A ‘widespread’ malicious advertising campaign that sent web browsers to immitation websites has been stopped by Google
The post Google puts a stop to Adsense malvertising campaign appeared first on We Live Security.
A ‘widespread’ malicious advertising campaign that sent web browsers to immitation websites has been stopped by Google
The post Google puts a stop to Adsense malvertising campaign appeared first on We Live Security.
In the minds of many, cybercrime was just something that was poorly depicted in movies from the past couple of decades, but the general public is starting to take it much more seriously now that major attacks are becoming a regular occurrence.
There are a number of reasons why this point in time has brought about so many online attacks. One of the most obvious ones is that many of us are moving more of what we do online or into the digital world, and the criminals are just following the trail. This digital shift applies to our communication and data, but it also applies to our financial transactions. The chances are high that you’re using less physical money and more digital payment solutions and credit or debit cards.
Since your data and money are moving around digitally, a criminal doesn’t need to make contact with you or your property in a personal way to inflict damage. Because of this, they can also attack more people in less time, and if you’re a criminal, that’s an attractive proposition.
Additionally, we often talk in a positive way about how easy it has become to learn new tech skills online, but there is a dark side to online education, as well. While there are plenty of ways to learn useful technical skills online, the Internet has also become a haven for cybercriminals to recruit others, share techniques, and coordinate attacks. Whether they’re a prior criminal or not, someone with bad intentions can learn a lot with just a few targeted online searches. The publicity that many attacks have been getting could even encourage certain individuals to do this research and see what’s involved in making the attacks happen.
There’s certainly no end in sight to cybercrime. As we continue to rely on digital solutions to an even greater extent and the systems containing this data continue to be analyzed from top to bottom by criminals, we can count on our perception of crime to become even more digital than it is today.
The post The changing perception of cybercrime appeared first on Avira Blog.
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:026 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : untrf Date : January 15, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: _______________________________________________________________________ References: http://advisories.mageia.org/MGASA-2015-0016.html _______________________________________________________________________ Updated Packages: Mandriva Business Server 1/X86_64: 5cd7586e3c11dd06c10a5372d6f41720 mbs1/x86_64/unrtf-0.21.9-1.mbs1.x86_64.rpm 8e8c788e010dd3e2aa9e60e18b03fcdb mbs1/SRPMS/unrtf-0.21.9-1.mbs1.src.rpm _______________________________________________________________________ To upgrade automatically use Mandriva
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:025 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : mpfr Date : January 15, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated mpfr packages fix security vulnerability: A buffer overflow was reported in mpfr. This is due to incorrect GMP documentation for mpn_set_str about the size of a buffer (CVE-2014-9474). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9474 http://advisories.mageia.org/MGASA-2015-0021.html _______________________________________________________________________ Updated Packages: Mandriva Business Server 1/X86_64: 1bacc42
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:024 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : libsndfile Date : January 15, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated libsndfile packages fix security vulnerabilities: libsndfile contains multiple buffer-overflow vulnerabilities in src/sd2.c because it fails to properly bounds-check user supplied input, which may allow an attacker to execute arbitrary code or cause a denial of service (CVE-2014-9496). libsndfile contains a divide-by-zero error in src/file_io.c which may allow an attacker to cause a denial of service. _______________________________________________________________________ References: http://cve.mitre.o
Original release date: January 15, 2015
The Internet Crime Complaint Center (IC3) has issued an alert addressing a spear phishing scam targeting university employees and their payroll accounts. Scam operators use fraudulent e-mails and websites to entice employees to reveal login credentials.
Users are encouraged to review the IC3 Alert for details and refer to Security Tip ST04-014 for information on social engineering and phishing attacks.
This product is provided subject to this Notification and this Privacy & Use policy.
Earlier in January, thousands of attendees and exhibitors descended on Las Vegas for the 2015 Consumer Electronics Show (CES).
One of the most exciting and talked about trends was the mass market arrival of the Internet of Things, something that I have been talking about since August 2013.
The Internet of Things (IoT) is a catch-all term for the growing number of Internet enabled devices in our lives. If you wear an activity tracker, have a smart Nest thermostat, or remote access CCTV in your home, these are all part of the IoT.
What we saw at CES was a potential glimpse into the future. We saw smart dog bowls, smart baby monitors and even Belty, a smart belt.

Apart from excitement, all smart devices have something in common, they create data. They generate data that helps us as users to take more steps each day, brush our teeth for the required time, not forget to water our plants etc.
All this data is very useful but it is also very real privacy concern. In fact, shortly after CES, the chairwoman of Federal Trade Commission Edith Ramirez warned that privacy and security should be a key consideration as we add more devices to the Internet of Things.
She outlined three major concerns brought about by the IoT:
I couldn’t agree more with Ramirez, as we have seen with voice recognition technologies, the connected world of the IoT has witnessed a land grab. Companies are developing smart devices as quickly as possible and putting them out into the market without proper consideration for what is safe or how data should be used responsibly.
The line between our connected lives and physical lives is more blurred with each passing year and we must change the way we view data and personal information.
I don’t believe that collecting data is a bad thing, in fact its data collection that allows many of the web’s most popular services to function at all. What I do insist on, however, is that data collection is transparent, easy to understand and most important of all, consensual.
People have come to learn that their data has value, and they should be the ones to decide who they share it with, and how it can be used.
If you’re a regular online shopper like me, you’re sure to be familiar with your credit card security code – otherwise known as the card verification value (or CVV).
If not, you can find the 3-4 digit code on the back of your VISA/MasterCard (the final 3 digits of the number printed on the signature strip) or on the front of your Amex card (the separate 4 digit code above the card number).
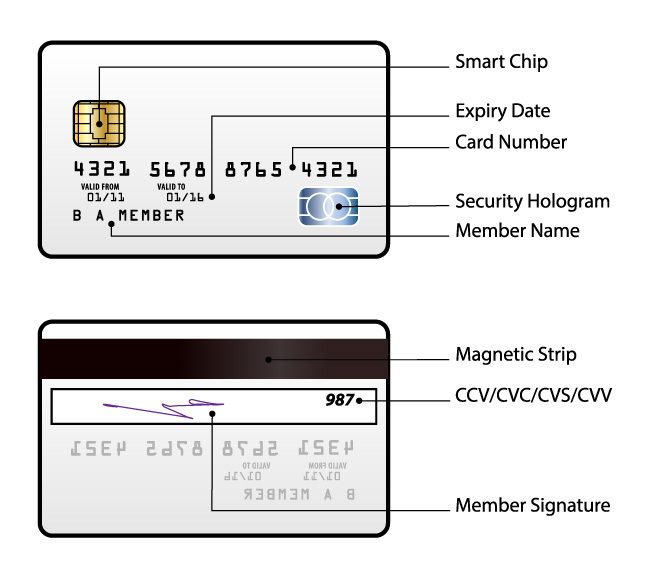
The intended purpose of the CVV is to provide added security when making purchases over the internet – it helps to verify that you’re in possession of the card, as the code shouldn’t be known to anyone other than you as the card holder. So it’s essentially a way of counteracting credit card fraud.
For online shopping, the answer is generally yes – it’s just simply a good idea to stick with well-known, reputable companies that you trust. You’ll find that most online retailers nowadays do require a CVV for purchases, which is encouraging because it means that they’re actively trying to prevent fraudulent transactions occurring on their site.
You may also be asked for your credit card security code when processing a payment over the telephone. As with online transactions, it’s usually safe to do this – you just need to be sure that no one overhears the details you give out (so avoid public places when doing this).
On the other hand, when purchasing an item or service in person, you should never provide the details of your CVV. In fact, there’s no need for the retailer or service provider to request this – it doesn’t show up when the card is scanned normally and they have other ways of verifying that you’re the authorised card holder (signature or another form of identification) should they need to.
Handing over your CVV for purchases completed offline serves no purpose other than providing someone with the opportunity to steal the information. Because if they were to do this, they’d have everything they need to go ahead and make a bunch of fraudulent online transactions – on you!
To avoid any issues with security or credit card fraud, there are a few things you can do:
Have you had any dramas when using your credit cards online? Share your story with us below.
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:023 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : libvirt Date : January 15, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated libvirt packages fix security vulnerability: The qemuDomainMigratePerform and qemuDomainMigrateFinish2 functions in qemu/qemu_driver.c in libvirt do not unlock the domain when an ACL check fails, which allow local users to cause a denial of service via unspecified vectors (CVE-2014-8136). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-8136 http://advisories.mageia.org/MGASA-2015-0002.html ____________________________