Monthly Archives: April 2015
Avira Antivirus Security for Android: they’re loving it!
Your device’s mobility makes it easier for crooks to hack it or simply steal it together with all the information you store on it. When choosing a certain mobile security provider, you might need to take into consideration more than just classical protection parameters that used to apply for your old computer. Take a look at all the amazing features offering you complete protection in our free Antivirus Security for Android.
Avira’s Mobile Development team has done an outstanding job in the last couple of months, updating our Android Security Solution on a regular basis. Besides the traditional bug fixes, some really useful features have been added to the menu, making sure that our users get full protection on all levels.
Here’s a complete list of the cool features in Avira’s Antivirus Security for Android:
- Complete device scan: no corrupted apps, files or malware can escape our radar
- Anti-theft feature: locate your device, wipe any data from it or simply lock it.
- Identity safeguard: scan your email address and your contacts to identify any association with potential account breaches at other companies.
- AppLock: lock your applications by using PIN code identification to allow access.
- Blacklist: keep away unwanted conversations
- Premium Secure Browsing: available only for users who upgrade, this feature scans the websites you visit on your mobile device to make sure they are safe and to prevent any potential phishing attack.
With all these features and powerful technology involved, it’s no wonder Avira’s Antivirus Security for Android is receiving so many awards. 83% of the users who rated us on Google Play awarded our product 4 and 5 stars. Want to know why everybody is loving it? See it for yourself, download it now!
The post Avira Antivirus Security for Android: they’re loving it! appeared first on Avira Blog.
Kaspersky Lab North America Promotes Mike Canavan to Vice President, Sales Engineering
Point-of-Sale vendor has used the same admin password for 25 years
A major vendor of point-of-sale terminals has not changed the default passwords used on its devices in a quarter of a century, researchers have revealed at RSA 2015.
The post Point-of-Sale vendor has used the same admin password for 25 years appeared first on We Live Security.
![]()
Hack on the track: Signaling flaw leaves UK trains vulnerable
UK train services could be vulnerable to being hacked, hijacked and crashed, due to the trial of new digital signaling system designed to make lines safer.
The post Hack on the track: Signaling flaw leaves UK trains vulnerable appeared first on We Live Security.
![]()
RSA Conference 2015: too much technology and not enough people?
Major themes of the 2015 RSA Conference: the degree to which the deployment of digital devices is outpacing our ability to deploy humans with the necessary skills and knowledge needed to secure data and systems.
The post RSA Conference 2015: too much technology and not enough people? appeared first on We Live Security.
![]()
Three Exciting Things In: Connected Cars
The motor industry is one of the most innovative spaces in business right now. From driverless technology to remote access and electronic cars, there is an abundance of exciting technology that promise to make a real difference to the way to move around our lives.
Augmented Reality Driving Goggles
Covered in this fascinating Wired article, these driving goggles (seen above) are being developed by the automaker Mini and have the potential to change the way we drive for good.

Headsup display: Make sure the most important information is available to you wherever you’re looking with speed and directions fed directly into the goggles.
Zero latency: Using special technology to predict how your head will move, the goggles approach to close to “zero latency” meaning that the augmented images displayed in the goggles are happening in real time.
Look through walls: By using cameras and microphones outside of the vehicle, you can look straight through the frame of the car to see potential hazards.
Remote Control Parking:
BMW recently revealed that they have developed remote control parking for the 2016 BMW 7 Series.
But that’s not all, BMW are looking to change “interaction between the driver and the car” by introducing in-car gesture control to the 7 series and improved voice commands. This means no more fiddling with that radio or satnav.

Wireless Car Charging
Electronic cars are slowly but surely making their way into the mainstream. One of the largest obstacles to their adoption is the lack of charging stations. A research team at Qualcomm has developed a wireless form of charging for electronic cars that could potentially make it much easier to charge vehicles.
Using inductive charging, the electronic car will charge wirelessly when parked over a magnetic plate.
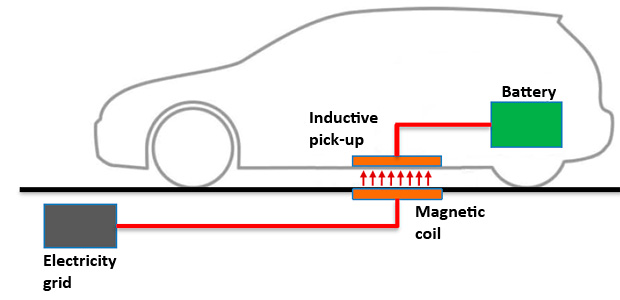
Inductive technology has only recently taken off in the consumer space with wireless smartphone charging stations so don’t expect to see these on the road any time soon.
The importance of privacy
As these three exciting technologies demonstrate, the Internet of Things is growing and advancing at an incredible rate. It’s important though to ensure that we are building and developing advanced functionality with privacy and security in mind.
The benefits of smart, connected vehicles are obvious for all to see but as AVG has highlighted several times already, vulnerabilities in system security can pose real risks to human safety and property damage.
![]()
![]()
RSA 2015, the year security goes mainstream
What were the major themes from the RSA 2015 conference? Cameron Camp is on hand to give his verdict…
The post RSA 2015, the year security goes mainstream appeared first on We Live Security.
![]()
InboxScan: the service that checks if you have saved your passwords in your email
Passwords are the unfinished business of Internet users. We have all had the same problem. After carefully picking the perfect password with capital letters, numbers, special characters and which is finally long enough, we have to sing up for another service. Whether it is to open bank account, a new profile on Instagram or to access our telephone bills via the Web we have to remember yet another password.
Although some platforms help us with this task by sending us a password to enable us to enter the account and which can be modified later, we end up learning it by heart instead of changing it.
That email with our password is then forgotten and ends up at the bottom of our inbox.
We already warned you when more than five million Gmail passwords were leaked on a file and security experts have demonstrated with various safety studies that this is an upward trend. If we look back to that forgotten email among other hundreds, you can figure out that its very existence poses a risk, because its content is at the mercy of the cybercriminals who are always ready to steal the information.
If you, like most people, suffer from ‘digital Diogenes syndrome’ it will be difficult to rescue all those emails with sensitive information and to prevent their theft. And to remember all the online services you have signed up for and for which you have kept the original password.
Whatever the case we recommend a useful and simple option called Scan Inbox. A tool which detects forgotten private information in your inbox and deletes it permanently. You don’t even have to download the service. It is available ‘online’.
The program works in Gmail, Hotmail, Yahoo or AOL and searches for and locates sensitive information such as automated emails with passwords or bank account numbers which you think are secure.
To use this tool you only have to indicate your mail server and it will automatically access and scan your email. Dashlane, the company owning the service, ensures that this intrusion is temporary and no personal information is stored.
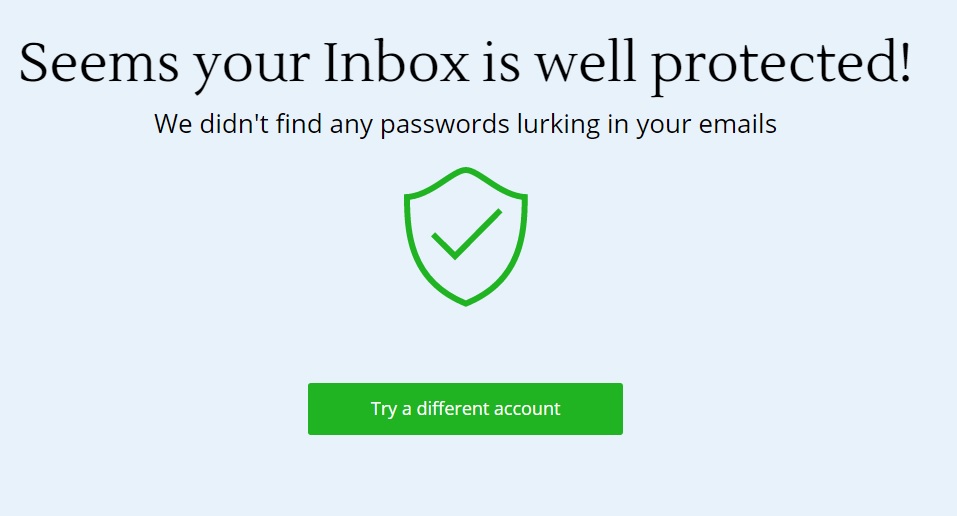
Once the analysis is executed and completed, Inbox Scan gives you a full report on the inbox’s ‘health’ with regard to security. The report includes details like the number of passwords and the number of new accounts created, those which might have been affected by a security breach and which passwords have been reused.
All the information is presented in a visual way: a lower bar indicates the time and above it a series of bubbles arranged chronologically. Each of these represents one of the accounts you have created. The bigger the bubble the more important it is, and the color red indicates whether this tool has found a password associated with the account in question.
If the display is not enough for you and you wish to study the report in depth you can download it in PDF. From there on, you just have to change the compromised passwords and delete all the sensitive emails.
An alternative for you to store your passwords safely
If you wish to have all your passwords stored in one place, you can use the password manager of our antivirus software Panda Global Protection.
If you use this you will only have to remember one master password to access all your Web services. In this way, you will never forget another password again!
The post InboxScan: the service that checks if you have saved your passwords in your email appeared first on MediaCenter Panda Security.
Apple Watch and the smartwatch revolution
The brand has done an excellent marketing campaign in rolling it out, including high-profile celebrity seedings (Katy Perry, Beyoncé and Christy Turlington Burns, to name a few) and a high-touch, pre-order program that included in-store previews for customized “fittings.”
Initial reports by analysts estimate Apple have already taken 2.3 million pre-orders, giving it the familiar headache of demand outstripping supply.
Some reports indicate the anticipated April 24 ship date has been quietly removed for their website, and Apple’s retail chief acknowledged in internal memos that the watch won’t be available for sale with inventory in its retail stores until June.
Meanwhile, research firm ABI estimates Apple will sell over 13 million Apple Watches this year. Whenever the Apple Watch arrives, it’s a big and much-anticipated step in the wearable marketplace – and one of the major reasons pundits are calling this “the year of wearables.”
No doubt, this is an exciting time and a major step in wearable technology becoming mainstream.
Excitement may be tempered by the mixed initial reaction to the Apple Watch from testers who have concerns over battery life and functionality. Others have had trouble navigating through the various features. You can see a good summary of the media reactions here.
My thoughts? The Apple Watch is certainly more attractive than most wearable technology, having that great Apple sense of style. It has many fitness features (if not all the health apps originally envisioned) and allows you to use Apple Pay along with all sorts of other apps, whose number and magnitude will rapidly increase as third-party developers come along.
Currently, the pricing may be the biggest drawback. I’m not talking about the $10,000 gold watch, but the starting price point of $349/$549 for the sport watch depending on finishes. This, in my view, makes it an early adopter choice and not yet truly mainstream.
Not to be overlooked, is Google’s Android Wear OS for watches –which recently received a major software update to greatly expand its watch capabilities. It comes just in time for the Apple Watch debut and looks to give that smartwatch platform a boost. The Android Wear watches made by Samsung and LG have opening prices in the more demur range of $150-$300. (Researchers estimated that 720,000 smartwatches based on Android Wear shipped in the last six months of 2014.)
For now, these smartwatches all seem like more of a sidekick for our smartphones. An iPhone 5 ($549 unlocked) or above is required for Apple Watch, and an Android device (around $249 and up, depending on the maker) for the Google watch platform. But then, smartphone tethering is the case with most wearable devices today.
Still, it remains to be seen whether the new category of smartwatches will become really useful tools vs. timepiece status symbols. At AVG, we have already integrated our AVG Zen product into smart watches so that you can monitor and control the protection, performance and privacy of your devices with a single touch.

Personally, I will be keeping privacy and data in mind as smart watch manufacturers add more functionality to their devices. Using the Apple Watch as an example, it already has access to my personal health and payment information as well as my contacts, email and calendar.
How smart watches store, transmit and share this information will be a major influencer on whether or not I decide to experiment with a smart watch of my own.
![]()
![]()
