AMSTERDAM, February 18, 2015 – AVG Technologies N.V. (NYSE: AVG), the online security company for 197 million active users and 101 million mobile users, today reported results for the fourth quarter and fiscal year ended December 31, 2014.
Key highlights
- Total revenue for the quarter at $100.2 million
- Subscription revenue showed double digit growth both for the quarter and full year
- Total revenue for the year at $374.1 million
- Total user count increased to 197 million
- Achieved 100 million mobile user milestone, growing 50% year over year
- Successful launch and continued acceleration of AVG Zen roll out
- Completed acquisitions of Locations Labs, Norman Safeground and Winco to support core elements of our strategy including mobile, channel and geographic expansion
- Non-GAAP diluted EPS was $1.91 and GAAP net income per diluted ordinary share was $ 1.02 for the full year
“Our fourth quarter confirmed another good year for AVG. Our pivot of the business and focus on predictable, sustainable subscription revenue already had strong traction which we accelerated with our fourth quarter execution. The acquisitions we completed are a key complement to our development activities.” commented Gary Kovacs, CEO of AVG. “In 2014 we repositioned AVG as the online security company and made great progress in delivering an easy to use, integrated set of security offerings to protect devices, data and people. We believe that our strong user base and growing mobile success, underpinned by our AVG Zen product and increasing SMB presence, means we are well-positioned to deliver in 2015 and beyond.”
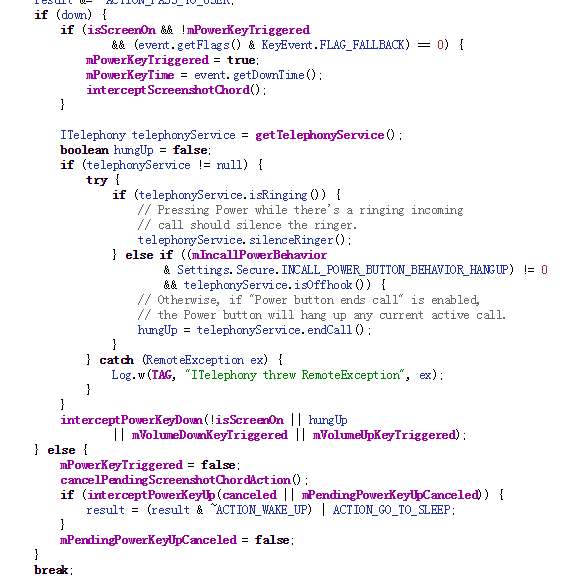
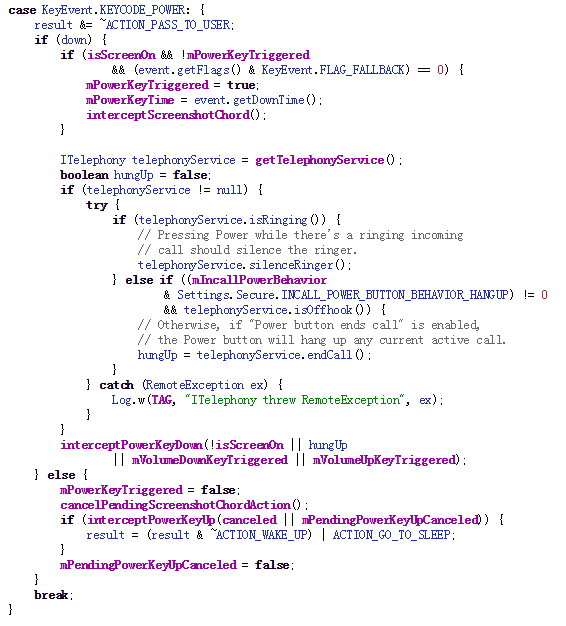
Fourth quarter 2014
Subscription revenue increased 15% over the same period one year ago to $77.4 million. The increase in subscription revenue was the result of growth in both the consumer and SMB segments of the business. Platform-derived revenue was $22.7 million, impacted by the Google policy changes and our continued exit from the third party search distribution business. Total revenue for the fourth quarter of 2014 was $100.2 million, which we estimate would have been $102.5 million on a constant currency basis. This compares to $101.9 million in the fourth quarter of 2013.
We completed a number of acquisitions in the fourth quarter, out of which Location Labs was the largest yet undertaken by AVG and accelerates our mobile monetization. During the fourth quarter AVG entered into a $280 million credit facility consisting of a $230 million term loan and a $50 million revolver facility. The term loan was fully drawn down and the revolver facility was left undrawn as of December 31st, 2014.
We delivered non-GAAP adjusted net income for the fourth quarter of 2014 of $16.2 million, or $0.31 per diluted ordinary share. This compares with non-GAAP adjusted net income of $28.2 million, or $0.52 per diluted ordinary share for the same period of the prior year[1] with the difference being attributable to expenses during the fourth quarter associated with newly incurred debt and acquisitions.
GAAP net income for the fourth quarter of 2014 was $4.6 million, or $0.08 per diluted ordinary share. This compares with GAAP net income of $12.8 million, or $0.23 per diluted ordinary share in the prior year’s fourth quarter.
GAAP net cash provided by operating activities was $35.2 million for the quarter, compared with $32.9 million for the same period in the prior year. Non-GAAP free cash flow was $27.7 million for the quarter, compared with $28.7 million for the same period in the prior year.
Fiscal Year 2014
Subscription revenue increased 12% to $281.6 million from $250.8 million year over year. Our consumer subscription business grew 11% to $223.1 million and our small business segment by 18.7% to $58.5 million. For the fiscal year 2014, total revenue was $374.1 million.
Non-GAAP adjusted net income for 2014 was $100.4 million, or $1.91 per diluted ordinary share. This compares to non-GAAP adjusted net income of $118.2 million, or $2.16 per diluted ordinary share, for the prior year. The year over year difference was largely driven by expenses in 2014 associated with newly incurred debt and acquisitions.
GAAP net income for fiscal year 2014 was $54.4 million, or $1.02 per diluted ordinary share, based on 52.6 million weighted-average diluted ordinary shares outstanding, compared with net income of $63.7 million, or $1.16 per diluted ordinary share, based on 54.7 million weighted-average diluted ordinary shares outstanding, for fiscal year 2013.
AVG generated $108.8 million in cash from operating activities in fiscal year 2014, compared to $145.2 million for the prior year. Non-GAAP free cash flow was $93.2 million for fiscal year 2014, compared with $128.5 million for fiscal year 2013.
During 2014, we repurchased 1.9 million shares at a total cost of $35.3 million under our share repurchase program, which was approved in 2013.
Financial Outlook
Based on information available as of February 18, 2015, AVG is confirming the following outlook for fiscal year 2015:
- Revenue is expected to be in the range of $410 million to $430 million.
- Non-GAAP adjusted net income is expected to be in the range of $94.2 million to $99.2 million; non-GAAP diluted EPS is expected to be in the range of $1.80 to $1.90.
- GAAP net income is expected to be in the range of $48.9 million to $53.9 million; GAAP net income per diluted ordinary share is expected to be in the range of $0.93 to $1.03.
AVG’s expectation of non-GAAP adjusted net income and non-GAAP diluted EPS for the fiscal year 2015 excludes share-based compensation expense, acquisition amortization and certain other adjustments, and assumes a normalized tax rate of 12.5%. For the purpose of calculating GAAP net income per diluted ordinary share and non-GAAP diluted EPS, the Company assumes approximately 52.6 million weighted-average diluted ordinary shares outstanding for the full year.
Conference Call Information
AVG will hold its quarterly conference call today at 23:00 CET/5:00 p.m. ET/2:00 p.m. PT to discuss its fourth quarter 2014 and full fiscal year 2014 financial results, business highlights and outlook. The conference call may be accessed via webcast at http://investors.avg.com or using the following phone numbers and conference ID: +1 646 254 3363 (USA); +1 416 216 4141 (Canada); +44 (0)20 3427 1909 (UK); Conference ID: 5098060.
A live version and replay version of the webcast can be accessed via http://investors.avg.com.
Use of Non-GAAP Financial Information
This press release contains supplemental non-GAAP financial measures that are not calculated in accordance with U.S. GAAP. These non-GAAP measures provide additional information on the performance or liquidity of our business and so we believe are useful for investors.
Adjusted net income, free cash flow and their related ratios are non-GAAP measures and should not be considered alternatives to the applicable U.S. GAAP measures. In particular, adjusted net income, free cash flow and their related ratios should not be considered as measurements of our financial performance or liquidity under U.S. GAAP, as alternatives to income, operating income or any other performance measures derived in accordance with U.S. GAAP or as alternatives to cash flow from operating activities as a measure of our liquidity.
Adjusted net income and free cash flow are measures of financial performance and liquidity, respectively, and have limitations as analytical tools, and should not be considered in isolation from, or as substitutes for, analysis of our results of operations, including our operating income and cash flows, as reported under U.S. GAAP. We provide these non-GAAP financial measures because we believe that such measures provide important supplemental information to management and investors about the Company’s core operating results and liquidity, primarily because the non-GAAP financial measures exclude certain expenses and other amounts that management does not consider to be indicative of the Company’s core operating results or business outlook or liquidity. Management uses these non-GAAP financial measures, in addition to the corresponding U.S. GAAP financial measures, in evaluating the Company’s operating performance, in planning and forecasting future periods, in making decisions regarding business operations and allocation of resources, and in comparing the Company’s performance against its historical performance. Some of the limitations of adjusted net income and free cash flow and their related ratios as measures are:
- they do not reflect our cash expenditure or future requirements for capital expenditure or contractual commitments, nor do they reflect the actual cash contributions received from customers;
- they do not reflect changes in, or cash requirements for, our working capital needs;
- although amortization and share-based compensation are non-cash charges, the assets being amortized will often have to be replaced in the future and such measures do not reflect any cash requirements for such replacements; and
- other companies in our industry may calculate these measures differently than we do, limiting their usefulness as comparative measures.
Because of these limitations, investors should rely on AVG’s consolidated financial statements prepared in accordance with U.S. GAAP and treat the Company’s non-GAAP financial measures as supplemental information only.
For a reconciliation of these non-GAAP financial measures to the most directly comparable financial measures prepared in accordance with U.S. GAAP, please see “Reconciliation of GAAP measures to non-GAAP measures”. All non-GAAP financial measures should be read in conjunction with the comparable information presented in accordance with U.S. GAAP.
Forward-Looking Statements
This press release contains forward-looking statements within the meaning of the Private Securities Litigation Reform Act of 1995, including those relating to an expected range of revenue, net income, net income per diluted ordinary share, non-GAAP adjusted net income and non-GAAP EPS for the fiscal year ending December 31, 2015 and/or future periods, as well as those relating to the future prospects of AVG. Words such as “expects,” “expectation,” “intends,” “assumes,” “believes” and “estimates,” variations of such words and similar expressions are also intended to identify forward-looking statements. These forward-looking statements involve risks and uncertainties that could cause actual results to differ materially from those contemplated herein. Factors that could cause or contribute to such differences include but are not limited to: changes in international and national tax regulations and related proposals; changes in the Company’s growth strategies; changes in the Company’s future prospects, business development, results of operations and financial condition; the anticipated costs and benefits of the Location Labs and other acquisitions; the Company’s ability to comply with its credit agreements; changes to the online and computer threat environment and the endpoint security industry; competition from local and international companies, new entrants in the market and changes to the competitive landscape; the adoption of new, or changes to existing, laws and regulations; flaws in the assumptions underlying the calculation of the Company’s key metrics, including the number of the Company’s active users, revenue per average active user, subscription revenue per subscriber and platform revenue per thousand searches; the potential effects of changes in the applicable search guidelines of our search partners, including the Company’s and its competitors’ responses to these changes; the termination of or changes to the Company’s relationships with its partners, including Google, Yahoo! and other third parties; changes in the Company’s and its partners’ responses to privacy concerns; the ability for the Company to successfully diversify its portfolio of search partners; the Company’s plans to launch new products and online services and monetize its full user base; the performance of the Company’s products, including AVG Zen; the Company’s ability to attract and retain active and subscription users; the Company’s ability to retain key personnel and attract new talent; the Company’s ability to adequately protect its intellectual property; flaws in the Company’s internal controls or IT systems; the Company’s geographic expansion plans; the outcome of ongoing or any future litigation or arbitration, including litigation or arbitration relating to intellectual property rights; the Company’s legal and regulatory compliance efforts; and worldwide economic conditions and their impact on demand for the Company’s products and services. Given these risks and uncertainties, you should not place undue reliance on these forward-looking statements.
Further information on these factors and other risks that may affect the Company’s business is included in filings AVG makes with the U.S. Securities and Exchange Commission (SEC) from time to time, including its Annual Report on Form 20-F, particularly under the heading “Risk Factors”.
The financial information contained in this press release should be read in conjunction with the consolidated financial statements and notes thereto to be included in the Company’s reports on Form 6-K and Form 20-F. The Company’s results of operations for the fourth quarter and the full year ended December 31, 2014 are not necessarily indicative of the Company’s operating results for any future periods.
These documents are available online from the SEC or in the Investor Relations section of the Company’s website at http://investors.avg.com. Information on the AVG website is not part of this release. All forward-looking statements in this press release are based on information currently available to the Company, and AVG assumes no obligation to update these forward-looking statements in light of new information or future events.
About AVG
AVG is the online security company providing leading software and services to secure devices, data and people. Over 197 million active users, as of December 31, 2014, use AVG´s products and services. AVG’s Consumer portfolio includes internet security, performance optimization, and personal privacy and identity protection for mobile devices and desktops. The AVG Business portfolio – delivered by managed service providers, VARs and resellers – offers IT administration, control and reporting, integrated security, and mobile device management that simplify and protect businesses.
All trademarks are the property of their respective owners.
Investor relations contacts:
Europe: Camelia Isaic
Tel. +420 702 205 848
Email: [email protected]
US: Scott McMullin
Tel: +1 415 741 9860
Email: [email protected]
IR team email: [email protected]
IR website: http://investors.avg.com
[1] Non-GAAP adjusted net income for the fourth quarter of 2014 excludes $2.7 million in share based compensation expense, $6.7 million in acquisition amortization, $1.2 million in acquisition-related costs, $1.5 million in restructuring, legal and other charges, $0.6 million in unwinding of discounts and changes in fair value, adjusted for $1.4 million in net reversal of capitalized development charges, together with a $0.3 million adjustment to normalize to a tax rate of 12.5%, as described in the Reconciliation of GAAP measures to non-GAAP measures.