What are web advertisements?
One basic premise of an advertisement is that its publisher has an adequate user base to be influential. The advertiser can be trying to get his new product out to the customer. Combine both, put it into the context of modern technology like the WWW, and big new opportunities emerge from the statically dull-looking world of HTMLs.
In most cases, advertisements are delivered through a dedicated server, the ad server. This makes it easy for the publisher to manage. All that needs to be done is to specify where the content is fetched from, the rest is taken care of by the advertising company. The latter is now able to fine-tune ads, for example via copy and design changes, to squeeze out the maximum click and conversion rates possible. Typical options for which ads can be tailored might include:
- Browser used by the visitor
- Browser language the visitor has set as default
- Country, state, city the visitor resides in
- Operating system the visitor uses
- Plugins the user has installed (Java, Adobe Flash and Reader, Quicktime and many more)
- Which page the visitor comes from
- Screen resolution
This vast potential can take somewhat weird forms. Kogan Technologies, an Australia-based consumer electronics retailer, introduced the “Internet Explorer 7 Tax†which charged online shoppers with an extra 6.8% for using that browser.² Furthermore, Orbitz, an online travel planning website, has chosen to show pricier hotels to Apple Macintosh users.³
Can these ads be malicious?
This also builds the foundation for distributing malicious content. While the method of propagation is the same as with legit ads, content mostly consists of harmful JavaScript snippets. These scripts reload more scripts or simply redirect the visitor to infected web pages without user interaction – meaning: you will not feel a thing until it is too late.
Keeping in mind the options that advertisement agencies have, this opens another door. Phishing sites can be shown in the browser’s native language. Exploits and other malware can be downloaded, depending on the software installed on the victim’s computer. We have seen these types of “malvertising†sites loading malicious code during prime time – directly after the evening news. In the end, it showed that people tend to watch free online movies (often illegally) during prime time rather than during the work day.
How so, please give me an example?
So, say it’s a ridiculously hot summer. You look for… an anti-perspirant by your favorite sports brand. You feed the search engine with the right terms and find a promising page on Amazon. Of course, the idea of malware striking at this moment does not even cross your mind – why would it? You click the link; bam! Now, your computer might be infected. Seems unrealistic? Too paranoid? Well, it is not.
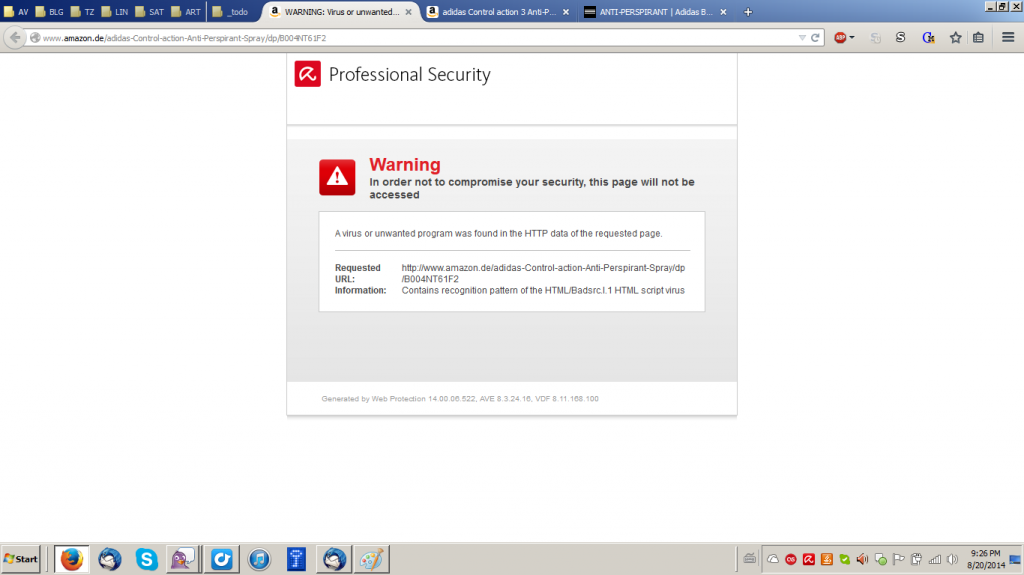
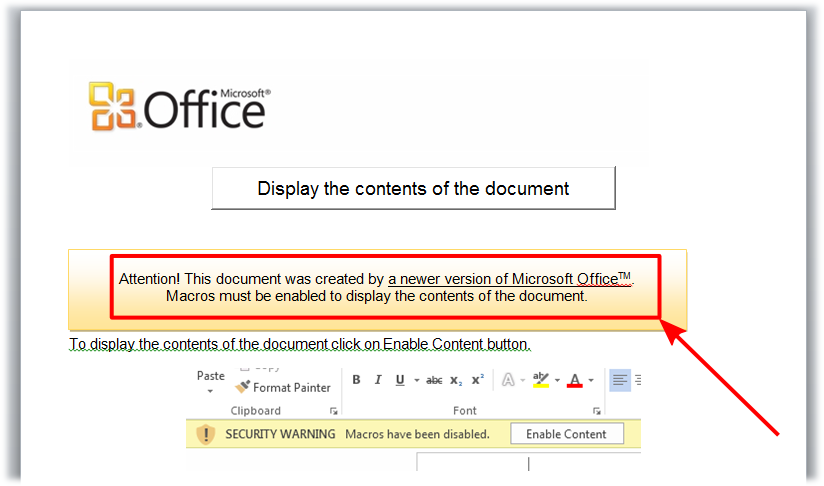
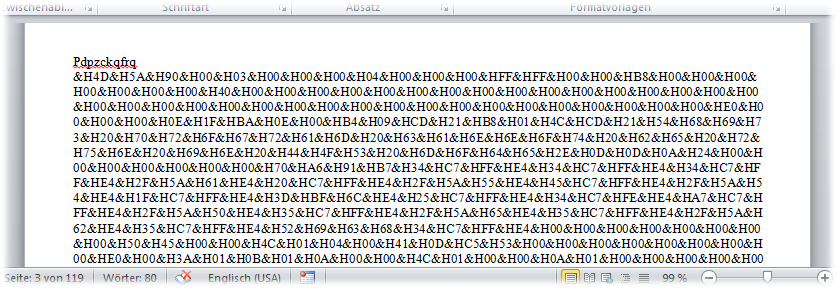
Some weeks ago, while I was on my couch and browsing the web, this exact thing happened to me. Analyzing the sample and the signature (HTML/Badsrc.I.1) brought me to the conclusion that this definitely was no false alarm. What happened is that the advertising agency Amazon used for this particular page was delivering malicious content (Note that it is not Amazon themselves delivering the malware). The difference, for an Avira user at least, is this:
So, can your computer be infected by browsing legit and trusted websites? Yes!
How can I protect myself?
The example above shows that being careful on the web and visiting only legit and well-known websites does not mean you cannot get infected with malware. Web advertisements have a right to exist, no doubt. Just to be on the safe side, basic malware protection should always be complemented with sophisticated URL detection and ad tracker blocking. Avira Browser Safety gives the security-concerned user just what is necessary to live free. It is able to detect malicious URLs using Avira’s globally distributed URL Cloud but will also keep pesky and harmful online ads away from you. Why not give it a try?
¹ TechChrunch: Internet Ad Spend To Reach $121B In 2014 […]
² Kogan: New Internet Explorer 7 Tax ![]()
³ The Wall Street Journal: On Orbitz, Mac Users Steered to Pricier Hotels
The post Why blocking advertisements matters appeared first on Avira Blog.


 O
O