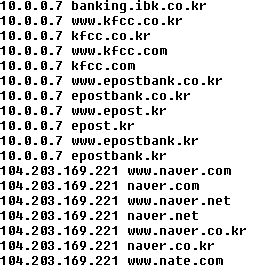
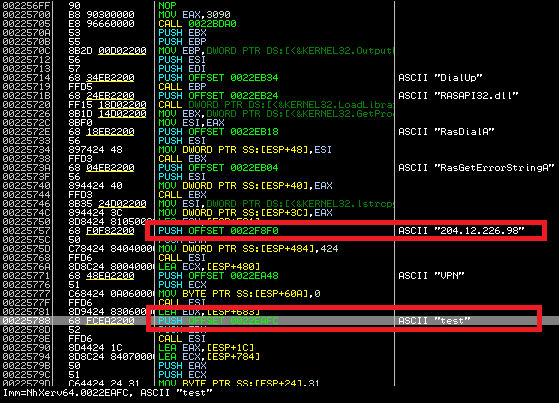
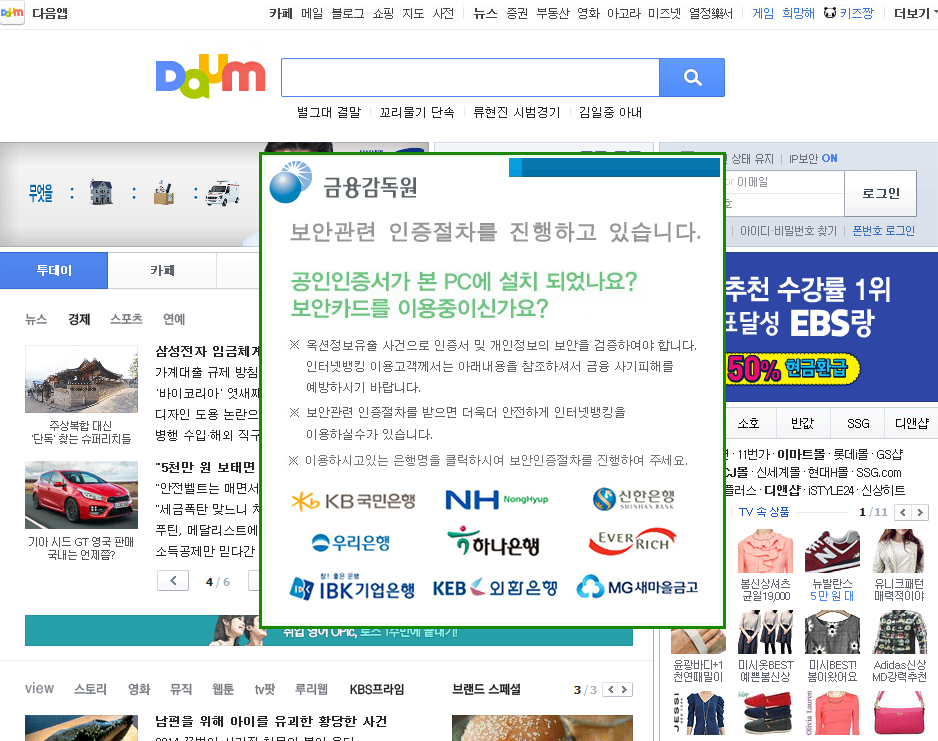
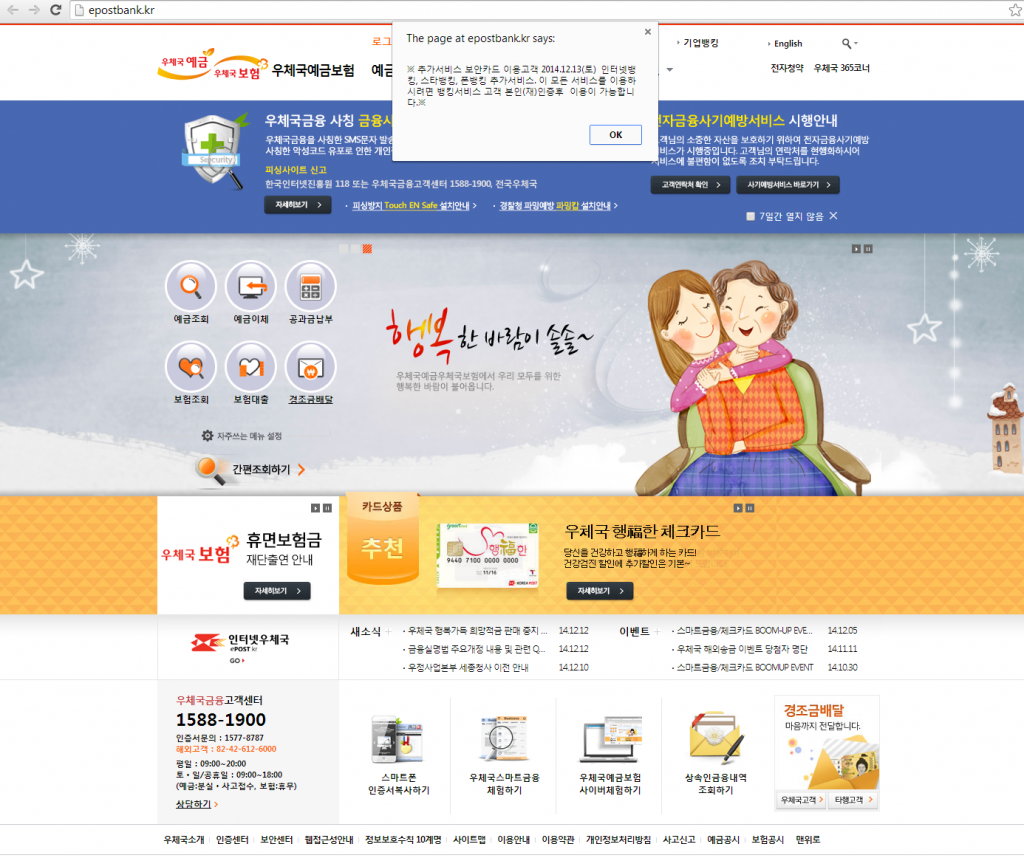
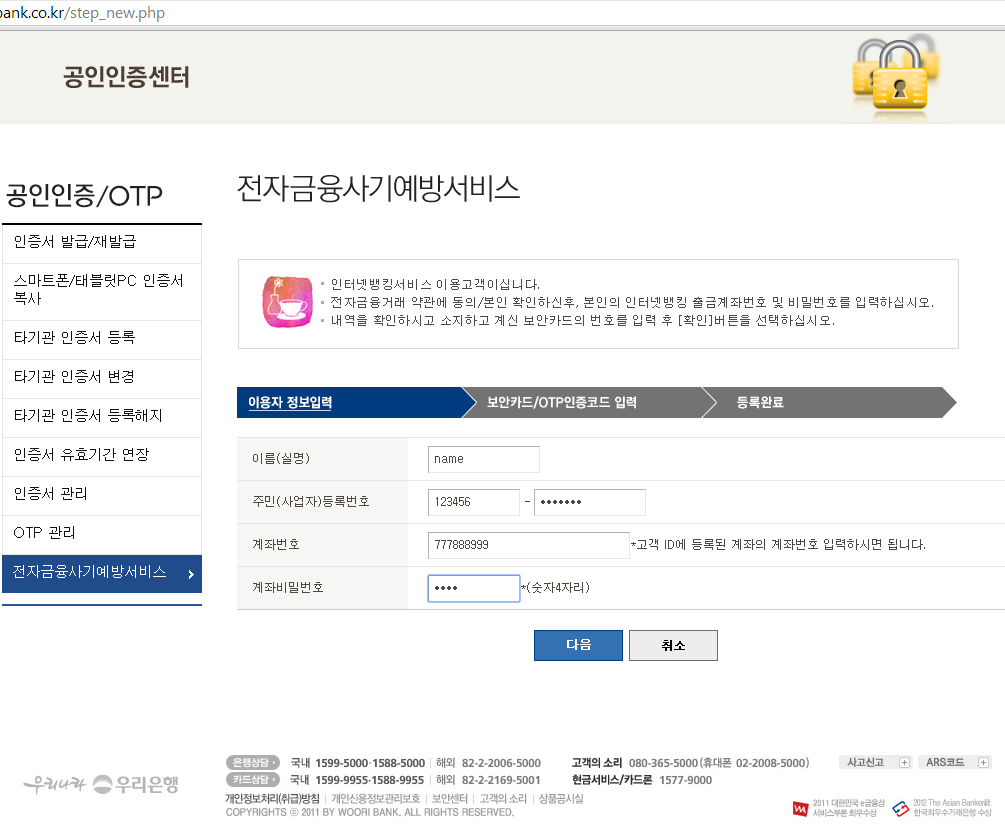
Chinese hackers were at it again, and again, targeting South Korean banking customers with banking malware using a VPN connection. The customers were sent to a look-alike webpage where they were unknowingly handing cybercrooks their banking passwords and login information.
Software vulnerabilities
Many of the breaches that occurred in 2014 were because of unpatched security holes in software that hackers took advantage of. The names we heard most often were Adobe Flash Player/Plugin, Apple Quicktime, Oracle Java Runtime, and Adobe Acrobat Reader.
Avast’s selection of security products have a feature called Software Updater which shows you an overview of all your outdated software applications, so you can keep them up to date and eliminate any security vulnerabilities.
 Numerous new exploits
Numerous new exploits
Flaws in software led to Shellshock and Heartbleed, two names that struck terror in IT administrator’s hearts.
Heartbleed takes advantage of a serious vulnerability in OpenSSL. It allows cybercrooks to steal encryption keys, usernames and passwords, financial data and other sensitive data they have no right to, and leaves no trace of the operation.
Shellshock ended up affecting more than half of the websites on the Internet. Hackers deployed malware on legitimate websites in order to retrieve confidential data from compromised computers.
Ransomware
Another name that made headlines was a group of malware dubbed ransomware, such as CryptoLocker, and its variants Cryptowall, Prison Locker, PowerLocker, and Zerolocker. The most widespread is Cryptolocker, which encrypts data on a computer and demands money from the victim in order to provide the decryption key.
Avast detects and protects its users from CryptoLocker and GameoverZeus. Make sure you back up important files on a regular basis to avoid losing them to ransomware.
Ransomware made its way from desktop to Android during the year, and Avast created a Ransomware Removal app to eliminate Android ransomware and unlocks encrypted files for free.
Privacy attacks
Mac users were shocked, celebrities mortified, and fans titillated by news of the iCloud hack which lead to the online publication of numerous private photos of Hollywood famous celebrities. The serious cloud breach was launched using brute force methods on targeted iCloud accounts.
Social engineering
The art of deception is a highly successful method for cybercrooks. The weakest link in security is the end-user, and hackers take advantage of us all the time using social engineering schemes.
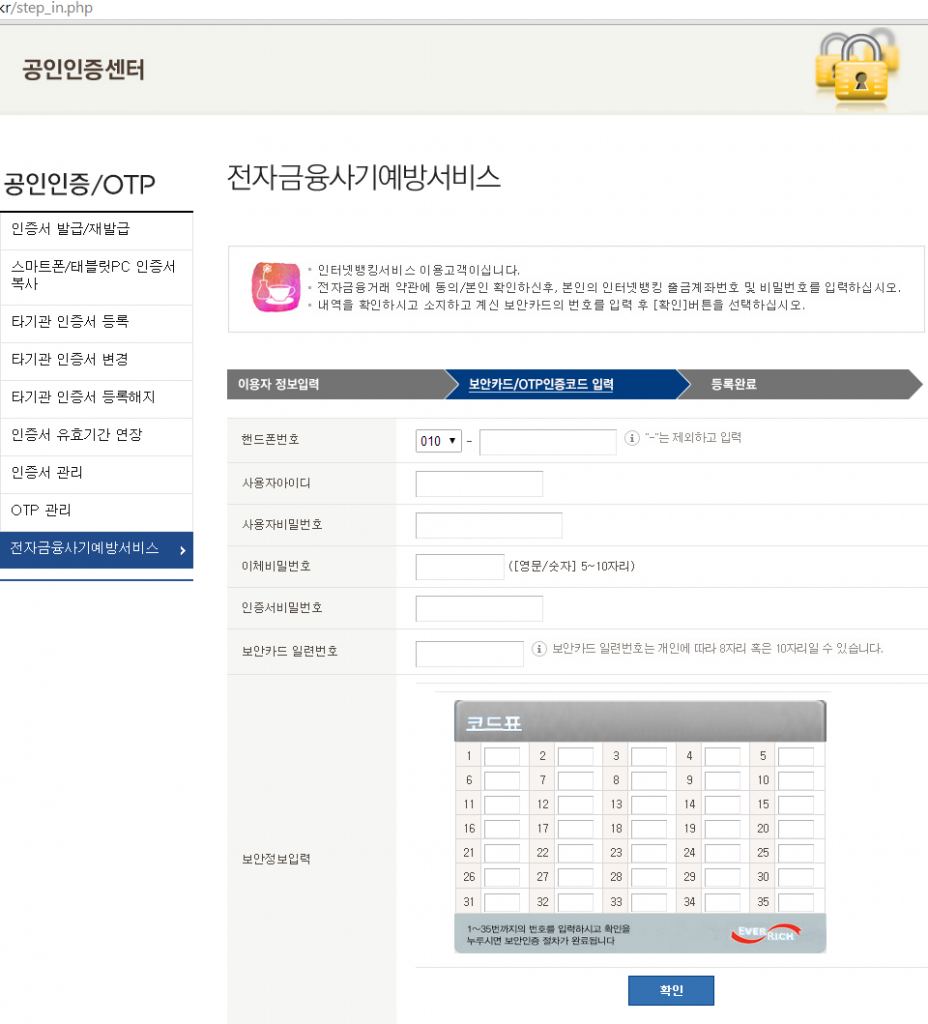
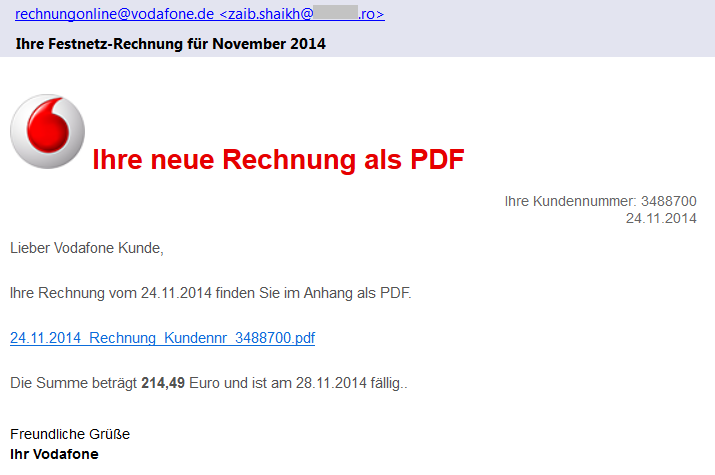
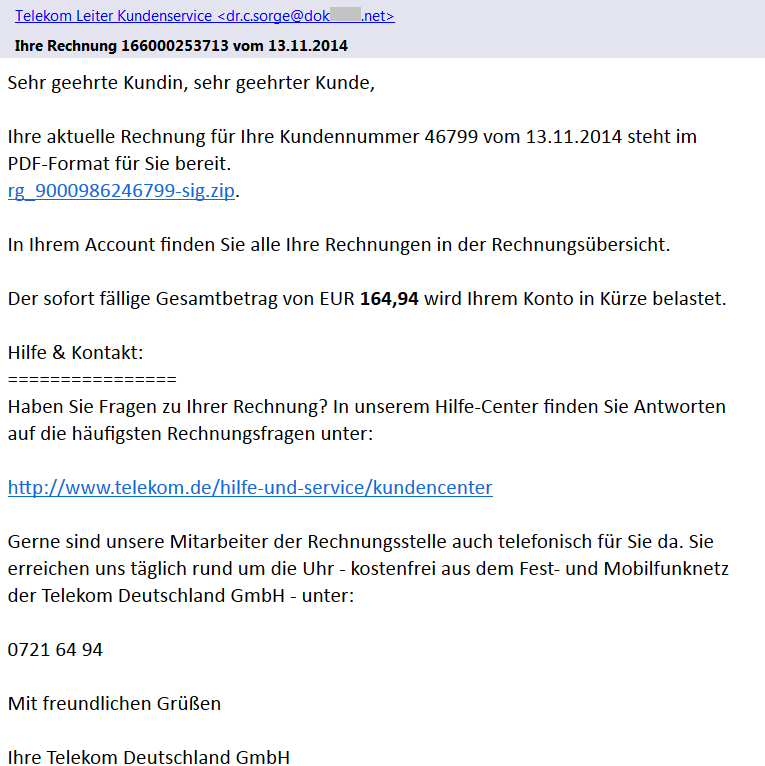
In a phishing or spearphishing attack, hackers use email messages to trick people into providing sensitive information, click on links, or download malware. One of the most famous instances was the Target breach, in which hackers got a network password from a third party vendor that worked for Target, to get into the network and compromise their point-of-sale machines in November 2013.
Social media scams
Social channels, like Facebook, offer a perfect environment for social engineers. They can create buzz, grab users’ interest with shocking content, and encourage people to share the scams themselves. Scams often come in the form of fake video links which lead to surveys and rogue webpages.
Exploit kits for sale
The Avast Virus Lab observed increased activity of malware distributed through exploit kits this year. These kits, often for sale on the deep web, allow cybercrooks to develop customized malware threats in order to attack specific targets. Zeus source code was used to develop Gameover, and the Zeus Gameover network was used to download and install Cryptolocker.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.