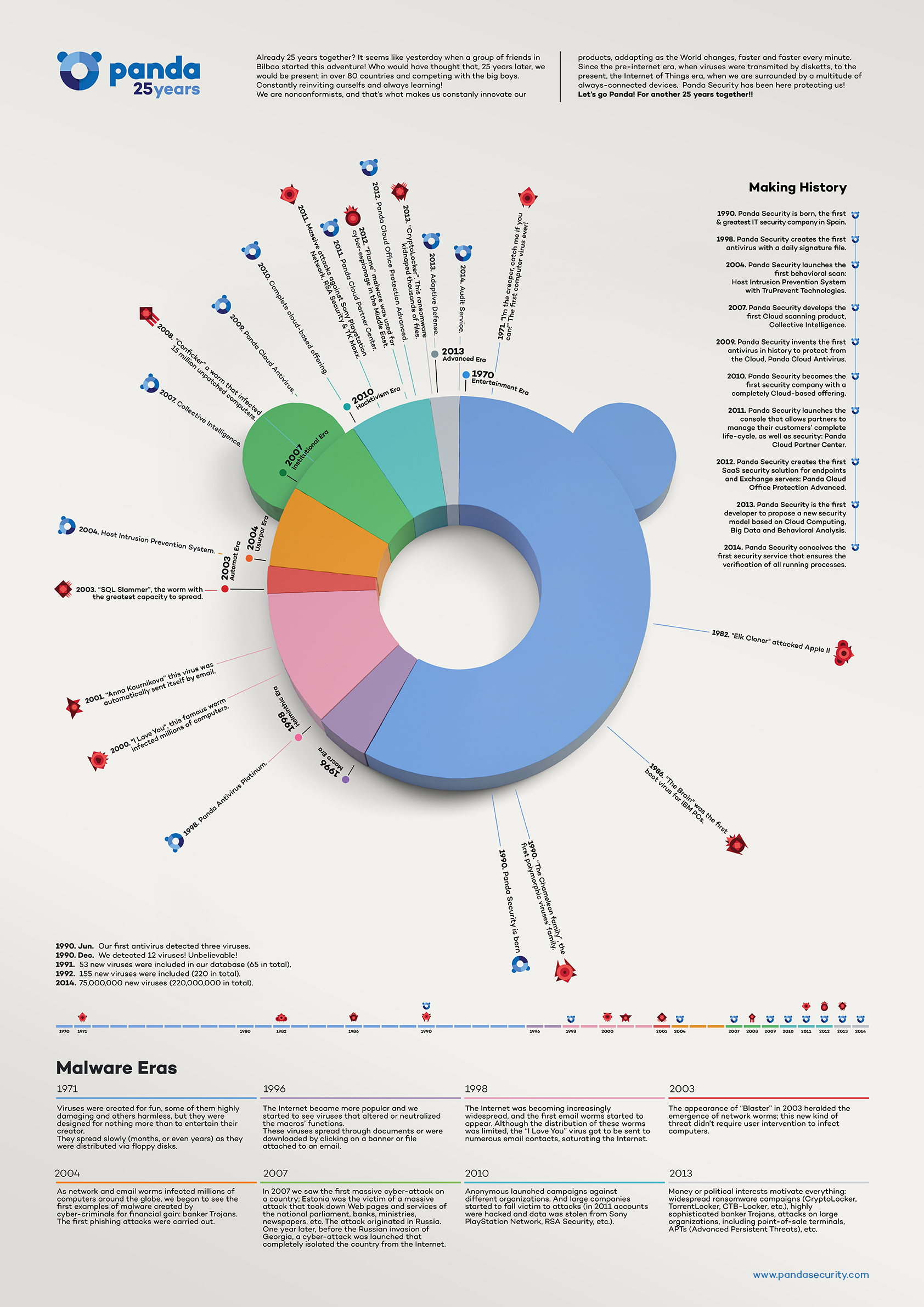
Smart TVs bring along benefits that actual televisions can’t offer. Internet access and communication with other devices make possible choose your broadcast program, share your favorite shows, watch YouTube videos and use other apps that we already have on our phones.
As Google couldn’t be less, has already launched Android TV, their small-screen Android operation system. We hope that the giant and the other technological companies are aware that connected TVs not only come loaded with virtues, but also with risks in security issues.
At least for now it doesn’t offer such a wide range of possibilities as smartphones, and it is neither a personal computer, but everything points that in a couple of years they will offer similar benefits. Take for example banking operations, like managing our accounts through the banks virtual platforms or online shopping. A delicious treat for cybercriminals.

A recent research of the European Union Agency for Network and Information Security (ENISA) identifies the cyberattacks as the main threats for Smart Homes, this threat will increase as more and more devices are connected within them and the network.
Apart from banking information, there is much more data at the mercy of the assailants. We just have to take a look into the new controversy that splattered Samsung, accused of listening to their customers conversations through their Smart TV’s microphones.
This is because the service conditions advise that in order to enable Voice Recognition, some voice commands must be captured and analyzed through remote control. The privacy policy states: “Please be aware that if your spoken words include personal or other sensitive information, that information will be among the data captured and transmitted to a third party.”
Samsung is not the first company accused of recording their viewers. In 2013, a British developer discovered that LG’s Smart TV was gathering information about the user’s television habits via its smart ad feature. Later that year, Malik Mesellem expert in cyber security found a weakness in Samsung TVs that would make them liable to denial-of-service attacks (the famous DDos).

Despite the South Korean company has strongly denied the listening’s accusation, and “third parties” would only be the company responsible of converting the voice commands into orders, suspicions have not disappeared. If they can spy with your phone microphone, why wouldn’t they do it through this one?
Nor should we forget that TVs also incorporate cameras, so making video calls is just around the corner. As we are connected to the Net, digital offenders may have access to images of your living room. Creating a new window for cyberespionage, directly into your home.
These devices also store large amounts of personal data, all kinds of documents stored both in the device’s internal memory and in the cloud. A malware installed in the TV could extract information and miss use it.
Experts admit that we must not fall into alarmism and completely reject smart appliances, but is important that we know the risks and be careful.
So if you have an Android operating system TV, the best thing you can do is protect it with Panda Mobile Security, our antivirus for Android. You will not regret it!
The post Smart TVs have become the new target for cyber criminals appeared first on MediaCenter Panda Security.