
This week, every WhatsApp user experienced a pop-up message asking them to agree to the company’s new Terms and Privacy Policy. Those who just simply clicked on the green Agree button probably don’t have much of a clue as to what is going on.
![]()

This week, every WhatsApp user experienced a pop-up message asking them to agree to the company’s new Terms and Privacy Policy. Those who just simply clicked on the green Agree button probably don’t have much of a clue as to what is going on.
![]()
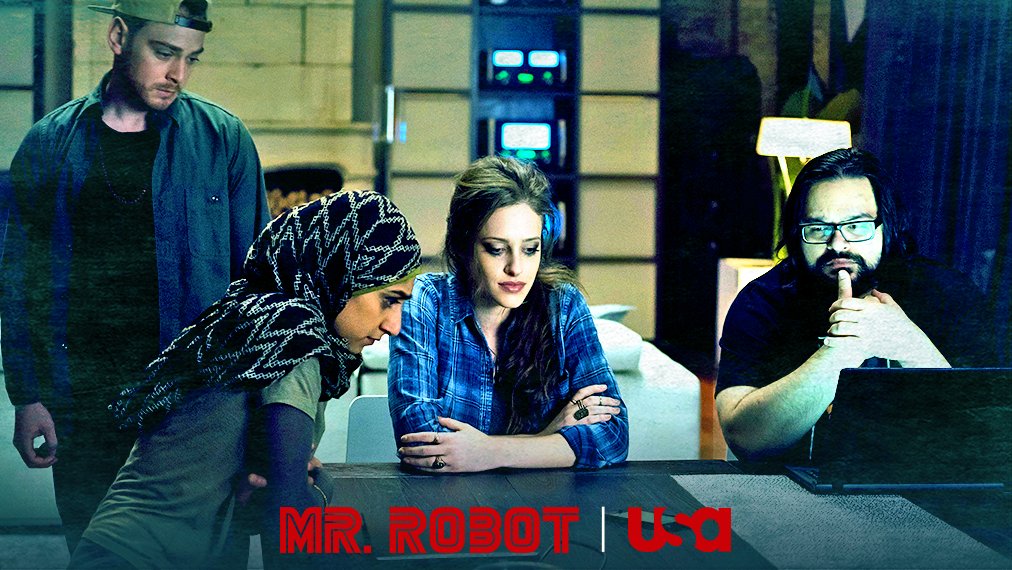
Image via: USA Network @whoismrrobot
Rami Malek must have been on vacation the week that this episode of Mr. Robot was filmed, since Elliot makes absolutely no appearances during the entire episode, not even via flashback. Darlene is very violent this episode, committing her first murder and then knocking her boyfriend Cisco out with a bat in the last scene!
![]()

The results of the July 2016 Whole Product Dynamic Real-World Protection Test from AV-Comparatives are in, and we’re excited to spread the word.
In describing its Real-World Protection Test, AV-Comparatives states the following on its website:
“Our Real-World Protection Test is currently the most comprehensive and complex test available, using a large number of test cases. This year, we are running this test under Microsoft Windows 7 Home Premium 64 Bit SP1 with up-to-date third-party software (such as Adobe Flash, Adobe Acrobat Reader, Java, etc.).“
![]()
This week’s episode of Mr. Robot had an usual start, more unusual than usual. The episode begins with Elliot, Darlene and their parents in a 90s style sitcom. ALF makes an appearance, yes you read correctly, ALF, and he even runs over and kills Gideon! Gideon is, of course, not Gideon in this 90s episode, instead he is a cop who is looking for a family that has a person locked up in their trunk. Elliot’s family is the family that has someone locked up in their trunk — Tyrell! Vulture wrote a nice article explaining how this scene came to be and how this was Mr. Robot’s way of distracting Elliot from all of the pain he is in in real life.
![]()
 Avast Threat Lab uses CyberCapture to detect unknown malware
Avast Threat Lab uses CyberCapture to detect unknown malwareOur Avast Threat Lab is Grand Central Station to malware. Somewhere between 600,000 and 1 million files come through the detection system every day. Nearly half of those are unknown files. That means that somewhere in the world, someone is targeted by cybercriminals. Avast Threat Lab analysts like Michal Salat, in the above picture, works to stop those attacks.
![]()
Finally! Elliot is back to his old ways, hacking and being a vigilante.
![]()

AV-Comparatives have released their 2016 Mac Security Test & Review, which focuses primarily on the security of Mac systems. When describing the significance behind the report, AV-Comparatives says:
“. . . it is necessary to understand that a computer virus is only one of a number of different types of malware (malicious software). These days, viruses make up a small percentage of all known malware; Trojans (malicious programs disguised as e.g. games or music files) are much more common. Whilst the number of actual viruses affecting Mac OS X may be negligible or even zero, Mac systems clearly can be infected by Trojans, if users are fooled into installing them.“
![]()

Image via: USA Network @whoismrrobot
Like last week’s episode, this week’s episode of Mr. Robot began with a flashback, providing us with more background on how fsociety was formed. In the flashback scene, Darlene visits Elliot at his apartment on Halloween. She is wearing the fsociety mask, which we learn is from the fictional movie Careful Massacre of the Bourgeoisie. We also see how Elliot first told Darlene about his master plan of hacking and taking down E Corp.
![]()

Many of you have likely been keeping up with recent news about the resignation of Democratic National Committee chairwoman Debbie Wasserman Schultz following a large email leak from WikiLeaks. An article from ZDNet summarizes the event in the following statement:
“The leak from WikiLeaks on Friday included 19,000 emails in a searchable database. Some alleged emails sent from the accounts of Democratic National Committee officials were trying to weaken [Bernie] Sander’s campaign for the nomination, with one thread even targeting his religion.”
![]()
The Olympic torch is making its way to Rio as the 2016 summer Olympics are set to begin on August 5th. The excitement is building and many are anxious to see the 306 events, which will take place across 37 different venues. The athletes, however, aren’t the only ones who have been working hard for the Olympics. Cybercriminals have also been preparing for the games and their ultimate reward is your data and money!
![]()