A researcher disclosed vulnerabilities in TP-Link C2 and C20i routers that allow for remote code execution and denial-of-service attacks with authentication.
Tag Archives: router
DNSChanger Exploit Kit Hijacks Routers, Not Browsers
An exploit kit called DNSChanger is attacking routers, not browsers, through a malvertising campaign.
Secure your router: How to help prevent the next internet takedown
Secure your router, says ESET’s Lysa Myers. It can help protect all of your connected devices while they are in your home.
The post Secure your router: How to help prevent the next internet takedown appeared first on WeLiveSecurity.
![]()
Cybercriminals target Brazilian routers with default credentials
Criminals are hunting for routers with default credentials and with vulnerabilities in their firmware, with Brazilians the main target.
The post Cybercriminals target Brazilian routers with default credentials appeared first on WeLiveSecurity.
![]()
At least 15% of home routers are unsecured
Tests show that software vulnerabilities and weak passwords are common in home routers, with up to 15% of them being unsecured.
The post At least 15% of home routers are unsecured appeared first on WeLiveSecurity.
![]()
Multiple vulnerabilities identified in Belkin router
An expert says that a popular Belkin router contains numerous vulnerabilities, making it extremely susceptible to attacks.
The post Multiple vulnerabilities identified in Belkin router appeared first on We Live Security.
![]()
Routers are set to become the digital battleground of the future
By now, most of us are familiar with the term the “Internet of Things”. It has come to describe the always on, always connected world where day to day objects are online. It ranges from smart-watches to smart fridges and is closer to reality than you may think.
Much has been written about the need to secure the devices that make up the Internet of Things, but I believe there is another battle to be won.
According to most reliable research, the number of Internet connected devices is growing rapidly and will continue to do so for the foreseeable future.
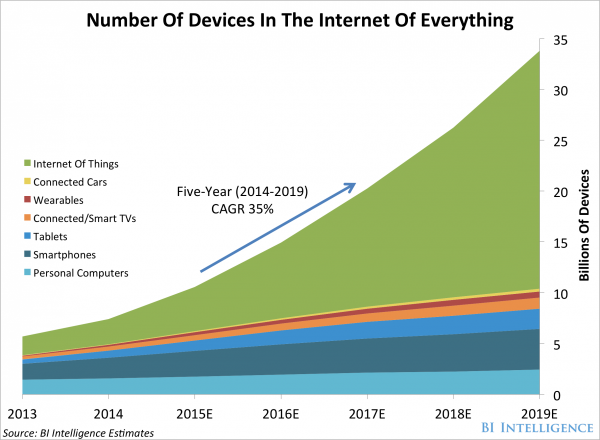
Building security into each and every one of these devices is no mean feat. In fact, it will be very difficult indeed. That’s what I believe that it is of vital importance that we focus our attention on securing routers and Wi-Fi hotspots.
As the number of Internet enabled devices in our homes continues to increase, more and more members of the public are getting ready to adopt smart home appliances, energy meters and wearables.

All of these newly connected devices entering the home should be rigorously secured as they will be handling data specific to your household. Securing them individually could be tough though, until you realise that they share something in common – they communicate via the Internet access point, a home router.
As you can see, the number of home routers in the market is continuing to grow rapidly, but is only a fraction of the number of total devices.

Robustly securing each home router or a public hotspot has the knock-on effect of securing the data transmission of dozens of devices and, for my money, is a much more realistic approach to securing the Internet of Things.
Sadly, security on most popular routers is still pretty basic and has a user experience to match. Clunky menus that aren’t immediately intuitive can leave users at a loss when it comes to making changes to their Internet settings.
Here are three simple things that you can do right now to help improve the security of your home Wi-Fi network.
Three steps to securing your home router:
Change the login details
Most routers will come with default login details. Many people never get round to changing them but you really should. “User name: admin Password: Password” is not a secure login and could potentially grant router level access to attackers if they know the manufacturer defaults of your device.
Set up an access list:
Most routers will allow you to set up a “permitted devices” list that limits access to your network. Setting this list up and including all your family’s devices is a good way to make sure that no unauthorized devices access your network.
Double check your Firewall
A Firewall is an important router feature that helps filter out bad traffic requests coming into your home. All traffic that is sent and received in your home goes through a Firewall and more specifically through “ports”. These are akin to doors, with each one dedicated to certain traffic types. It is always worth checking your Firewall settings in your router to make sure that you do not have any unnecessarily opened ports.
For tips on how to improve your home Wi-Fi Signal, check out the video below.
![]()
![]()
Are SOHO Routers A Hopeless Case?
I sure have one! It’s a nice little TP-Link, that’s doing what it’s supposed to do. Until now I felt pretty good and also kind of secure. Recently my feeling have changed though.
The Hungarian company Seach-Lab and some Spanish students, who are working at their master thesis, disclosed that there are quite a few SOHO routers (Small Office, Home Office routers) out there which are basically inviting cybercriminals to drop by and take a look at your data due to their vulnerabilities.
Search-Lab discovered 53 unique vulnerabilities on only 4 different D-Link devices, all running the latest firmware. According to their report “several vulnerabilities can be used by a remote attacker to execute arbitrary code and gain full control over the device”. They listed a few of the most critical findings’ problem areas in it as well so take a look at their paper if you want to know more.
The students published their findings on Full Disclosure and they lost more than 40 vulnerabilities in 22 different SOHO router models. The issues range from persistent and unauthenticated cross site scripting vulnerabilities and information leaks to Universal Plug and Play related vulnerabilities.
Routers which made it on the list are: Observa Telecom AW4062, RTA01N, Home Station BHS-RTA and VH4032N; Comtrend WAP-5813n, CT-5365, AR-5387un and 536+; Sagem LiveBox Pro 2 SP and Fast 1201; Huawei HG553 and HG556a; Amper Xavi 7968, 7968+ and ASL-26555; D-Link DSL-2750B and DIR-600; Belkin F5D7632-4; Linksys WRT54GL; Astoria ARV7510; Netgear CG3100D and Zyxel P 660HW-B1A.
Really, it doesn’t look good for SOHO router vendors. They either do not care or (even worse) do not know that their firmware is that insecure.
The post Are SOHO Routers A Hopeless Case? appeared first on Avira Blog.
Moose – the router worm with an appetite for social networks
A new worm is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The post Moose – the router worm with an appetite for social networks appeared first on We Live Security.
![]()
Avast Home Network Security is ideal for the self-employed

Don’t let your router be the weakest link when it comes to protecting your home business.
For those of us who are self-employed and/or work from home, our houses are sacred spaces on both personal and professional levels. Although often overlooked, our routers hold the key to our productivity, as they provide the powerful and consistent network connection that we depend on in order to get our work done. Unfortunately, we often take these little guys for granted, and because of this, routers have become the weakest security point in many home and small business networks these days.
“Unsecured routers create an easy entry point for hackers to attack millions of American home networks,” said Vince Steckler, chief executive officer of Avast. “If a router is not properly secured, cybercriminals can easily gain access to an individual’s personal information, including financial information, user names and passwords, photos, and browsing history.”
Securing your router is vital for both you and your business
You may have heard about the recent NetUSB driver flaw that made millions of routers vulnerable to malicious attacks. Unfortunately, this is just one case surrounded by the larger issue of users not taking the necessarily precautions to properly secure their home networks.
Avast now features Home Network Security (HNS), which scans for home router security problems. Avast is the only security company to offer a tool to help you secure this neglected area. Avast Home Network Security scans a user’s home network and routers for potential security issues that could allow a hacker attack. The scan looks for misconfigured Wi-Fi networks, exposes weak or default Wi-Fi passwords, vulnerable routers, compromised Internet connections, and enabled, but not protected, IPv6. It also lists all devices on the network so you can make sure only your known devices are connected.
In addition to protecting your devices using Avast Home Network Security, there several steps you can take in order to further improve your router’s security.
- Change the default admin username and password to a strong password. Do not use default passwords because they’re generated from well-known algorithms that makes hacker attacks even easier. Do not use your name, date of birth, home address or any personal information as the password.
- Turn off WPS, the automated network configuration method that makes your wireless password more vulnerable to hacker attacks.Turn on WPA2 encryption and, if you can, protect it with a strong password.
- Change the default admin username and password to a strong password. Do not use default passwords because they’re generated from well-known algorithms that makes hacker attacks even easier. Do not use your name, date of birth, home address or any personal information as the password.
- Upgrade your router firmware to fix known vulnerabilities of the router.
- Don’t forget to log out after managing the router, avoiding abuse of the authenticated browser sessions.
The Home Network Security Solution is available in free and paid versions of Avast. Get it at www.avast.com.
Follow @avast_antivirus
// <![CDATA[
!function(d,s,id){var js,fjs=d.getElementsByTagName(s)[0],p=/^http:/.test(d.location)?’http’:’https’;if(!d.getElementById(id)){js=d.createElement(s);js.id=id;js.src=p+’://platform.twitter.com/widgets.js’;fjs.parentNode.insertBefore(js,fjs);}}(document, ‘script’, ‘twitter-wjs’);
// ]]>



