Category Archives: Antivirus Vendors
Antivirus Vendors
Spotlight: Threat Visualizations – Software Advice
The Boletos Fraud: An Online Threat to Offline Users
Shellshock, the security hole in Bash that affects Linux and OS X

A security hole has been discovered in Bash that jeopardizes the security of Linux and Mac users. This vulnerability, dubbed ‘Shellshock’, affects the command interpreter in these operating systems.
So what does this mean? To give you an idea, this flaw could allow a cyber-criminal to remotely access a system using Bash and insert spyware designed to steal confidential information or even take control of the system.
The hole was discovered by Stephane Schazeblas and it would appear that it is more serious than Heartbleed, the vulnerability discovered in the OpenSSL library last April. According to the CVSS rating of the security hole, Shellshock has a score of 10, while Heartbleed was rated 5.
What can you do to protect yourself from the Bash vulnerability? Update your software and keep your operating system up-to-date.
* Many thanks to our colleague from Critical Malware, Daniel Garcia, for his help.
The post Shellshock, the security hole in Bash that affects Linux and OS X appeared first on MediaCenter Panda Security.
Week in security: Bash Bug, BlackEnergy and hoax attacks
This week, a serious software vulnerability, which rapidly became known as the ‘Bash Bug’ or ‘Shellshock’ dominated the headlines, as two other faked news stories showed that hoaxes can fool the world very easily these days.
The post Week in security: Bash Bug, BlackEnergy and hoax attacks appeared first on We Live Security.
![]()
What is the Bash bug, and how do I prevent my systems from being Shellshocked?
Shellshock is a newly discovered security flaw that has been around for 22 years, and works by exploiting the very nature of web GUI.
Working in the same way as SQL injection, Shellshock allows users to insert Bash (a Unix-based command processor, or shell) commands into a server via a web form or similar method, and exploits the very nature of environment variable handling, which is that after assigning a function to a variable, any trailing code in the function will be then executed.
Where the SQL injection vulnerability allows a hacker access to the database, Shellshock gives the hacker an authentication-free access to the server, which makes it much more powerful. With this type of access, one with malicious intent could create a worm that could multiply and reproduce the exploit across entire networks to collect or modify data, or open other security holes that would otherwise be closed. Though Bash does not natively run on Microsoft Windows machines, it can be ported, but it is not yet known if the vulnerability will remain present.
Ok, so I get it, it’s dangerous. Am I vulnerable?
Absolutely.
Why?
Because Unix has a much wider grip on our networks than most people can really appreciate. Due to its ubiquity, everything from routers and smartphones, TVs, cars and more could be exploited. Worse, is that many of those devices are very difficult to update. Your home router, for example, has control of all your incoming and outgoing network traffic, and if someone has that, not only do they have the potential to collect your data, but to enable ports, disable the firewall, and further their access into your network infrastructure. With that being said, if you are running any versions of Unix or Mac, and haven’t familiarized yourself with this vulnerability, you’re well overdue.
Luckily, many vendors have now patched for Shellshock by updating Bash, but at this time, Apple users should wait for an update.
I’m running Unix. What do I do now?
First, it’s best to find out if you’re affected. Specifically, are you running Redhat, Ubuntu, Fedora, CentOS (v5-7) CloudLinux, or Debian? If so, then run this command to find out if you’re vulnerable.
$ env x=’() { :;}; echo vulnerable’ bash -c “echo this is a test”
If you see nothing but “this is a test,†you’ve successfully run the exploit, and you’ve got some work to do.
Luckily, most Linux distributions have issued fixes, so you can simply run your update manager. For those who haven’t, you can do so manually by running the following commands:
yum update bash
OR
sudo apt-get update && sudo apt-get install bash
Help, I have a Mac!
Are you infected? Run this command from your shell and find out.
$ env x=’() { :;}; echo vulnerable’ bash -c ‘echo hello’
If you’ve got Mac machines in your environment that can be exploited, you can disable the exploit by temporarily changing the default user shell. For IT administrators that have the know-how, get started right away – but for those that have to ask “how?,†it’s best to keep your eyes peeled and wait for an official update from Apple.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
What to do about Shellshock bash bug on Mac OS X, web servers, routers, and more
The “Bash Bug” or “Shellshock” vulnerability means a wide range of devices, servers and computers, including Mac OS X, will need to be patched to prevent abuse by malicious persons. Here’s advice about what to do and links to more in-depth resources.
The post What to do about Shellshock bash bug on Mac OS X, web servers, routers, and more appeared first on We Live Security.
![]()
4Chan: destructive hoaxes and the Internet of Not Things
The media have associated a number of destructive hoaxes with 4chan: people need some historical perspective on how the site actually works.
The post 4Chan: destructive hoaxes and the Internet of Not Things appeared first on We Live Security.
![]()
Who Dares Wins in The Pitch, UK
On Thursday 18th September more than 40 intrepid small business entrepreneurs – including one  17 year-old – from around the UK assembled in Manchester for the Northern semi-final of The Pitch 2014, the small business competition that this year has AVG as its lead sponsor.  As with the first semi-final in London the event took the form of a Boot Camp during which the competition’s main sponsors provided a series of mentoring workshops designed to help the contestants hone their pitches as they bid to land a coveted place in the Live Final taking place in Bristol on 23rd October.
The AVG workshop – appropriately held in a room called ‘dare’ – centred on overcoming sales objections. Adapted from the classic objection-rebuttal cycle training that AVG provides to IT partners our workshop was based on the premise that entrepreneurs are great at dreaming up ideas for new products and services but are less confident when it comes to dealing with negative responses to their sales proposition.
Led by Mike Byrne, the workshop taught one or two simple techniques for overcoming common sales objections. People were then split into pairs for a role-playing exercise where they had the chance to practice what they’d learnt.  This format seemed to work very well, never failing to break the ice and fully engage the participants. This was reflected in the numerous pieces of positive feedback that we received – a good example being this tweet from RecruitPacks.
Then it was time for the main event. Â Everyone was given just 90 seconds to step up in front of a room full of judges and rivals, pitch their business idea and make the case why they should be selected to go through to the live final. There was a hugely diverse range of start-ups to choose from.
As lead sponsor and one of the judges AVG has the very difficult task choosing between such a high calibre of entries. Of course, AVG is always interested in eye-catching new ideas – especially in tech -Very occasionally, we take more than a passing interest as the recent acquisition of mobile monetization start-up Location Labs demonstrates. If you would like to read more on this why not check out Mike Foreman’s recent interview with BusinessZone, published this week, where he talks more about what companies like AVG look for when weighing up prospective acquisitions and what entrepreneurs can expect.
The Boot Camp had a whole spectrum of businesses: everything from e-book stores and games for teaching numeracy; radon detectives and crime scene cleaners ; Twitter-driven advertising concepts and nano technology; and many more besides. However in one thing Manchester was united. They all shared the same courage and determination. A willingness to push themselves well beyond their personal comfort zones in pursuit of making their business dreams come true.
For some the experience was plainly quite traumatic. But in conquering their nerves they won the sympathy and support of the whole room.  A place in the live final awaits 30 of the top semi-finalists and a chance to present their pitch to a live audience, a panel of judges that will include Judy Bitterli, as well as investors and supporters.
One final word on Manchester to end on. There cannot be many other business contests where people who are technically in fierce competition do so much bonding with their peers and provide so much emotional support for each other. As Dan Martin editor of BusinessZone put it, “There was a lot of love in the room!â€
![]()
![]()
How to identify the warning signs of work-from-home scams
 Home-based jobs are attractive to people who are looking to supplement their regular or retirement income, those who want part-time employment, or those who want to save money on child care or gas. Many people have dreams of being entrepreneurs and working independently of traditional businesses. Cybercrooks take advantage of this to create fake offers for work-from-home opportunities.
Home-based jobs are attractive to people who are looking to supplement their regular or retirement income, those who want part-time employment, or those who want to save money on child care or gas. Many people have dreams of being entrepreneurs and working independently of traditional businesses. Cybercrooks take advantage of this to create fake offers for work-from-home opportunities.
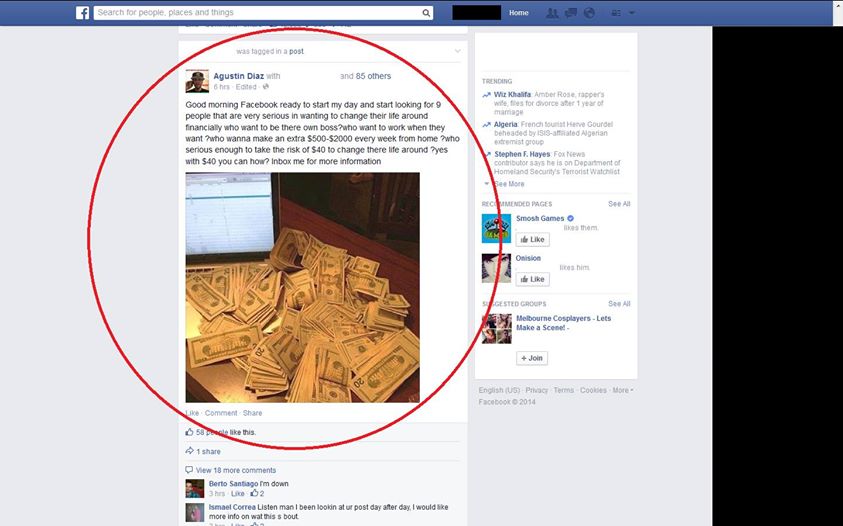
Sharp-eyed avast! Facebook fan, Timothy B., shared a post that he received for a work-from-home scam.
The post says,
Good morning Facebook ready to start my day and start looking for 9 people that are very serious in wanting to change their live around financially who want to be there own boss?who want to work when they want ?who wanna make an extra $500-$2000 every week from home ?who serious enough to take the risk of $40 to change there life around ?yes with $40 you can how? Inbox me for more information
Work-at-home and get-rich-quick schemes have been around for a long time, first appearing in people’s real mailboxes, on TV, and in magazine advertisements. Cybercrooks have created variations of this scam to harvest email addresses and contact lists from Facebook. Social networking makes it easy to create fake profiles and identities quickly.
The grammatically-challenged swindler from Timothy B.’s newsfeed entices potential victims with the ease and flexibility of working from home whenever they want. The message promises big earnings, and all you need to do is make a $40 investment to find out how. This scammer will most likely try to get you to wire money and then collect your personal information.
Warning signs of a work-from-home scam
- No business name or contact address – No legitimate company will advertise for jobs without stating their name, brand identity and physical contact address.
- You’re required to pay a fee for additional information. Legitimate employers don’t charge a fee to hire you or to get you started. Don’t send money for directories or start-up kits.
- Promises of exceptional earnings.
- Claims that no experience is necessary or resume is required.
- Asks for personal information like a Social Security or bank account number over the Internet.
How to report a scam
File a report with the Internet Crime Complaint Center – In order to file a report, you’ll need to provide the following information:
- Your name, mailing address, and telephone number.
- The name, address, telephone number, and web address, if available, of the individual or organization you believe defrauded you.
- Specific details on how, why, and when you believe you were defrauded.
Report the company to the Better Business Bureau (BBB) – If you have a company name or web address, use the BBB’s search tool to find out if there have been complaints filed. You can file your own complaint online.
Report spam on Facebook – The best way to report abusive content or spam on Facebook is by using the Report link that appears near the content itself. To report something someone posted on your Timeline:
- 1. In the top right of the post, click the down-pointing arrow
- 2. Select I don’t like this post
- 3. Select I think it shouldn’t be on Facebook and follow the on-screen instructions
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.