The Avast Virus Chest is a safe place to store potentially harmful files. These files are completely isolated from the rest of the operating system, meaning that they are not accessible for any outside process or software application. Files cannot be run while stored in the Virus Chest.
How to open the Avast Virus Chest
To open the Virus Chest, right click on Avast’s little orange ball icon in the system tray in the bottom right hand corner of your computer. Select Open Avast user interface from the menu. Another way to open the user interface is to double click the desktop icon.
From the main menu, select Scan, then Scan for viruses, and then click the Quarantine (Virus Chest) button at the bottom of the screen to open the Virus Chest window.
If Avast 2015 detects an infected or suspicious file, it will try to repair it at first. Unfortunately, some files cannot be repaired so Avast will try to move the file to the Virus Chest. If the infected file refuses to move to the Virus Chest, it will be automatically deleted from your computer.
How to set up quick access to the Virus Chest
For quick access to the Virus Chest, you can assign it to one of the four shortcut squares in the Avast user interface. To change which function you see, click on the drop-down menu icon in the top right hand corner of the square. There you will find a choice to place the Virus Chest right on the Overview of your Avast product.
Once you have the shortcut on the user interface, then simply click it to open the Virus Chest.
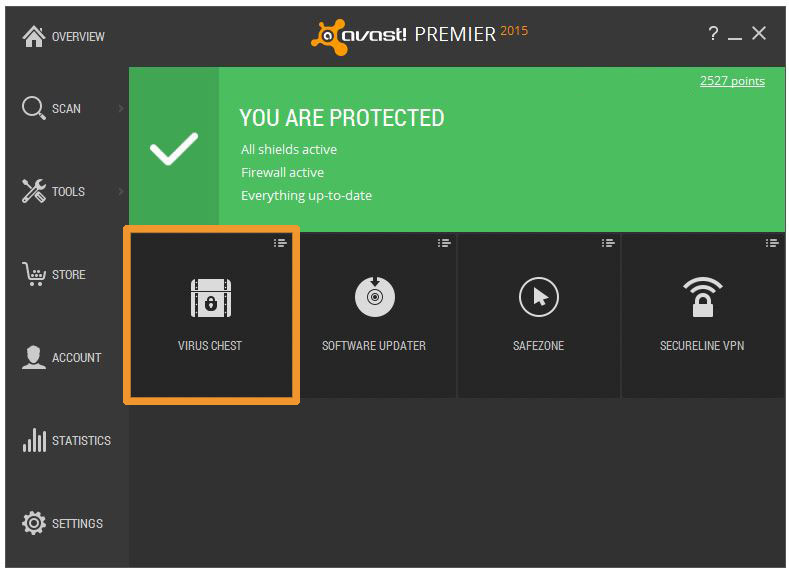
Set the shortcuts that you want in the Avast user interface.
You can perform different actions while in the Virus Chest
You can perform different actions on the file inside the Virus Chest by right clicking. For example, you can
- Restore a file
- Exclude it from scanning
- Report it to the virus lab
- Delete the file
Once you have made the decision on which action to take, you will be asked to confirm your choice. When you have finished, close the Virus Chest to exit.
NOTE: Exercise extreme caution when restoring a file from the Virus Chest as it may still be infected. This is a high security risk action that requires advanced skills and experience handling infected files to avoid further potential infection of your computer.
How to manually move a file to the Virus Chest
If you need to move a file manually into the Virus Chest, right click anywhere on the contents table on the Virus Chest screen and select Add from the menu. A navigation dialog will open so all you need to do is locate the desired file that you want to move. Then click the Open button. The desired file will then appear in the contents table on the Virus Chest screen.
How to restore files from the Avast Virus Chest
When you open the Virus Chest, you will see a list of files contained within it. Right click on the file that you want to restore and the drop-down menu will appear. Select the Extract option, then select the location to save the file and click OK to close your window.