The fledgling industry has grown rapidly and is estimated to be valued around $16 billion by 2018. Now it seems that almost anything is possible. Here are some of the three great uses of 3D printing technology emerging today.
Clinical testing
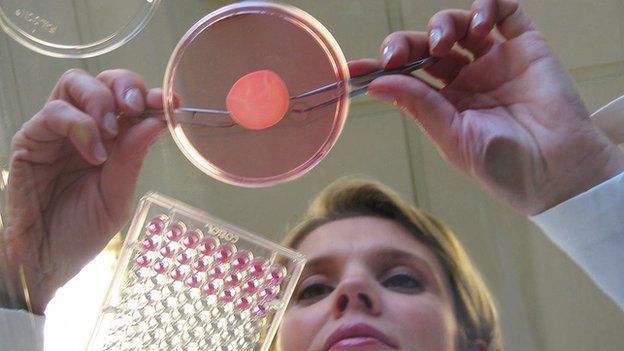
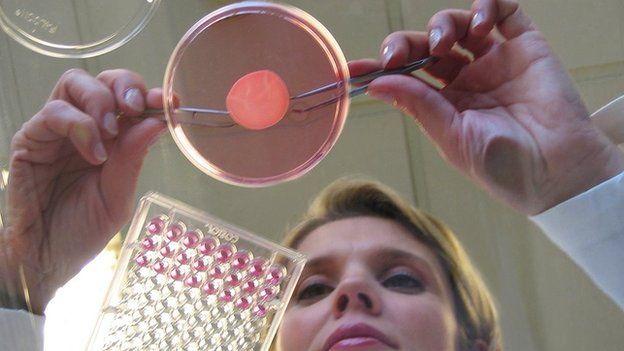
Cosmetics company L’Oreal has started developing 3D printed skin to help them test cosmetics without the need for animals or real human skin. Working in collaboration with bio engineering company organovo, L’Oreal said “Our partnership will not only bring about new advances in vitro methods for evaluating product safety and performance, but the potential for where this new field of technology and research can take us is boundless.”
This is clearly a big step forward for a whole range of cosmetics and can help build a future less dependent on animal testing.
Fashion and textiles
While it most fashion conscious people may take some convincing before they agree to don a garment made out of 3D printed fabrics, the emerging industry shows a lot of promise and potential.
The opportunity to create custom pieces, built to specific physical dimensions could potentially give clothes of the future a convenience and suitability rarely found in traditional clothes.
It doesn’t stop there though, when you consider the market for fashion bags and accessories, the possibilities for customization and personalization are as broad as they are deep.
Body Parts
Perhaps the biggest success story for 3D printing thus far has been in the area of prosthetic limbs and body parts. Recently, a seven year old California girl received a new 3D printed prosthetic hand that was created for only $50.
Clearly this is one of the most inspiring and uplifting ways that 3D printing technology can touch lives for the better, but it’s not just for humans.
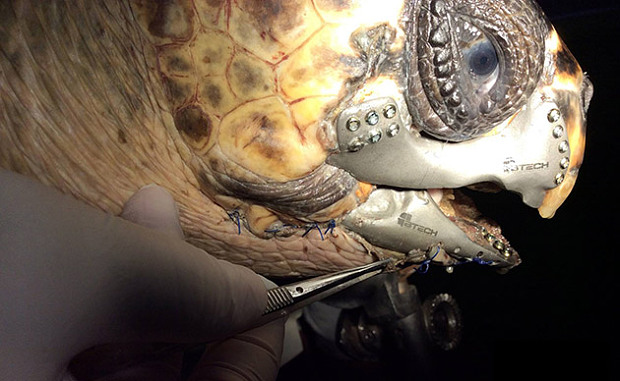
In the last few days, a loggerhead turtle that was gravely wounded in an accident with a boat propeller received a brand new 3D printed jaw. Without its brand new 3D printed titanium jaw, the turtle would have had to spend a lifetime in captivity, unable to fend for itself in the wild.
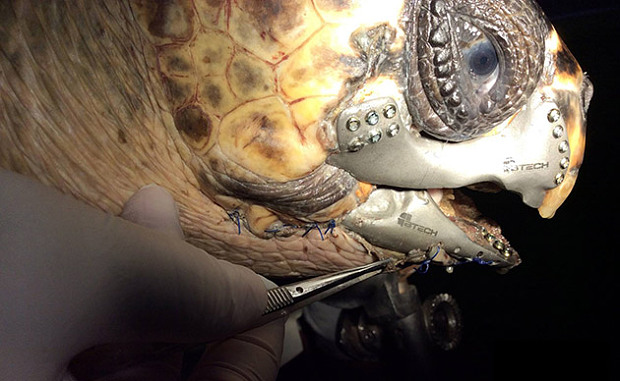
Photo: BTech Innovation
What most excites you about 3D printing. I’d love to hear from you on Twitter or Facebook.
Title image courtesy of CNN.com
![]()
![]()