We’ve been following the slow evolution of an interesting strain of ransomware we have named ‘Crypt888’, which is unlike other strains that have reported on over the past few months.
Crypt888 has been focused on experimenting with user interfaces rather than improving its code, serving up ransom instructions in a variety of languages including Italian and, most recently, Czech.
In June 2016, AVG’s Virus Lab released six free decryptors for the recent strains of ransomware. We continue to monitor the situation, ready to update the tools as the ransomware evolved.
Our research uncovered one strain, Crypt888, behaving differently to the others. Instead of improving the code, the malware authors were focused on experimenting with the user interfaces such as changing the language of the ransom message.
This means that the underlying Autolt script remains the same in the previous versions … but oddly, the ransom instructions are served up in the Czech language only in the latest version.
This is how we identified and tracked the evolution of Crypt888’s.
Tracking a threat
Crypt888, also known as MicroCop and Mircop, is one of the many ransomware strains discovered in 2016 and its evolution has been very specific. After analyzing various samples, we found that the wallpaper containing ransom instructions is the only part of Crypto888 that has changed.
The underlying AutoIt script has remained more or less the same in all the known versions of this strain. So too has the encryption algorithm, encryption key, file names, and various other components, which is not so usual. While this means our decryptor can rescue your encrypted files, it means that the way in which Crypt888 presents itself keeps changing. In the latest version, the instructions appear in Czech.
Changing the language in which the ransom message is delivered has been a hallmark of this particular threat. We tracked several evolutions of Crypt888 from its first appearance in June this year.
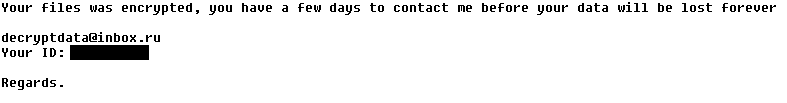
- The ‘Guy Fawkes’ version, June 22, 2016: first known version of this ransomware
- The ‘Business Card’ version, July 8, 2016: this version appears and looks like a test version as there are no payment instructions
- The ‘Italian’ version, July 29, 2016: this version had several new features and the errors in the language suggest machine translation
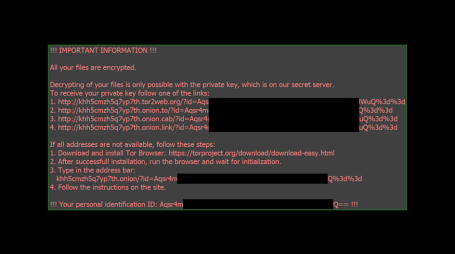
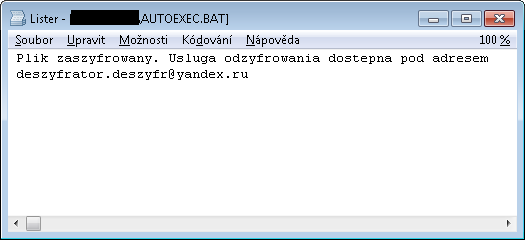
- The ‘Czech’ version, September 21, 2016: the latest variety appears in yet another language, again with errors suggesting the author is not a native speaker
The first encounter
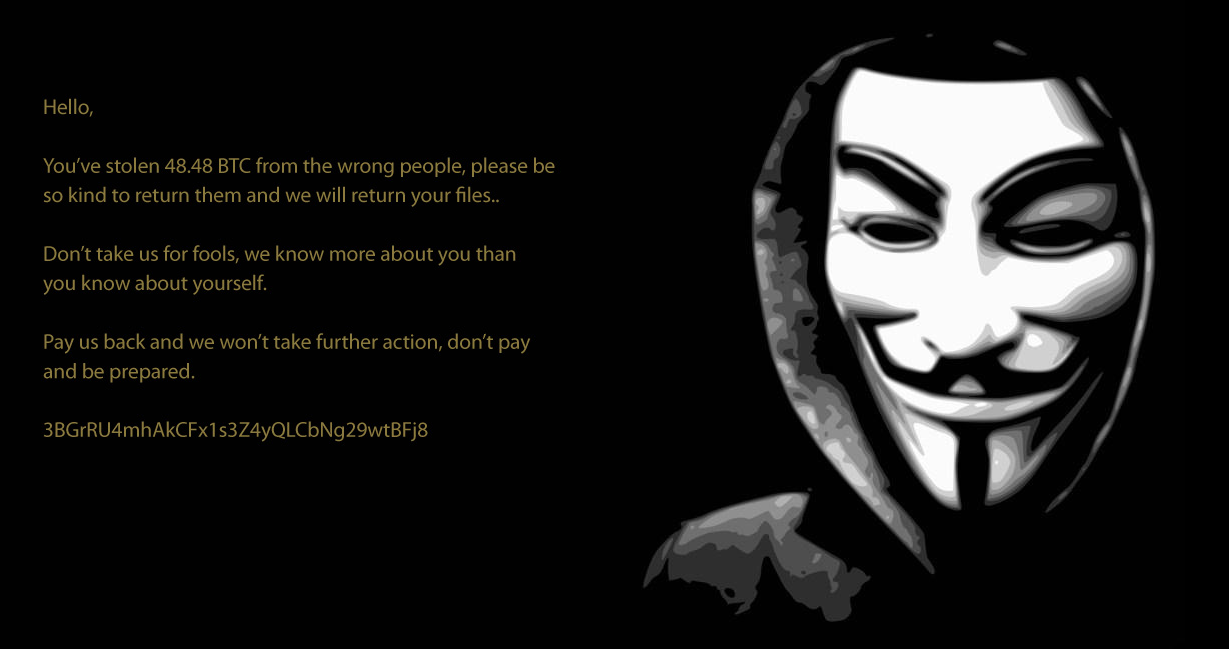
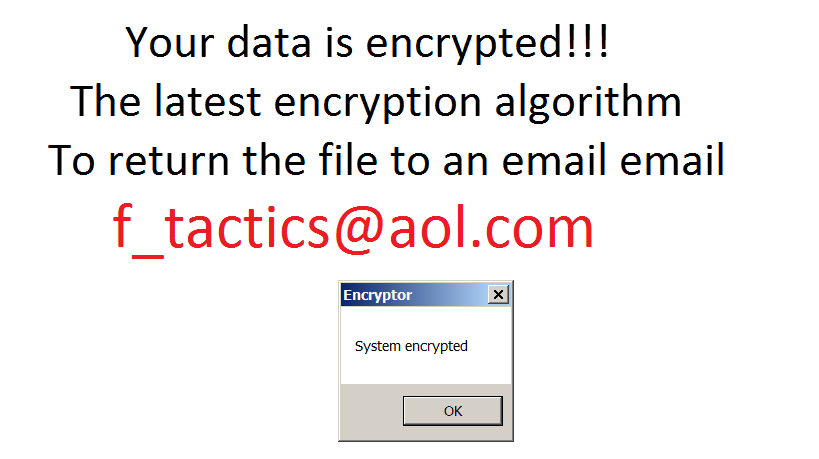
The first known version of Crypt888 appeared as black wallpaper with the image of a Guy Fawkes mask, a notorious symbol usually associated with Anonymous. The message accused the victim of stealing 48.48 Bitcoins ($30,000) from ‘the wrong people’ and requesting its return.
The threat intimated there would be repercussions but there were no details about how to comply with repayment or how the decryption process would work after payment was made. This is probably the reason why we found only one transaction to the provided bitcoin address so far.

Testing, testing, 1 – 2 – 3
A few weeks later, we identified a second version. This time, the wallpaper with the story and related accusations were gone. In fact, there were no payment instructions at all and instead, the wallpaper contained the “business card” (as seen in this video).
We have no clear explanation why this particular image has been used but we think it was probably a test version based on a fact that there were no instructions or payment addresses provided to victims.
Just in case, however, we released a free Crypt888 decryption tool, which was able to recover files encrypted by both of this and the earlier version.
The Italian affair
Three weeks later, we identified yet another version of Crypt888 which had multiple changes. While the AutoIt code was once again similar to the previous versions and the same algorithms used – so our decryption tool is still fully functional for this version – the code was obfuscated.
There was a new image which contained ransom instructions in Italian, with typos and errors that suggest machine translation. In addition, this version of Crypt888 did not create the text file LEGGIMI.txt, which should contain the payment instructions. This means victims would find themselves left with encrypted files and no instructions as to how to recover them.

Czech-mate
Malware researcher S!Ri identified this latest version one month after the Italian version. We investigated further and found its code is no longer obfuscated, and essentially, it’s the same as the first two versions with the wallpaper being the only notable difference.
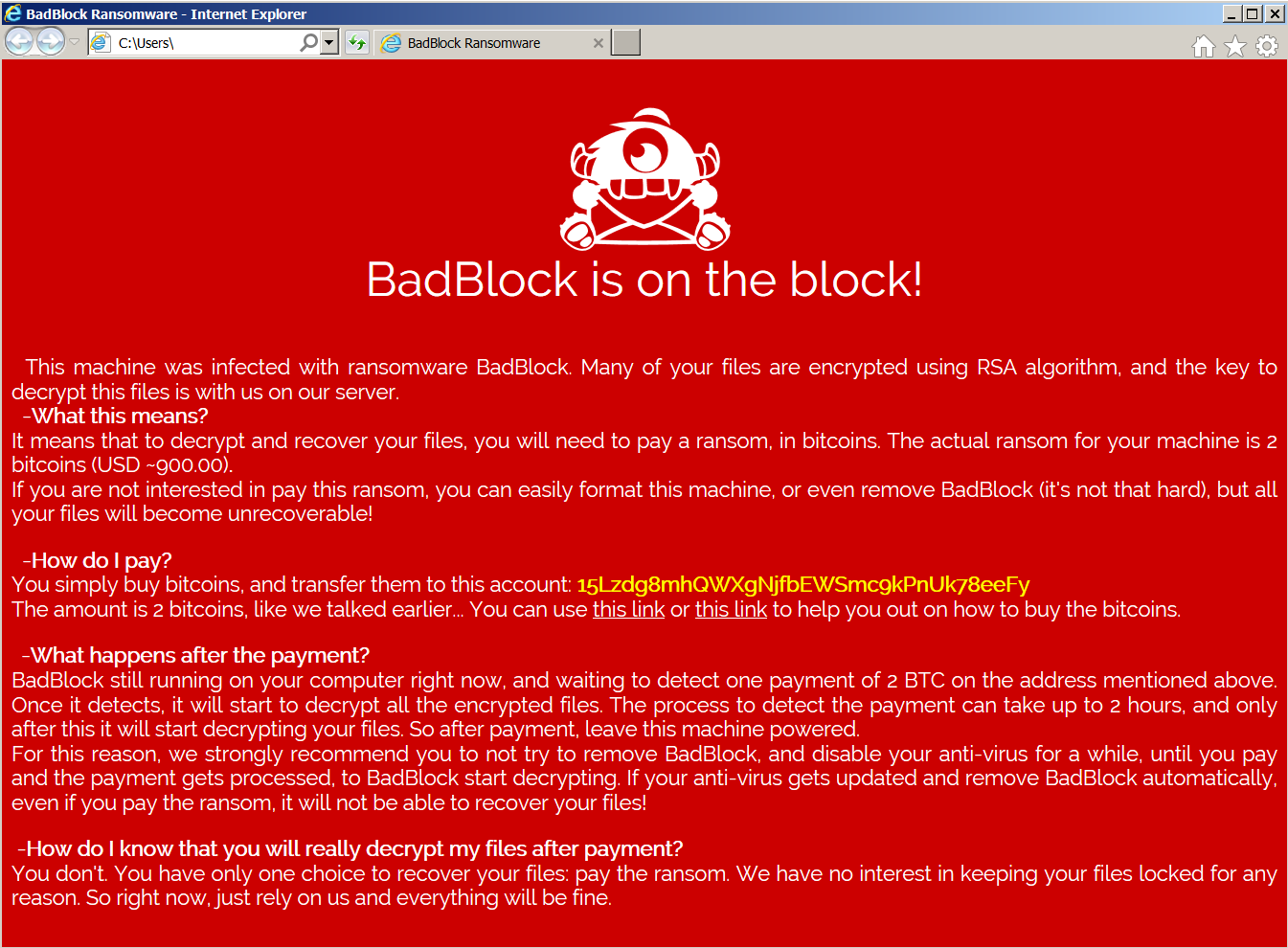
These ransom instructions this time appear in Czech and are a departure from previous versions in terms of content. Firstly, the ransomware claims that it is a ‘Petya ransomware 2017’. But don’t be fooled – it is not. This is probably a maneuver to fool victims hit by Crypt888 that are trying to find a free fix online.
Petya is a much more sophisticated piece of ransomware and it is not decryptable at the moment. This is not the first time one ransomware strain has pretended to be another; we observed lesser known ones have masqueraded as a more famous one, such as TeslaCrypt, CryptoLocker, or CryptoWall on a number of occasions.
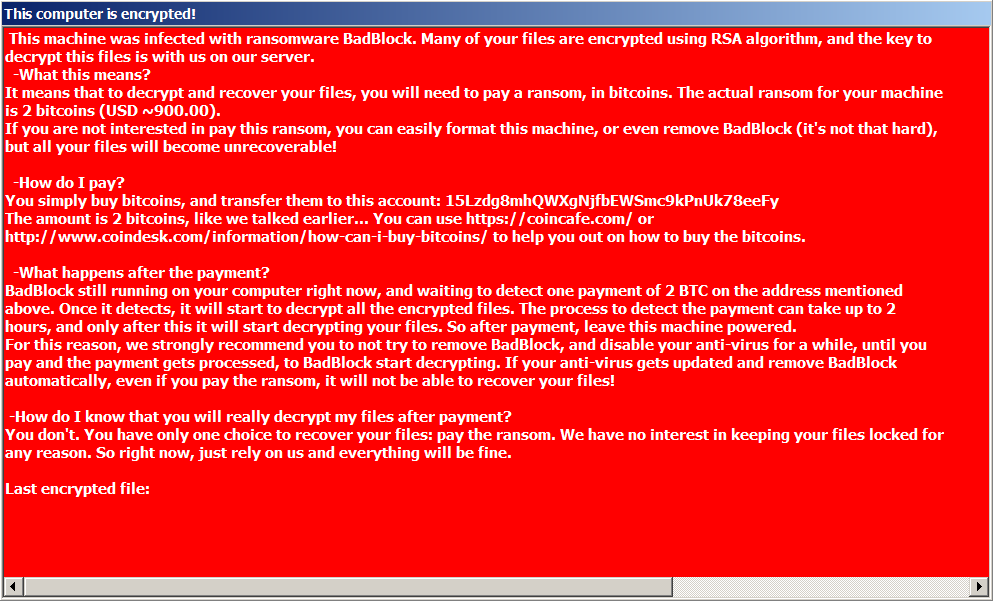
The Czech version also differs in that the ransom amount is ‘only’ 0.8 Bitcoin ($480 at the time of writing). The number reflects an apparent fixation with the digit ‘8’ as it is heavily used across the program: in the ransom amounts, the configuration of the encryption algorithm, the created file names, etc. That’s why we chose the name Crypt888 when we identified it.
Another change is that victims are threatened with a five-day deadline to pay, and two email addresses are provided for the victim to send proof of payment (and to receive the decryption tool, allegedly) yet no penalties are mentioned if the deadline is missed.
Finally, the authors hint in the text about the ransomware’s origin with the sentence which, when translated, means “We belong to Czech/Russian Hackers”. Based on the accuracy of the available text and code quality, it is hard to believe those claims, as it contains many typos, incorrect word order, odd mixtures of text with and without Czech diacritics, and other errors. More likely, the text was created by machine translation, like the Italian version.

At the time of writing, we have not found any further language variants of this ransomware and can reassure people that our free decryption tool will work for all the versions described here.
We suspect the authors of Crypt888 are still producing new versions of their ransomware. Their technique is in contrast to authors of other ransomware families in that they focus primarily on changing graphics and preparing fake stories rather than on improving their code. We are continuing to monitor for any new variants that will make it necessary to adapt our decryption tool to ensure victims have a means to mitigate a Crypt888 attack.
![]()
![]()