-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:056 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : rpm Date : March 9, 2015 Affected: Business Server 2.0 _______________________________________________________________________ Problem Description: Updated rpm packages fix security vulnerabilities: It was found that RPM wrote file contents to the target installation directory under a temporary name, and verified its cryptographic signature only after the temporary file has been written completely. Under certain conditions, the system interprets the unverified temporary file contents and extracts commands from it. This could allow an attacker to modify signed RPM files in such a way that they would execute code chosen by the attacker during package installation (CVE-201
Monthly Archives: March 2015
Kaspersky Lab North America Celebrates Ten Years of Technological Innovation and IT Security Expertise
FBI investigating apparent ISIS attacks on Western websites
A number of seemingly unconnected Western websites were hacked over the weekend, with messages claiming Islamic State as the perpetrator.
The post FBI investigating apparent ISIS attacks on Western websites appeared first on We Live Security.
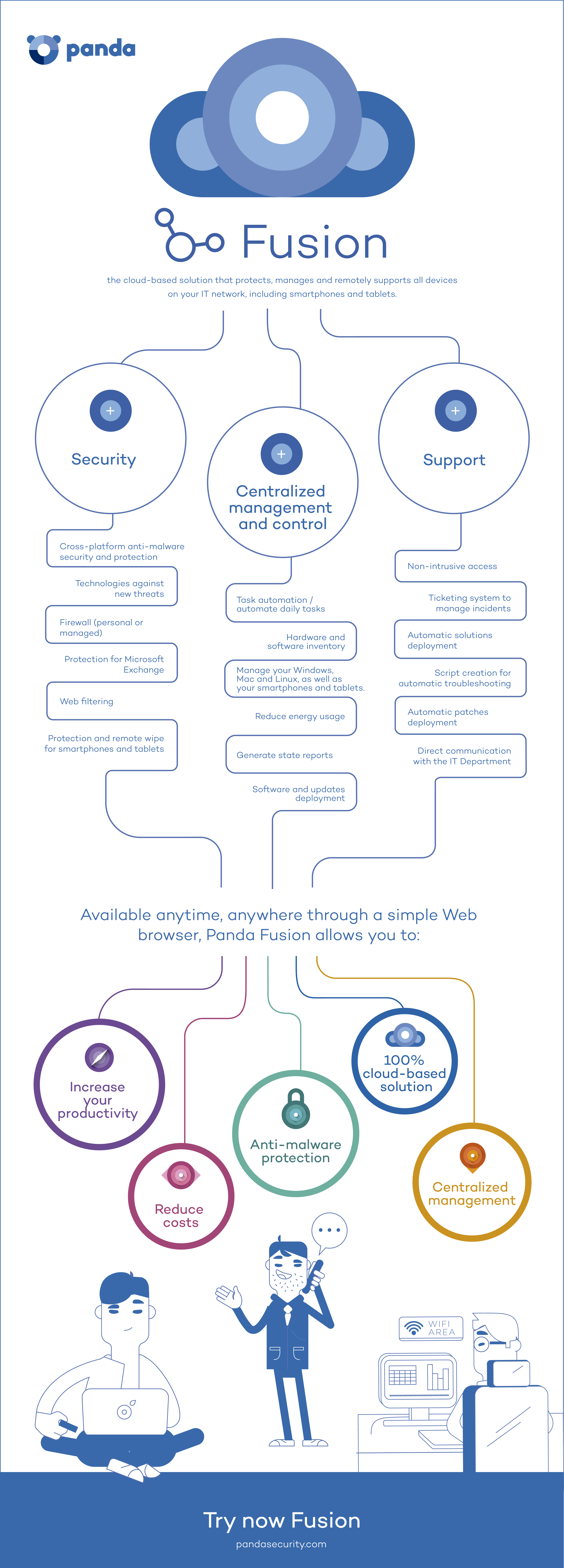
Fusion: Cloud Security, Management and Support
Do you need a security solution capable of protecting, managing and remotely supporting all devices on your IT network, including smartphones and tablets? If so, meet Panda Fusion.
Panda Fusion is a cloud-based solution that meets all your needs, and is easy to deploy and scale as it doesn’t require maintenance or infrastructure investment. Available anytime, anywhere through a simple web browser.
Try now Panda Fusion and discover its benefits:
- It offers maximum protection against malware and unknown threats.
- It reduces costs through optimization of your IT infrastructure.
- It provides an optimal support experience, through proactive problem resolution and remote, non-disruptive access to their devices, wherever they are.
Want more information?
Want to share this infographic? Here is the code!
The post Fusion: Cloud Security, Management and Support appeared first on MediaCenter Panda Security.
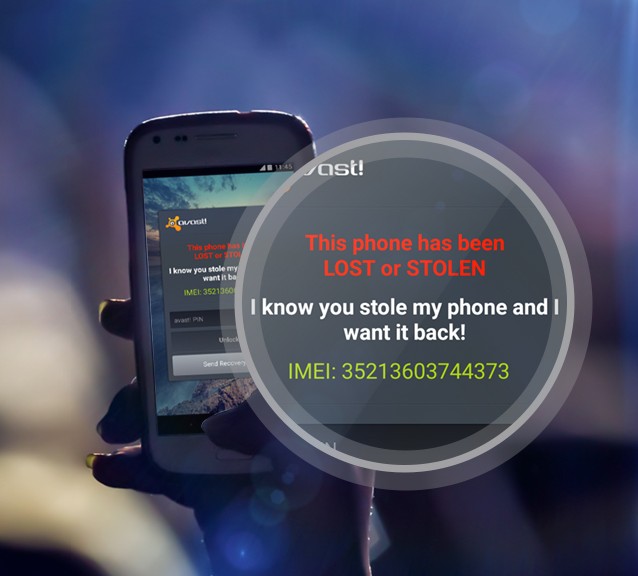
Don’t be sorry for party rocking – install Avast Anti-Theft!
Andreas L. lost his phone at a party, but that’s not the end of the story. Avast Anti-Theft helped him find the thief and get his phone back.
A lot can happen when you go to a party: you may bump into old friends, make new ones, or dance like there is no tomorrow. Losing track of your personal belongings can also happen when you party, which is exactly what happened to Andreas from Bangkok.
Andreas recently commented the following on our Facebook page:
// <![CDATA[
(function(d, s, id) { var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) return; js = d.createElement(s); js.id = id; js.src = “//connect.facebook.net/en_US/all.js#xfbml=1”; fjs.parentNode.insertBefore(js, fjs);}(document, ‘script’, ‘facebook-jssdk’));
// ]]>
We were happy to hear Avast Anti-Theft helped Andreas get his phone back and asked him what happened and how exactly he used Avast’s features to get his phone back. Here is his story:
Andreas went to a party in Bangkok where he made new friends, had a few drinks and at the end of the night Andreas responsibly took a taxi home. When he woke up the next morning he realized that every smartphone owner’s worst nightmare had happened to him, his phone was missing! Losing a smartphone is not only frustrating because the hardware is expensive, but because it contains so much personal information.
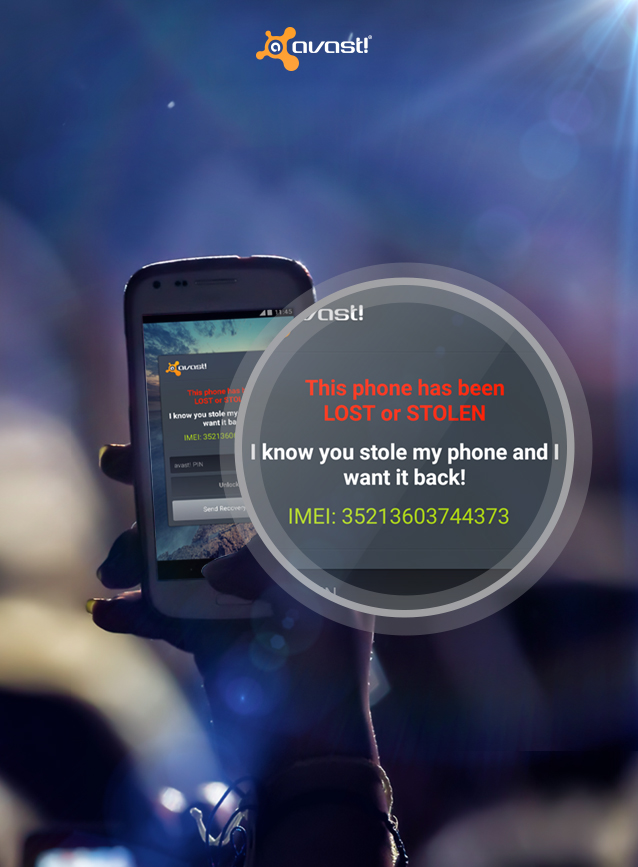
Find your lost phone with Avast Anti-Theft like Andreas did.
Avast Anti-Theft to the rescue!
While Andreas worried about his phone, he received a message from Avast. The message informed him that his phone’s SIM card had been changed and provided him with the new SIM card’s number and service provider. That is when Andreas realized he could use Avast’s other anti-theft features to GPS locate his phone and perform commands like wiping his phone remotely. Luckily, Andreas did not have to go as far as wiping his phone, but the option did help him in his efforts to get his phone back.
I will look for you, and I will find my phone
With his phone’s new number in hand, Andreas called the thief to confront him and demand he return his phone. Andreas let the thief know that he knew his location (and more) and could render the phone useless and go to the police if the thief did not cooperate. The thief gave in and sent Andreas his phone.
Andreas’ story is one of many lost and found stories we have received from Avast Anti-Theft users and each story gets more interesting! From this experience we can only recommend partiers install Avast Anti-Theft before going out, we will have your back so you can party worry free!
You can install Avast Anti-Theft for free from the Google Play Store.
If you have a story to share, write us on our Facebook or Google+ page. We could share it in our blog.
DDoS attack on feminist blog backfires on International Women’s Day
An attempt to silence feminism blog Femsplain backfires on DDoS attackers, as they only help to raise its profile.
The post DDoS attack on feminist blog backfires on International Women’s Day appeared first on We Live Security.
Let’s ‘Make It Happen’ for Women in Tech
The first International Women’s Day was held in 1911. The day is actually celebrated worldwide, and not just on one day, but from late February through March and beyond.
This year, thousands of events are occurring to mark and encourage the economic, political and social achievements of women. Organizations, governments, charities, educational institutions, women’s groups, corporations and the media celebrate the day. The activities span the realm of possibilities for women, including women in tech.

There were more than 340 events scheduled to take place in the United Kingdom alone to celebrate International Women’s Day. For example, an event on March 6, focused on women’s work in creative and technology industries was scheduled in London’s tech hub. And in a variation of Girls Who Code, in Luxembourg they were holding “Mums and Girls Code”– a fun introductory workshop in coding for mothers and their daughters.
Here in the USA, 186+ events were scheduled for International Women’s Day. You can see a complete list here. The list of events is inspiring, promoting awareness, culture, and learning for women and girls across the nation. Many of the IWD events are also online, including webinars, for people who don’t have time to visit a particular event.
Later this March, I’m personally very excited to be speaking at SXSW Interactive on the subject of furthering women’s roles in technology. My session at 3:30 p.m. March 14 (JW Marriott Room 407), “Boardroom or Baby: The Choices Women Have in Tech” will address closing the gaps in opportunities for women in technology and achieving work/life balance. If you can’t join in person, you can join the conversation at @judyatavg #techwomen #SXSW.
It’s actually very encouraging to see that there are many conversations on the topic of women in technology scheduled for SXSW Interactive 2015: Among them: “End To Brogramming” with Re/code and Elle.com, which takes place from 5-6 p.m. on March 13; “Geek Girls Are Chic!” on March 15 by Girls Who Code and IBM, and “#OurTimeToLead: Why Tech Needs More Women” by the Anita Borg Institute on March 17. You can see the SXSW schedule here.
We’ve all done the math. But women in tech (or the lack of such) is not just a pipeline issue, it’s a retention issue and a culture issue as well. It’s encouraging to see major tech companies are recognizing this. It is for everyone’s own good: we need a smart tech workforce and can’t dismiss half the population, and on the consumer side, women represent significant adopters when it comes to technology.
So progress is happening. Good moves are being made. Though more must happen. I think International Women’s Day is a great day to see how far we have come, and serve a fantastic spark to light and then pass the torch to following generations to empower all women, our sisters and daughters.
Fedora 21 Security Update: 389-ds-base-1.3.3.9-1.fc21
Resolved Bugs
1199675 – CVE-2014-8112 CVE-2014-8105 389-ds-base: various flaws [fedora-all]<br
Release 1.3.3.9 with security bug fixes
Fedora 22 Security Update: freexl-1.0.0i-1.fc22
Resolved Bugs
1199328 – freexl-1.0.0i is available<br
Four potentially harmful bugs causing crashes and stack corruption
were detected in FreeXL by American Fuzzy Lop and are solved in this release.
Please note: such issues are never realistically expected
to be encountered in real world XLS spreadsheets, anyway
some purposely forged XLS document could be used as a
“poisoned bait” to maliciously open a security breach.
https://groups.google.com/forum/#!topic/spatialite-users/plxKNbYw184
Fedora 21 Security Update: libgcrypt-1.6.3-1.fc21
Resolved Bugs
1198152 – CVE-2015-0837 CVE-2014-3591 libgcrypt: various flaws [fedora-all]
1198145 – CVE-2014-3591 libgcrypt: use ciphertext blinding for Elgamal decryption (new side-channel attack)
1198147 – CVE-2015-0837 libgcrypt: last-level cache side-channel attack<br
New upstream release fixing two minor security issues.