A pair of modules included in the Drupal content management system have been updated to fix access bypass vulnerabilities that could allow an attacker to take actions on the behalf of some users. One of the modules fixed is the Twitter module, which allows users to take a variety of actions, including pulling in public […]
Tag Archives: Twitter
Customers of UK’s Metro Bank targeted by Twitter fraudsters
Be on the lookout for copycat social media accounts which may be attempting to lead your customers astray.
The post Customers of UK’s Metro Bank targeted by Twitter fraudsters appeared first on We Live Security.
![]()
Threatpost News Wrap, August 28, 2015
Dennis Fisher and Mike Mimoso discuss the quasi-interesting fallout from the Ashley Madison hack, the appeals court decision about the Wyndham data breaches, and Charlie Miller leaving Twitter.
Charlie Miller to Leave Twitter Security Team
Charlie Miller, one of the more respected and accomplished security researchers in the industry, is leaving Twitter’s security team after three years. Miller said on Monday that he is leaving the company at the end of this week and that he plans to announce his new job next week. Miller joined Twitter in 2012, shortly […]
Twitter Adds Email Privacy Data to Transparency Report
The number of information requests Twitter is receiving from the United States government is increasing steadily, having risen roughly 50 percent in the first six months of this year compared to the last six months of 2014. In its latest transparency report, Twitter said that it received 2,436 information requests from the U.S. government from […]
New Hammertoss Espionage Tool Tied to MiniDuke Gang
Hammertoss, a backdoor uncovered by researchers at FireEye, combines many previous communication venues used by APT29, a espionage outfit linked to the Russian government.
Trolls on Twitter. How to avoid them

“We suck at dealing with abuse and trolls on the platform”, said Dick Costolo, former CEO of Twitter, as he stepped down July 1, at the beginning of the year. This statement showed what any user of the social network already new: that Twitter regrettably fails to control harassment.
A recent study carried out by Pew Research Center showed that 40% of the Internet users surveyed claimed to have been victims of cyber harassment. That’s why, one of the purposes of the social network is implementing the necessary tools so that the users do not suffer the abuses of those who are hiding behind anonymity to insult and attack others.
The most recent attempt from Twitter to minimize its impact was allowing users to share with their friends their lists of blocked tweeters. Thus, you can already block several trolls at the same time. Mass-blocking.
“You can now export and share your block lists with people in your community facing similar issues or import another user’s list into your own account and block multiple accounts all at once, instead of blocking them individually”, explained from the social network’s blog.
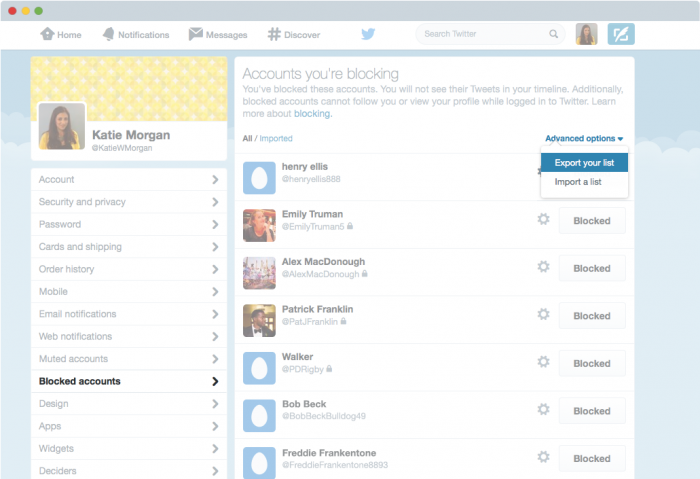
To use this new feature to import and export lists of blocked users, tweeters who want to avoid harassment on Twitter just need to follow a few simple steps, starting from the ‘Blocked accounts‘ section of the settings on Twitter:
How to export a block list on Twitter
- In the ‘blocked accounts settings’, click on ‘advanced options’ and select ‘export your list’.
- Twitter will ask you to confirm which accounts you want to export. In this intermediate step, you have two options: select all the accounts that you have blocked with a single click or uncheck those that you don’t want to share.
- Once you have selected the accounts that you want to incorporate to the file, click ‘Export’. It will generate a .csv file that will be downloaded automatically on your computer and which you can share with who you want.
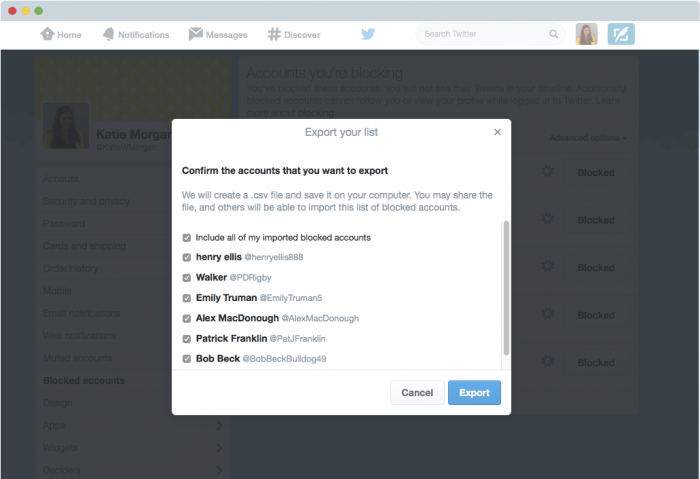
How to import a block list on Twitter
- Before starting, you must have received from a contact the .csv file corresponding to their list of blocked accounts on Twitter.
- With the file already downloaded on your computer, go to ‘advanced options’, in the ‘blocked accounts settings’, and there select ‘Import a List’.
- In the pop-up, click on the paperclip icon on the option ‘attach a file’ to upload it. From there, you must select the .csv file you had downloaded.
- It will display the list of accounts blocked by your twitter friend that shared the file with you. It will be then when you will have to select if you want to block the whole list (with just one click) or if you prefer to give some of them a chance. To do so, you will have to uncheck those accounts which you don’t want to block.
- Click on ‘Block’ to confirm your selection and automatically, the marked accounts on that list will no longer be among the potential stalkers who someday may decide to attack you on Twitter.
With these simple tools, the lists of blocked users will be shared very easily, so that Twitter users may clip with hardy any effort the wings of several trolls simultaneously (and by recommendation the contact who has shared with us his list).
The post Trolls on Twitter. How to avoid them appeared first on MediaCenter Panda Security.
EFF Privacy Report 2015: Which Companies Have Your Back?
On Wednesday the EFF published their yearly report called “Who Has Your Back? 2015: Protecting Your Data From Government Requests”. It answers important questions like which companies follow industry-accepted best practices, tell their users about government data demands, disclose policies on data retention or government content removal request, and oppose backdoors.
For the EFF report 24 companies are evaluated and being awarded (or not awarded, depending on the outcome) stars in the five categories mentioned above. Nine companies managed to get stars in all of them: Adobe, Apple, CREDO, Dropbox, Sonic, Wickr, Wikimedia, WordPress.com, and Yahoo.
Facebook and Twitter received four out of five stars, with Facebook “not providing transparency into ways it cooperates with the U.S. government to block content and remove accounts” and Twitter „not providing notice after an emergency has ended or a gag has been lifted”.
The worst rating with only one star went to WhatsApp who at least opposes backdoors but seems lacking in all other privacy regards. The EFF recommends WhatsApp to “publicly require a warrant before turning over user content, publish a law enforcement guide and transparency report, have a stronger policy of informing users of government requests, and disclose its data retention policies.”
Take a look at the full report to find out more.
The post EFF Privacy Report 2015: Which Companies Have Your Back? appeared first on Avira Blog.
Some GTA V Mods Serve You Malware
What it’s all about
aboutseven, a newly registered member on the GTA forums, was the first one to notice that all was not well with the processes running on his computer. “I came across something pretty startling today after reviewing my processes that were running on my computer. I tend to do this a lot out of paranoia, just checking that I don’t have stuff running in the background that I don’t want running, or if I ever possibly run into something that is out of the ordinary that could possibly be malware. I happened to notice that the Windows C# compiler running the background as csc.exe”, he wrote in his post.
After looking into it some more he dredged up a file called Fade.exe, which hijacked a part of the registry in order to being launched at boot. Some more testing revealed that a GTA mod named Angry Planes was to be held responsible for the malware landing on his system. Since the discovery, other players are claiming they’re finding similar harmful files on other mods as well, such as No Clip.
What it does
So, why exactly is Fade.exe such a problem? To answer the question, let’s just take a look at the modules that are loaded with the mod, according to another forum user named ckck:
- “Facebook spam/credential stealing module
- Twitch spam/credential stealing module
- com spam/credential stealing module
- A Steam spamming module
- A Steam module that evaluates the items in your inventory and their value based on current market value
- A Keylogger module that logs individual button presses in an XML like format, it also includes information about context switches (switching from one app/window to another)
- A UDP flooding module
- I hadn’t deciphered and didn’t see in action.”
What you can do
In case you have one of the mods installed, make sure to scan your computer with your AV and remove the malicious files. Keeping in mind that Fade.exe also sniffs around your Facebook, Steam, and Twitch accounts, make sure to change all your passwords as well.
The post Some GTA V Mods Serve You Malware appeared first on Avira Blog.
This is how Facebook, Twitter or LinkedIn fight to protect your security

Probably when you were reading about the privacy policy on Facebook or Twitter, you skipped the part of ‘how to protect yourself from cyber attackers’. Each time you download a new application you agree to its terms and conditions, and we are sure that you don’t stop to read them and never worry about how the applications manage your sensitive information.
Social networks strive to inform you on how they protect your information and what can you do to contribute to this task. That’s why they offer the information in the most understandable possible way.
Facebook the most complete
Facebook just had its guide to security redesigned and in the ‘How to Keep Your Account Secure’ section offers new recommendations on how to prevent cyber-attacks through interactive graphics. And to assure everyone can read these tips, they are available in 40 languages and you can share them on your profile.
The recommendations “focus on the tools we make available to help you secure your account, the steps we take to keep your information secure, and the ways you can recognize and avoid attempts to compromise your information” explained Melissa Luu-Van, product manager at Facebook. Van-Luu added in the same post that already millions of people have read the new privacy settings launched last November.

Click on ‘help’ if you think your account might have been taken over by someone else, explain you that you have to log out if you are not using your habitual computer or inform you that you can report suspicious profiles and posts are some of the features included in the new security collection.
The guide also warns you of the possibility of a phishing attack. Facebook will never send you an email asking for your password, so if you ever receive an ‘email’ requesting this information could come from a cyber-attacker who created a fake web site to steal your information.
LinkedIn the less organized
Facebook isn’t the only social network which has improved its security information recently. LinkedIn has also a new ‘Security Blog’ with helpful guidelines. “We’ll use this site to share some of our security research, whitepapers on how we handle data and the security features and diligence we’ve built into our products. If you are responsible for information security at an enterprise that uses LinkedIn’s products” says Cory Scott, LinkedIn’s Information Security Director.
This professional network explains how your information is used and protected. For example, inform that they can hire third party companies to provide their services with limited access to your information. In addition its support center offers advice on how to better protect your account: changing your password regularly, check the privacy settings or activate the two-step verification to prevent phishing attacks, that many users have suffered in the last few months. Nevertheless, this information is less organized than in Facebook, so you will have to dive deeper to find what you want.
Twitter the one that offers personal tips
Twitter also wants to show you its way of protecting your information. If you are interested to know more details, in their help center there is a wide security and protection section, you can access it from the tab of ‘help and support’ in your profile.

Here you can find out some tips on how to maintain secure account (similar to other social networks), or how to inform Twitter if you find your account has been violated. The company pays special attention to cyberbullying and includes custom security tips for teens, parents and teachers.
What about Google?
But not only social networks detail their security policy; google has been doing it for a while. A complete manual is included in the web ‘How to stay safe and secure online’ where explains how to prevent cyber-attacks protecting your passwords, checking your Gmail’s settings or verifying the emails’ sender if you think it might be a scam.
You can also dig through all the security and privacy tools offered, like two-step verification or who to browse through Chrome without your computer recording it in your browsing history.
So, if you ever wonder how the services you trust every day protect your information against cyber-attacks now you have no excuse, the answer is here!
The post This is how Facebook, Twitter or LinkedIn fight to protect your security appeared first on MediaCenter Panda Security.