When we asked AVG Business customers in the US and UK how they keep company passwords safe, we were surprised to learn just how many of them … simply don’t.
Hundreds of millions of employees worldwide use passwords multiple times every day to access business resources ranging from email and domain management to banking and accountancy. These passwords—strings of letters, numbers, and symbols used to validate access—are one of your business’s primary ways to protect vital resources. But what is your business doing to protect them?
In June, AVG surveyed businesses about their password-protection policies and practices. 381 of our small-to-medium business (SMB) customers in the US and UK answered 16 questions, and here are some of the things we discovered from their answers:
- A third of respondents believe their company’s passwords could be more secure.
- 72% believe their workplace passwords are stored in a safe place.
- 22% of businesses use password management software.
- Four out of ten people use the same passwords for different business log-ins.
- 50% of people use between 1 and 10 passwords to access different networks, software, and accounts.
- A quarter of participants use two-factor authentication for their passwords.
- 67% claimed there are 1-2 people who have access to their company passwords.
- 43% of people with access to company passwords don’t have a clause in their contract to keep these passwords confidential.
- 51% of employees save all or some of their passwords through their web browser.
- For one-third of businesses, the owner, president, or MD is responsible for managing company passwords.
- 16% of non-employees (contractors, freelancers, temps) can access company passwords.
- 19% of people surveyed said their business uses an automated password generator.
- 68% of people surveyed say they have heard of the term ‘ransomware.’
The results in full
Password Security
A third of participants believe their company’s passwords could be more secure.
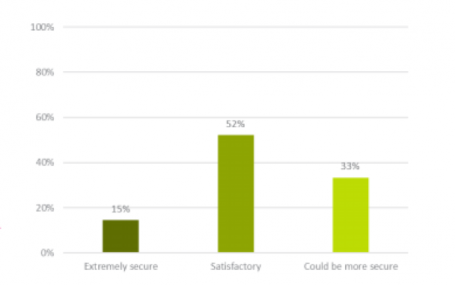
This result isn’t too surprising, considering the most-used passwords in 2015 were ‘123456’ and, you guessed it, ‘password.’
Password Storage
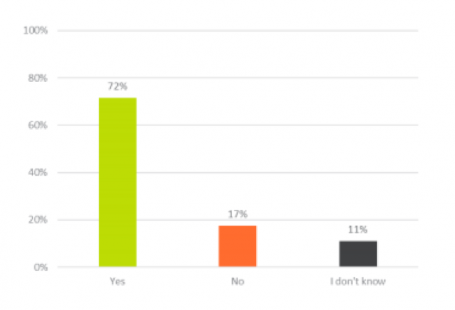
72% believe their workplace passwords are stored in a safe place (i.e. not accessible by unauthorized personnel).
22% of businesses use password management software.
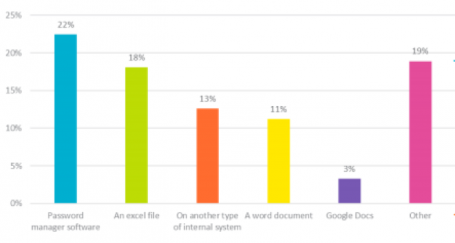
Small businesses can benefit from using a tool allowing them to securely manage several different accounts simultaneously and store all company passwords in one place. Or a user authentication service, such as AVG Single Sign-On (SSO), lets users employ a single set of log-in credentials—with a two-factor authentication option—to access multiple applications.
Logging in
Four out of ten people use the same passwords for different business log-ins.
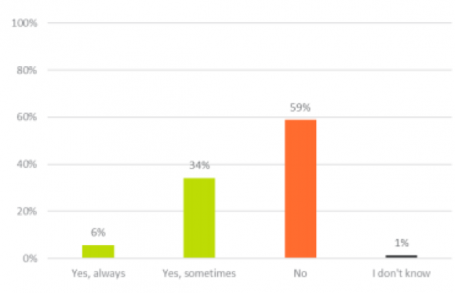
Using one password for multiple services may feel like a time-saver, but it weakens the gateway to your business, data, customers, and potentially your identity. So just imagine if this one password got into the wrong hands. We recommend giving each employee their own password and account, to ensure accountability and improve security.
50% of people use between 1 and 10 passwords to access different networks, software, and accounts.
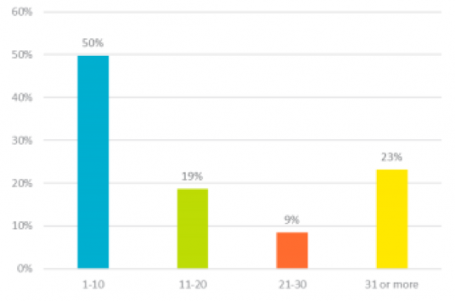
Small businesses often use so few passwords because they have a small domain, which combines sign-on for email, network and, other linked services. However, whatever the number of passwords a business uses, they must always:
- store them somewhere safe,
- control who has access to them, and
- ensure the passwords are strong, i.e. contain caps, numbers and symbols.
A quarter of participants use two-factor authentication for their passwords.
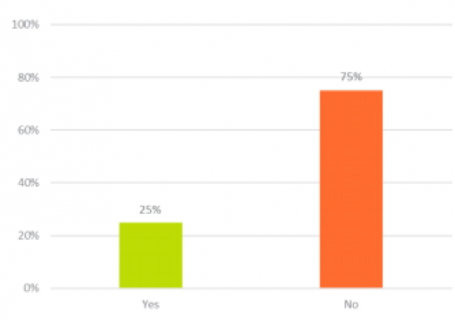
More and more big brands such as Apple, Twitter, and Evernote have introduced the two-factor authentication option, which confirms user identity through a combination of something you have (e.g. an ATM card) and something you know (e.g. your ATM PIN).
Password Access
67% claimed there are 1-2 people who have access to their company passwords.
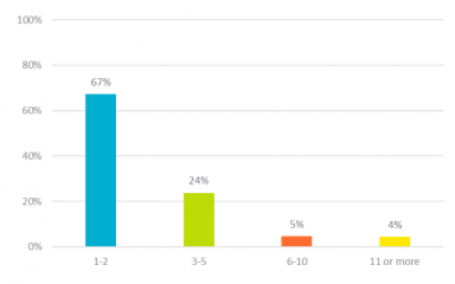
IBM’s 2014 Cyber Security Intelligence Index showed 95% of all security incidents involved human error. Successful security attacks happen when human weakness is exploited to lure a company’s employees to unwittingly provide access to sensitive information.
43% of people with access to company passwords don’t have a clause in their contract to keep these passwords confidential.
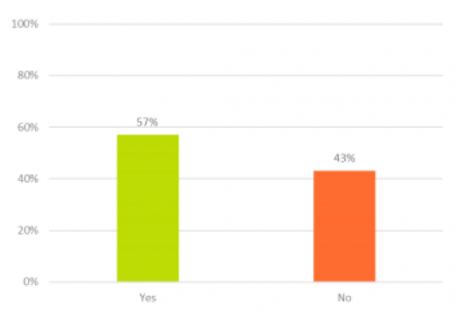
Including a confidentiality clause in every employee or third-party contract is an additional—and necessary—layer of protection for your business.
51% of employees save all or some of their passwords through their web browser.
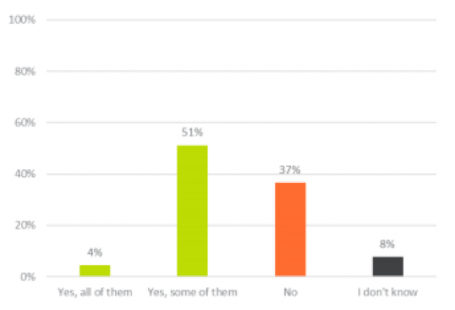
Using a web browser to remember your password is convenient, but poses a security risk. How big a risk depends on whether you sync with other devices, what browser you use, and how many people have access to your business computer(s) using the same profile. Next time your web browser asks to save your password, reconsider, and select “Never for this site.”
For one-third of businesses, the owner, president, or MD is responsible for managing company passwords.
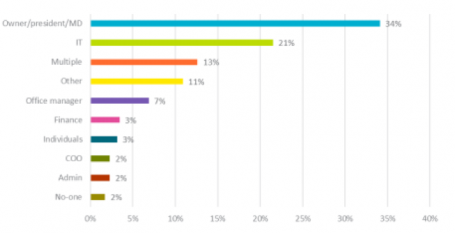
When it comes to IT security, small businesses are in a tight spot, because they’re heavily dependent on computers, yet not large enough to have a dedicated IT staff member. So often the owner, president, or MD becomes the closest thing a company has to an infosec expert. As a business grows, so will the IT infrastructure, at which point dedicated personnel should take responsibility for managing company passwords.
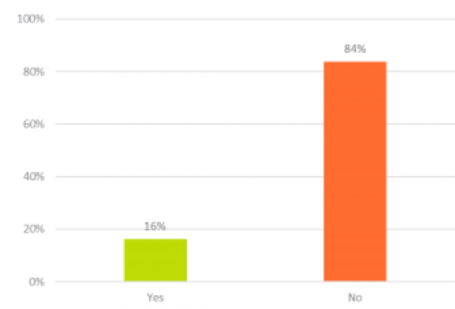
16% of non-employees (contractors, freelancers, temps) can access company passwords.
For the most part we know and trust our colleagues, so granting system access to full-time employees makes sense. But what about for short-term projects involving a contractor with understandably less of a commitment to the company? Should you really share passwords with these staff? The best solution, if access is essential, is to create temporary log-ins, which you can delete when temporary employees leave. Otherwise, you’re left having to change the password for everyone … or be comfortable leaving it alone, knowing someone who’s left the company technically still has access. And in case it’s not clear, we don’t recommend you ever do this.
For the most part we know and trust our colleagues, so granting system access to full-time employees makes sense. But what about for short-term projects involving a contractor with understandably less of a commitment to the company? Should you really share passwords with these staff? The best solution, if access is essential, is to create temporary log-ins, which you can delete when temporary employees leave. Otherwise, you’re left having to change passwords for everyone … or be comfortable leaving passwords alone, knowing someone who’s left the company technically still has access. And in case it’s not clear, we don’t recommend you ever do this.
Password Generation
19% of people surveyed said their business uses an automated password generator.
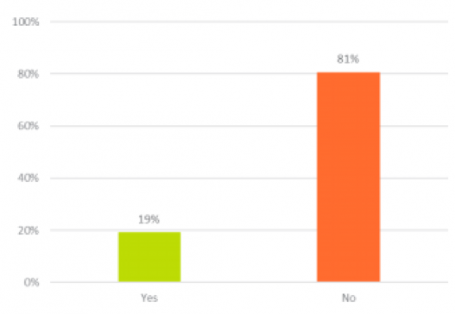
The best, easiest way to create strong passwords is to use a password generator.
Ransomware
68% of people surveyed say they have heard of the term ‘ransomware.’
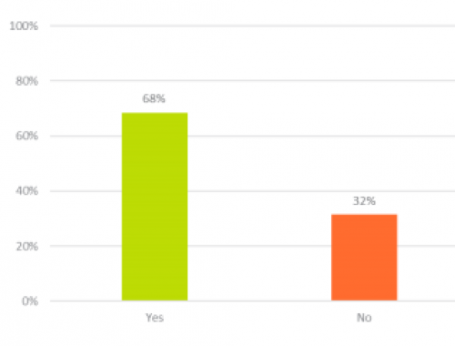
However, 36% (101 out of 277) of those who thought they knew what ransomware is actually didn’t.
Ransomware is malware that encrypts your files, then demands payment—often with a time limit—before decrypting them. Not only does ransomware target your most valuable files, it can lock down system files to render your web browser, applications, and entire operating system unusable.
So what do businesses need to know? And what can you do?
Experts warn that small businesses are fast becoming cybercriminals’ favorite target—and those businesses are quite often woefully unprepared. Cybercriminals know that SMBs can be an easy path to a much bigger target, that is your customers and partners. Many breaches could have been prevented with robust employee and contractor education, more stringent password policies, and the use of two-factor authentication.
In 2015, US businesses saw an average 160 successful cyberattacks per week, more than times the 2010 weekly average. Cybercrime globally cost businesses $400-$500 billion last year, and the estimate for 2016 is $2-3 trillion.
In the UK, the latest Government Security Breaches Survey found that nearly three quarters (74%) of small businesses reported a security breach in the last year, an increase from both 2013 and 2014. And the cost of each breach was £75,000-310,800, with 31% being staff-related.
Ultimately, you cannot take it for granted that your employees or colleagues have the tools and knowledge to make the necessary decisions to keep the business secure. But by implementing sound policies and proven practices, you can equip yourself and everyone in your business to be part of protecting it.
And when it comes to IT security and password policies, never, ever, ever underestimate hackers. Where data could be stolen or money could be made, cybercriminals will persist until they find a vulnerability they can exploit. Your password policy is your key to the kingdom, so guard it accordingly.















