A poor crypto implementation in the Blockchain Android app results in lost Bitcoin for a number of affected users.
Monthly Archives: May 2015
Flash Timing Side-Channel Data Exfiltration
Flash by design allows local SWF files to read arbitrary local files, but prevents communication with remote servers. By smuggling data through a timing side-channel, this can be circumvented, allowing local SWF files to exfiltrate the contents of arbitrary local files to the internet.
Three reasons to be excited about: drones
Much like selfies, drones have a love/hate status with the public. On one hand, they are fun and useful tool for hobbyists and scientists but their popularity has been hampered by privacy and security concerns.
Several large scale public events such as the Super Bowl have announced they are “No Drone Zones” and the reasons are certainly understandable. The highly affordable nature of drones and their ability to carry a payload (either a camera or something more nefarious) can be a major security concern for officials.
While authorities and companies grapple with the complexities of bringing drone services to the market and how to legislate them, it leaves us some time to contemplate the exciting ways that drones could be used in the future.
Transport:
Just this week a Canadian broke the Guinness World Record for the longest hover-board flight standing on a large drone.
While this is still some way away from being a viable transport alternative, the proof of concept shows that humans, as much as anything else, can be viable cargo for drones.
As we continue to look for viable and more environmentally friendly personalized transport, drones could well hint at a solution.
Conservation:
One of the most inspiring use for drones that I’ve seen in recent months is the Air Shepherd project in Africa where rangers are using drones to help combat poaching of big game animals such as rhinos and elephants.
Faced with a limited budget and vast swathes of land to protect, drones have become a vital tool to help conservationists patrol boundaries, track animals and crack down on illegal hunting and poaching even at night.
Business:
Companies like Amazon have brought drone delivery into the public conscience and it’s easy to see why they are keen to get the service off the ground. Using drones to deliver goods and services to clients brings a whole raft of new opportunities for businesses and a new world of convenience for purchasers.
The idea that within moments of placing an order online, whether for a tin of paint or for a pizza, a drone will be sent directly to your exact location carrying your order is nothing short of incredible.
The days of having to stay home to take a delivery look numbered and very soon anything we could need will be just a click away from flying directly to us.
What are the uses for drones that most excite you? Let me know on Twitter or on Facebook.
Title image courtest of The Volt Report
![]()
![]()
Android’s factory reset may leave data behind
We’ve given tips in the past about what you could do with an older smartphone, and a few of those involved donating it to charity or selling it. A vital step before doing either of these is to perform a factory reset to clear out your data. New research has emerged that says that a factory reset may not be enough to keep your data safe from some more advanced data retrieval techniques.
Researchers at Cambridge University have just released a study outlining several flaws in the way most Android handsets handle factory resets. The issue arises from the way devices store information on flash memory. Reading data has a negligible impact on flash drives, but writing new data to them can cause considerable wear.
To prolong the drive’s health, instead of deleting content directly (“writing off” the data), flash drives will instead designate memory blocks where the data resided as “logically deleted”–meaning they are available to be overwritten.
So when you perform a factory reset, those “logically deleted” content blocks aren’t being overwritten, as they are already considered “empty” by the system. Given enough time and the right tools, the researchers were able to retrieve personal data such as photos and chat logs. They were also able to retrieve the master tokens for automatically signing in to Gmail and other Google apps as well as Facebook apps an alarming 80% of the time.
How to protect your data
If you are looking to sell or donate your phone, there are a few things you can do to help keep your data private. We suggest you do all of these steps:
Encrypt your phone before factory resetting your data.
Devices running Android 3+ or above all allow you to encrypt your phone. The option can generally be found in the settings under the Security tab. Encrypting your phone before the reset ensures that any data that survives the factory reset has to be decrypted.
The Cambridge researchers were able to retrieve some encrypted data and run brute strength attacks until they found the right passwords. So make sure you create a long password of over 15 characters, using upper and lower cases, numbers and symbols: a longer, more complex password would take years to crack. Ideally, use a password generator: you don’t have to remember this password, since you’re “erasing this data”. Now complete the factory reset.
Remove your device from your Google account
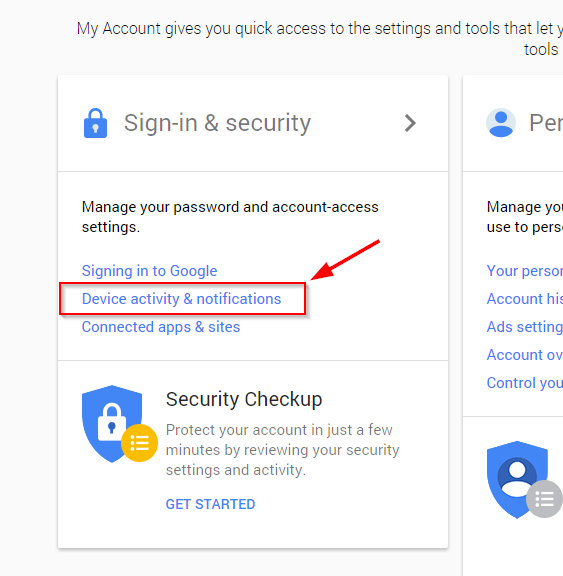
From a browser on a new device, go to myaccount.google.com. Under Sign-in & Security you’ll find the Device activity & notifications section, which allows you to review all the devices currently connected to your account.
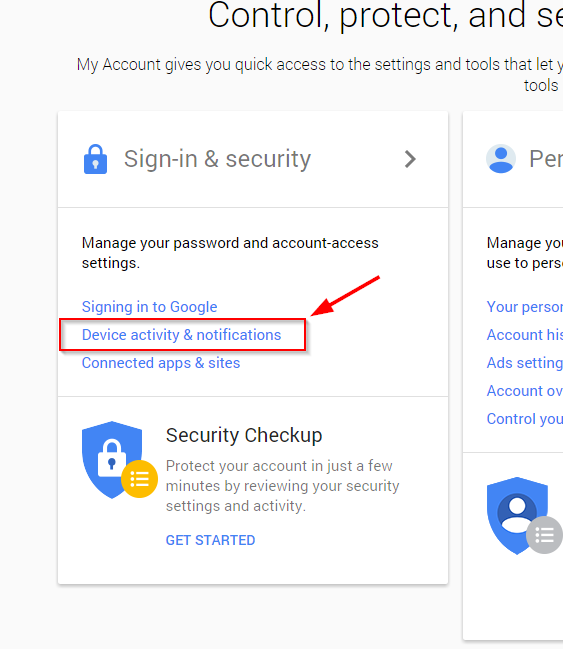
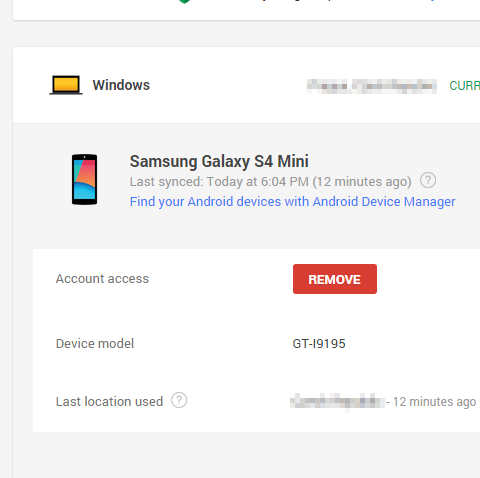
Select your old device, and Remove it. This will prevent any automatic sign-ins from your old device.
Change your account passwords
Changing passwords regularly is simply good digital hygiene, so it makes a lot of sense to change your passwords when changing devices. Even if a hacker were to somehow retrieve your passwords to your Facebook or Google accounts after the factory reset, they would no longer work.
Though the risks of your data being exploited this way are relatively low, it pays to take extra precautions. With these three steps, you should be reasonably secure from even a determined criminal.
As always, stay safe out there!
![]()
![]()
Google to add permission controls in upcoming Android M
At the Google I/O event in San Francisco, the company announced a number of changes to its Android mobile operating system, including the option to deny any app individual permissions.
The post Google to add permission controls in upcoming Android M appeared first on We Live Security.
![]()
CVE-2013-7441
The modern style negotiation in Network Block Device (nbd-server) 2.9.22 through 3.3 allows remote attackers to cause a denial of service (root process termination) by (1) closing the connection during negotiation or (2) specifying a name for a non-existent export.
CVE-2014-9727
AVM Fritz!Box allows remote attackers to execute arbitrary commands via shell metacharacters in the var:lang parameter to cgi-bin/webcm.
CVE-2015-0200
IBM WebSphere Commerce 6.x through 6.0.0.11 and 7.x before 7.0.0.8 IF2 allows local users to obtain sensitive database information via unspecified vectors.
CVE-2015-0751
Cisco IP Phone 7861, when firmware from Cisco Unified Communications Manager 10.3(1) is used, allows remote attackers to cause a denial of service via crafted packets, aka Bug ID CSCus81800.
CVE-2015-0752
Cross-site scripting (XSS) vulnerability in Cisco TelePresence Video Communication Server (VCS) X8.5.1 allows remote attackers to inject arbitrary web script or HTML via a crafted URL, aka Bug ID CSCut27635.