Category Archives: Antivirus Vendors
Antivirus Vendors
BlackBerry Messenger. The app that lets you chat only to those you want to.

A few years back, when we discovered that our parents’ business phones could be used for more than just sending emails, something changed. BlackBerry Messenger made everyone want to switch to this new device which let you chat with friends for free.
I have to admit that practically all my friends started out with a BlackBerry and for months we did nothing but send messages back and forth via the application. I remember worrying about whether the message that had been delivered (the famous ‘D’) had been read, or when I didn’t get a reply after a message that had been read (‘R’).
Over time, it became apparent that other apps, such as WhatsApp and Viber offered just as much and more. That’s why we left BB chat behind in favor other messaging apps.
Previously BBM could only be installed on BlackBerry devices, while competitors had versions for all operating systems. But now you no longer need to feel nostalgic about the dancing, hugging icons, because you can now download BBMessenger for Android, iOS or Windows Phone, free.
Though it seems incredible, I still speak with a friend who only has BBM, and what’s more, he has no interest in WhatsApp or other such apps.
The great advantage that it offers, according to my friend, is that you can speak only to whom you want to. BBM continues to work by invitation. This means that to add someone to your contacts they have to give you their app PIN. So in the end you have a list of contacts that you have ‘chosen’. Other than that, the way it works is pretty much the same as before.
New features in BlackBerry Messenger
Perhaps one of the more interesting new features is the BBM store. It’s a sticker store, a bit like Line where you can buy different images to add to your chats.
Another thing you will come across with the new BBM are the chats on the BBM Channels, which could be between people, brands or communities. For example, you could create a new channel to talk about a given topic or sign up to an existing BBM Channel.
What do you think? Do you miss your BBM chats? Vintage is now the latest thing, and they don’t come more vintage then BBM…
The post BlackBerry Messenger. The app that lets you chat only to those you want to. appeared first on MediaCenter Panda Security.
AVG’s Joanna Brace Appointed to MEF North and Latin America Board
MEF members elected ten new regional Board Directors during its recent MEF Global Forum in San Francisco. Among the new directors elected was AVG’s own Joanna Brace, VP Marketing & Product Marketing SMB.
Joanna leads AVG’s business global marketing, product management, product marketing, channels marketing, web marketing and partner enablement teams.
She brings understanding of the ever-changing SMB environment and the needs of todays’ mobile businesses to MEF. “The days when work was confined to an office with four walls and a locked door are gone. Thanks to mobile technology and popular cloud-based applications today’s start-ups are living in a world where doing business without walls is perfectly normal,” Joanna noted.
Judith Bitterli was elected to MEF’s Global Board in October. AVG has been an active MEF member in the policy working group which developed AppPrivacy, part of MEF’s Mobile Initiative, and sponsored exclusively MEF’s Global Consumer Trust Report in 2013 and 2014.

AirHopper, the malware that infects your corporate network even though you are not connected to the Internet
Seems logical, doesn’t it? If your company has ever warned you that you must tread very carefully when browsing the Internet so that your computer (and sooner or later, every computer in the office) does not get infected with a virus, it would be normal to think that going offline is not a bad (although drastic) alternative.
We are very sorry but you cannot rest easy even if the computer you use at work is not connected to the Internet; it is still vulnerable unless you have an enterprise antivirus solution like Panda Advanced Protection Services.

To start, a pen drive can easily replace the Internet for malicious pursuits. Your work computer’s USB port will thereby become your Internet connection, as far as viruses are concerned, as this would be its entrance.
However, USB ports are not your work computer’s only weak spot if you do not have an Internet connection. There are other vulnerabilities that compromise, and greatly, the security of your computer.
One of these vulnerabilities lies in the radio receivers on smartphones and electromagnetic signals, as proven by AirHopper, a malware that can infect a computer and collect data from it without needing it to be online.
Although it sounds complicated, a group of researchers in Israel have proved it in a study: A computer without an Internet connection is also vulnerable. To start, the cyber-crook needs to install AirHopper on the computer. That is undoubtedly the largest hurdle faced by data thieves because unfortunately, the rest is a breeze.
Once AirHopper is installed on the computer, the malware uses the monitor to emit electromagnetic signals whenever a key is pressed. The cyber-criminal, who must be within seven meters of the computer, will need a smartphone with FM radio to receive the data typed on the computer.
According to the researchers, the data can be transmitted from the computer to the cyber-criminal’s smartphone screen at a rate of 13 to 60 bytes per second.
It might not seem like a fast method that downloads large amounts of data but it is fast enough for a cyber-criminal to steal passwords in just 8 seconds or short texts that you type into your work computer.

Fortunately, it is a type of attack that will probably not go beyond being a proof of concept, as in order to carry it out the cyber-criminal needs physical access to the computer in order to infect it, and then needs to be close by in order to receive the data you type on their smartphone. In addition, not all monitors can emit electromagnetic waves that are strong enough.
So now you know; if you want to keep your company secure from these types of threats, request a free demo of Panda Advanced Protection Services and our team of experts will help you with whatever you need.
The post AirHopper, the malware that infects your corporate network even though you are not connected to the Internet appeared first on MediaCenter Panda Security.
Cyber Monday: Costco and Home Depot phishing emails target shoppers
Thanksgiving Day phishing emails leverage this popular American holiday to target consumers who shop at The Home Depot and Costco. Here’s what to watch for, and advice on how to handle such messages.
The post Cyber Monday: Costco and Home Depot phishing emails target shoppers appeared first on We Live Security.
![]()
5 must do’s for a safer Cyber Monday
With so many retailers offering great deals online, its important to be extra wary of cyber criminals looking to take advantage. Keep in mind these 5 must dos on Cyber Monday.
The post 5 must do’s for a safer Cyber Monday appeared first on We Live Security.
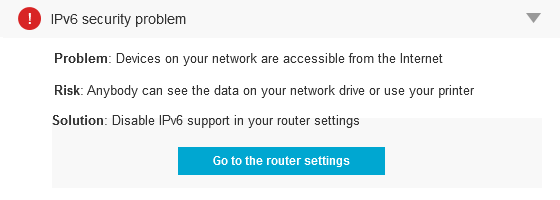
How to disable IPv6 support in your router settings
After the previous articles you should be convinced that router vulnerabilities are one of the major concerns in network security. As you already know, the new Avast 2015 version includes a security feature called Home Network Security (HNS) which scans your network and router for vulnerabilities and prevent threats.
One serious problem occurs when when IPv6 (Internet Protocol version 6) is enabled (both by the ISP and on the router), but there is no IPv6 firewall being used. Which means that anyone on the Internet can access devices on the network (like printers, network disks, etc.). This is often the case because the routers are small, embedded devices that cannot handle IPv6 firewalling.
The main advantage of IPv6 over IPv4 is its larger address space: it allows 2128 or approximately 3.4×1038 addresses (or sites) which is an enormous number! In addition to offering more addresses, IPv6 also implements features not present in IPv4: it simplifies address assignment, network renumbering and packets processing.
In fact, a proper IPv6 firewall requires quite some processing power and RAM, so it’s no wonder that many of the cheap routers don’t have that functionality at all (or it’s not working properly).
The remediation is relatively simple: Just disable IPv6 on the router. In most cases, this shouldn’t have any impact on other services, unless they require IPv6 (in which case, it would be good to replace the router with something better which is IPv6 certified).
Avast Internet Security and Premium products offer full support to IPv6 for your computer on our silent firewall. Take into account that other devices, like network drives connected to the router won’t be protected.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.
League of Legends Bug Bounty Scheme has awarded over $100k
Riot Games, the creator of League of Legends, has paid out over $100,000 to security researchers poring over the game looking for exploits, hacks and bugs, Security Week reports.
The post League of Legends Bug Bounty Scheme has awarded over $100k appeared first on We Live Security.
![]()
Healthcare security needs investment to stave off cyberattacks, says report
A new report from IDC Health Insights claims that healthcare firms need to invest to ensure protections from cyberattacks, according to the Computing website.
The post Healthcare security needs investment to stave off cyberattacks, says report appeared first on We Live Security.
![]()
Infographic: Cyber Monday – Everything you need to know
Cyber Monday is one of the biggest shopping days in the year, and in 2013 a massive $2.3bn was spent on shoppers getting their Christmas bargains in. Where this kind of money is flowing, cybercriminals are also around though, as this infographic shows.
The post Infographic: Cyber Monday – Everything you need to know appeared first on We Live Security.
![]()