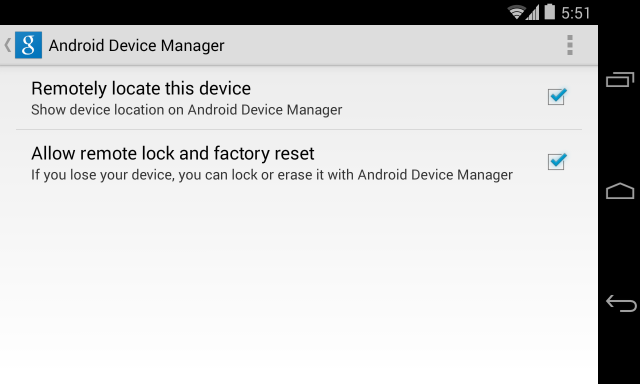
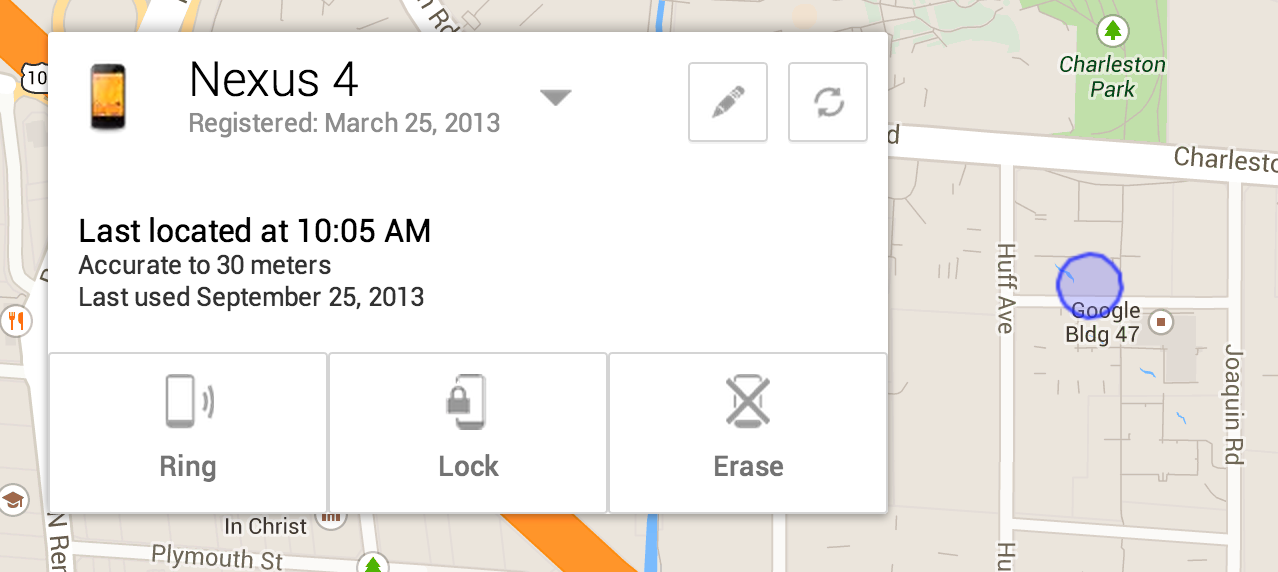
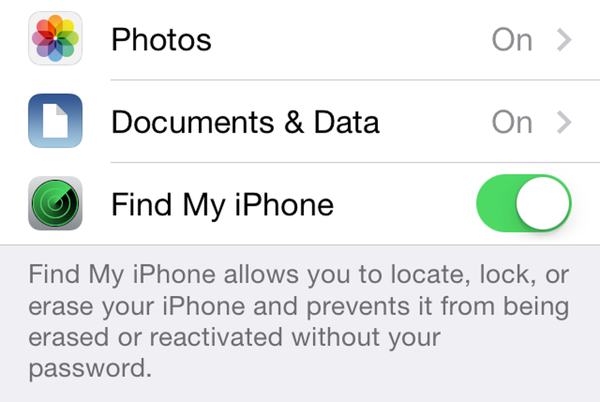
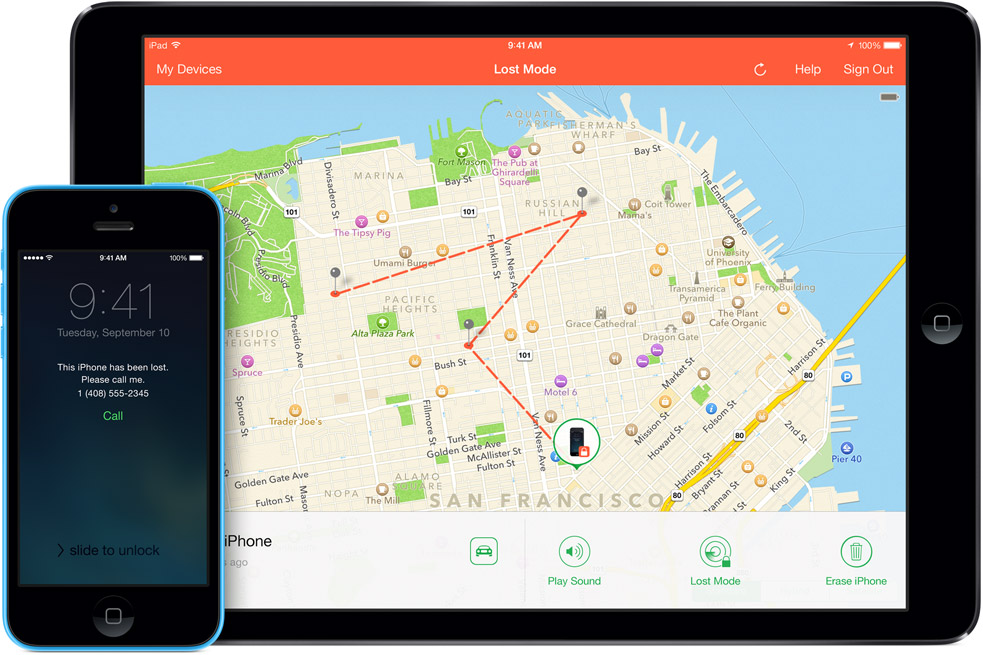
Mid January we informed you of a data-stealing piece of Android malware called Fobus. Back then Fobus mainly targeted our users in Eastern Europe and Russia. Now, Fobus is also targeting our users in the USA, United Kingdom, Germany, Spain and other countries around the world.
Fobus can cost its unaware victims a lot of money, because it sends premium SMS, makes calls without the victims’ knowledge and can steal private information. More concerning is that Fobus also includes hidden features that can remove critical device protections. The app tricks users into granting it full control of the device and that is when this nasty piece of malware really begins to do its work. You can find some more technical details and analysis of Fobus in our previous blog post from January.
Today, we decided to look back and check on some of the data we gathered from Fobus during the last six months. We weren’t surprised to find out that this malware family is still active and spreading, infecting unaware visitors of unofficial Android app stores and malicious websites.
The interesting part of this malware is the use of server-side polymorphism, which we suspected was being used back in January but could not confirm. We have now confirmed that server-side polymorphism is being used by analyzing some of the samples in our database. Most of these have not only randomly-generated package names, but it also seems that they have randomly-generated signing certificates.
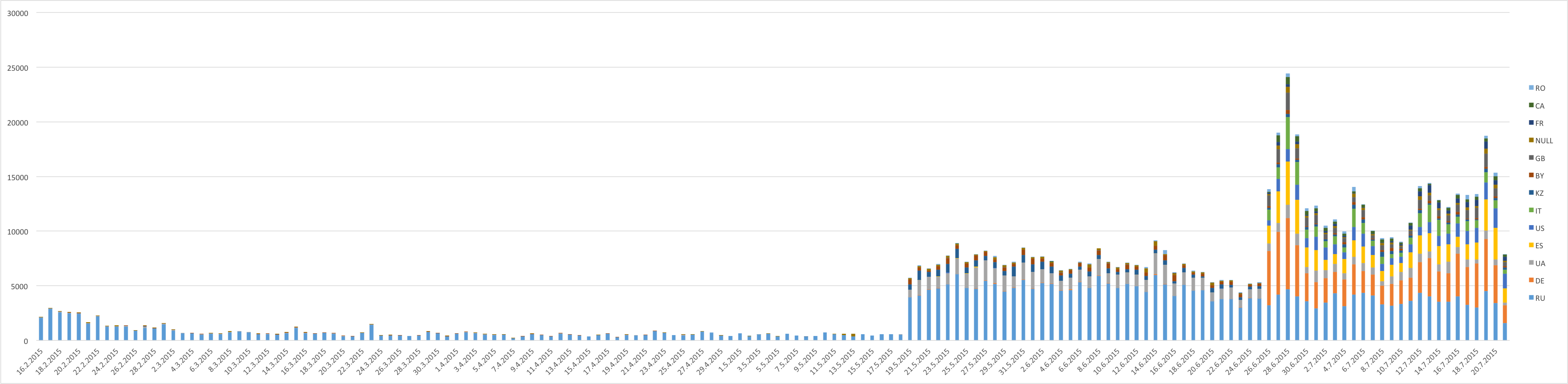
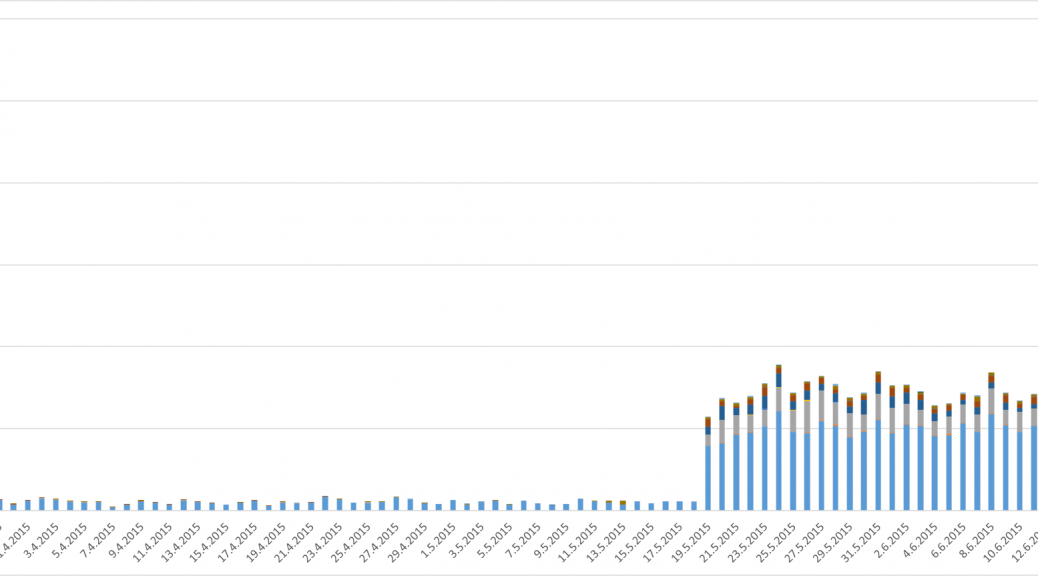
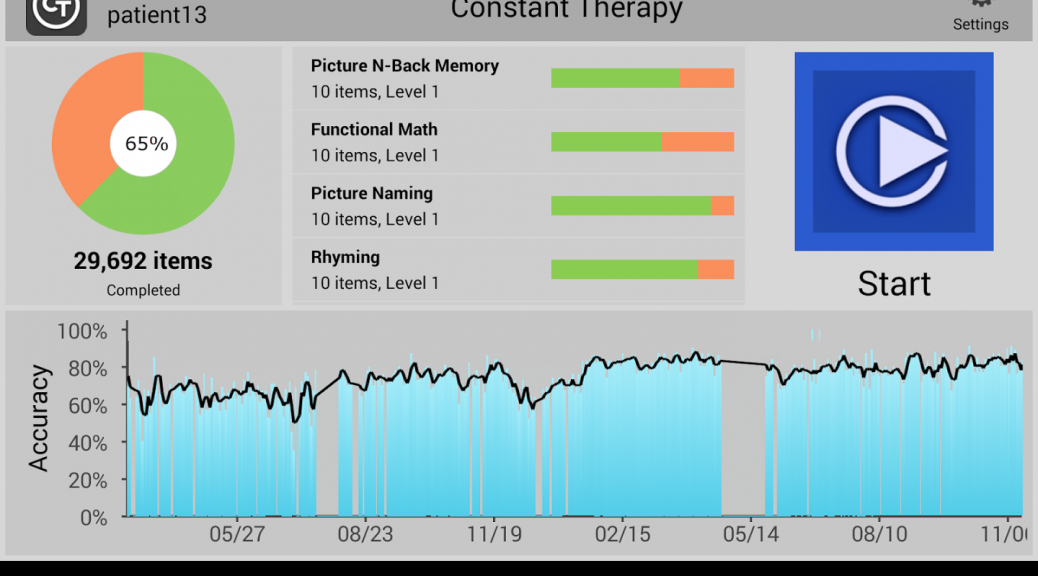
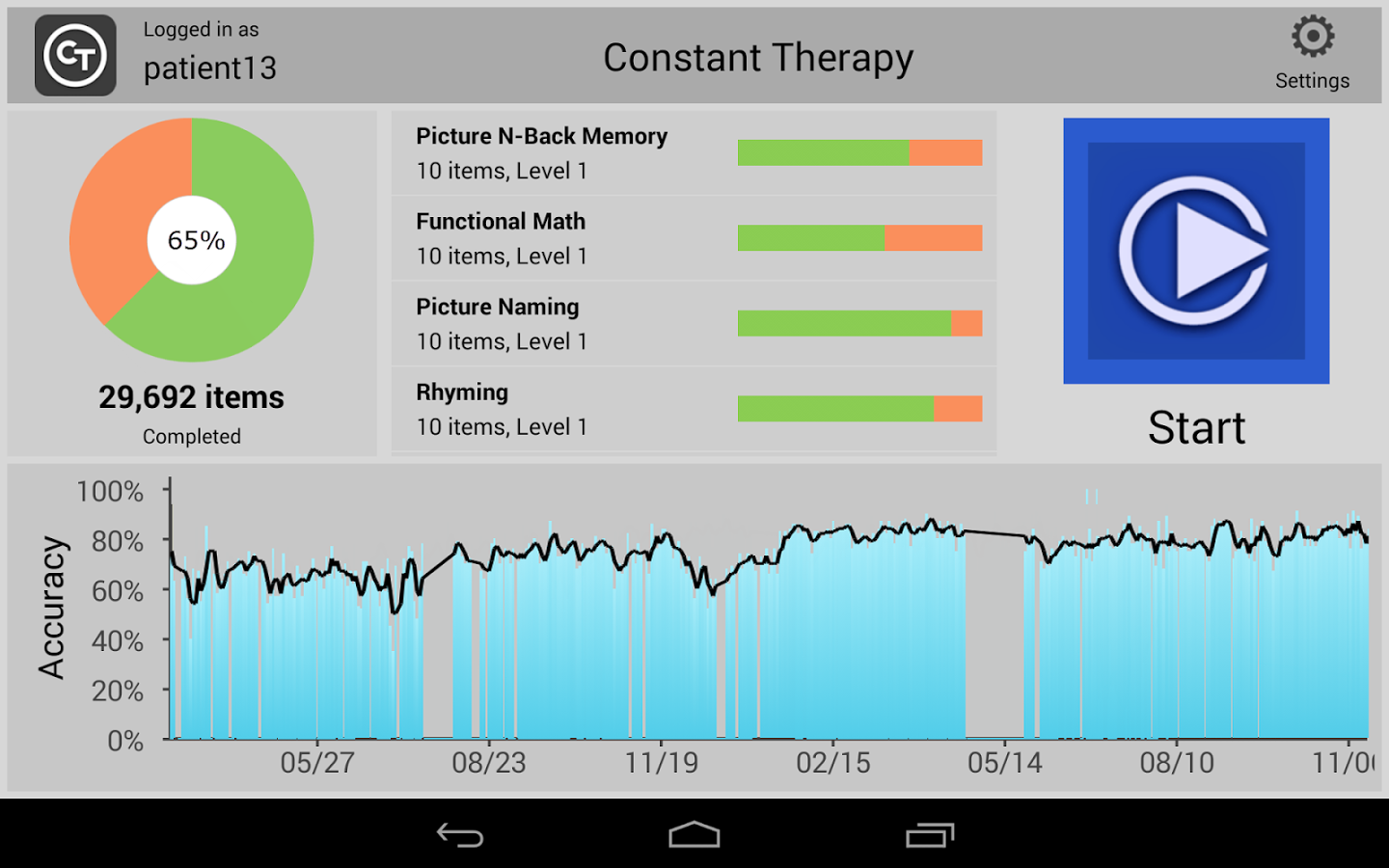
Number of users who have encountered Fobus
Geographical reach expanded from the East to the West
Previously, we predicted that we would probably see a steady growth in the number of encounters users have with this malicious application. A review of the results, however, beats all of our predictions. At the beginning, this malware mainly targeted mobile users in Russian speaking countries. As our detections got smarter and we discovered new mutations of Fobus, we discovered that many other countries are affected as well. Now Fobus, although it still mainly targets users in Eastern Europe and Russia, is also targeting our users in the USA, Germany, United Kingdom, Spain, and other countries around the world.
The above graph shows the number of unique users (user IDs) encountering Fobus per day. The graph is also geologically divided by country codes as reported by the users’ connection location.
Number of times users encountered Fobus by country (as of July 21, 2015):
- Russia: 87,730
- Germany: 25,030
- Spain: 12,140
- USA: 10,270
- UK: 6,260
- Italy: 5,910
There are two great leaps visible in the graph, which mark the days when new versions of Fobus were discovered and new detections protecting our users were released. These three detections seem to be particularly effective at their task. The high impact in countries outside of Russia and English speaking regions, which can be seen in the graph, is a little surprising. Especially considering that the malware typically is only in Russian and English and even the English version contains some strings in Russian. Seems like the authors were too lazy to translate their own app properly…
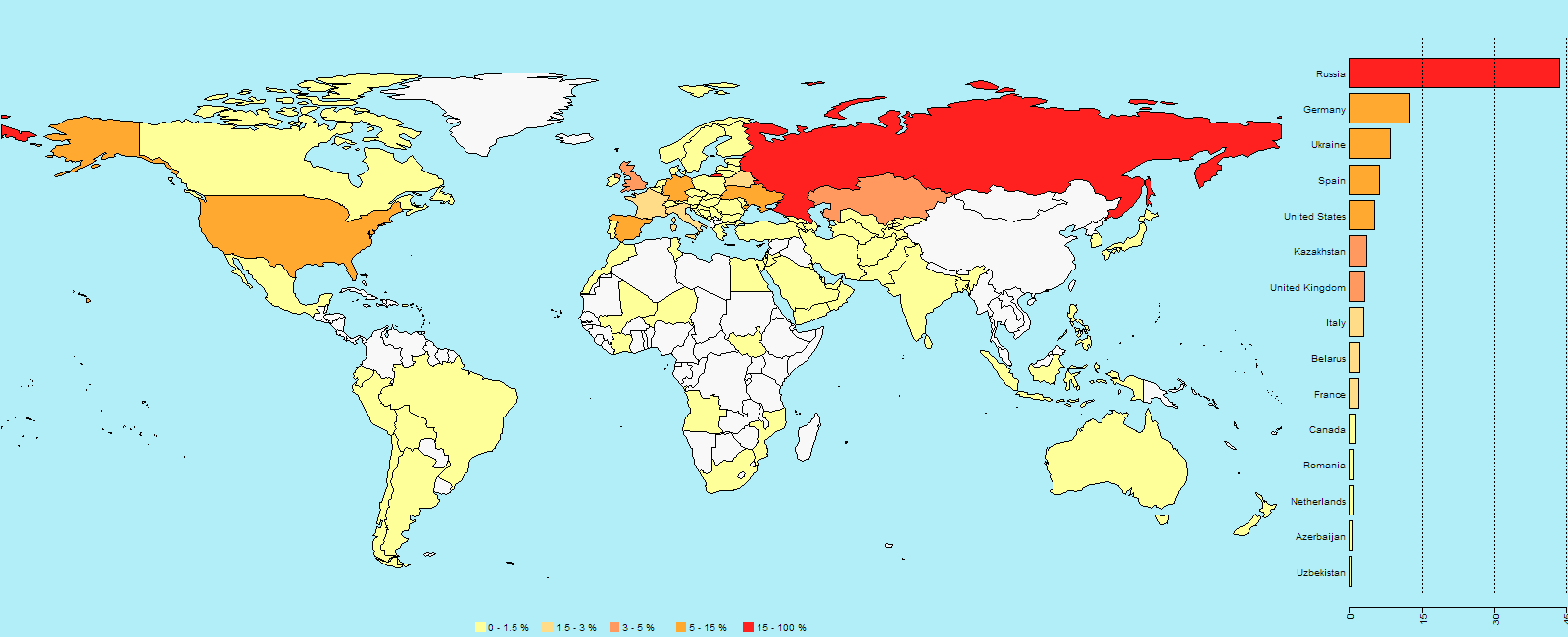
World map showing the percentage of users who encountered Fobus
An app, built just for you
Now, let’s dig into the analysis. We will look at the certificates used to sign some of the Fobus samples. We already mentioned the problems connected with generating unique applications for each victim (server-side polymorphism). This does not only apply to rebuilding, repackaging and obfuscating each instance of the app itself, but also extends to their signing certificates. To back this up, we analyzed around 4,000 samples and data and inspected the usage of these certificates. We verified that each build of the malicious app is typically seen by one user only, even though its signing certificate can be used to sign multiple apps. Virtually all of the samples we have are very low prevalent, meaning that different users only very rarely see an app instance multiple times. As for the signing certificates, we believe that they are being regenerated on a timely basis. We were able to pick a few examples of such certificates from our statistics.
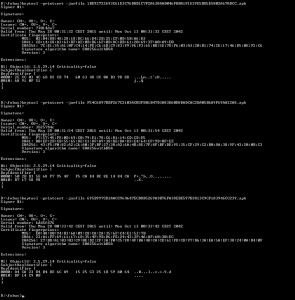
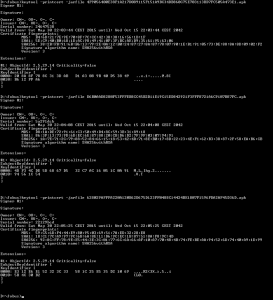
As you can see from the screenshots above, these certificates are dated the 28th and 30th May 2015 and the time differences in the beginning of the validity period between these certificates are in the order of minutes, sometimes even seconds. We have also found some samples that have certificates with randomly generated credentials altogether.

The above provided screenshot is an example of such randomly generated certificates.
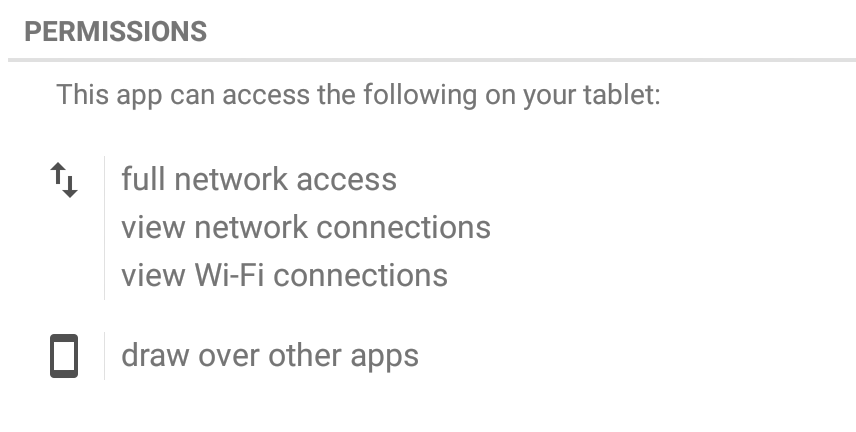
To conclude, we would like to encourage you to think twice about the apps you install on your phone. Especially if the apps you download are from third party stores and unknown sources. If you download apps from the Google Play Store you’re on the safe side. Requiring nonstandard permissions – especially permissions that don’t seem necessary for the app to properly function – may be a sign that something fishy going on. You should be very suspicious of an app that requests device administrator access and think twice before downloading it.
Acknowledgement
Special thanks to my colleague, Ondřej David, for cooperation on this analysis.