Do you regularly lose connectivity to your Wi-Fi network at home? Are network speeds so low that it takes forever to even copy a simple picture or music file across your PCs – let alone stream video? In this two-part series, we are covering the most important lessons and tips for boosting wireless (WLAN) throughput across your home network. Ready? Let’s dive in!
Figure out the best possible router position
Have you wondered why your wireless signal is strong in some rooms and incredibly weak in others? It’s not only a matter of distance between your wireless router and your PCs or laptops. It’s also a matter of what objects (walls, doors, furniture, electrical equipment/outlets) interfere with a good signal.
In many scenarios, you will be able to boost wifi strength significantly by just repositioning either your router or the connected PCs slightly.
Now, the “Trial and error” method works eventually, but is a waste of time. To get the best possible location you need to create a visualization of network coverage across your home. Heatmapper, a free software for Windows, will do just that:
Click here to download Heatmapper (100 MByte). Note: A registration is required to download this free tool.
After installation, the program asks you if you’ve got a map of your map of your floor – no worries, if you don’t, you can create this heatmap based on a grid. Simply walk around your apartment or house with a laptop in your hand running Heatmapper. As you walk (slowly!), use the left-click button frequently as you walk. Walk through all the areas of your home left-clicking as much as you can.
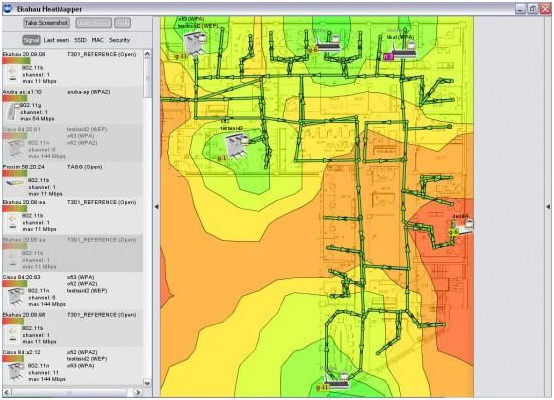
When you’re done, right click and HeatMapper will create a map of your home, showing you where the Wi-Fi signal is stronger or weaker. Here’s how my map at home looks like:
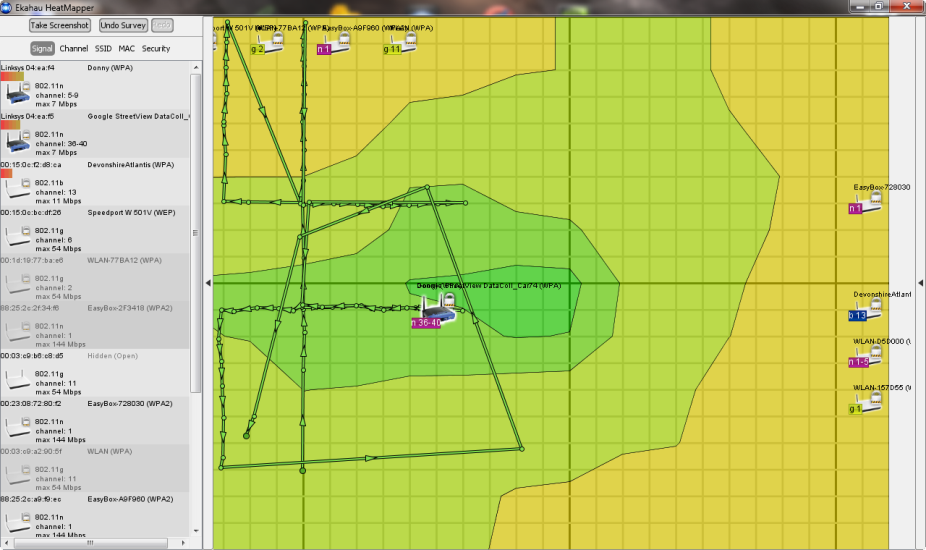
The green area in the middle is also the center of my apartment – a good location for the router! However, in the bedroom (upper part of the screen) I only get „ok“ wireless strength because the router is blocked by three walls.
By looking at the heatmap, I quickly knew where to position the router in order to get a better Wi-Fi signal!
General advice: Make sure not to position the router directly on the floor or next to thick walls. Ideally, the best position is in the center (probably the corridor) of your apartment with no or minimal objects blocking the signal!
Use the latest drivers and firmware
It’s rare to find firmware for a router or driver for a network adapter that works perfectly right out of the gate. Most „V1“ drivers and firmwares of network equipment I have used were bad and came with all sorts of problems: slow connections, drop outs, missing features and other quirks. The first thing I always do when I get a new network device is: look for updates!
For example, when I bought my Linksys WUSB600N adapter it didn’t work (at all!) under the 64-bit-version of Windows 7. I actually bought the device and couldn’t use it for a couple of weeks until the manufacturer delivered an updated driver that worked under the x64 architecture.
Upgrading the firmware of your router has become somewhat easy over the past couple of years: Simply open up the firmware configuration page in your browser (see below) and find the „Firmware Upgrade“ page.

Here you will find direct links to drivers for some popular router manufacturers:
These links will you to the most recent Wi-Fi drivers available. Your wireless adaptor is not on the list? You haven’t found anything using popular search engines? Hit the comment section and provide us with the detailed specs of the Wi-Fi adaptor as shown in your device-manager.
Upgrade your Wi-Fi hardware
If you’re using the 802.11g (or even b/a) wireless standard, more bandwidth-related tasks such as video streaming, launching remote applications or file copy operations will be painfully slow. All three network standards provide a relatively low maximum bandwidth:
Theoretical speed
| 802.11 (1997) |
2 MBps |
| 802.11a (1999) |
54 MBps (short range, high cost – mostly in business use) |
| 802.11b (1999) |
11 MBps (slower, but higher range than a) |
| 802.11g (2002) |
54 MBps (long signal range) |
| 802.11n (2006) |
300 MBps (through multiple channels and frequencies) |
| 802.11ac (2012) |
1 GBps (through multiple channels and frequencies) |
As you can see, 802.11ac is the way to go these day– over the next couple of months, it’ll replaced the older 802.11a/b/g networks, and offers much improved speed, coverage and reliability. In general, 802.11n is at least twice as fast than its predessor “n” while promising theoretical speeds of up to 1000 Mbp/s.
If you’re suffering from a low network bandwidth, be sure to pick a router and Wi-Fi adapters that supports at least the 802.11n specification. If you bought a PC or laptop within the last couple of years, it’ll (very likely) have a 802.11ac wireless adapter. To go check, simply fire up Device-Manager…
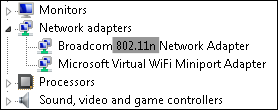
…or take a look at your hardware specification sheet, for example:
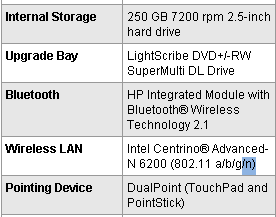
If your adapter does not support 802.11n or ac but your router does, it’ll obviously use the lower N, G, B or even A modes. So make sure that all parts of your wireless chain are “n” compatible!
When shopping for a new network adapter or a router that supports 802.11ac, you should take the following three tips into consideration.
Pick a dedicated USB adapter:
Even if your laptop or desktop has a built-in 802.11ac adapter that is connected to a full-fledged 802.11n router, you might want to look into getting a dedicated (external) USB wireless adapter. Sounds ridiculous, but in my experience many external Wi-Fi adapters perform much better than built-in devices.
When I first got my Linksys WRT610N router, I got quite mixed results and only an average of 100-170 Mbps when the theoretical limit of this beast is around 300 Mbps. So I drank the cool-aid and ordered the adapter that, according to the manufacturer Linksys, “works best with” my router – the WUSB600N USB wireless adapter! And what a difference that made: Signal strength did not change, but the speed went up significantly. Here’s a screenshot of my laptop that’s using both the built-in Wi-fi chip as well as the external USB adapter to connect to the router:
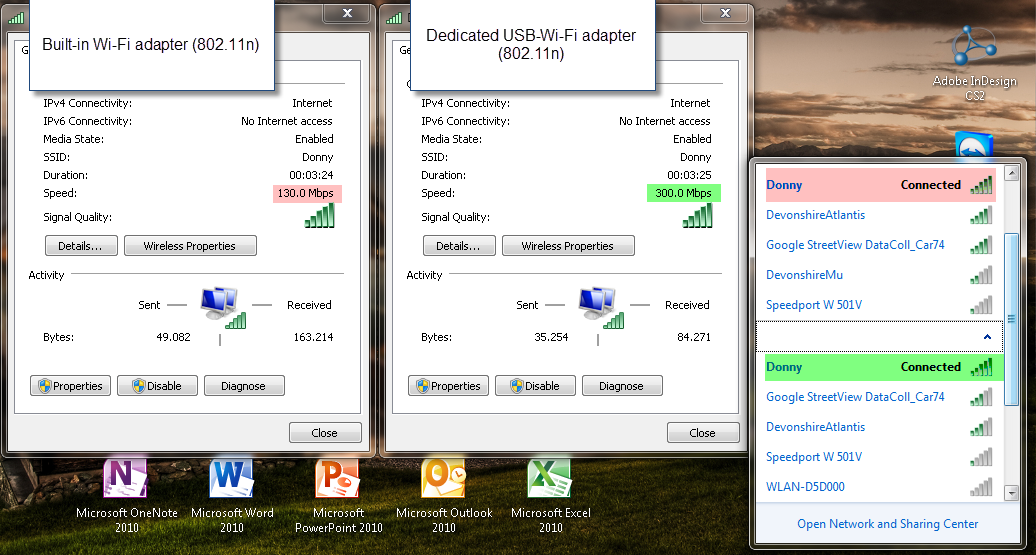
The maximum speed meter went up from 130 Mbps to 300 Mbps. Of course, that is the peak value, but only with this little addition was I able to stream full-definition 1080p video across my apartment with no stuttering or delay whatsoever.
Stay in the family: Besides using external dedicated Wi-Fi devices, I’d also recommend to pick a router and the adapter from the same company. Now, that doesn’t mean that a Linksys router wouldn’t work with a Broadcom or D-Link network adapter, but it’s also my experience that you get the best-possible performance if you „stay in the family“. Now I know that this is what the manufacturer wants but in this case I’d go with it.
Use an external antenna for your router. You can significantly boost your Wi-Fi connection by replacing the antenna or add another external antenna. This guide as well as this one help you figure things out.
Change the Wi-Fi channel
All modern routers are capable of communicating to your PC or laptop on several different channels. However, if your neighbours Wi-Fi equipment is communicating on the same channel, your network speeds and reliability might suffer. Windows offers a built-in solution that lets you see on what channels all your surrounding Wi-Fi networks conmunicate. This is how it works:
Step 1 – Launch the command line. To do that, click on the Start orb, go to „All ProgramsAccessories“ and click on „Command Prompt“.
Step 2 – Type in the following command: netsh wlan show all.
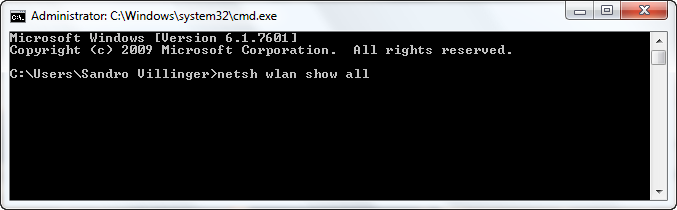
Step 3 – You’ll see a large list of all wireless networks in your area.
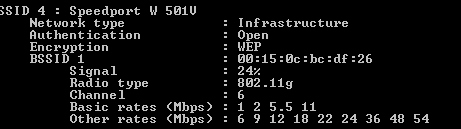
Scroll through the list and watch out for the entry that says „Channel“. Out of those 7 networks, 4 are using channel 6 to send data, two use channel 5 and one is using channel 13.
This is why I should probably choose either a lower channel or a channel between 6 and 13.
Try changing the channel on the routers configuration page.
To open the page, you’ll usually enter it’s IP adress into your browser (check the manual to see which address you need to type in), for example http://192.168.1.1, and enter the user name and password you specified at setup – or the default credentials if you never specified it (which is potentially dangerous)!
Find your wireless channel settings. On my router, that’s under the “Wireless” tab right in the “Basic Wireless Settings” category:
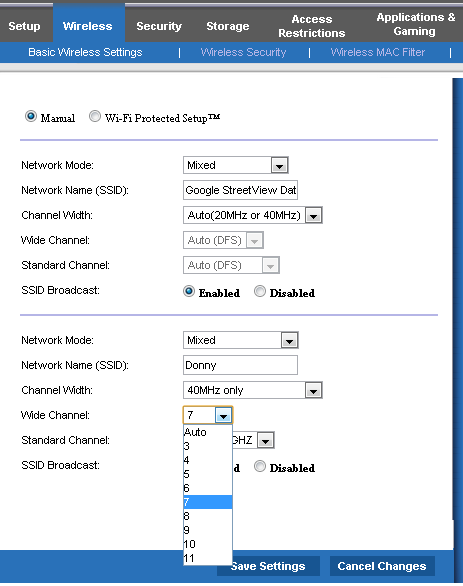
Pick the channel that is not (or barely) used in your area. In my example, I choose channel 10. Reconnect all your devices and see if you’ve got better speed or if you’re reliability issues are fixed!
That was part 1 – look out for part 2 that’ll show you even more in-depth tricks to improve your wireless network speed!