On a typical business or vacation day, my phone barely makes it through the day: A bit of Googling here, a bit of research there, some email and gaming in between and before I know it, my battery life is down to 10% and it’s only 4pm!
It’s not necessarily my smartphone’s fault, but likely a consequence of the demanding apps that I run, often completely invisibly in the background. These apps drain not just battery life but also fill up my storage or cause a ton of mobile traffic.
Turns out, I’m not alone.
When looking at one million of our anonymous AVG AntiVirus and AVG Cleaner users, we discovered the most resource-hungry apps in the first quarter of 2015. Plus, we found the most-used apps in each category! Curious as to what’s new this quarter?
Key findings:
Dating & chatting apps surge into the Top 10
Android owners worldwide were trying to meet Mr or Mrs Right in the first three months of 2015. POF Free Dating entered the Top 10 and there was a new entrant at number six from the chat category, OoVoo Video & Text, which also had a noticeable impact on battery life.
Facebook Messenger is now the top communication app:
Facebook Messenger has previously been ranked as the third most popular communication app behind WhatsApp and Google Mail but has since overtaken them and now sits top of the pile.
Samsung Knox, Samsung Push, and Beaming Service are the top battery drainers
Samsung’s KNOX security service drains the battery of your Galaxy smartphone invisibly in the background.
In addition, the built-in Samsung Push Service now also runs in the background and made it to 7th position. This service is required for ChatON, a WhatsApp rival that packaged with almost all of the company’s handsets. The good news for your batter is that Samsung turned it off on February 1st.
The top spot among battery draining apps is a background service called Beaming Service by Mobeam Inc., which also comes bundled with many Samsung phones.
Tip: See our all-new AVG Android Optimization Guide to identify and turn off such resource-hungry apps.
Cleaning and security apps that drain your phone
People looking to protect and clean their phone should know some of the top used apps, including Lookout Security & Antivirus and Clean Master, show up in the top spots on our lists of top battery drainers and traffic consuming apps. What’s interesting is that 88% of all measured apps in the traffic consumption category consume less traffic than Clean master, which clocked in at several hundred megabytes of data per user.

New gaming style on the rise: casino games start a new trend
In the first three months of 2015, we identified a massive spike in the use of card and casino games as well as big blockbuster arcade games.
While the casino category didn’t even exist previously due to its low usage, in the January to March period of 2015, it featured as up to 7% of usage, and arcade games also grew to 12% usage from 1.6% in the previous quarter. Solitaire and Zynga’s Livepoker stood out as particularly popular.
Conversely, we spent far less time playing casual, strategy, puzzle or family games. See graph below:
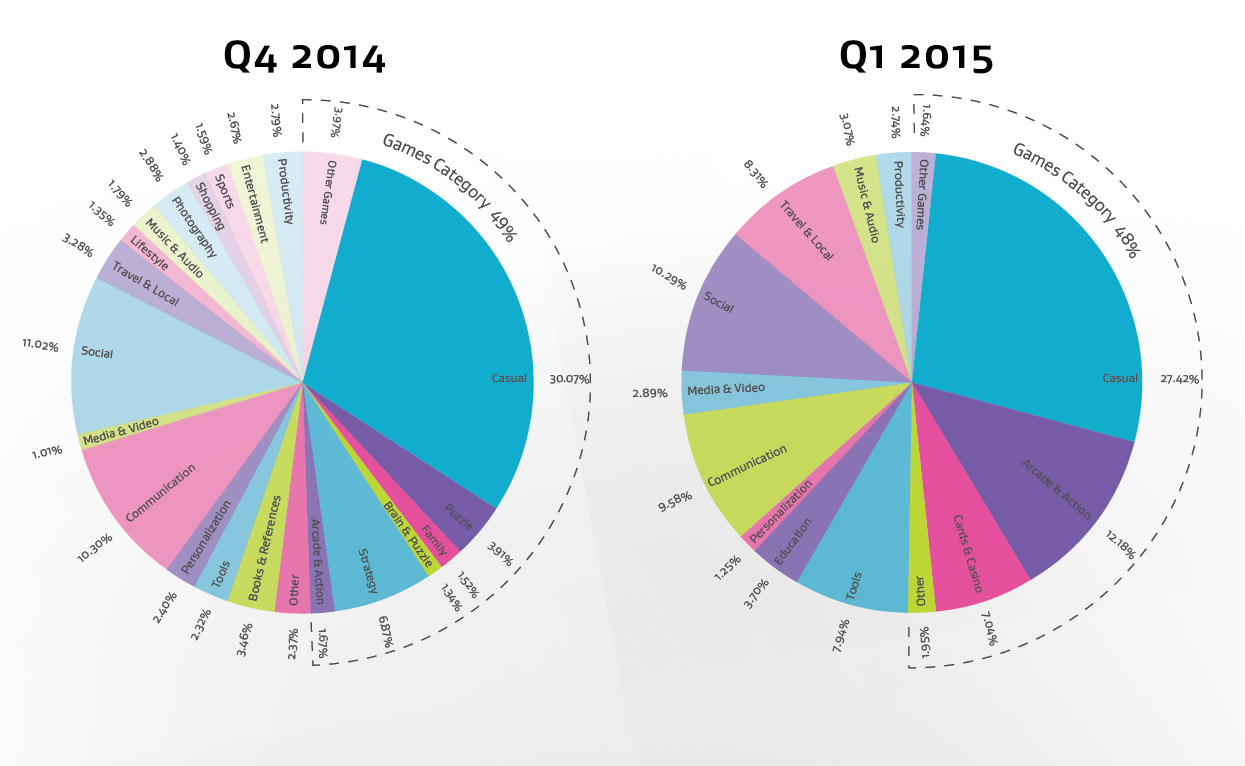
Find a full list and all the data in our app report here.
So what are you supposed to do if you’ve got one or even many of our resource drainers installed? Our AVG Android Performance Guide will help you out with great tips to improve battery life and clean up space in no time!
For highlights from the report, check out the infographic below.