We’ve just released a new update to our AVG Cleaner for Android PRO.
In version 2.2.1 we’ve tweaked one of your favorite features, Battery Profiles, and now support Android L to help you clean up, speed up and especially boost battery life even better than before and on all the bleeding-edge devices out there.
So what’s new?
Despite that it started out as a cleaning app, we’ve made it a super-powerful tool to help you speed up and boost the battery life of your Android and even tell which apps drain your devices mobile data traffic, battery and storage. We’ve continued this tradition in our latest update even more.
Smarter Battery Savings with Battery Profiles
First and foremost, for the folks who love to improve battery life manually, we added a new button called “Choose Manual Settings” which puts you in charge of what features and built-in devices of your Android can drain your battery, such as Wi-Fi, Bluetooth, Mobile Data or the automatic synchronization of your files:
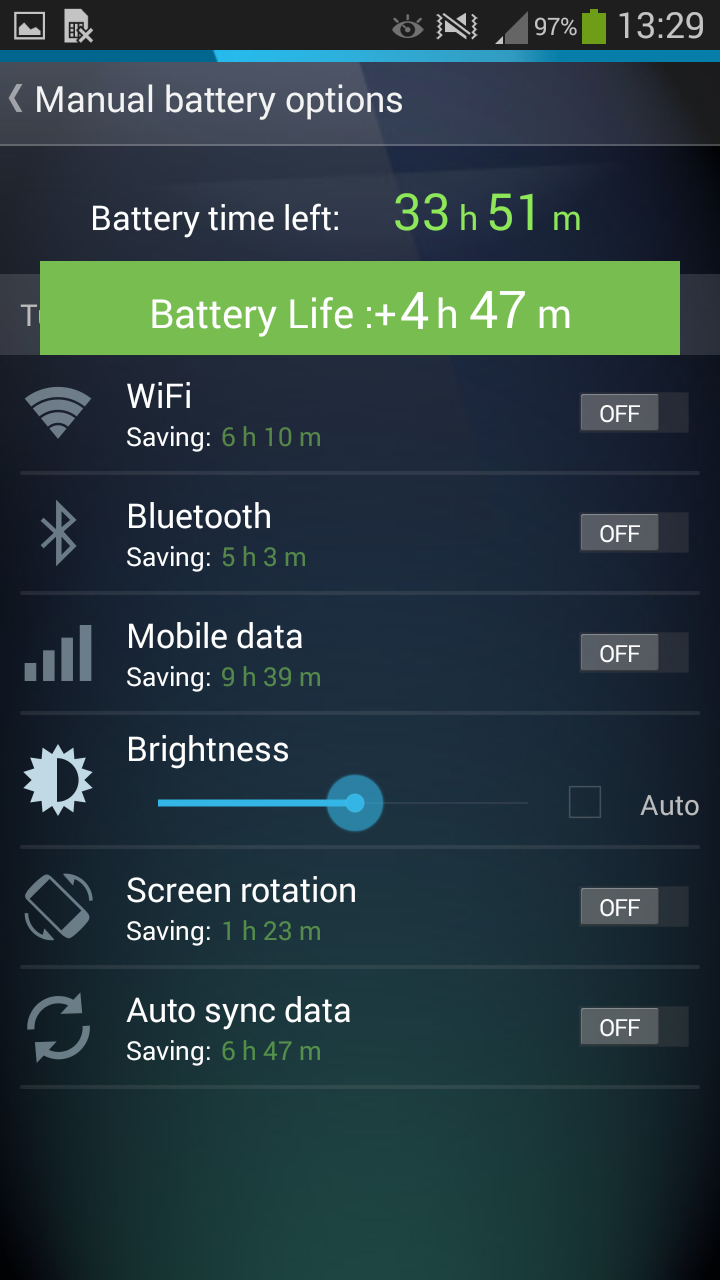
As you can see, we’ve also added new “On/Off” buttons to make it more clear what’s enabled and what’s not – the green indicator now shows you exactly how much battery life you can save with each tweak.
Plus, there’s a new profile called “Low Battery” which is available in the PRO version and kicks in when battery life hits a certain threshold, such as “20%” (you have to run it once and then set it up):
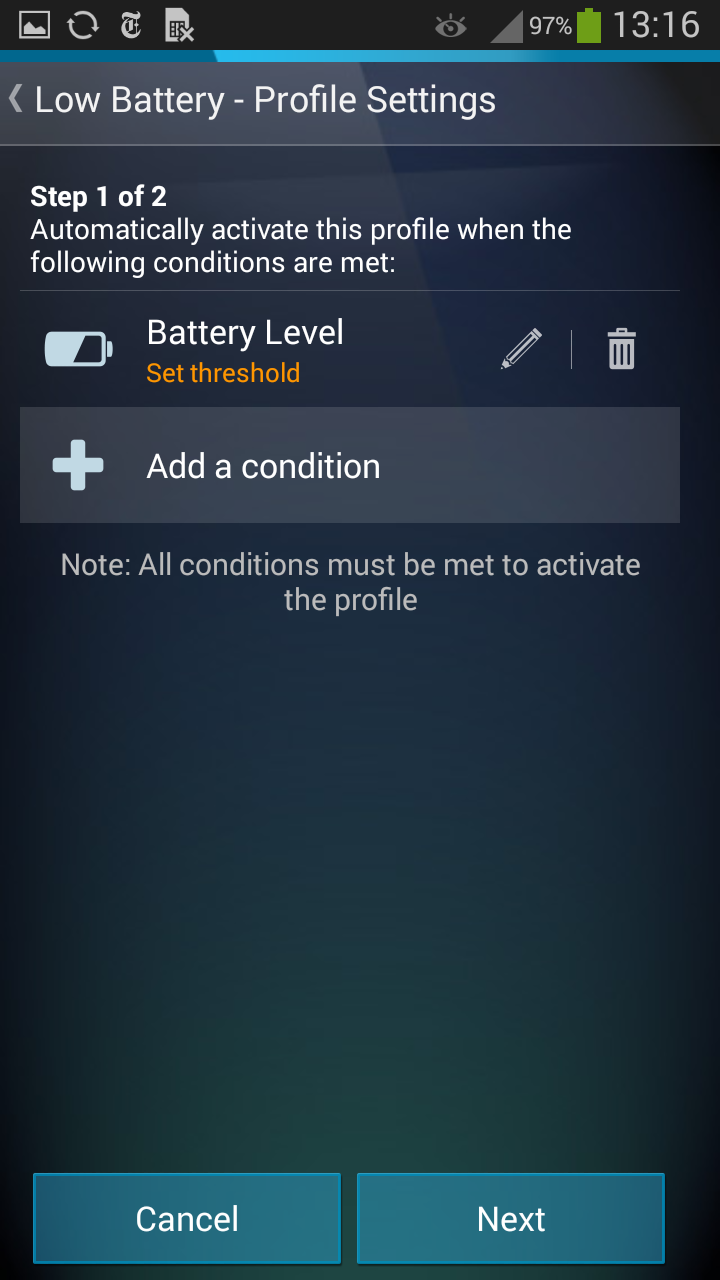
That’s super important when you’re nowhere near a power outlet and the phone is running on fumes. It saved my digital life more than once…
Overall, we’ve also made the “Profiles” easier to set up. Once you select a profile for the first time, such as “Car” (for when you’re on the road), we’ll walk you through what conditions and settings you can set up. In the example of car, I set it up so that AVG Cleaner for Android always disables Wi-Fi, auto-sync, screen rotation and screen time-out whenever it’s connected to the Bluetooth of my car:
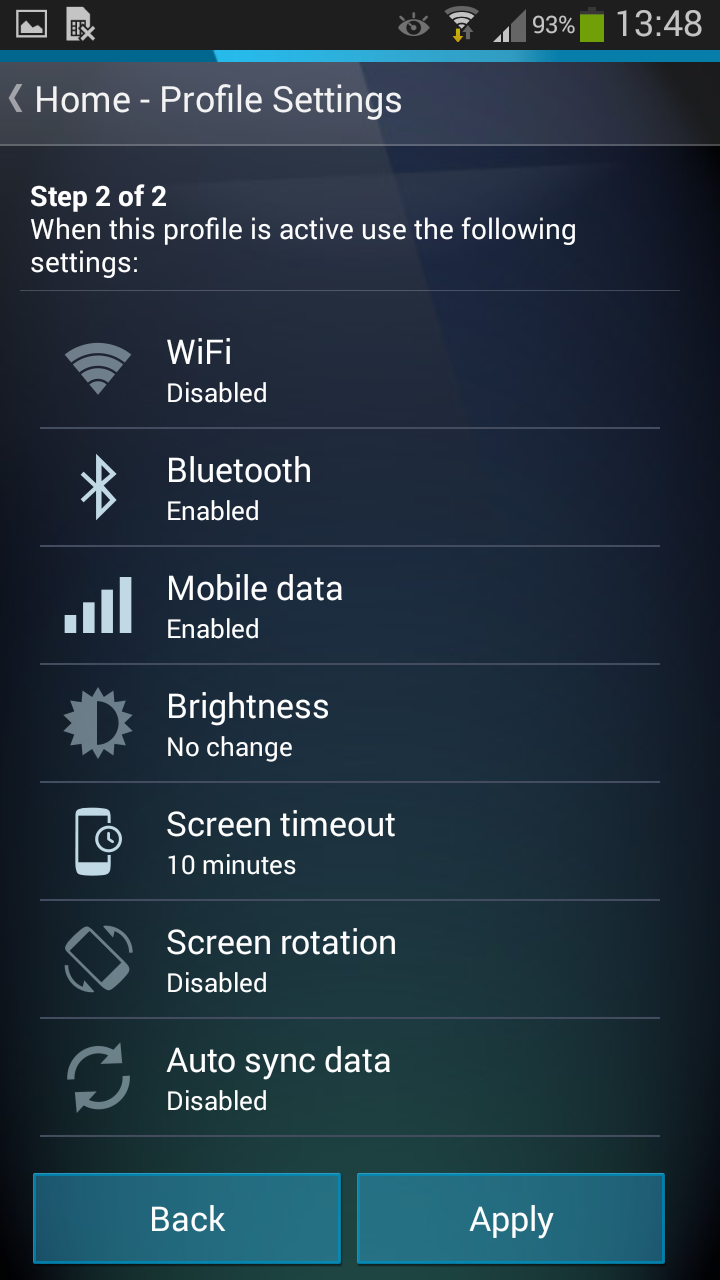
That’s because I don’t need any Wi-Fi in my car. Plus, I’m using the phone as my GPS so I don’t want the screen rotating randomly or turning itself off after a while.
Download AVG Cleaner for Android now.