libraries/Config.class.php in phpMyAdmin 4.0.x before 4.0.10.10, 4.2.x before 4.2.13.3, 4.3.x before 4.3.13.1, and 4.4.x before 4.4.6.1 disables X.509 certificate verification for GitHub API calls over SSL, which allows man-in-the-middle attackers to spoof servers and obtain sensitive information via a crafted certificate.
Monthly Archives: May 2015
CVE-2015-3906
The logcat_dump_text function in wiretap/logcat.c in the Android Logcat file parser in Wireshark 1.12.x before 1.12.5 does not properly handle a lack of termination, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted message in a packet, a different vulnerability than CVE-2015-3815.
Scamware or why you shouldn’t believe in miracles
We normally make fun of this, or just totally ignore it. We know that it probably is a scam. So, if we don’t believe those ads, why do we believe in some apps? Apps that advertise things like:
- Get free stuff in our shop through your favorite social network with the ‘Just click and win’!
- Fix your computer; increase your RAM and hard disk space all in one click with ‘Ultra Optimizer Plus’!
- Install this app on your phone to get ‘Sexy videos on your phone for free

 ‘!
‘! - Buy the NEW SUPER SHINY (not official) Video ‘Not-Fake Player’!
Nowadays Social Networks appear to be the best places to find victims for scams. Who hasn’t seen offers like “Like and share to win an iPhone”, “See the leaked video of the last Pop Star”, “New Facebook features!” and so on Facebook? These are – of course – usually tricks to make you fall for a scam.
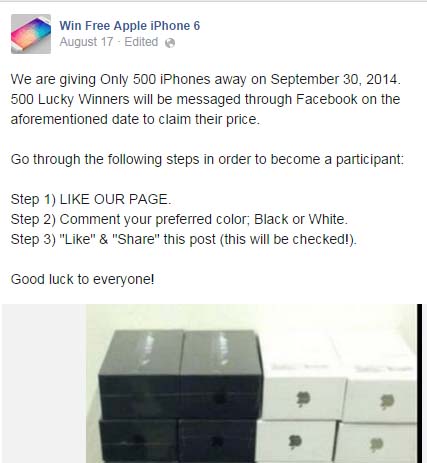
facecrooks has a huge list of Facebook related scam. Below are just two of the countless examples:
Free iPhones: Like the Facebook page and share the picture. It is easy to win a phone right? Wrong. There is no iPhone and you will be spammed from this page (pages can be sold as advertising spaces) because you gave them a like.
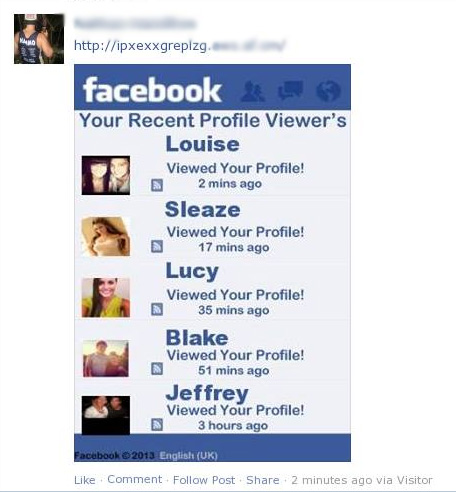
Profile viewer: Don’t you want to know if the girl from school or the boy from work is seeing your pictures? So better ask them because these kinds of plugins/features/apps don’t work. Normally behind these links you will find some PUA or Adware ready to be downloaded and installed on your computer.
Then there are applications that can improve the performance of your computer. We offer you Avira System Speedup. This program can defragment your hard drive or delete useless folders and registry entries. It works perfectly well and WILL speed up your PC – to some degree. But there is just no application that will perform wonders on your PC. If it is 8 years old and slow, it will just never feel like a newer machine with more RAM and a better CPU despite your efforts and you paying €50 to improve it with a random program that promises you just that. Those scam apps, apart from not fixing your computer, also create errors or problems that didn’t exist before, in order to make you pay even more money for fixes you would not have needed in the first place.
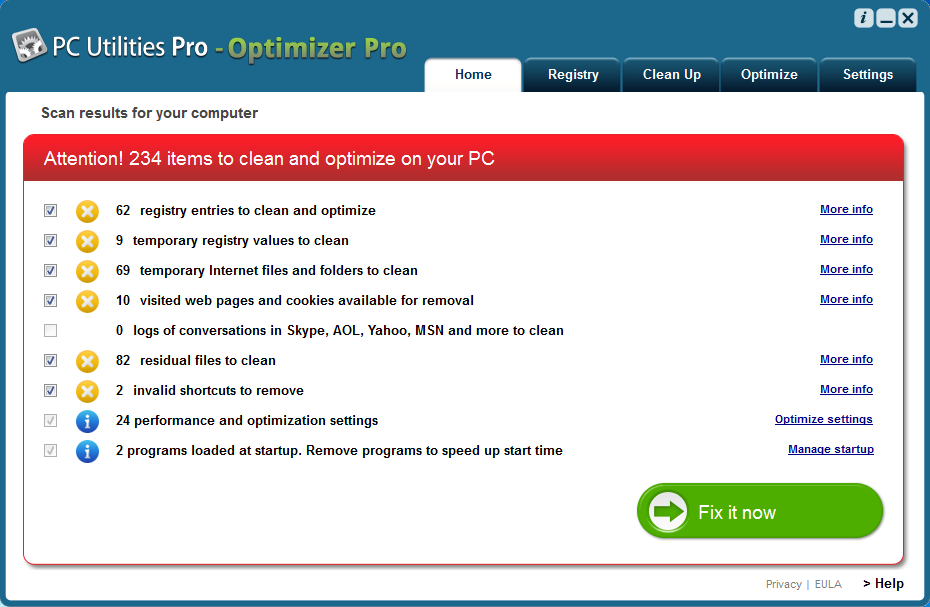
Optimizer Pro (another real world example) could be classified as scareware as well; it tells us that the computer needs to fix things that, in fact, are working correctly. It uses our fear to get us to pay for the product.
Scam is not getting old. It is also very present on our smartphones. Do you want an app that does things for free where others take money? It is possible, but be careful. With these applications you will usually be walking on thin ice.
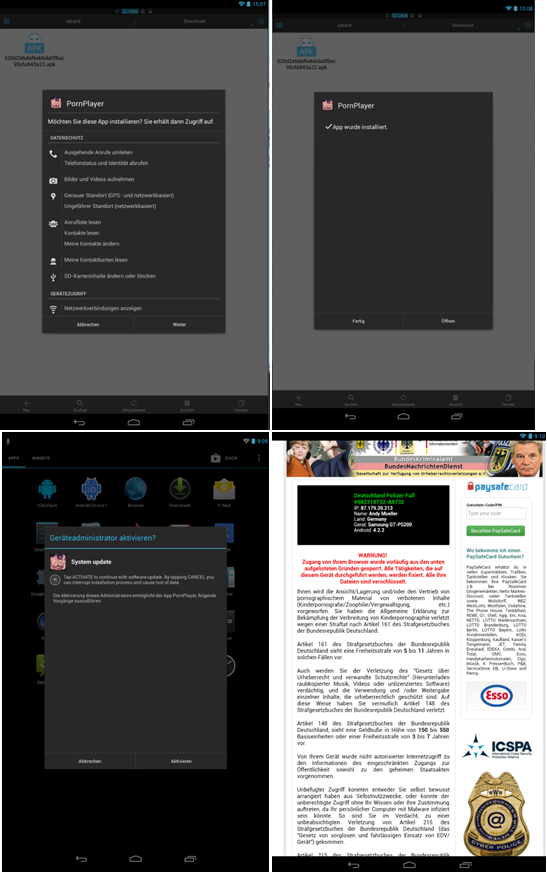
Porn app for Android for example is an app that allows users to watch porn videos for free. Just accept the conditions, give them permissions and run the app as soon as you can! Ooops! Did you think ransomware was only affecting your PC? Now you also have your phone blocked.
When you want to get an application, try to download it from the original source if possible. Also check different sites first, since lots of applications are actually for free.
Even on a well-known and trusted site like Amazon it is easy to find scam regarding original software. VLC is a popular video player which can be downloaded for free – but believe it or not, there are actually people trying to sell it to you to make some quick bucks.
If you don’t trust the source, or if it looks just a tiny bit suspicious, turn around and run as fast as you can. Regarding scam applications: If you are looking for something specific, first check for another users opinions and more information, compare it with other products, and if you are still not sure, just leave it be.
In conclusion, Scamware is a waste of time and money and never does the things you were promised it was going to do. So don’t believe in these false promises of “eternal life potion”, “Ferraris for free” or “1 click super computer”.
Links:
The post Scamware or why you shouldn’t believe in miracles appeared first on Avira Blog.
Exploit Kit Using CSRF to Redirect SOHO Router DNS Settings
French researcher Kafeine has found an exploit kit delivering cross-site request forgery attacks that focus on SOHO routers and changing DNS settings to redirect to malicious sites.
The safe mobile company, a fantasy?

Mobile companies are now a reality. Nobody doubts that accessing corporate applications through smartphones and / or tablets is not only convenient but also necessary, for increasing productivity to levels which were thought impossible until a few years ago. In addition, the demand by workers, employees and companies’ suppliers for access to the organizations’ mobile satellite systems, applications and certain data, is imperative. The problem, however, is that the boom in mobility has also brought certain risks which many companies are not yet aware of.
A company is not secure anymore if it only limits itself to protecting the traditional organizational perimeter. It is no longer enough to have firewalls, threat management solutions, antispam and content filtering. Now it is necessary to protect access and not only from a PC. So it is essential to have a real strategy and best practice regarding the use of mobility in the company: a strategy that in addition to ensuring the safety of the devices also incorporates other elements such as the protection of data and applications with which the mobile users interact. In addition, this strategy must be compatible with another requirement: that it does not interfere, in any way with the agility and entrepreneurial dynamism which the use of mobile devices provides.
Secure devices and encrypted communications
One of the first requirements to be included in any mobile security strategy is to protect mobile devices with antimalware security software. Yes, malicious software attacks not only the operating systems of traditional desktops or laptops. Recently especially Android, Google’s mobile operating system which is the most widespread in the market, and iOS, the Apple platform, have become a focus for cybercriminals. Even so, and despite the evangelization of the leading manufacturers of security software, there are still many companies (as also occurs with users on a personal level) who have not protected their mobile devices with the high risk that this entails. It is an indispensible task to have antivirus software in place and, of course, updated.
Another important aspect, in addition to encrypting communications on mobile devices so that no data can be intercepted, is to use a user authentication device that goes beyond the traditional password. In fact, many mobile devices already allow by default identification by fingerprint and there are even some prototypes which will bring recognition through the iris as standard practice. There is no need, however, to use biometrics. The use of passwords can also be combined with other means of identification, for example involving the use of email or text messages to the mobile itself, other security tokens, etc. In this respect, organizations should train employees to use the correct identification tools and to know how to act in case of loss or theft of the device.
Beware of third-party software
It should also establish policies that restrict employees from using third party software that may cause risks for companies. There are many professionals who, when installing an app of dubious origin or which, although it seems authentic is in fact an imitation created by cybercriminals, see how their device is attacked and consequently the security of data handled by their organization seriously compromised. Following this line, the consultants, Gartner, advise that jailbreaks on iOS devices and rooting on Android phones should be avoided, these being two practices which give the user administrator privileges with the risks which this involves for companies.
Interestingly, the experts at Gartner claimed in a public study in 2014 that most of the security breaches which will occur on mobile devices in 2017 (up 75%) will be the result of a bad configuration of applications built for these gadgets. An example of this is the misuse of personal cloud services through apps that users of smartphones and tablets have installed. The best defense, they argue, is that the company should install a fixed configuration for this type of device under the umbrella of a management policy for mobile equipment which must be complemented with other tools for data protection.
The consultants also recommend that companies should specify which platforms and operating systems should be used for their mobile devices by their employees and that versions which cannot be updated or supported should be avoided, and that users should be required to register or be certified when entering applications such as virtual corporate email, VPNs, wireless and other shared applications. What is essential, they stress, is that the security team know what types of systems and applications its employees need to access and for what purpose, in order to establish the appropriate controls. Also, mobile devices must be configured to prevent wireless networks that are not safe and users should be recommended to disable the Bluetooth option to avoid unexpected scares.
Controls and audits are highly recommended
Finally, it is also recommended that companies undergo regular audits and controls (at least once a year) to evaluate the quality and robustness of their mobile security policy. It should not be forgotten that security incidents not only entail negative economic repercussions and loss of core assets such as the company’s own data or that relating to customers (or citizens, in the case of government departments) but also damage reputation and image. And to remedy this is just to be more aware of the new realities of today’s organizations, now completely mobile.
The post The safe mobile company, a fantasy? appeared first on MediaCenter Panda Security.
CVE-2015-4091
XML external entity (XXE) vulnerability in SAP NetWeaver AS Java allows remote attackers to send TCP requests to intranet servers or possibly have other unspecified impact via an XML request, related to “CIM UPLOAD,” aka SAP Security Note 2090851.
CVE-2015-4092
Buffer overflow in the XComms process in SAP Afaria 7.00.6620.2 SP5 allows remote attackers to cause a denial of service (crash) or possibly execute arbitrary code via a crafted request, aka SAP Security Note 2153690.
Synology Fixes File-Takeover Flaw in Cloud Station OS X Client
There is a vulnerability in some versions of Synology’s Cloud Station client for OS X that can enable any user to take over system files and gain complete control of the machine. Cloud Station is a system that allows users to sync files across a number of devices. The system saves changes to files on […]
Ubuntu Security Notice USN-2622-1
Ubuntu Security Notice 2622-1 – It was discovered that OpenLDAP incorrectly handled certain search queries that returned empty attributes. A remote attacker could use this issue to cause OpenLDAP to assert, resulting in a denial of service. This issue only affected Ubuntu 12.04 LTS. Michael Vishchers discovered that OpenLDAP improperly counted references when the rwm overlay was used. A remote attacker could use this issue to cause OpenLDAP to crash, resulting in a denial of service. Various other issues were also addressed.
Debian Security Advisory 3273-1
Debian Linux Security Advisory 3273-1 – William Robinet and Michal Zalewski discovered multiple vulnerabilities in the TIFF library and its tools, which may result in denial of service or the execution of arbitrary code if a malformed TIFF file is processed.