New research from ESET, which polled over 500 gamers, has found that 6% of gamers have spent around a full-day immersed in a video game.
The post Security takes a backseat for uninterrupted, video game marathons appeared first on WeLiveSecurity.
![]()
Antivirus Vendors
New research from ESET, which polled over 500 gamers, has found that 6% of gamers have spent around a full-day immersed in a video game.
The post Security takes a backseat for uninterrupted, video game marathons appeared first on WeLiveSecurity.
![]()

Pirates of old were on the hunt for gold, silver, and rum. Modern pirates just want WiFi — and they want it free.
The post Here come the free WiFi Pirates of the Adriatic appeared first on Avira Blog.

![]()

Though it may seem trivial, it is not: the security of your company and of your customers depends largely on the passwords that your employees use. In fact, should any of them make such a serious error as, for example, reusing their login credentials across different services, the consequences could be catastrophic, as Dropbox has recently learned.
Just a few days ago, the cloud storage company acknowledged that passwords of more than 68 million accounts had been leaked, with a security issue jeopardizing the information of its more tan 500 million users. All the problems started with a simple lapse on the part of one of the company’s employees
The incident occurred in 2012, when some Dropbox users began to complain: email accounts that they had used exclusively to register for the service had started to receive a lot of spam messages. The key to the mystery lay in the theft of passwords from a Dropbox employee: cyber-crooks had got hold of the employee’s LinkedIn password, which was the same as the one used for the cloud storage account. And in the Dropbox account, the employee had a document with a list of user’s email accounts. The perfect gift for spammers.
Some of the passwords that have now been leaked correspond to those accounts included in the previous theft some years before. In fact, a few days before its acknowledgement of this latest leak, Dropbox asked users that had not changed their passwords for some years to do so as soon as possible: “We’re reaching out to let you know that if you haven’t updated your password since mid-2012, you’ll be prompted to update it the next time you sign in. This is purely a preventative measure and we’re sorry for the inconvenience”, read the email.
Some of the passwords filtered correspond to hacked accounts years ago (…) Dropbox asked users that has not changed their passwords for 4 years ago to do so as soon as possible.
In short, poor password practice by employees in company email or service accounts can put the whole company at risk. In fact, Dropbox has already taken measures to enable employees to comply with corporate security rules, including among other things, not reusing passwords. You can also do the same. Panda’s security solutions include a password manager to facilitate the use of different passwords for different services, without having to memorize each one.
The post Companies that are making the same mistake as Dropbox appeared first on Panda Security Mediacenter.
In this article, ESET’s Miguel Ángel Mendoza asks: “At what age should kids be able to access online services?”
The post At what age should kids be able to access online services? appeared first on WeLiveSecurity.
![]()

Have you already heard about the term “Malvertising” in the mobile world?
The post Malvertising campaign intent on soiling Avira’s white vest appeared first on Avira Blog.
Google is looking to deliver even greater transparency when it comes to online security by identifying publicly – or “marking”, as it puts it – websites that are not as secure as they should be.
The post Google to draw attention to insecure HTTP websites appeared first on WeLiveSecurity.
![]()
WeLiveSecurity takes a look back at the life of the programming pioneer US Navy Rear Admiral Grace Hopper, who changed the world of technology.
The post Grace Hopper: Computer bugs & the language of programming appeared first on WeLiveSecurity.
![]()

In this new Tales from Ransomwhere we discovered the tricks of one of the most infamous families in the landscape of the ransomware: Locky .
Recently (our colleagues from Avira reported it in July) they added a new feature, it includes an offline mode so it is able to encrypt files when the connection to the server is not available. The weak point is that this key is the same for every computer which files are encrypted, that’s why this is just something that is performed when for some reason the C&C server is unavailable.
On top of this now they have changed the way they infect computers. Usually these attacks rely on a small downloader Trojan who downloads and executes the ransomware. For example, when the attack comes from a javascript file, this usually downloads a small executable which only function is to get the ransomware and execute it. As I have explained in previous articles, cybercriminals are all the time making small changes trying to avoid detection from security solutions.
In this case the attack is being distributed through email, we have seen a number of them with a zip file that has a javascript file inside named “utility_bills_copies <random characters>.js”. However there are different versions using different subjects and file types, for example this one:
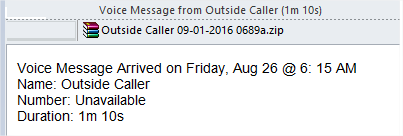
Which inside has the following file:
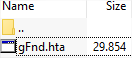
They have skipped the downloader Trojan part and the script gets the Locky variant in DLL format (with the downloader in most cases the downloaded file was an EXE), which is executed using Windows rundll32.exe. The first sighting of this was on August 22nd, and so far they keep using the same strategy. As you can see they are launching one wave per week:
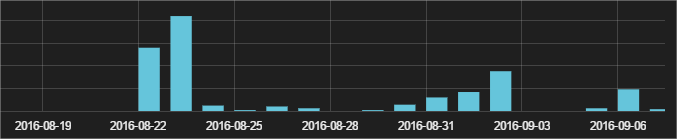
We have seen just a few hundred infection attempts mainly in North and South America and Europe, although there are some in Africa and Asia too. In case they get a good return of investment we’ll probably see an increase in the next weeks. Here you can find a few hashes of this Locky variant:
The post Know the tricks of the new Locky appeared first on Panda Security Mediacenter.
Kaspersky Lab announced today its experts have discovered a new version of the RAA ransomware, a malware written entirely on JScript.