The marketplace for browser extensions is quite big. With Firefox alone, there have been more than four billion add-ons downloaded. But not every extension makes the user happy:
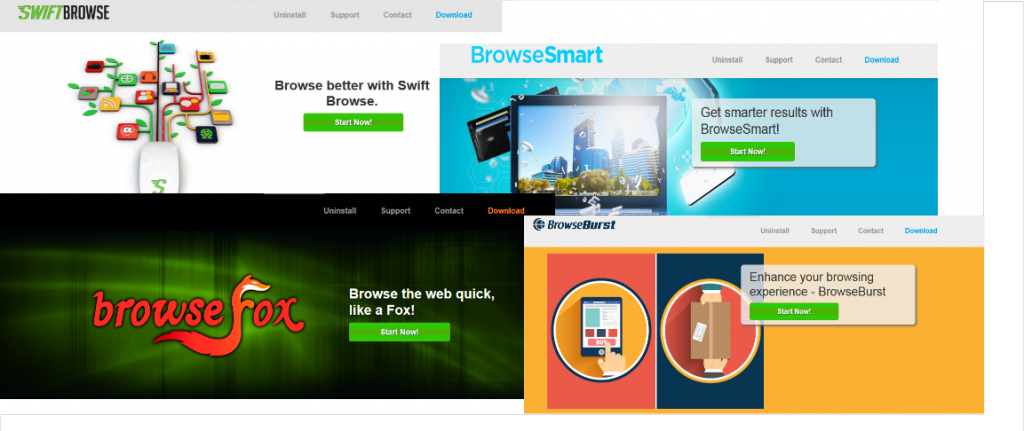
In the last couple weeks, we monitored rampant spreading of browser extensions with new machinery for harming the user – via the publishing of unwanted advertisements. The list of names of such extensions is long: Browsefox, Swiftbrowse, Betterbrowse, Browsesmart, Browseburst… All share the same two major traits: They user doesn’t want them, and they are hard to remove from the computer.
Of course, we’ve had our attention on this kind of browser extension, with the aim to protect and warn Avira customers about it. We tracked the extensions’ speed of global growth, created specific Avira Intelligent Repair System (AIRS) routines, and adjusted our engine detection to detect these types of unwanted browser extensions.
Finally, with the engine detection pattern “Adware/Browsefox.Gen,†included in Avira version 8.3.24.22, we took the first step forward.
And the first results are incredible:
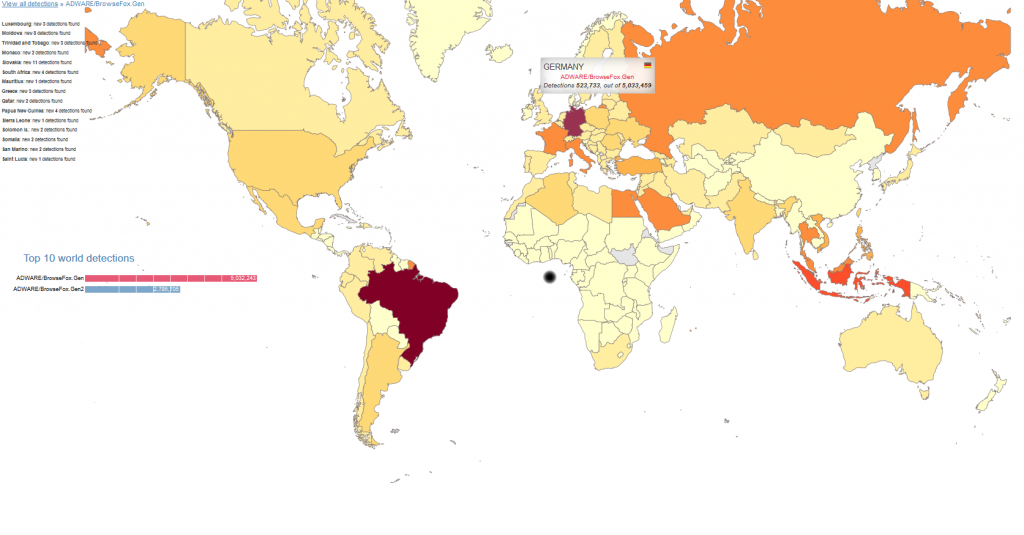
Since the release of the engine version, we were able to recognize more than 20 million detections in the ‘Avira World’. And regarding the spreading of these extensions: During our initial research, we noticed extreme propagation for the browser extension in Germany. But after the release of the generic detection, we saw that even more regions in the world have these unwanted extensions installed. Now, we can see better their global movement.
But what exactly are these browser extensions doing on your computer? Their primary goal is to make money. And, as mentioned, their means of doing such is, after the installation, to publish unwanted advertisements on your computer. For example, it will show coupons with their offers. And this is exactly their means of earning money. With each additional advertisement, the cash flows.
The list of names using this tactic is long. Very long. But if you take a look at some of their “official†websites, you will see that they are all related. They share the same style and options. Only the name of the product changes, along with different photos…
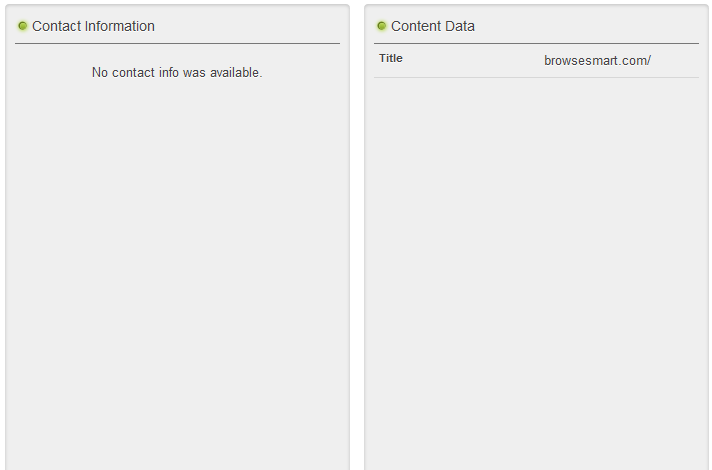
Also interesting is the word ‘official’. We tried to find out the official company or person behind these sites, but there is no official contact information.
How would you get this extension? It would most likely be installed as a third-party software in other setups. For example, if you are looking for a new Internet Browser, search for it in your search engine of choice and pick the first offer – you will get an installer and won´t recognize that this installer was not from an official website. When starting the browser installation process, the extension will also be installed – silently. The behavior of these components is typically the same. They create new folders on your computer in the following directories. Here is one example with the extension ‘BrowseBurst’:
%PROGRAM FILES%BrowseBurst
bin
utilBrowseBurst.exe
BrowseBurst.BrowserAdapter.exe
FilterApp_C64.exe
BrowseBurst.PurBrowse64.exe
BrowseBurst.PurBrowse.exe
BrowseBurst
updater.exe
On the registry, there are some changes made by installing the extension:
HKLMSoftwareBrowseBurst
HKLMSoftwareWow6432NodeBrowseBurst
HKLMSoftwareMicrosoftInternet ExplorerApproved Extensions
Value: %CLSID%
HKLMSoftwareMicrosoftWindowsCurrentVersionexplorerBrowser Helper Objects{%CLSID%}
HKLMSoftwareMicrosoftWindowsCurrentVersionUninstallBrowseBurst
HKLM SYSTEMCurrentControlSetservices%ExtensionName%
The extension may contain options (Browser Helper Object) that the extension will load into the memory all the time. This is why the combination of detection and repair routine by AIRS is so important.
If you like to know more details about the extensions’ behaviors, our virus researchers have created a detailed description:
Adware/Browsefox.Gen: http://www.avira.com/en/support-threats-summary/tid/8495/tlang/en
The post Browser Extensions that nobody wants… but a lot of people have! appeared first on Avira Blog.