This day be a jolly day to be a scurvy pirate!
Celebrate all things pirate by installing a pirate-themed voice for your avast! Antivirus products. Download and install it from our Facebook avast! Voices tab and all yer antivirus alerts will henceforth be in a pirate voice. Go to avast! Voices on our Facebook page and choose Themed>1-pirate.mp3>Download Voice.
International Talk Like a Pirate Day started after syndicated columnist and author, Dave Barry, mentioned a group of zany guys who liked to talk using pirate lingo. Years earlier, these guys decided to start their own Talk Like a Pirate Day and make it a national holiday on September 19th. Trouble was, no one knew about it. But in 2002, when Dave Barry wrote about the fledgling holiday, it was a breakout success.
Since the name of our company, AVAST, also means stop or desist, as in “Avast, ye landlubbers!”, it made sense for us to be a part of the celebration. Jezebel, the Webwench from the Talk Like a Pirate’s Day crew declares,
avast! Antivirus software is the official AV protection of at least one-quarter of the Talk Like A Pirate Day crew. I installed the pirate voice and I LOVE IT SO MUCH, mate!
So join th’ ruckas this day, ‘n install th’ scurvy pirate voice on ye avast! Antivirus. Like our avast! Facebook page, click the avast! Voices tab and Talk Like a Pirate!
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.

 It’s more or less impossible to check all links individually in detail.
It’s more or less impossible to check all links individually in detail.  Some links are weaker than others and make the whole chain vulnerable.
Some links are weaker than others and make the whole chain vulnerable. When a vulnerability is found, it’s critical to fix it. CORRECTLY.
When a vulnerability is found, it’s critical to fix it. CORRECTLY. So, a patch is created…
So, a patch is created…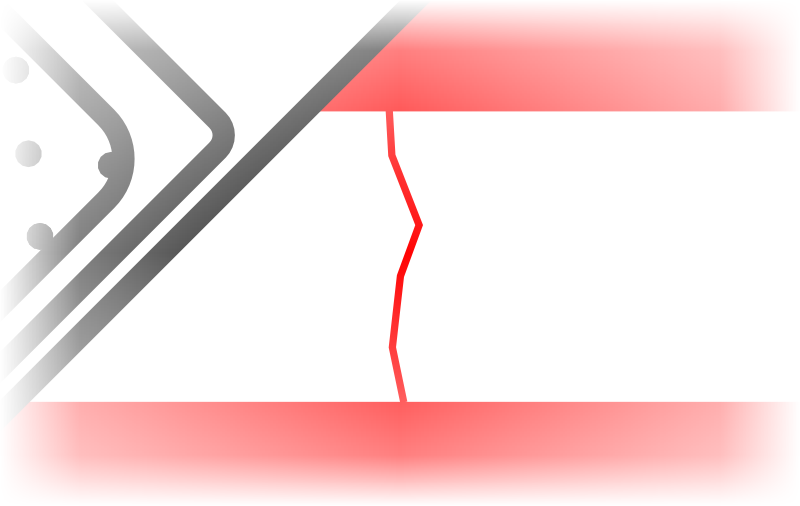 By looking closely where the patch was applied, it’s possible that a related and smaller vulnerability which is still not fixed might be easy to find, thanks to the information provided by the patch.
By looking closely where the patch was applied, it’s possible that a related and smaller vulnerability which is still not fixed might be easy to find, thanks to the information provided by the patch.