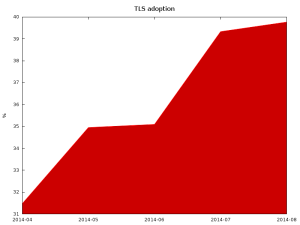
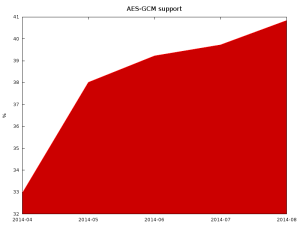
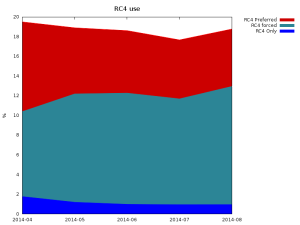
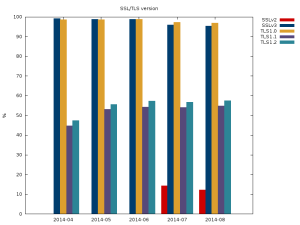Celebgate, the leaking of nude photos of celebrities from iCloud that started in August, continues to make headlines but now has competition from another big cybercrime story. The compromise of payment card data at Home Depot is emerging under headlines that make comparisons with another huge retail breach, as in: “bigger than Target?†What’s the connection between the sleazy creeps who hack private online storage accounts to share the contents thereof and folks who hack into point-of-sale systems to steal and sell payment card data? They are all criminals, a fact that is too often overlooked in the angry aftermath of the data breach du jour.
Blaming Cybercrime Victims
As the Celebgate story was emerging I received an interview request from a journalist with the Hungarian edition of CHIP magazine. His first question was: “Who’s responsible for the latest Apple iCloud ‘celebrity nude pictures leak’ scandal and why?†My response went something like this: The correct answer to this question is people, not technology. I continued:
The creepy people who stole the pictures are the ones responsible for this scandal and they should be held accountable. For some strange reason, the world tends to approach computer security differently from physical security. If you forget to lock your car, that does not make you responsible for it being stolen. The car thief is clearly the only person truly responsible. To think that any party other than the sleazy criminals who exposed private information is responsible is to condone their actions.
I was not just saying this to differentiate my analysis from that of actress and Celebgate victim Kirsten Dunst. I’m sure most people have seen headlines like this: “Kirsten Dunst Slams Apple After Alleged Nude Photo Leak: blames iCloud for photo hacking†(Hollywood Life). Much as I admire Ms. Dunst as an actress and sympathize with her entirely justified outrage at this incident, I don’t agree that Apple is to blame, any more than I would blame BMW if my car was stolen. Of course, any company whose business model involves handling sensitive private information has a responsibility to protect it. But persons who work to defeat those protections and then violate the privacy of that information are, in that case, the persons to blame, the responsible party. We must not forget that Target and Home Depot are victims of cybercrime, just as Ms. Dunst and other celebrities whose private photos were exposed are victims of cybercrime, whatever the passwords protecting their accounts happened to be.
To think that any party other than the sleazy criminals who exposed private information is responsible is to condone their actions. I say this because to say otherwise is to go down a road best avoided. Consider Apple’s reaction to Celebgate: they have instituted improved security measures. What if we fast forward 12 months and hear that, once again, a determined group of sick-minded perverts has defeated those enhanced security measures and exposed another batch of private pictures. Is Apple still responsible? Before you answer, let’s consider the Home Depot hack. Reports so far indicate that the criminals used an enhanced version of the malware deployed to steal tens of millions of payment card records from Target stores. The response from Target includes a commitment to use EMV cards in the future. EMV cards contain a chip and are much harder for criminals to replicate, making the conversion of stolen card data into cash more challenging. But notice that I’m saying “harder, more challenging†but not impossible.
In other words, unless human nature experiences a sudden and unprecedented global upgrade, some people somewhere will always be trying to defeat security measures for their own ends. A certain number will always succeed, so the trick is to reduce that number. And that is why societies put in place policies and allocate resources to deter criminal activity, notably through the detection, identification, apprehension, prosecution, and punishment of persons deemed to be criminal perpetrators. If any party other than the criminals is to blame for Celebgate and the Target and Home Depot hacks I would say it is society for failing to devote enough resources to the deterrence of cybercrime.
Cybercrime and Society
Sure, many companies and consumers could do a better job of protecting the information systems they use, from changing the default password on point of sale devices, to using stronger passwords on our accounts than 123456 (which recently replaced password as the most widely used password, according to an analysis of millions of compromised records – see this paper on password advice to choose something better).
In recent years a lot of useful advice on how to improve our digital security has been made freely available. The federal government publishes a wide range of guides to best practices, including the comprehensive Framework for Improving Critical Infrastructure Cybersecurity from NIST (the National institute of Standards and Technology).
So why don’t more organizations do a better job at security? There are many reasons, cost being the most obvious, but failing to fit your front door with an expensive pick-proof lock does not make you responsible for a burglary or home invasion; there seems to be broad consensus that responsibility for those crimes rests with any criminal who chooses to violate your physical space. Violations of private virtual space should be considered equally criminal, and violators should be vigorously pursued.
America has well-established measures in place for responding to such physical crimes, from tracking down the perpetrators to arresting, prosecuting, and punishing them. And America’s efforts to deter traditional physical crime appear to be effective when you look at the number of bank robberies each year and the average amount of loot they yield. Both numbers are gradually declining: from 7,644 incidents yielding an average of $10,000 in 2003 to 5,086 incidents yielding $7,539 in 2011 (based on FBI reporting).
When it comes to computer fraud, the graph is a steep line going in the opposite direction: up from $125 million in 2003 to $781 million in 2013 (based on Internet Crime Complaint Center reporting, in conjunction with the FBI). So where is the effort to deter cybercrime? And where is it located on the list of national priorities? Clearly there are some law enforcement resources devoted to catching and prosecuting cybercriminals. We have seen a number of high profile arrests already this year (and I expect to see more). I have seen some very impressive computer forensics conducted by law enforcement at the local, national, and international levels.
What I don’t see are sufficient resources deployed to fight cybercrime at anything like the scale on which such crime is being conducted. In no way is this a criticism of the folks in the field who are knocking on doors and dissecting hard drives. I just don’t think there are enough of them. An in-depth academic study of cybercrime put the annual global law enforcement spend on the fight against cybercrime at $400 million in 2010 (Anderson, Barton, Bohme, Clayton, van Eeten, Levi, Moore, Savage. 2012). In speaking with one of the authors of that study, I found that about half of that figure, $200 million, was U.S. spending. Compare that to the FBI’s total budget request for fiscal year 2015: $8.3 billion.
Now compare that number to the $21 billion budget for the espionage activities of the NSA/NRO, which is on top of the $14.7 billion we shell out for whatever the CIA does these days. Now look at the staffing levels funded in the 2015 FBI budget request: 34,970 permanent positions including 13,050 special agents. Compare that with the FBI’s 2014 request for $8.4 billion to cover 34,787 permanent positions including 13,082 special agents. By my count, that $100 million less in spending, and a reduction in force of 32 special agents.
I’m a security professional and not a budget analyst, but to me those numbers don’t seem consistent with a firm national resolve to tackle cybercrime. So, speaking as a security professional, I suggest that the next time a major IT security breach hits the headlines, we take a break from blaming the victims, and that includes people who use weak passwords on their accounts or companies who have holes in their security systems. Let’s put some of that anger and outrage into lobbying our government to take more decisive action against cybercrime and the people who perpetrate it.
Disagree? Leave a comment and let me know what you think. BTW, here’s a link to the FBI’s most wanted cyber criminal page.
Â
The post Nude Celebs, Target, Home Depot: Who is to blame? Criminals! appeared first on We Live Security.

![]()