Ubuntu Security Notice USN-2505-2
9th March, 2015
firefox regression
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 14.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
USN-2505-1 introduced a regression in Firefox.
Software description
- firefox
– Mozilla Open Source web browser
Details
USN-2505-1 fixed vulnerabilities in Firefox. This update removed the
deprecated “-remote” command-line switch that some older software still
depends on. This update fixes the problem.
We apologize for the inconvenience.
Original advisory details:
Matthew Noorenberghe discovered that whitelisted Mozilla domains could
make UITour API calls from background tabs. If one of these domains were
compromised and open in a background tab, an attacker could potentially
exploit this to conduct clickjacking attacks. (CVE-2015-0819)
Jan de Mooij discovered an issue that affects content using the Caja
Compiler. If web content loads specially crafted code, this could be used
to bypass sandboxing security measures provided by Caja. (CVE-2015-0820)
Armin Razmdjou discovered that opening hyperlinks with specific mouse
and key combinations could allow a Chrome privileged URL to be opened
without context restrictions being preserved. If a user were tricked in to
opening a specially crafted website, an attacker could potentially exploit
this to bypass security restrictions. (CVE-2015-0821)
Armin Razmdjou discovered that contents of locally readable files could
be made available via manipulation of form autocomplete in some
circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to obtain sensitive
information. (CVE-2015-0822)
Atte Kettunen discovered a use-after-free in the OpenType Sanitiser (OTS)
in some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to cause a
denial of service via application crash. (CVE-2015-0823)
Atte Kettunen discovered a crash when drawing images using Cairo in some
circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service. (CVE-2015-0824)
Atte Kettunen discovered a buffer underflow during playback of MP3 files
in some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to obtain
sensitive information. (CVE-2015-0825)
Atte Kettunen discovered a buffer overflow during CSS restyling in some
circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code with the
privileges of the user invoking Firefox. (CVE-2015-0826)
Abhishek Arya discovered an out-of-bounds read and write when rendering
SVG content in some circumstances. If a user were tricked in to opening
a specially crafted website, an attacker could potentially exploit this
to obtain sensitive information. (CVE-2015-0827)
A buffer overflow was discovered in libstagefright during video playback
in some circumstances. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to cause a
denial of service via application crash, or execute arbitrary code with
the privileges of the user invoking Firefox. (CVE-2015-0829)
Daniele Di Proietto discovered that WebGL could cause a crash in some
circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service. (CVE-2015-0830)
Paul Bandha discovered a use-after-free in IndexedDB. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit this to cause a denial of service via application
crash, or execute arbitrary code with the privileges of the user invoking
Firefox. (CVE-2015-0831)
Muneaki Nishimura discovered that a period appended to a hostname could
bypass key pinning and HSTS in some circumstances. A remote attacker could
potentially exloit this to conduct a Man-in-the-middle (MITM) attack.
(CVE-2015-0832)
Alexander Kolesnik discovered that Firefox would attempt plaintext
connections to servers when handling turns: and stuns: URIs. A remote
attacker could potentially exploit this by conducting a Man-in-the-middle
(MITM) attack in order to obtain credentials. (CVE-2015-0834)
Carsten Book, Christoph Diehl, Gary Kwong, Jan de Mooij, Liz Henry, Byron
Campen, Tom Schuster, Ryan VanderMeulen, Christian Holler, Jesse Ruderman,
Randell Jesup, Robin Whittleton, Jon Coppeard, and Nikhil Marathe
discovered multiple memory safety issues in Firefox. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to cause a denial of service via application
crash, or execute arbitrary code with the privileges of the user invoking
Firefox. (CVE-2015-0835, CVE-2015-0836)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 14.10:
-
firefox
36.0.1+build2-0ubuntu0.14.10.1
- Ubuntu 14.04 LTS:
-
firefox
36.0.1+build2-0ubuntu0.14.04.1
- Ubuntu 12.04 LTS:
-
firefox
36.0.1+build2-0ubuntu0.12.04.1
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to restart Firefox to make
all the necessary changes.
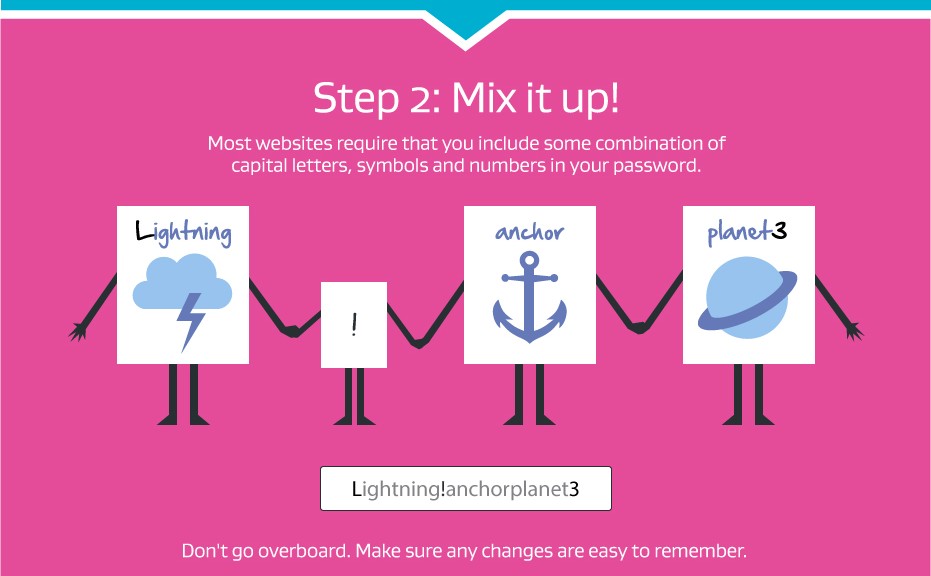
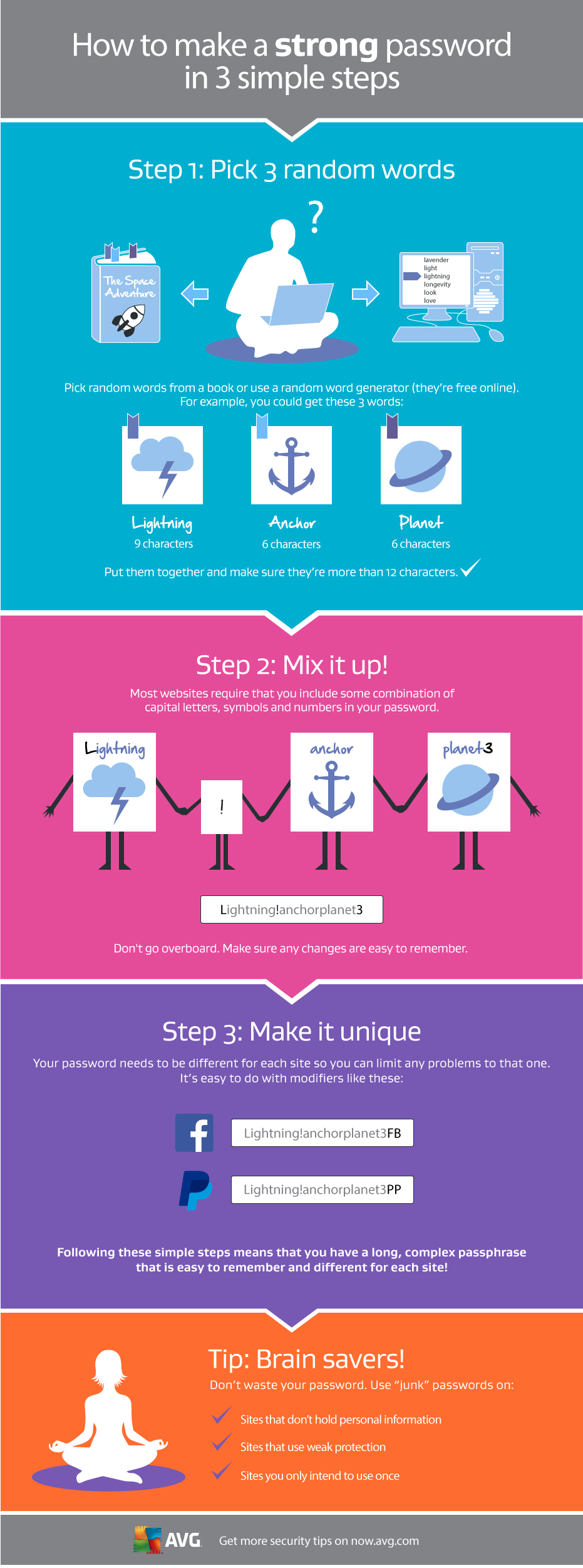

 Prepare yourself before disaster strikes
Prepare yourself before disaster strikes