A couple of days ago, a user posted a comment on our forum regarding apps harboring adware that can be found on Google Play. This didn’t seem like anything spectacular at the beginning, but once I took a closer look it turned out that this malware was a bit bigger than I initially thought. First of all, the apps are on Google Play, meaning that they have a huge target audience – in English speaking and other language regions as well. Second, the apps were already downloaded by millions of users and third, I was surprised that the adware lead to some legitimate companies.
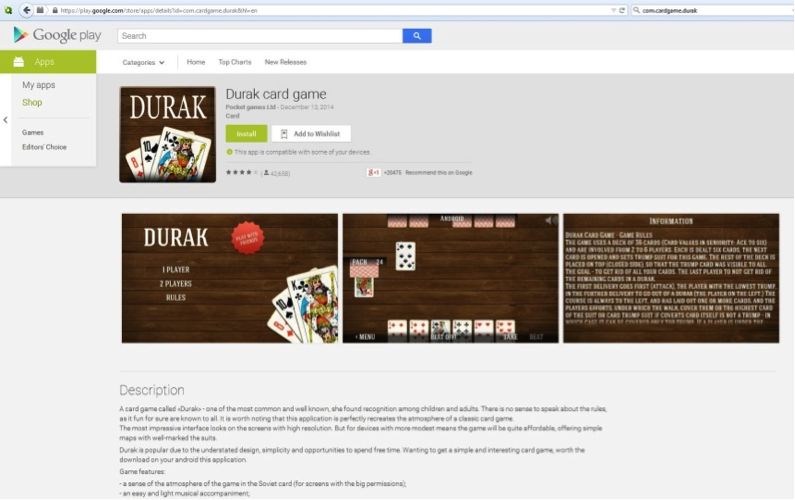 The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.
The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.

When you install Durak, it seems to be a completely normal and well working gaming app. This was the same for the other apps, which included an IQ test and a history app. This impression remains until you reboot your device and wait for a couple of days. After a week, you might start to feel there is something wrong with your device. Some of the apps wait up to 30 days until they show their true colors. After 30 days, I guess not many people would know which app is causing abnormal behavior on their phone, right? ![]()
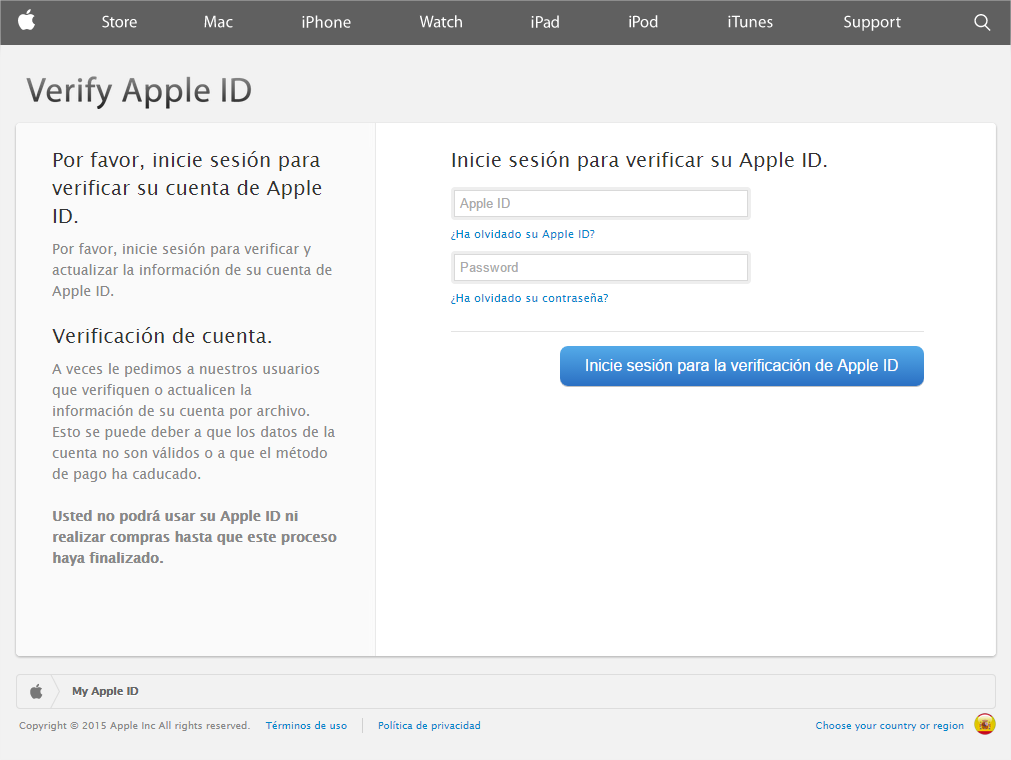
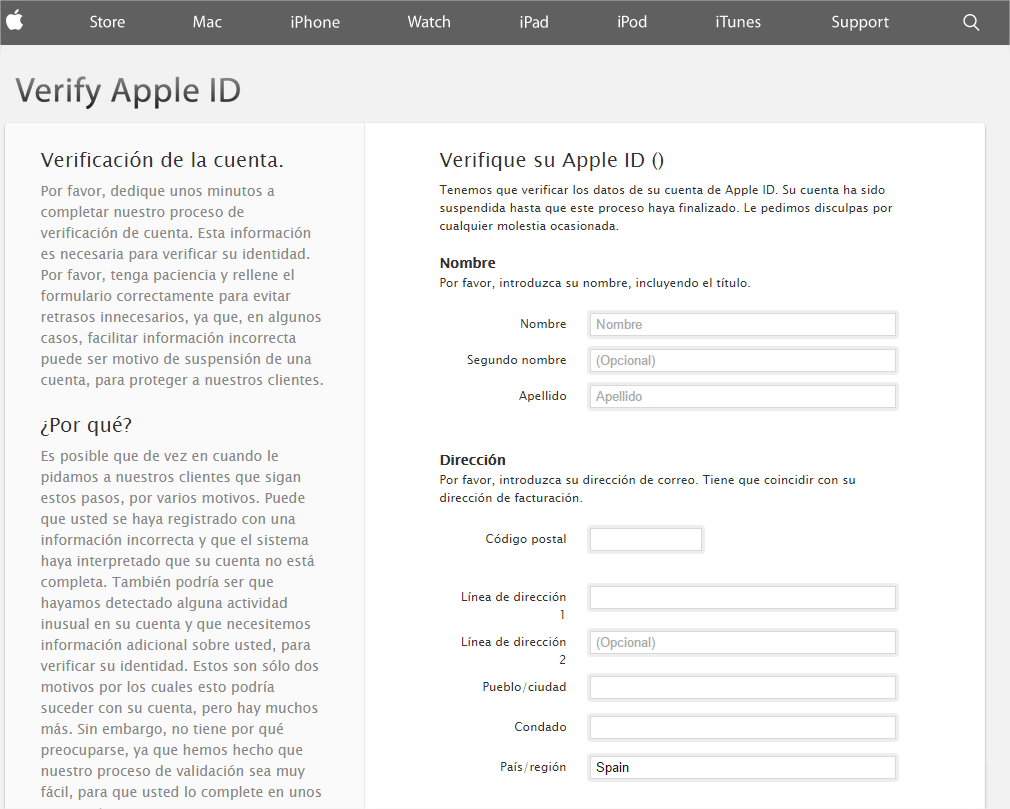
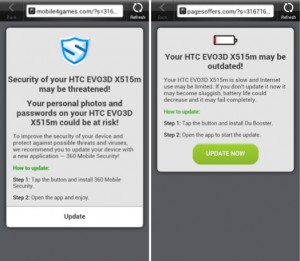 Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.
Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.
An even bigger surprise was that users were sometimes directed to security apps on Google Play. These security apps are, of course, harmless, but would security providers really want to promote their apps via adware? Even if you install the security apps, the undesirable ads popping up on your phone don‘t stop. This kind of threat can be considered good social engineering. Most people won‘t be able to find the source of the problem and will face fake ads each time they unlock their device. I believe that most people will trust that there is a problem that can be solved with one of the apps advertised “solutions” and will follow the recommended steps, which may lead to an investment into unwanted apps from untrusted sources.
Avast Mobile Premium detects these apps, protecting its users from the annoying adware. Additionally, the apps’ descriptions should make users skeptical about the legitimacy of the apps. Both in English and in other languages such as German, were written poorly: “A card game called ‘Durak‘ – one of the most common and well known game“.
The apps‘ secure hash algorithm (SHA256) is the following: BDFBF9DE49E71331FFDFD04839B2B0810802F8C8BB9BE93B5A7E370958762836 9502DFC2D14C962CF1A1A9CDF01BD56416E60DAFC088BC54C177096D033410ED FCF88C8268A7AC97BF10C323EB2828E2025FEEA13CDC6554770E7591CDED462D