BlackBerry used to define the Smartphone sphere. Once popular for its physical keyboard and exclusive-for-users IM service, now BlackBerry has been left out in the cold. The Canadian company recently announced that they will no longer make the devices. However, they will continue to market the phones that will be manufactured by other companies. So, why buy a BlackBerry in 2016?
Because they’ve got an incredible reputation for security (as a matter of fact, many government officials use BlackBerry devices for that reason). In 2000 the brand was known as Research In Motion (RIM) and offered Subscription-based emailing. At this time, all emails sent and received by BlackBerry phones had to pass through highly-protected servers. This means that an attacker wouldn’t be able to intercept the phone’s messages. This encryption measure is pretty common in today’s phones, but it wasn’t 16 years ago.
User security remains a priority for BlackBerry. They have hardened security in their newest model, the DTEK50– a Smartphone manufactured by Alcatel that’s running on Android.
The phone is also named “the smartest smartphone in the world” and has a number of security-related features. This super secure Smartphone encrypts its users’ photographs, bank information and also uses the software necessary to store passwords safely. It also notifies its owners if someone uses the camera remotely to take photos or videos, or if the microphone is being used to record conversations.
Most businesses think about security when building their IT infrastructure. By focusing exclusively on the corporate environment, BlackBerry is going back to its roots, and for good reason: it doesn’t matter who continues to make BlackBerry phones, the company still promises to enforce the strongest security possible.
The post Bye Bye BlackBerry. There’s a new kind of smartphone security. appeared first on Panda Security Mediacenter.





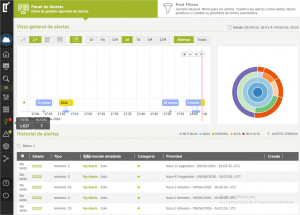 In addition to the existing Big Data Cloud Service and its real-time alerts, the latest version includes predefined and adaptable analysis with three different action areas:
In addition to the existing Big Data Cloud Service and its real-time alerts, the latest version includes predefined and adaptable analysis with three different action areas:

 In addition to the physical iPhones, a new operating system is also added to the new 7. The iOS 10 is presumed to be more robust in terms of cybersecurity (this is great news, especially after discovering various faults in the beta operating system).
In addition to the physical iPhones, a new operating system is also added to the new 7. The iOS 10 is presumed to be more robust in terms of cybersecurity (this is great news, especially after discovering various faults in the beta operating system).
 Except for the few of us who choose to visit faraway places at other times of the year, for the majority of us, our vacation time is coming to end. Whether we are refreshed or nostalgic for our summertime getaway, let’s make sure to take into account our IT security while we get back on track.
Except for the few of us who choose to visit faraway places at other times of the year, for the majority of us, our vacation time is coming to end. Whether we are refreshed or nostalgic for our summertime getaway, let’s make sure to take into account our IT security while we get back on track.
 It is reaching the end of its first year and now companies are asking, is it the right moment to update to Windows 10?Now that it’s becoming somewhat mature, should businesses take the plunge and invest time and money to upgrade their software? The general opinion is that yes, companies should upgrade. After all, it takes far less time and resources to plan the transition than to deal with it after problems emerge due to outdated software.
It is reaching the end of its first year and now companies are asking, is it the right moment to update to Windows 10?Now that it’s becoming somewhat mature, should businesses take the plunge and invest time and money to upgrade their software? The general opinion is that yes, companies should upgrade. After all, it takes far less time and resources to plan the transition than to deal with it after problems emerge due to outdated software.